Computer Science > QUESTIONS & ANSWERS > CISSP 1356 Exam Questions with 100% Correct Answers and Explanations (All)
CISSP 1356 Exam Questions with 100% Correct Answers and Explanations
Document Content and Description Below
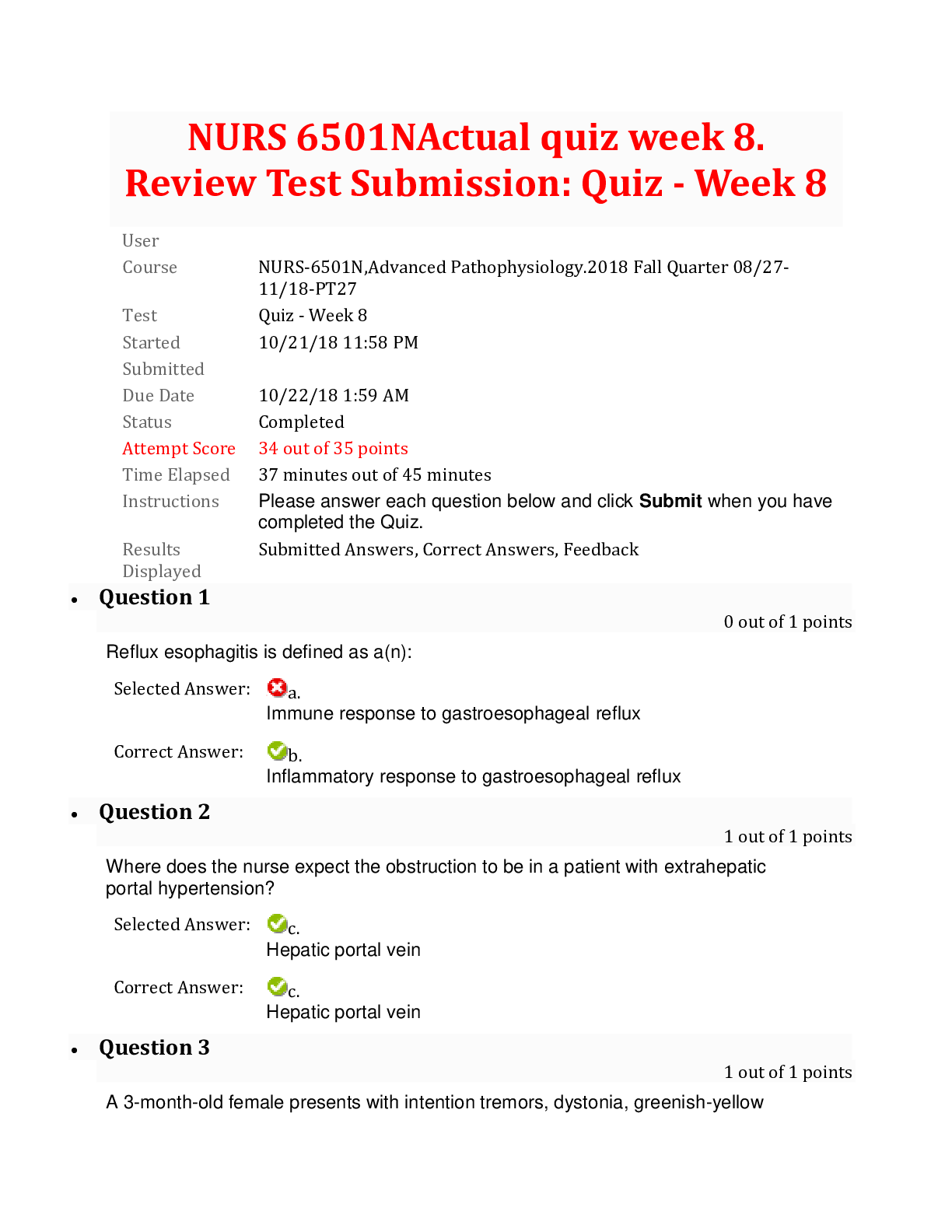
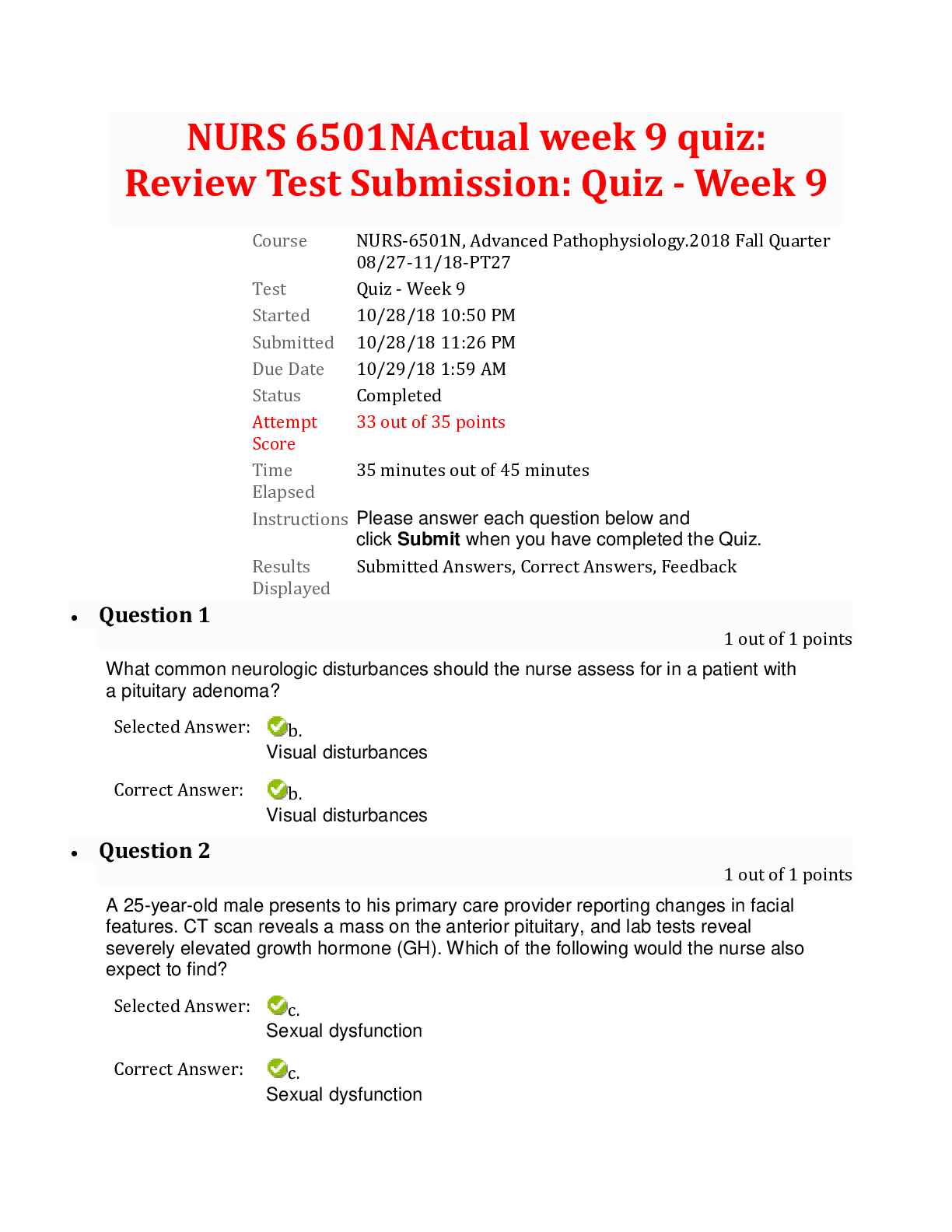
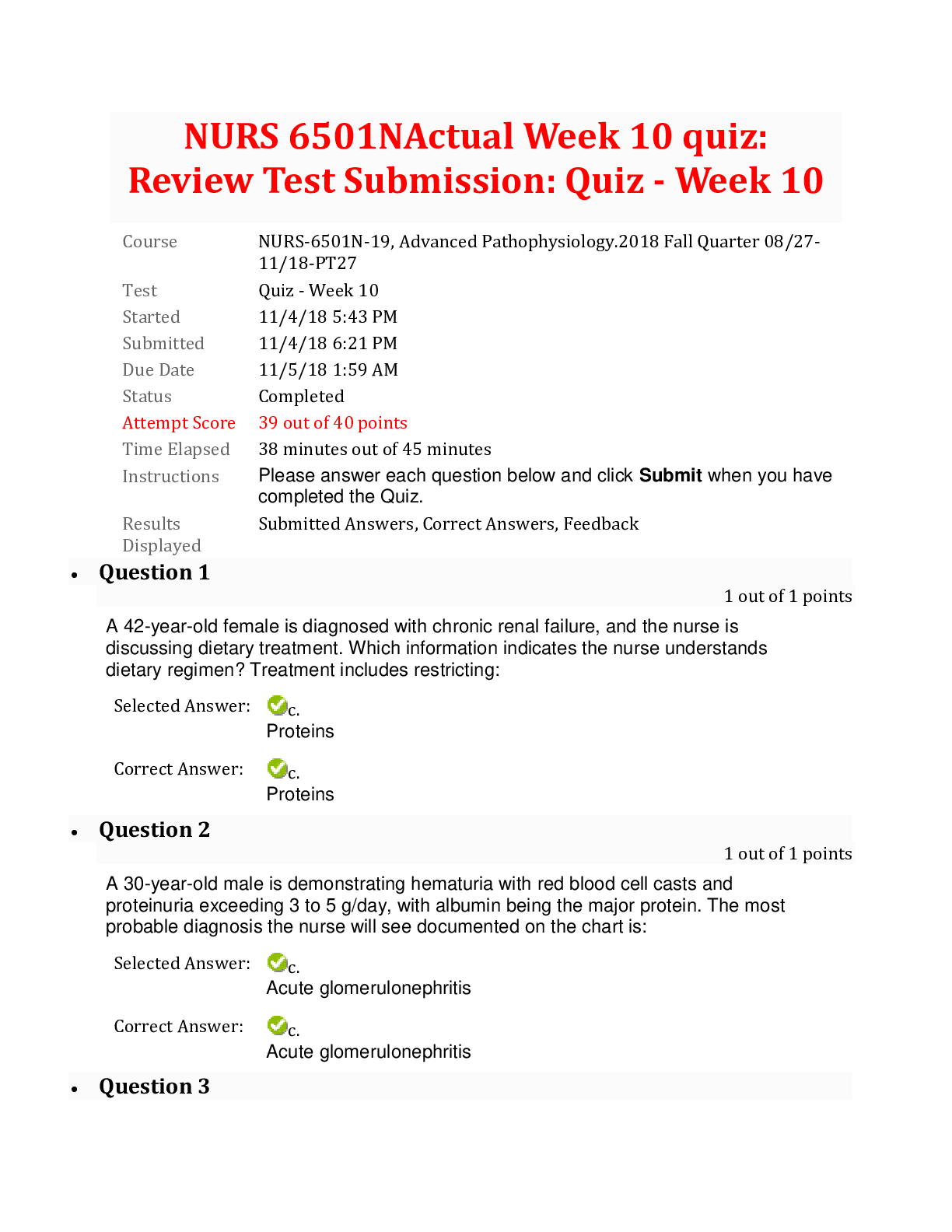
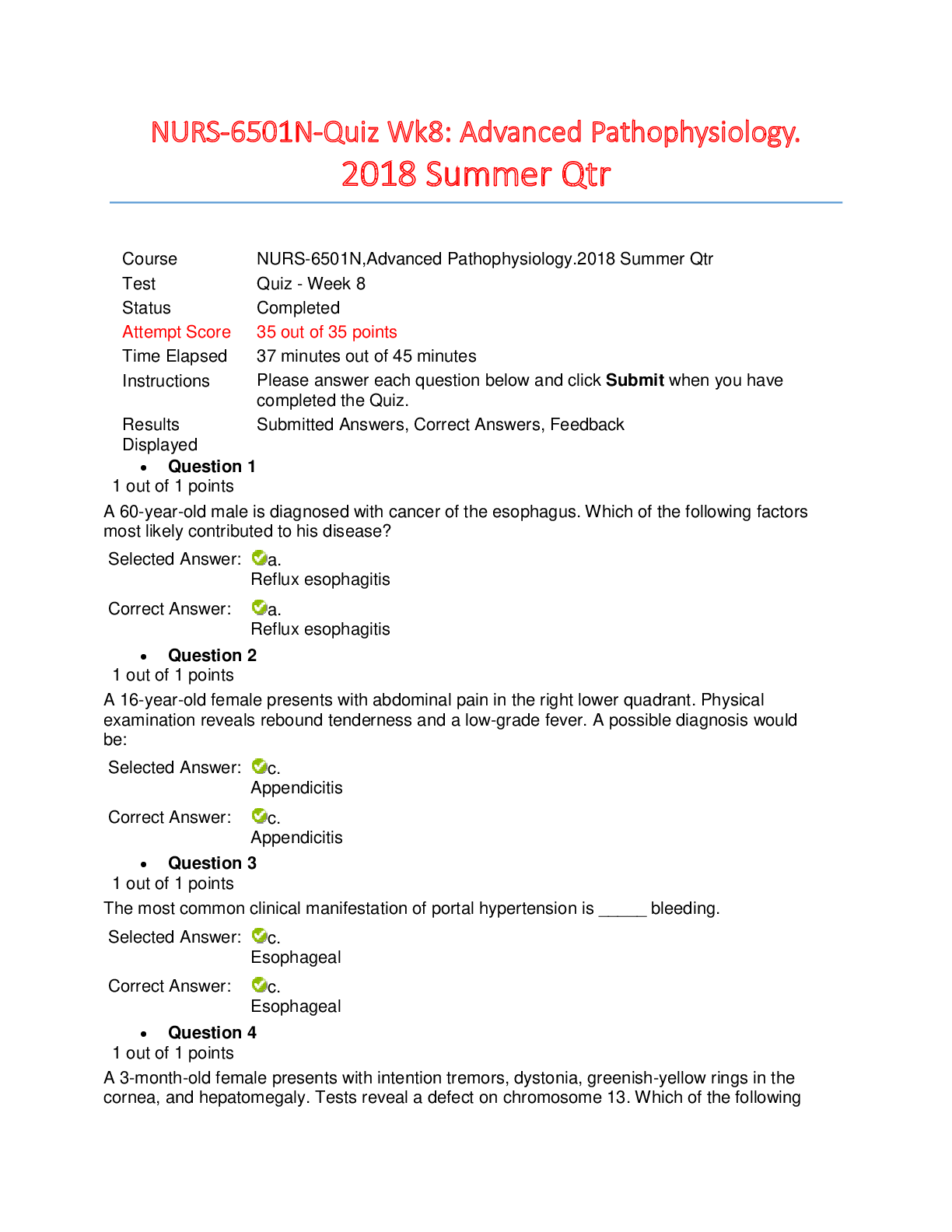
Topic 1, Access Control QUESTION NO: 1 A potential problem related to the physical installation of the Iris Scanner in regards to the usage of the iris pattern within a biometric system is: A. Co... ncern that the laser beam may cause eye damage. B. The iris pattern changes as a person grows older. C. There is a relatively high rate of false accepts. D. The optical unit must be positioned so that the sun does not shine into the aperture. Answer: D Explanation: The optical unit of the iris pattern biometric system must be positioned so that the sun does not shine into the aperture. QUESTION NO: 2 In Mandatory Access Control, sensitivity labels attached to object contain what information? A. The item's classification B. The item's classification and category set C. The item's category D. The item's need to know Answer: B ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 2Explanation: A sensitivity label is required for every subject and object when using the Mandatory Access Control (MAC) model. The sensitivity label is made up of a classification and different categories. QUESTION NO: 3 Which of the following is true about Kerberos? A. It utilizes public key cryptography. B. It encrypts data after a ticket is granted, but passwords are exchanged in plain text. C. It depends upon symmetric ciphers. D. It is a second party authentication system. Answer: C Explanation: Kerberos makes use of symmetric key cryptography and offers end-to-end security. The majority Kerberos implementations works with shared secret keys. QUESTION NO: 4 Which of the following is needed for System Accountability? A. Audit mechanisms. B. Documented design as laid out in the Common Criteria. C. Authorization. D. Formal verification of system design. ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 3Answer: A Explanation: Accountability is the ability to identify users and to be able to track user actions. Through the use of audit logs and other tools the user actions are recorded and can be used at a later date to verify what actions were performed. QUESTION NO: 5 What is Kerberos? A. A three-headed dog from the Egyptian mythology. B. A trusted third-party authentication protocol. C. A security model. D. A remote authentication dial-in user server. Answer: B Explanation: Kerberos is a third-party authentication service that can be used to support SSO. Kerberos (or Cerberus) was the name of the three-headed dog that guarded the entrance to Hades in Greek mythology. QUESTION NO: 6 Kerberos depends upon what encryption method? A. Public Key cryptography. B. Secret Key cryptography. C. ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 4El Gamal cryptography. D. Blowfish cryptography. Answer: B Explanation: Kerberos makes use of symmetric key cryptography and offers end-to-end security. The majority Kerberos implementations works with shared secret keys. QUESTION NO: 7 A confidential number used as an authentication factor to verify a user's identity is called a: A. PIN B. User ID C. Password D. Challenge Answer: A Explanation: Personal Identification Number (PIN) is a numeric password shared between a user and a system, which can be used to authenticate the user to the system. QUESTION NO: 8 Individual accountability does not include which of the following? A. unique identifiers B. ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 5policies & procedures C. access rules D. audit trails Answer: B Explanation: Accountability would not include policies & procedures because while important on an effective security program they cannot be used in determining accountability. References: A: Accountability would include unique identifiers so that you can identify the individual. C: Accountability would include access rules to define access violations. D: Accountability would include audit trails to be able to trace violations or attempted violations. References: Harris, Shon, All In One CISSP Exam Guide, 6th Edition, McGraw-Hill, 2013, pp. 248-250 QUESTION NO: 9 Which of the following exemplifies proper separation of duties? A. Operators are not permitted modify the system time. B. Programmers are permitted to use the system console. C. Console operators are permitted to mount tapes and disks. D. Tape operators are permitted to use the system console. Answer: A ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 6Explanation: Changing the system time would cause logged events to have the wrong time. An operator could commit fraud and cover his tracks by changing the system time to make it appear as the events happened at a different time. Ensuring that operators are not permitted modify the system time (another person would be required to modify the system time) is an example of separation of duties. The objective of separation of duties is to ensure that one person acting alone