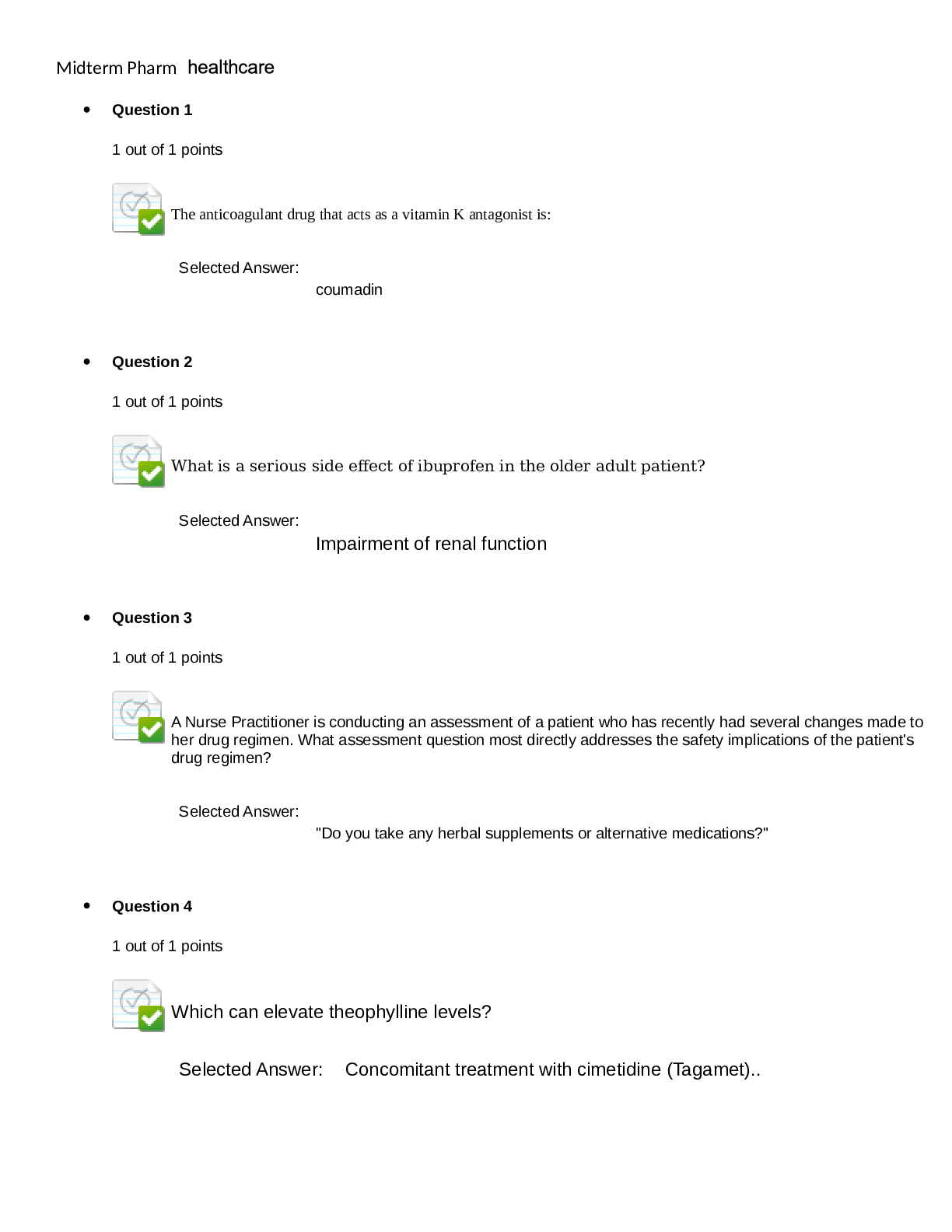
Telecommunication and Information Technology > EXAM > C724-M9-SYSTEMS ANALYSIS DESIGN AND IMPLEMENTATION Quiz (All)
C724-M9-SYSTEMS ANALYSIS DESIGN AND IMPLEMENTATION Quiz
Document Content and Description Below
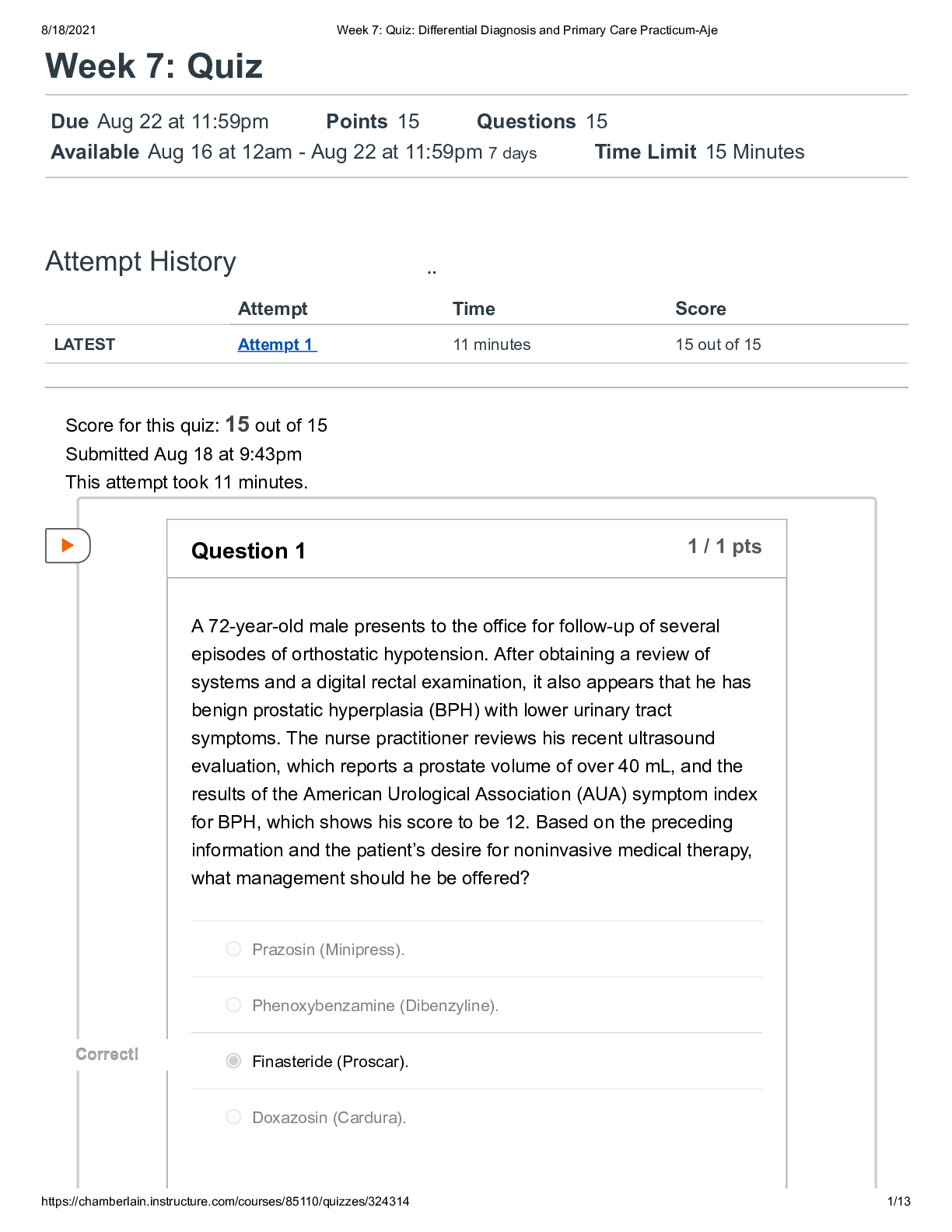
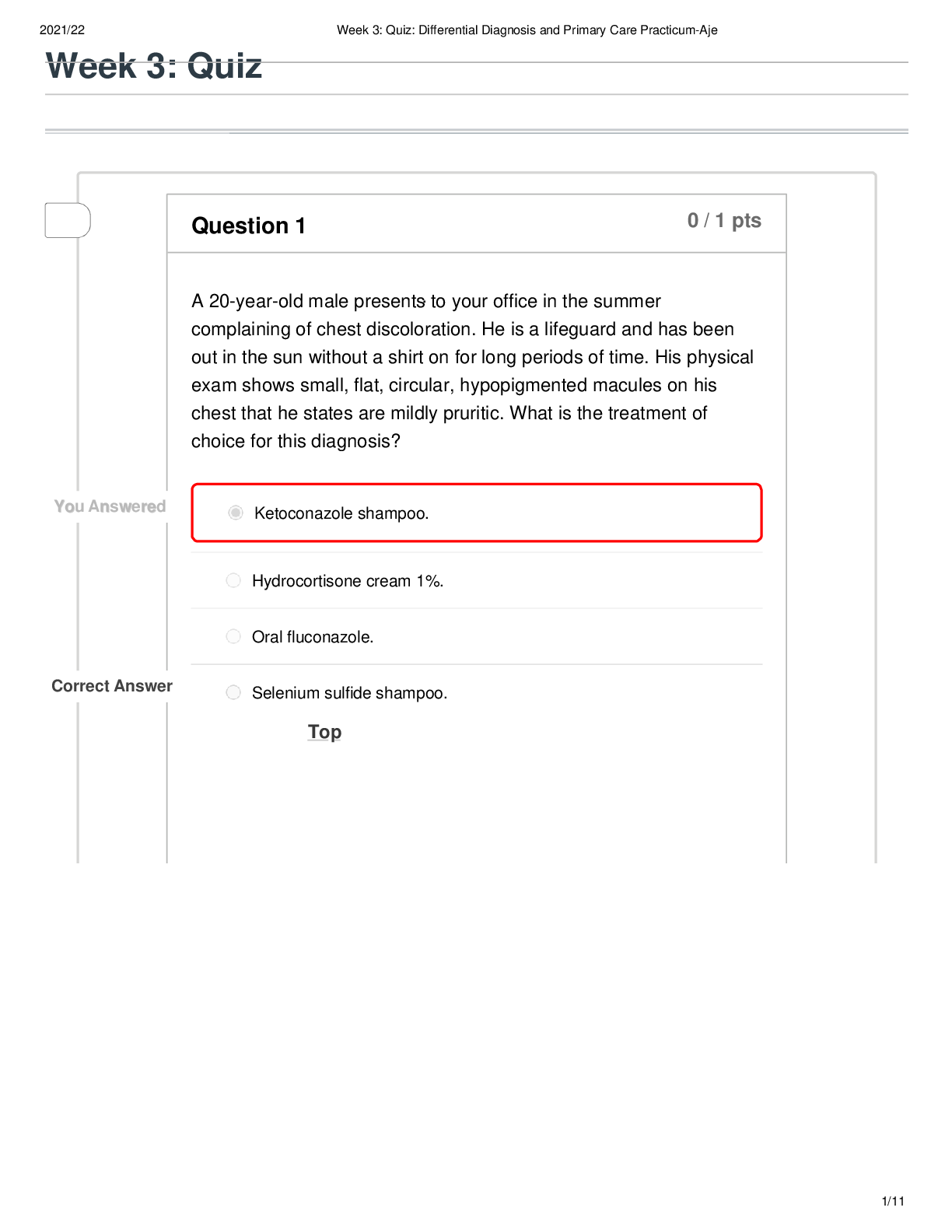
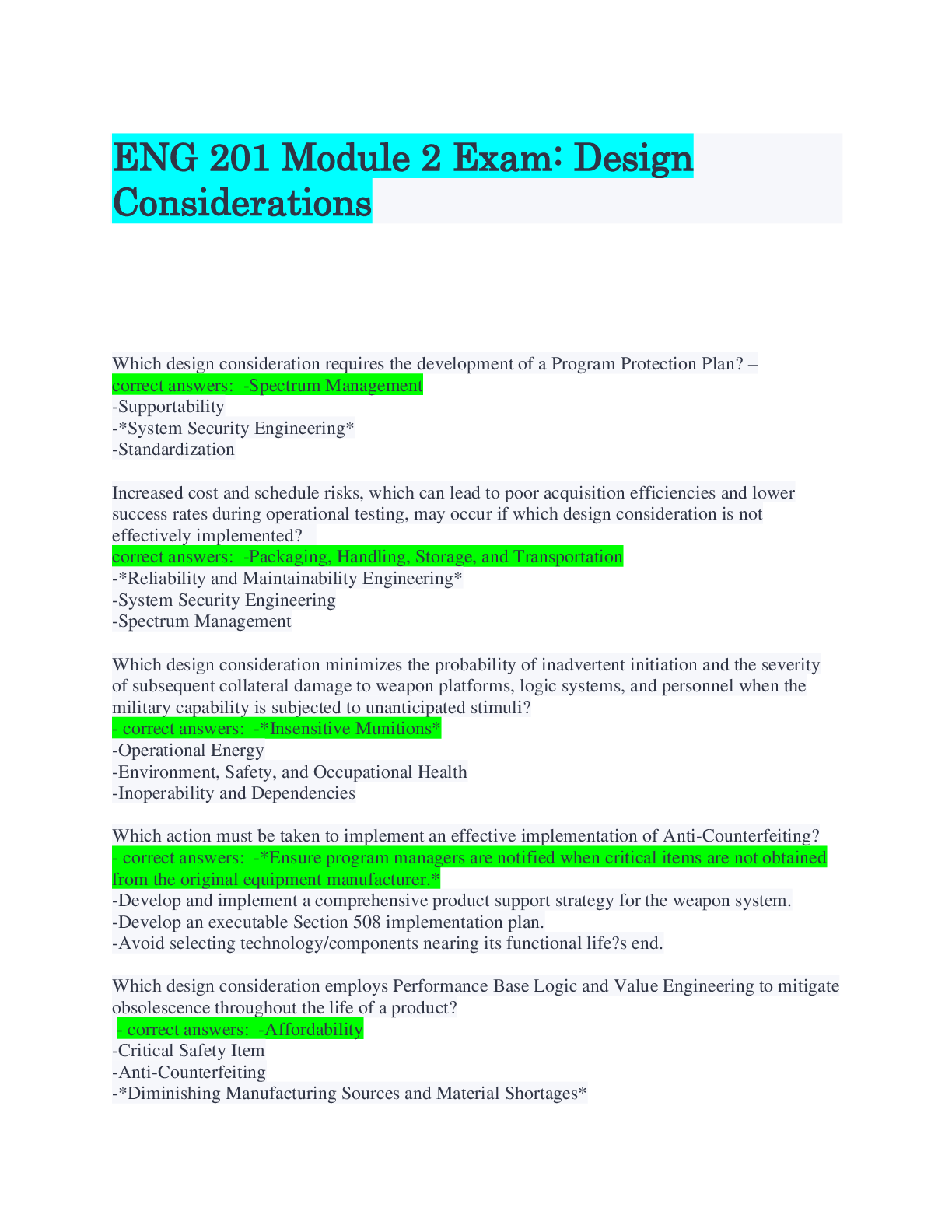
C724-M9-SYSTEMS ANALYSIS DESIGN AND IMPLEMENTATION QuizC724-M9-SYSTEMS ANALYSIS, DESIGN, AND IMPLEMENTATION Step 1 of 1 Question 1 of 20 Which of the following is NOT part of the systems analysis p... rocess? Information requirements Feasibility study Root causes Defining the problem Correct. Identifying the causes to the problem is part of systems analysis. Question 2 of 20 Which of the following is NOT a method for gathering user requirements? Interview users Analyze existing system Monitor users Correct. Monitoring users is not a method for gathering user requirements. Rather, this can be achieved with hands-on interviewing and by discussing the processes. Question 3 of 20 For what purpose is scrum software development methodology designed? Scrum is designed for a sequential, step-by-step approach. Scrum is designed to address customer need changes. Scrum is designed for quick development. Correct. Quick development is a prototyping methodology. Question 4 of 20 "Fill in the blank" question: select the correct answer. The waterfall model for software development is ideal when systems requirements are clear and unlikely to change. clear and unlikely to change Correct. The waterfall model is best used when requirements are clear and unlikely to change. Question 5 of 20 [True/False] A legal feasibility study is appropriate when dealing with government agencies in which information and data might be sensitive. True False Correct. A legal analysis of the impact of a new system is desired when dealing with regulated industries. Question 6 of 20 Which of the following best defines a work breakdown structure (WBS)? List of project tasks that define the critical path List of broken down project deliverables List of resources and tasks in a project Correct. WBS can help define the critical path. Question 7 of 20 Unified modeling language (UML) is a general-purpose modeling language designed to provide what? A standard method to represent the design of a system A method to represent the design of a system without visualization A standard method to represent the input of a system Correct. UML is a language that helps visualize systems through diagrams. Question 8 of 20 Which of the following is NOT a process description tool? Decision tree Modular design Critical path Correct. Critical path methodology is not a process description