Computer Networking > EXAM REVIEW > Final Exam Review - Sheridan College INFO 24178 (All)
Final Exam Review - Sheridan College INFO 24178
Document Content and Description Below
Exam Review INFO24178 Chapter 9: Client Security: o Securing the client involves, securing the operating syste, o Using hardware system security o Protecting peripheral devices connected to t... he client Hardware Security: o Securing booting tools o A hardware root of trust o Preventing electromagnetic spying Secure Booting: o BIOS (Basic Input/Output System) o Firmware used on early computers to hold the boot process o Ability to update the BIOS with a firmware update opened the door for threat actors to create malware to infect BIOS o To combat attacks, UEFI (Unified Extensible Firmware Interface) was developed to replace BIOS o In conjunction with UEFI Secure Boot security standard was also created o When using UEFI and Secure Boot, a computer checks the digital signature of each piece of boot software o If signatures are deemed valid the computer starts otherwise it does not boot up Hardware Root of Trust o Chain of trust o Each element of the boost process relies on the confirmation of the previous element to know that the entire process is secure o Hardware root of trust o Strongest point is hardware, which cannot be modified o Security checks are rooted in hardware checks Electromagnetic Spying o US gov has developed a classified standard intended to prevent attackers from picking up electromagnetics fields from government buildings o Known as TEMPEST (Telecommunications Electronics Material Protected from Emanating Spurious Transmissions) Supply Chain Infections o A network that moves products from the supplier to the customer o All of the different steps opened the door for malware to be injected into products during manufacture or storage o If planted in the firmware ROM of a device, it can be difficult or impossible to clean an infected device of malware o Users may receive infected devices at the point of purchase unaware o Cannot be easily prevented OS Security Config o Should include, disabling unn [Show More]
Last updated: 2 years ago
Preview 1 out of 3 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$5.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Dec 14, 2022
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Dec 14, 2022
Downloads
0
Views
64


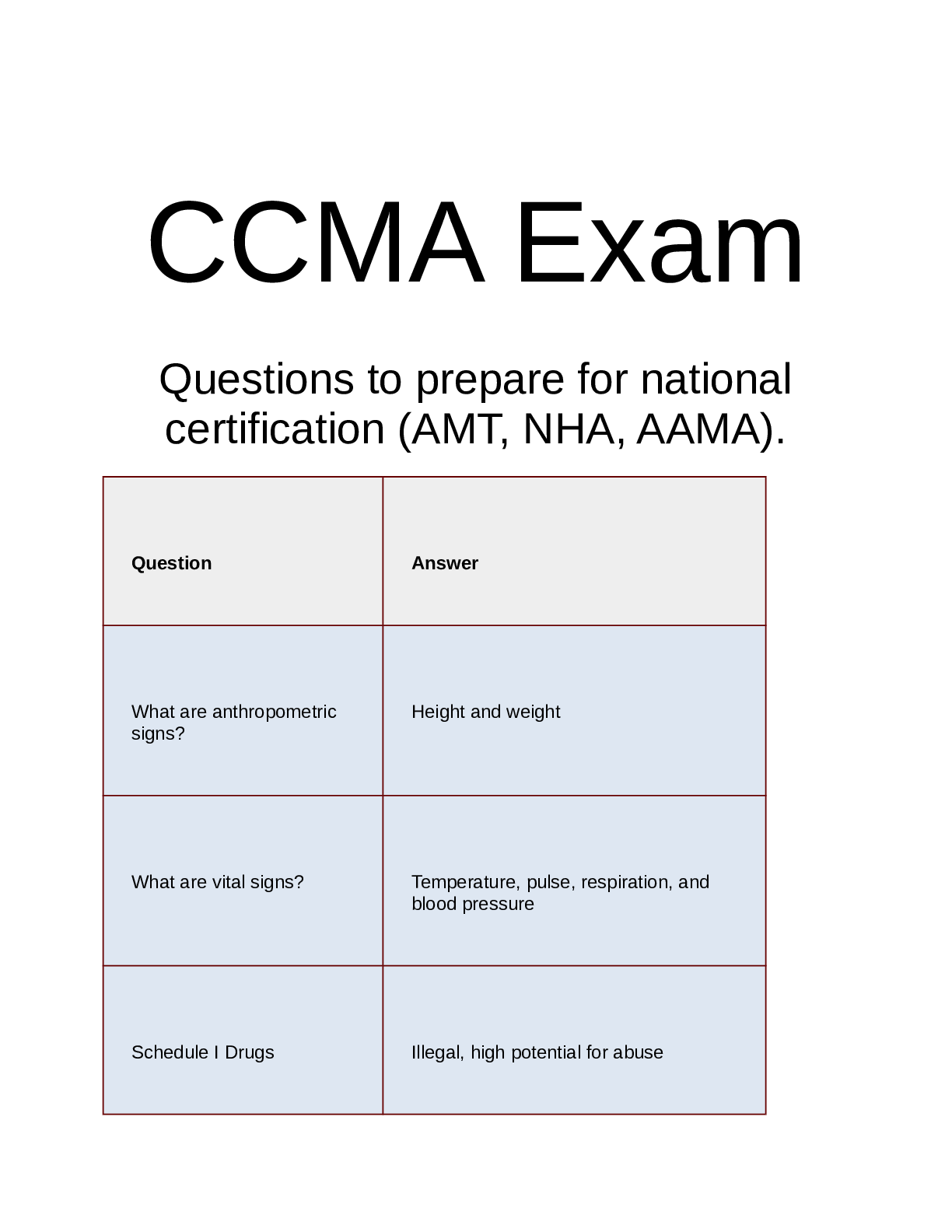






.png)



