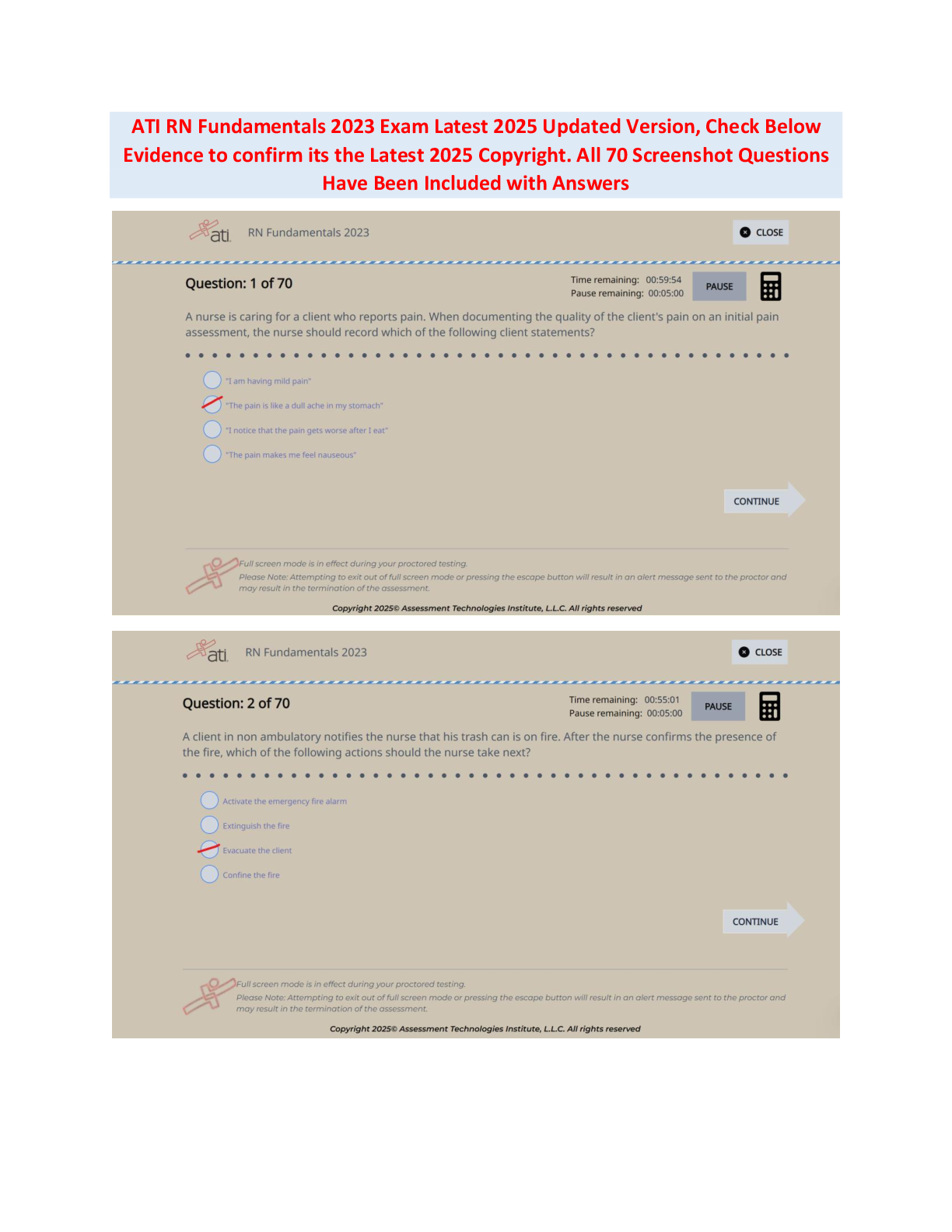
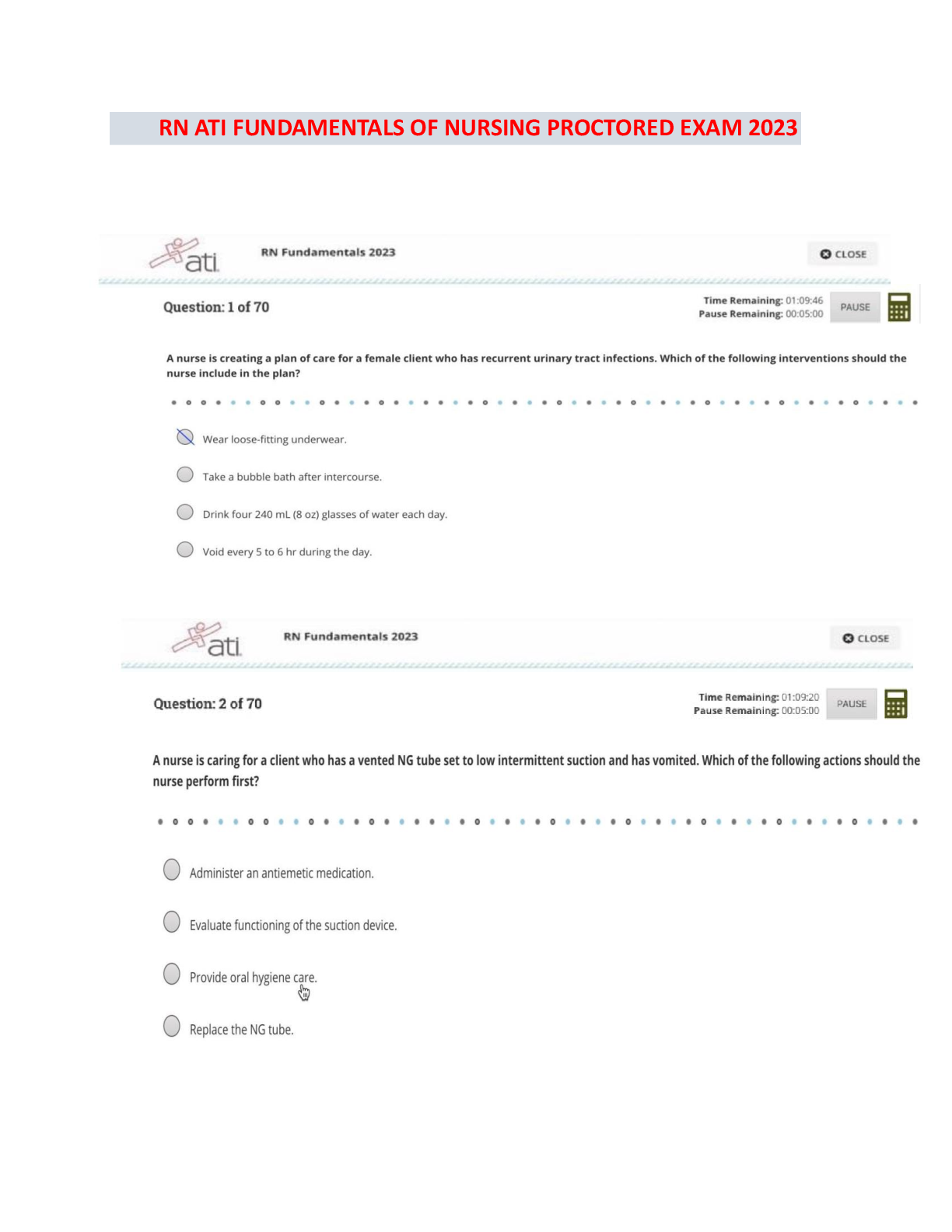