tool. Question 9 of 20 An advantage to prototyping is that the user gets to do what? “Test drive” the system before it is implemented Analyze the system on paper before continuing with development Test the system after it is implemented for errors Correct. Prototyping during implementation allows the user to test drive the system. Question 10 of 20 What are the basic activities of information management? Data storage, data processing, and data mining Input, processing, and output User query, processing, and storage Correct. Input, processing, and output are the key information management activities. Question 11 of 20 Which of the following occurs during the acquisition phase? Technical staff is hired. Software and hardware are procured. Software development is outsourced. Correct. During the acquisition phase, the software and the hardware of the designed system is acquired. Question 12 of 20 "Fill in the blank" question: select the correct answer. It is important for management to periodically evaluate information systems in order to determine whether the system is effective and relevant to the organization. There are three types of system evaluation: system-oriented, function-oriented, and strategy-oriented. Correct. The focus of strategic-oriented evaluation is the determination of whether the information system outputs enable management to make strategic decisions that will help develop and achieve the future mission and vision of the organization. strategy-oriented Question 13 of 20 What is one of the benefits of adequate budgeting for user support? Less need for training Less reliant on outside consultants Less difficulty with GUI acceptance Correct. GUI acceptance is part of training. Question 14 of 20 System quality problems can include which of the following? Hardware bugs and errors Software or facility failures Poor data input quality All of the above Correct. System quality problems include software defects, hardware failures, and poor data input quality. Question 15 of 20 What role should a change agent play when implementing a new information system? A change agent sees errors and defects, and embarks on transformation. A change agent identifies positive improvements and helps train and motivate users. A change agent redesigns user interfaces and adds complexity to systems. Correct. A systems analyst can play the role of a change agent, helping improve operations through systems and getting users to adopt the new environment. Question 16 of 20 The systems analyst is required to do which job? Prepare documentation for others to create reports and share with the teams Prepare and explain written reports and keep stakeholders updated Prepare reports and let others disseminate