Computer Science > EXAM > The Bits and Bytes of Computer Networking: Troubleshooting and the Future of Networking WK 6 (All)
The Bits and Bytes of Computer Networking: Troubleshooting and the Future of Networking WK 6
Document Content and Description Below
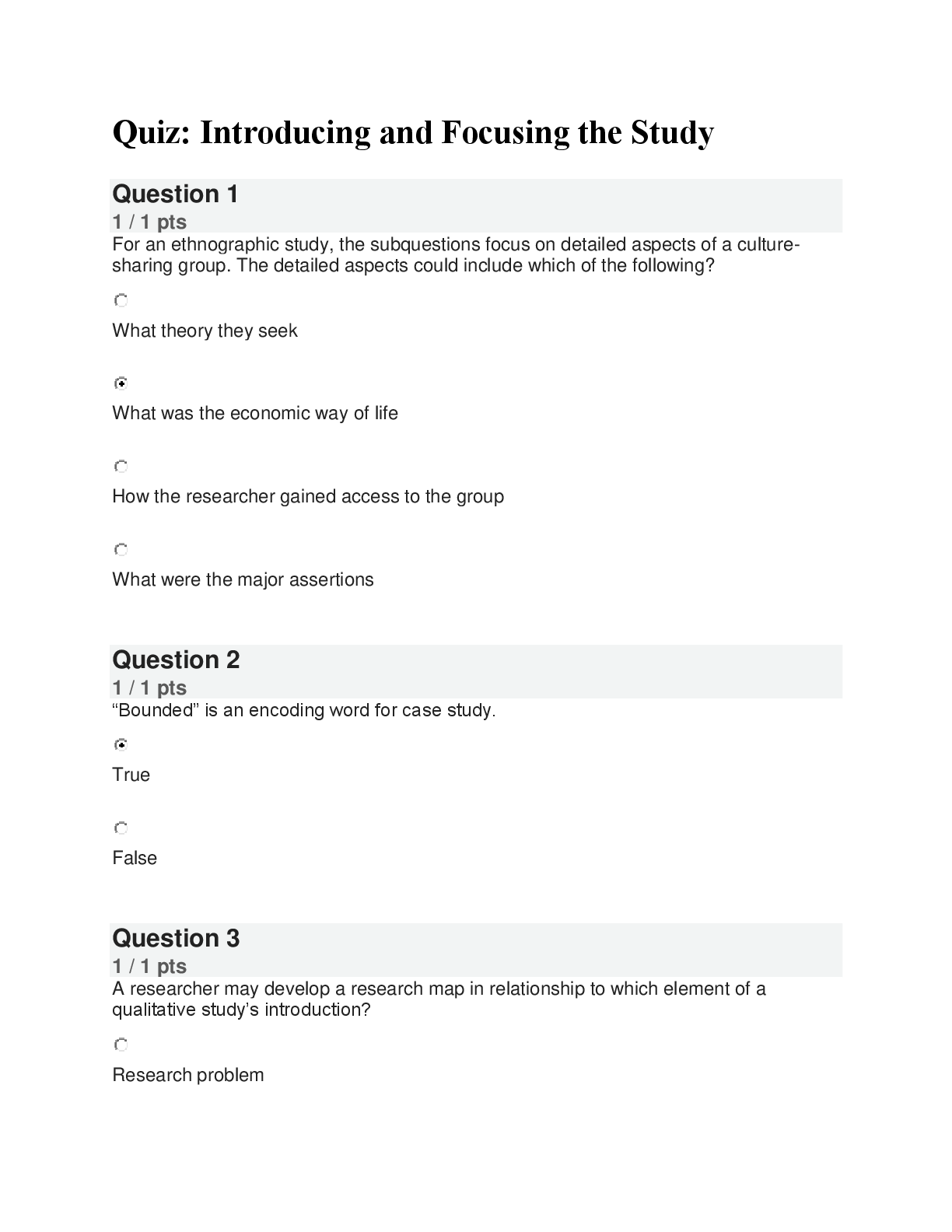
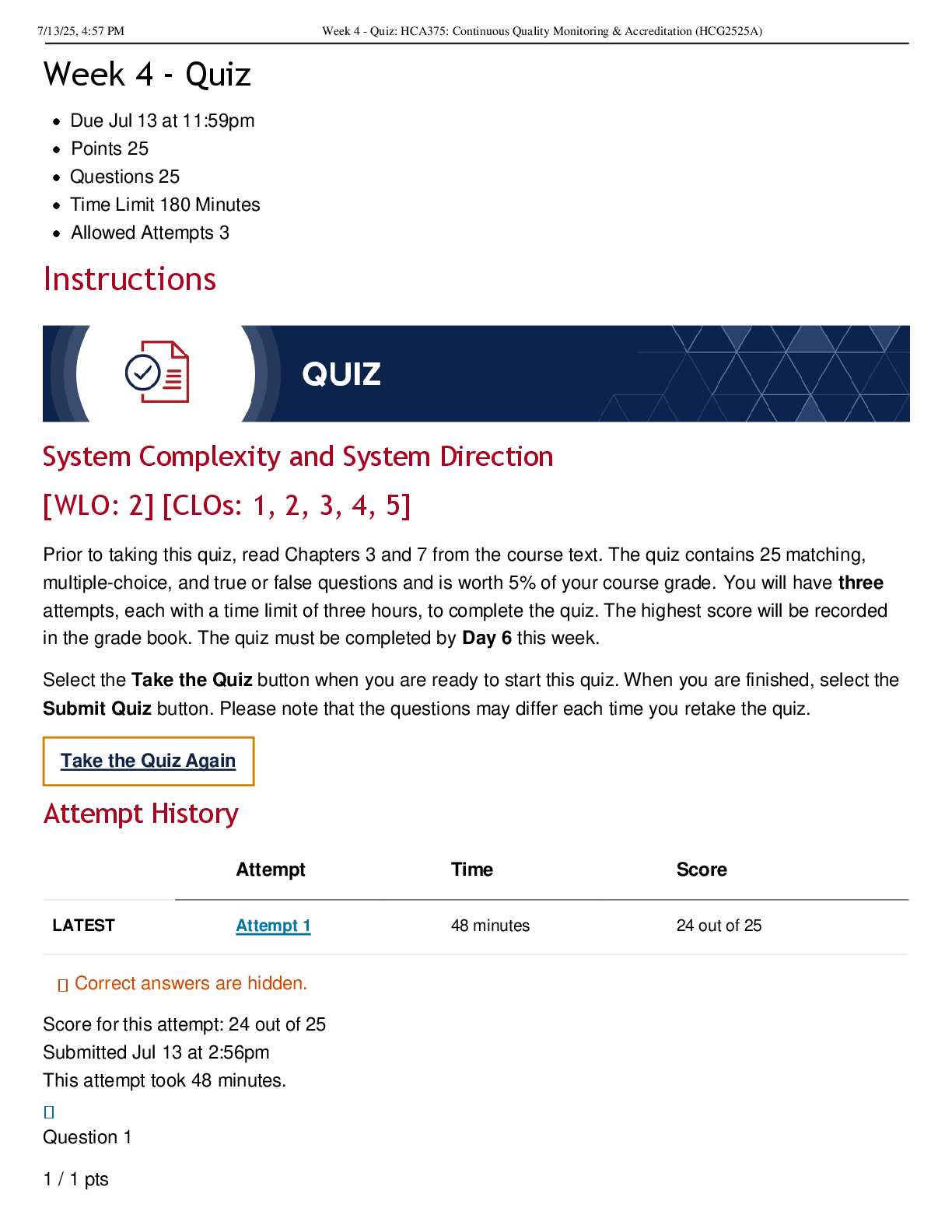
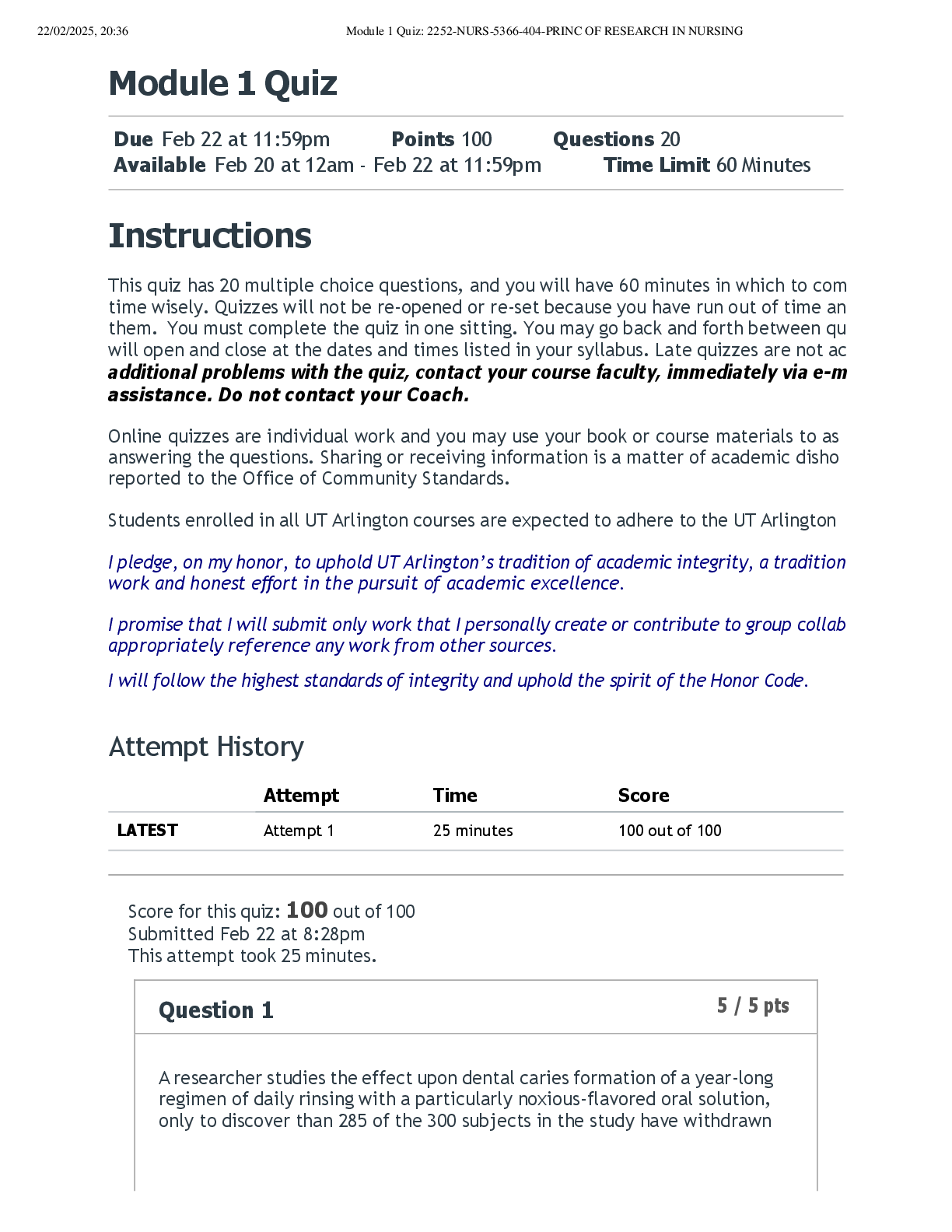
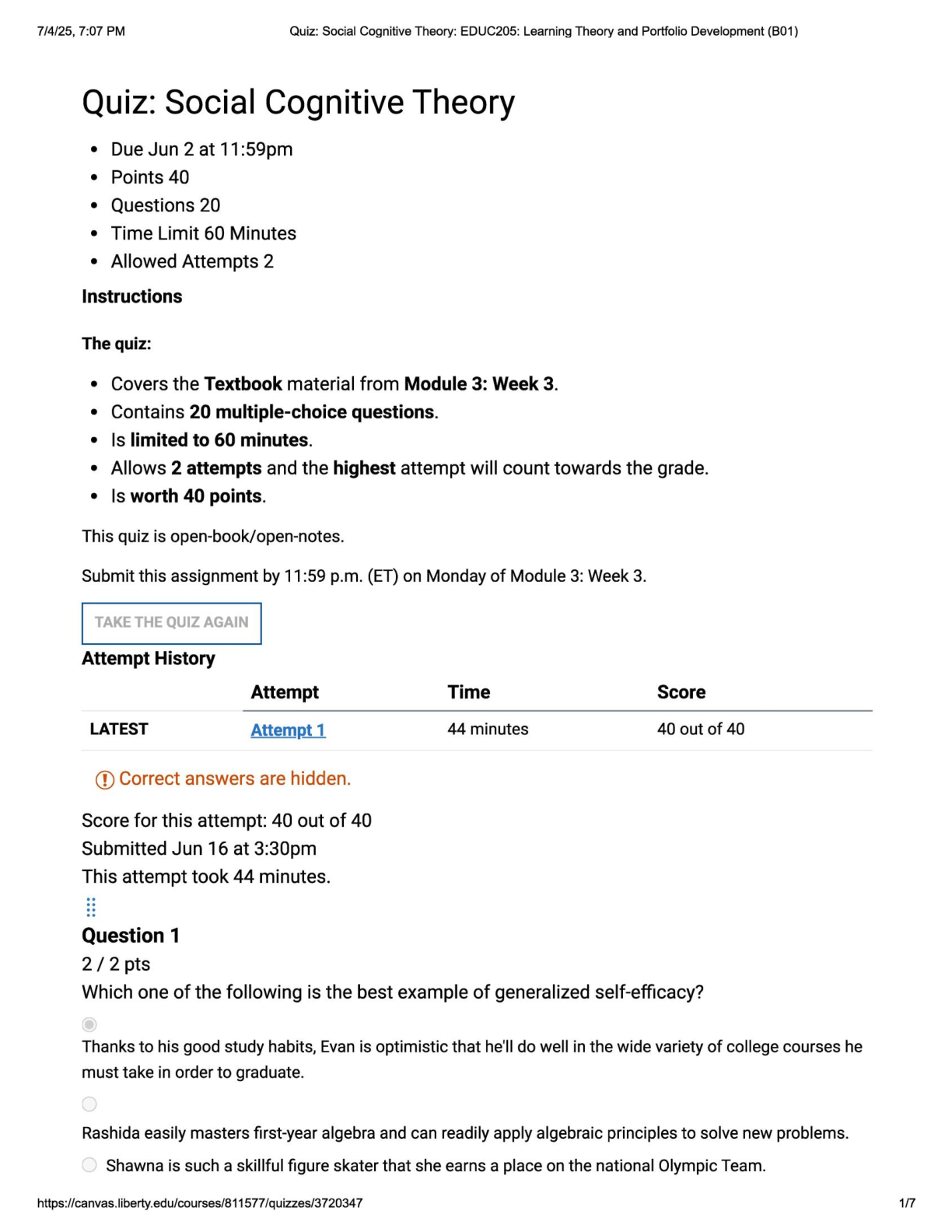