cannot compromise the company’s security in any way. High-risk activities should be broken up into different parts and distributed to different individuals or departments. That way, the company does not need to put a dangerously high level of trust in certain individuals. For fraud to take place, collusion would need to be committed, meaning more than one person would have to be involved in the fraudulent activity Job rotation in the workplace is a system where employees work at several jobs in a business, performing each job for a relatively short period of time. QUESTION NO: 10 An access control policy for a bank teller is an example of the implementation of which of the following? A. Rule-based policy B. Identity-based policy C. User-based policy D. Role-based policy Answer: D Explanation: Role-based access control is a model where access to resources is determined by job role rather than by user account. In this question, a bank teller is a job role. Therefore, an access control policy for a bank teller is a role-based policy. Within an organization, roles are created for various job functions. The permissions to perform certain operations are assigned to specific roles. Members or staff (or other system users) are assigned particular roles, and through those role assignments acquire the computer permissions to perform particular computer-system functions. Since users are not assigned permissions directly, but only acquire them through their role (or roles), management of individual user rights ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 7becomes a matter of simply assigning appropriate roles to the user's account; this simplifies common operations, such as adding a user, or changing a user's department. QUESTION NO: 11 Which one of the following authentication mechanisms creates a problem for mobile users? A. Mechanisms based on IP addresses B. Mechanism with reusable passwords C. One-time password mechanism. D. Challenge response mechanism. Answer: A Explanation: Authentication mechanisms based on IP addresses are useful if a user has a fixed IP address. This could be a fixed IP address at work or even a fixed IP address at home. With authentication mechanisms based on IP addresses, a user can access a resource only from a defined IP address. However, authentication mechanisms based on IP addresses are a problem for mobile users. This is because mobile users will connect to different networks on their travels such as different WiFi networks or different mobile networks. This means that the public IP address that the mobile user will be connecting from will change frequently. QUESTION NO: 12 Organizations should consider which of the following first before allowing external access to their LANs via the Internet? A. Plan for implementing workstation locking mechanisms. B. Plan for protecting the modem pool. ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 8C. Plan for providing the user with his account usage information. D. Plan for considering proper authentication options. Answer: D Explanation: LANs are typically protected from the Internet by firewalls. However, to allow external access to a LAN, you need to open ports on the firewall to allow the connections. With the firewall allowing external connections into the LAN, your last line of defense is authentication. You need to ensure that the remote user connecting to the LAN is who they say they are. Therefore, before allowing external access into a LAN, you should plan and implement proper authentication. QUESTION NO: 13 Kerberos can prevent which one of the following attacks? A. Tunneling attack. B. Playback (replay) attack. C. Destructive attack. D. Process attack. Answer: B Explanation: In a Kerberos implementation that is configured to use an authenticator, the user sends to the server her identification information, a timestamp, as well as sequence number encrypted with the session key that they share. The server then decrypts this information and compares it with the identification data the KDC sent to it regarding this requesting user. The server will allow the user access if the data is the same. The timestamp is used to help fight against replay attacks. QUESTION NO: 14 ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 9In discretionary access environments, which of the following entities is authorized to grant information access to other people? A. Manager B. Group Leader C. Security Manager D. Data Owner Answer: D Explanation: Discretionary access control (DAC) enables data owners to dictate who has access to the files and resources owned by them. QUESTION NO: 15 What is the main concern with single sign-on? A. Maximum unauthorized access would be possible if a password is disclosed. B. The security administrator's workload would increase. C. The users' password would be too hard to remember. D. User access rights would be increased. Answer: A Explanation: A major concern with Single Sign-On (SSO) is that if a user's ID and password are compromised, the intruder would have access to all the systems that the user was authorized for. ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 10QUESTION NO: 16 Who developed one of the first mathematical models of a multilevel-security computer system? A. Diffie and Hellman. B. Clark and Wilson. C. Bell and LaPadula. D. Gasser and Lipner. Answer: C Explanation: The Bell-LaPadula model was the first mathematical model of a multilevel security policy used to define the concept of a secure state machine and modes of access, and outlined rules of access. QUESTION NO: 17 Which of the following attacks could capture network user passwords? A. Data diddling B. Sniffing C. IP Spoofing D. Smurfing Answer: B Explanation: Password sniffing sniffs network traffic with the hope of capturing passwords being sent between computers. ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 11QUESTION NO: 18 Which of the following would constitute the best example of a password to use for access to a system by a network administrator? A. holiday B. Christmas12 C. Jenny D. GyN19Za! Answer: D Explanation: A generally accepted minimum standard for password complexity is a minimum of eight characters, one uppercase alpha character, one lowercase alpha character, one number character, and one symbol character. Therefore, “GyN19Za!” is the best example. QUESTION NO: 19 What physical characteristic does a retinal scan biometric device measure? A. The amount of light reaching the retina B. The amount of light reflected by the retina C. The pattern of light receptors at the back of the eye D. The pattern of blood vessels at the back of the eye Answer: D Explanation: A Retina Scan is a biometric system that scans the blood-vessel pattern of the retina on the backside of the eyeball. ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 12QUESTION NO: 20 The Computer Security Policy Model the Orange Book is based on is which of the following? A. Bell-LaPadula B. Data Encryption Standard C. Kerberos D. Tempest Answer: A Explanation: The Orange Book used the Bell-LaPadula Computer Security Policy model as a comparative evaluation for all systems. QUESTION NO: 21 The end result of implementing the principle of least privilege means which of the following? A. Users would get access to only the info for which they have a need to know B. Users can access all systems. C. Users get new privileges added when they change positions. D. Authorization creep. Answer: A Explanation: Least privilege means an individual should have just enough permissions and rights to fulfill his ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 13role in the company and no more. QUESTION NO: 22 Which of the following is the most reliable authentication method for remote access? A. Variable callback system B. Synchronous token C. Fixed