updates and information Correct. Systems analysts have to keep stakeholders up to date with reporting. Question 17 of 20 Which of the following best describes oral communication? Oral communication is the transfer of information via verbal and visual content. Oral communication is conducted via reports. Oral communication involves using body language. Correct. Oral communication is verbal and can include the use of visual aids. Question 18 of 20 [True/False] Process-centered environments are the least resourceful category due to the lack of capability of specifying analysis and design, as well as the formal software control process. True False Correct. Process-centered environments are the most resourceful category. Question 19 of 20 Newsletters are often Internet-published bulletins that are distributed to users and typically cover what? Monthly updates or information for business partners One general or specific topic of interest Several areas of interest or areas in a company Correct. Internet-based newsletters cover a specific issue. Question 20 of 20 "Fill in the blank" question: select the correct answer. Both cloud computing and Web 2.0 are disrupting systems design and implementation. Correct. Cloud computing and Web 2.0 are disrupting systems design and implementation. Attempt 2 Question 1 of 20 What is the most critical step in systems analysis? disrupting systems design and implementation Conducting the feasibility study Identifying information requirements Identifying root causes Correct. Most cost overruns and failures of systems design are a result of the inadequate definition of information requirements. Question 2 of 20 "Fill in the blank" question: select the correct answer. The objective of SDLC is to deliver a high quality system, provide management control, and maximize productivity. Correct. The System Development Life Cycle helps deliver a quality, effective system under management control, providing maximum project productivity. Question 3 of 20 RAD is a method in which products can be developed faster and with higher quality through prototyping and early testing. What does RAD stand for? Ready application development Radical application development Rapid application development Correct. RAD stands for rapid application development, and is a software development methodology. Question 4 of 20 "Fill in the blank" question: select the correct answer. Waterfall derivative models in the SDLC methodology include fountain, spiral, and build and fix. Correct. Build and fix is a derivative of the waterfall model using sequential methodology . Question 5 of 20 "Fill in the blank" question: select the correct answer. Fill in the blank TCO is an economic feasibility