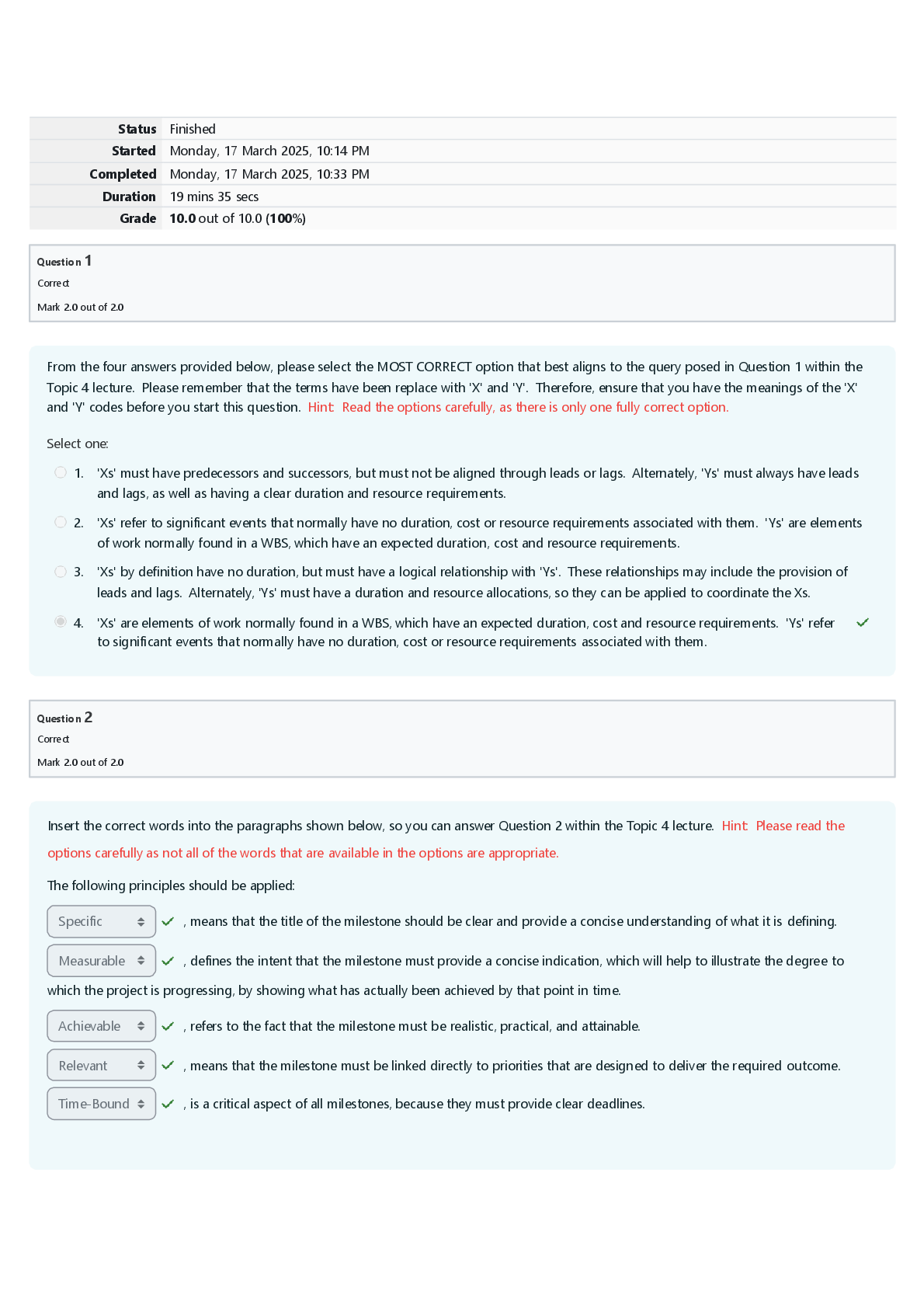
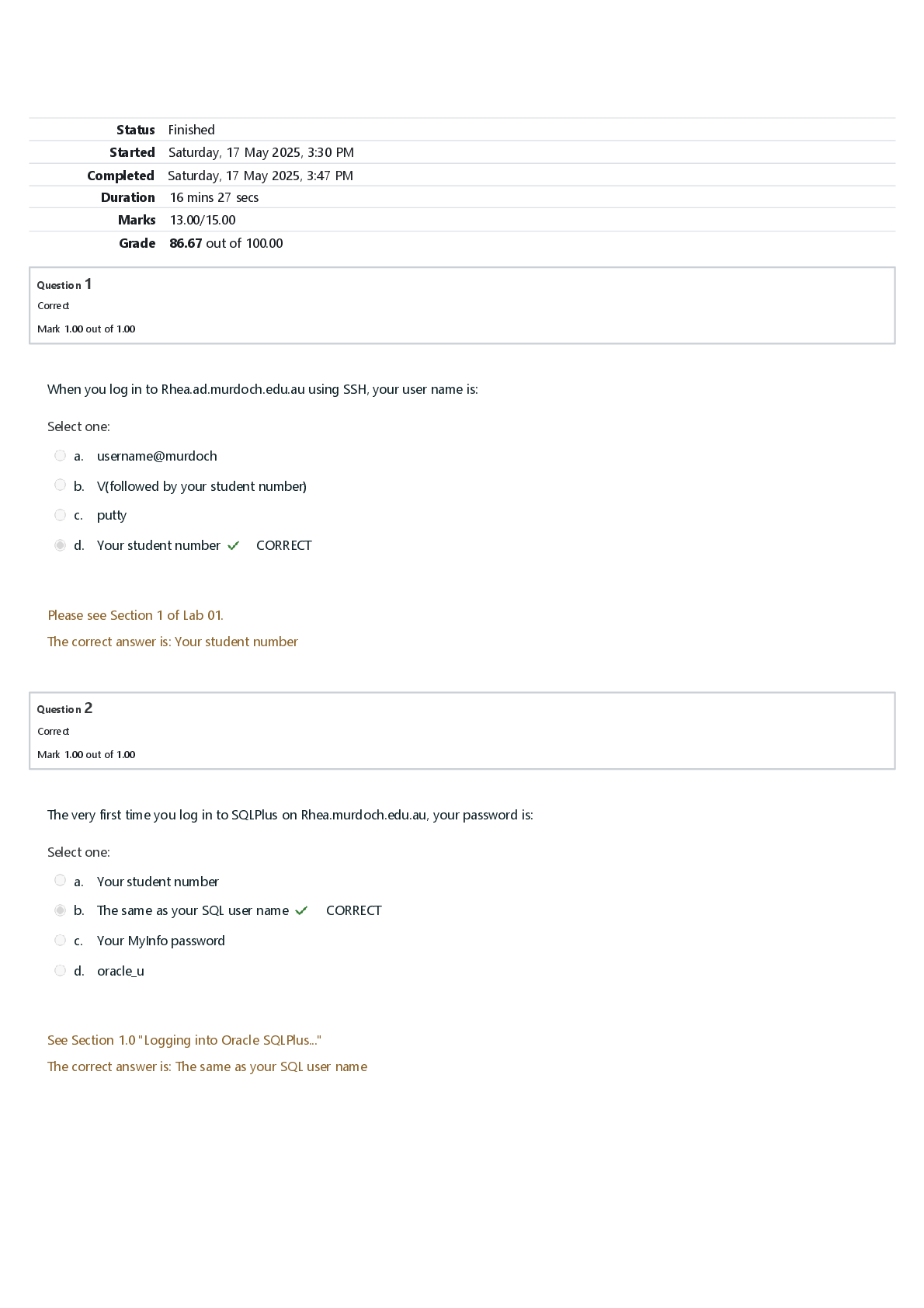
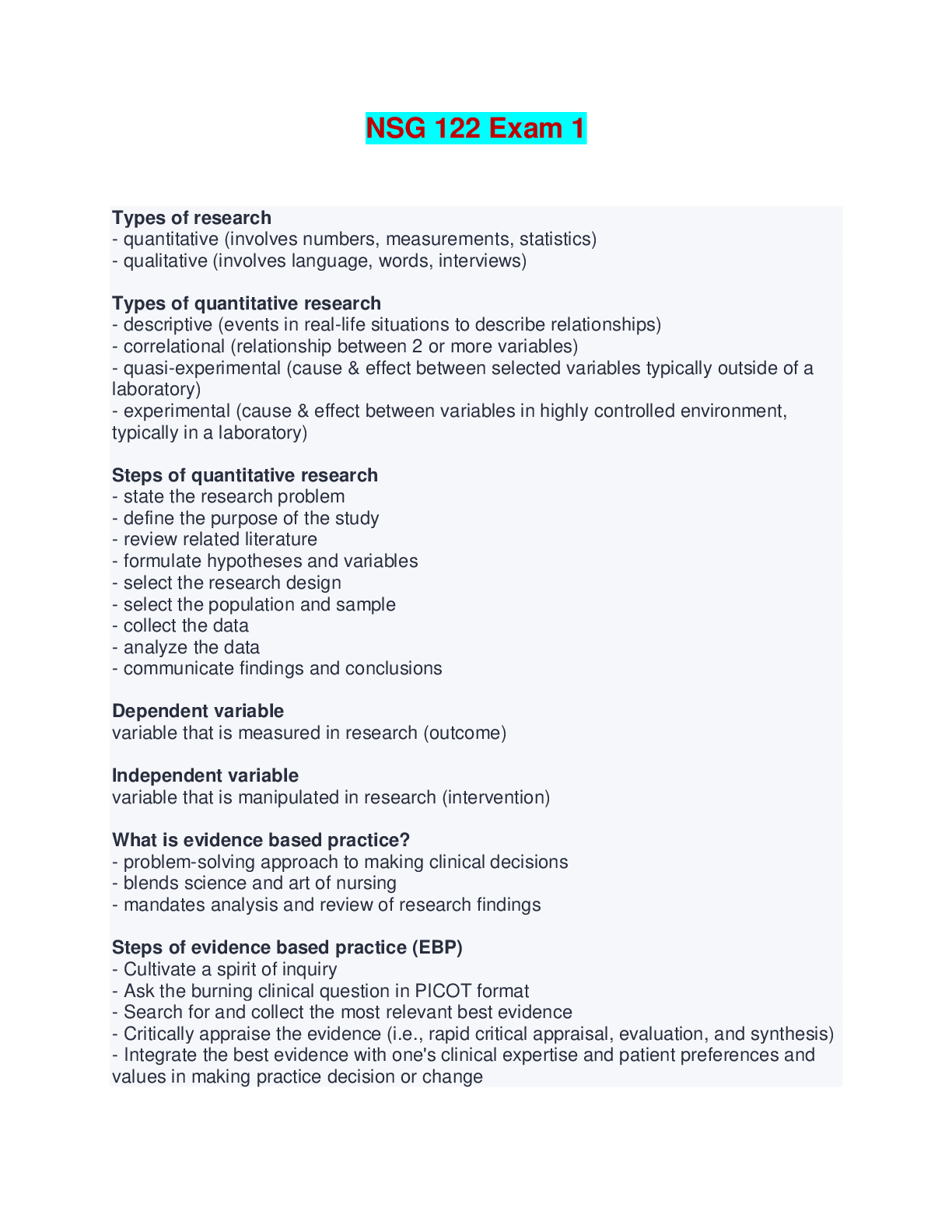
The Bits and Bytes of Computer Networking: Troubleshooting and the Future of Networking WK 6 The protocol used to communicate network errors is known as __________. ICMP, ICMP is used to communicate ... errors back to the client. The ping utility sends what message type? echo