callback system D. Combination of callback and caller ID Answer: B Explanation: A Synchronous token generates a one-time password that is only valid for a short period of time. Once the password is used it is no longer valid, and it expires if not entered in the acceptable time frame. QUESTION NO: 23 Which of the following is true of two-factor authentication? A. It uses the RSA public-key signature based on integers with large prime factors. B. It requires two measurements of hand geometry. C. It does not use single sign-on technology. D. It relies on two independent proofs of identity. Answer: D ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 14Explanation: There are three general factors that are used for authentication: Something a person knows. Something a person has. Something a person is. Two-factor authentication requires two of the three factors to be part of authentication process. QUESTION NO: 24 The primary service provided by Kerberos is which of the following? A. non-repudiation B. confidentiality C. authentication D. authorization Answer: C Explanation: Kerberos is a third-party authentication service that can be used to support SSO. QUESTION NO: 25 There are parallels between the trust models in Kerberos and Public Key Infrastructure (PKI). When we compare them side by side, Kerberos tickets correspond most closely to which of the following? A. public keys ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 15B. private keys C. public-key certificates D. private-key certificates Answer: C Explanation: Public Key describes a system that uses certificates or the underlying public key cryptography on which the system is based. In the traditional public key model, clients are issued credentials or "certificates" by a Certificate Authority (CA). The CA is a trusted third party. Public key certificates contain the user's name, the expiration date of the certificate etc. The most common certificate format is X.509. Public key credentials in the form of certificates and public-private key pairs can provide a strong distributed authentication system. The Kerberos and public key trust models are very similar. A Kerberos ticket is analogous to a public key certificate (a Kerberos ticket is supplied to provide access to resources). However, Kerberos tickets usually have lifetimes measured in days or hours rather than months or years. QUESTION NO: 26 Which of the following security control is intended to avoid an incident from occurring? A. Deterrent B. Preventive C. Corrective D. Recovery Answer: B Explanation: Preventive controls stop actions from taking