method. Correct. Total cost of ownership is an economic feasibility analysis method. Question 6 of 20 productivity build and fix TCO What is the most important aspect of the critical path method (CPM) in project management? CPM outlines the work breakdown structure. CPM identifies the risks in a project. CPM defines the critical and noncritical tasks. Correct. CPM identifies the critical and noncritical tasks, which helps avoid delays or schedule changes. Question 7 of 20 "Fill in the blank" question: select the correct answer. The first step when building a system model is to collect information about the proposed system. Correct. Information includes input, output, and processes. Question 8 of 20 Which of the following describes how the modular design process description tool works? Modular design uses diagrams and arrow nodes to represent a system. Modular design uses graphical representation of rules and conditions. Modular design uses building blocks to represent a system. Correct. Modular design uses a combination of sequence, selection, and looping as building blocks to represent a system. Question 9 of 20 "Fill in the blank" question: select the correct answer. Fill in the blank Scope creep is usually the result of a lack of proper documentation, definition, or control over the project requirements and can sneak up and destroy a project. Correct. A project can undergo scope creep if it is not well defined. Question 10 of 20 Which of the following is a weakness of manual keying for data capture? Overload information Scope creep Slowness Human error Correct. Human error is a key weakness in manual keying. Question 11 of 20 Which of the following is a definition of a software patch? A patch is a software bug. A patch is a debugging process. A patch is a code that fixes a software defect. Correct. A patch is the terminology for a code that fixes a defect. Question 12 of 20 "Fill in the blank" question: select the correct answer. Fill in the blank Evaluation is defined as the process of gathering and analyzing information in order to compare performance with predetermined objectives, and to determine whether or not the objectives were achieved. Correct. System performance must always be evaluated. Question 13 of 20 How many methods are there to increase user adoption and lower the cost of a system, post implementation? Eight Five Six Correct. There are six methods, including benchmarking, usability testing, user communication, internal user groups, planning, and leveraging existing resources. Question 14 of 20 "Fill in the blank" question: select the correct answer. Fill in the blank Qualitative risk analysis involves performing an analysis of the risks and conditions in order to prioritize