request; By default, the ping utility sends an Echo Request ICMP message type. On Windows, one of the tools you can use to verify connectivity to a specific port is ________. Test-NetConnection ; Test-NetConnection lets you test many things, including connectivity to a specific port on a remote host. One of Level 3's public DNS servers is ____________. 4.2.2.3; Level 3's public DNS servers are 4.2.2.1 through 4.2.2.6 A DNS resolver tool available on all major desktop operating systems is __________. nslookup; nslookup is available by default on Windows, macOS, and Linux. The organization responsible for DNS at a global level is ________. ICANN; ICANN is responsible for DNS at a global level. A piece of software that runs and manages virtual machines is known as a __________. hypervisor; A hypervisor manages many virtual instances running on a single host. Office 365 Outlook is an example of _______. SaaS; Office 365 Outlook is an example of Software as a Service (SaaS). A hybrid cloud is ________________. a combination of a public cloud and a private cloud; A hybrid cloud runs some services on a cloud provider and some services in-house. An IPv6 address is how many bits long? 128; An IPv6 address is 128 bits long The very first field in an IPv6 header is the _______. version field; This field is used to indicate what version of IP is being used. The IPv6 header field that indicates how many routers can forward a packet before it's discarded is called the ________. hop limit field ; The hop limit field configures how many routers can try to forward a packet before it's discarded. [Show More]
Last updated: 2 years ago
Preview 1 out of 3 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)

THE BITS AND BYTES OF COMPUTER NETWORKING: WEEK 1 - WEEK 6 EXAMS BUNDLE
THE BITS AND BYTES OF COMPUTER NETWORKING: WEEK 1 - WEEK 6 EXAMS BUNDLE
By Ajay25 2 years ago
$20
6
Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Nov 23, 2022
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Nov 23, 2022
Downloads
0
Views
105