place. It applies restrictions to what a possible user ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 16can do, whether the user is authorized or unauthorized. QUESTION NO: 27 Which of the following was developed to address some of the weaknesses in Kerberos and uses public key cryptography for the distribution of secret keys and provides additional access control support? A. SESAME B. RADIUS C. KryptoKnight D. TACACS+ Answer: A Explanation: Secure European System for Applications in a Multi-vendor Environment (SESAME) was developed to address some of the weaknesses in Kerberos and uses public key cryptography for the distribution of secret keys and provides additional access control support. QUESTION NO: 28 Single Sign-on (SSO) is characterized by which of the following advantages? A. Convenience B. Convenience and centralized administration C. Convenience and centralized data administration D. Convenience and centralized network administration ISC CISSP Exam "Pass Any Exam. Any Time." - www.actualtests.com 17Answer: B Explanation: Single sign-on allows users to type their passwords only once when they first log in to access all the network resources. This makes SSO convenient. Single Sign-on allows a single administrator to add and delete accounts across the entire network from one user interface, providing centralized administration. QUESTION NO: 29 What is the primary role of smartcards in a PKI? A. Transparent renewal of user keys B. Easy distribution of the certificates between the users C. Fast hardware encryption of the raw data D. Tamper resistant, mobile storage and application of private keys of the users Answer: D Explanation: A smart card, which includes the ability to process data stored on it, is also able to deliver a twofactor authentication method as the user may have to enter a PIN to unlock the smart card. The authentication can be completed by using an OTP, by utilizing a challenge/response value, or by presenting the user’s private key if it is used within a PKI environment. The fact that the memory of a smart card is not readable until the correct PIN is entered, as well as the complexity of the smart token makes these cards resistant to reverse-engineering and tampering methods. QUESTION NO: 30 What kind of certificate is used to validate a user identity? [Show More]
Last updated: 2 years ago
Preview 1 out of 873 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 14, 2021
Number of pages
873
Written in
Additional information
This document has been written for:
Uploaded
Aug 14, 2021
Downloads
0
Views
79



.png)
.png)
.png)
.png)


.png)