the effects on a project. Correct. Qualitative risk analysis involves looking at conditions that can affect the project. Evaluation Qualitative Question 15 of 20 Why are good communication skills necessary for systems analysts? Systems analysts interact with internal and external resources. Systems analysts must get approval from the executive team. Systems analysts must train and help users adopt the new system. Correct. Systems analysts must have strong communication skills because they work heavily with external and internal resources and participate in and document analysis, design, and implementation of systems. Question 16 of 20 "Fill in the blank" question: select the correct answer. Fill in the blank Visual aids are helpful in maintaining audience interest, as well as helping the presenter follow and control the presentation. Correct. Visual aids, like Powerpoint presentations, assist with the presentation. Question 17 of 20 What is the downside of oral communication outside formal presentations? There is no downside; oral communication is necessary at all times. Oral communication is not documented and, therefore, subject to misinterpretation. The downside is that oral communication relies on body language. Correct. Oral communication can be forgotten or misunderstood. Question 18 of 20 Upper CASE tools are important to analysts in the project planning phase. What is meant by Upper CASE tools? Upper CASE tools support design and testing. Upper CASE tools support coding and debugging. Upper CASE tools support software modeling and analysis. Correct. There are Upper CASE tools that support software modeling and analysis. Question 19 of 20 "Fill in the blank" question: select the correct answer. Visual The proper techniques for developing an internet search strategy include reviewing information requirements, using proper search techniques and tools, evaluating the results, and determining copyright and data integrity issues. Correct. Information obtained on the Internet could be protected by copyright or contain inaccurate data. Question 20 of 20 "Fill in the blank" question: select the correct answer. Cloud computing and Web 2.0 are enabling new Internet utilization business models. Correct. Cloud computing and Web 2.0 are enabling new Internet utilization business models. Attempt 3 Question 1 of 20 What does SDLC stand for? Software Design Life Cycle Systems Development Life Cycle Structured Design Life Cycle Correct. SDLC stands for Systems Development Life Cycle. Question 2 of 20 [True/False] The user requirements analysis determines inputs, outputs, process steps, and data storage needs. True False Correct. User requirements analysis determines inputs, outputs, process steps, and data storage needs. Question 3 of 20 Which of the following best describes the RAD methodology? RAD is focused on planning and process definition. RAD is a sequential, deterministic, and consistent software development method. copyright and data integrity issues Web 2.0 RAD focuses on software development with limited emphasis on planning. Correct. RAD methodology allows for frequent prototypes in lieu of pre-determined specifications. Question 4 of 20 How many stages are in the waterfall methodology? Four Five Six Correct. There are six stages in the waterfall methodology. Question 5 of 20 "Fill in the blank" question: select the correct answer. The objective of a political feasibility study is to determine if stakeholders will support the development program and not sabotage or disrupt it. Correct. Organizational and political consequences must be evaluated when implementing a new information system. Question 6 of 20 What is the name of a chart representing tasks using an activity-on-arrow diagram? Work breakdown structure (WBS) Gantt chart PERT chart Correct. Earlier CPM developers utilized activity-on-arrow diagrams to outline the critical paths of projects. Question 7 of 20 "Fill in the blank" question: select the correct answer. The process of creating a model is iterative with the desired outcome of a validated model. Correct. Creating a system model requires review and several iterations. Question 8 of 20 Which of the following best describes structured English as a process description tool? It depends only on data terminology. political iterative It is similar to modular design with data terminology. It represents all combinations in a logical structure. Correct. The structured English process description uses the modular design concept along with data terminology. Question 9 of 20 "Fill in the blank" question: select the correct answer. The scope of a project defines the elements of cost, time, quality, and risk. Correct. The scope of a project defines cost, time, quality, and risk. Question 10 of 20 What is information system output? Output is the process of reporting tools for managers. Output is the transferring of data to a data warehouse. Output is the act of transferring processed data to users. Correct. Output can have many formats and is the transfer or display of processed information to appropriate users. Question 11 of 20 [True/False] Software defects, also called patches, can affect system reliability and security. True False Correct. Software defects are not patches. Question 12 of 20 "Fill in the blank" question: select the correct answer. The focus of strategic-oriented evaluation is the determination of whether the information system outputs enable management to execute the plan and mission of the organization. Correct. Strategic evaluations try to determine if the system will help the mission. Question 13 of 20 "Fill in the blank" question: select the correct answer. risk mission Benchmarking requires contacting users and teams that have successfully implemented a similar system in order to gather best practices. Correct. Benchmarking is learning and targeting best practices. Question 14 of 20 What are the components of system-level security? System-level security consists of user, policy, and firewall levels. System-level security consists of the architecture, policy, and process levels. System-level security consists of user, process, and design levels. Correct. System security must be designed at layers and must also be supported by processes and policies. Question 15 of 20 [True/False] When a systems analyst acts as a consultant, he or she interacts with the users to understand their needs and requirements. True False Correct. In systems analysis, user requirements must be documented. Question 16 of 20 "Fill in the blank" question: select the correct answer. Effective written communication is also important in emails. Although less formal than written documents and manuals, with email communication, attention should be given to all of the following, except technical jargon. Correct. Any written communication about the project should limit the use of technical jargon. Question 17 of 20 What should be defined when giving an oral presentation? All technical acronyms and terminology System design and analysis Objectives and the mission gather best practices technical jargon Correct. When presenting project status to stakeholders, all technical terms and acronyms should be defined. Question 18 of 20 "Fill in the blank" question: select the correct answer. Fill in the blank Lower CASE tools support development activities, such as design, testing, debugging, and maintenance. Correct. Lower CASE tools support development activities. Question 19 of 20 What is a downside of using the Internet as a resource? Potential for hacking Accuracy of information Potential for copyright infringement Correct. Not all information on the Internet is accurate. It must be validated. Question 20 of 20 What activities do Web 2.0 enable? Chat rooms and forums Collaboration and interaction among users Webinars and VOIP Correct. Web 2.0 signifies active experiences with user-generated content. [Show More]
Last updated: 2 years ago
Preview 1 out of 14 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Apr 27, 2021
Number of pages
14
Written in
Additional information
This document has been written for:
Uploaded
Apr 27, 2021
Downloads
0
Views
88






.png)