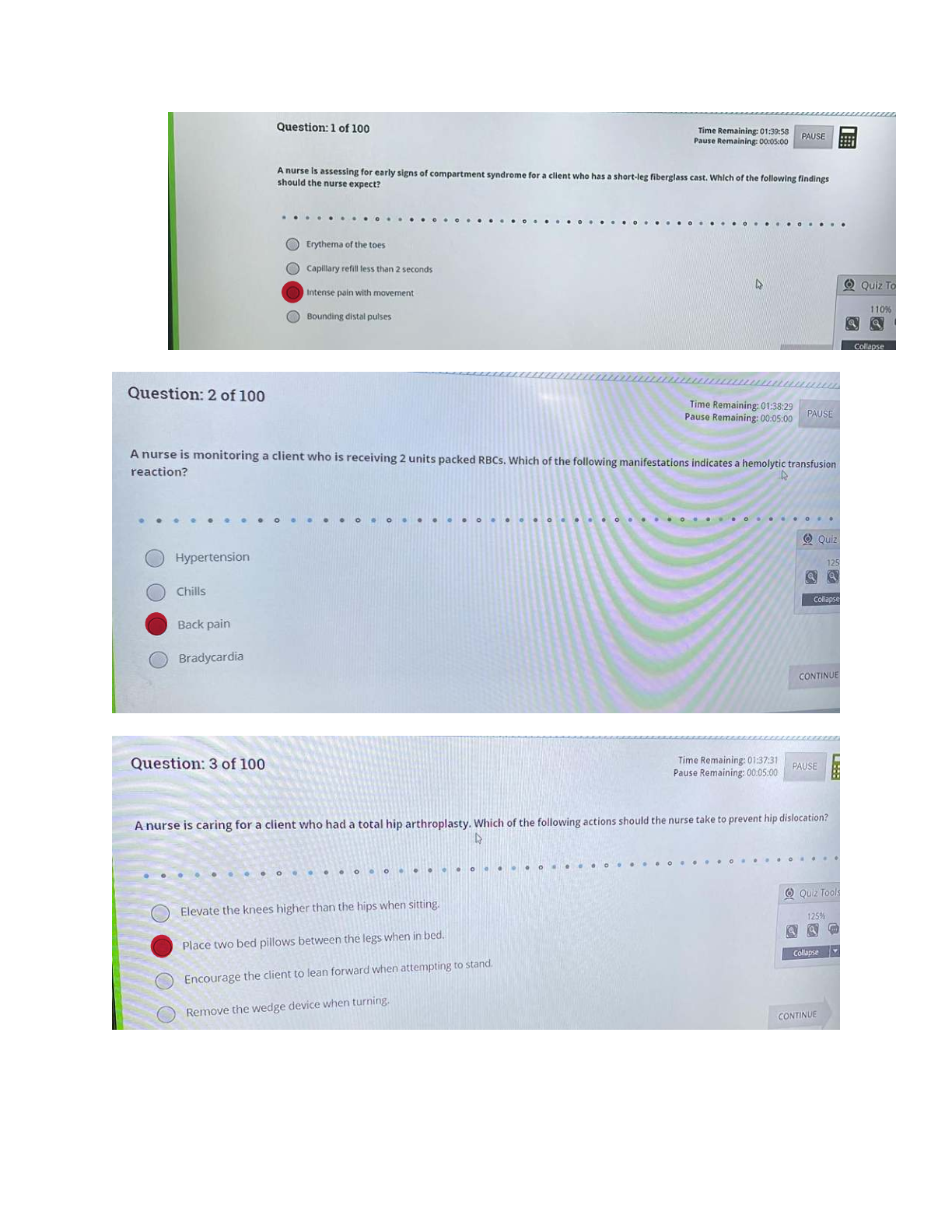
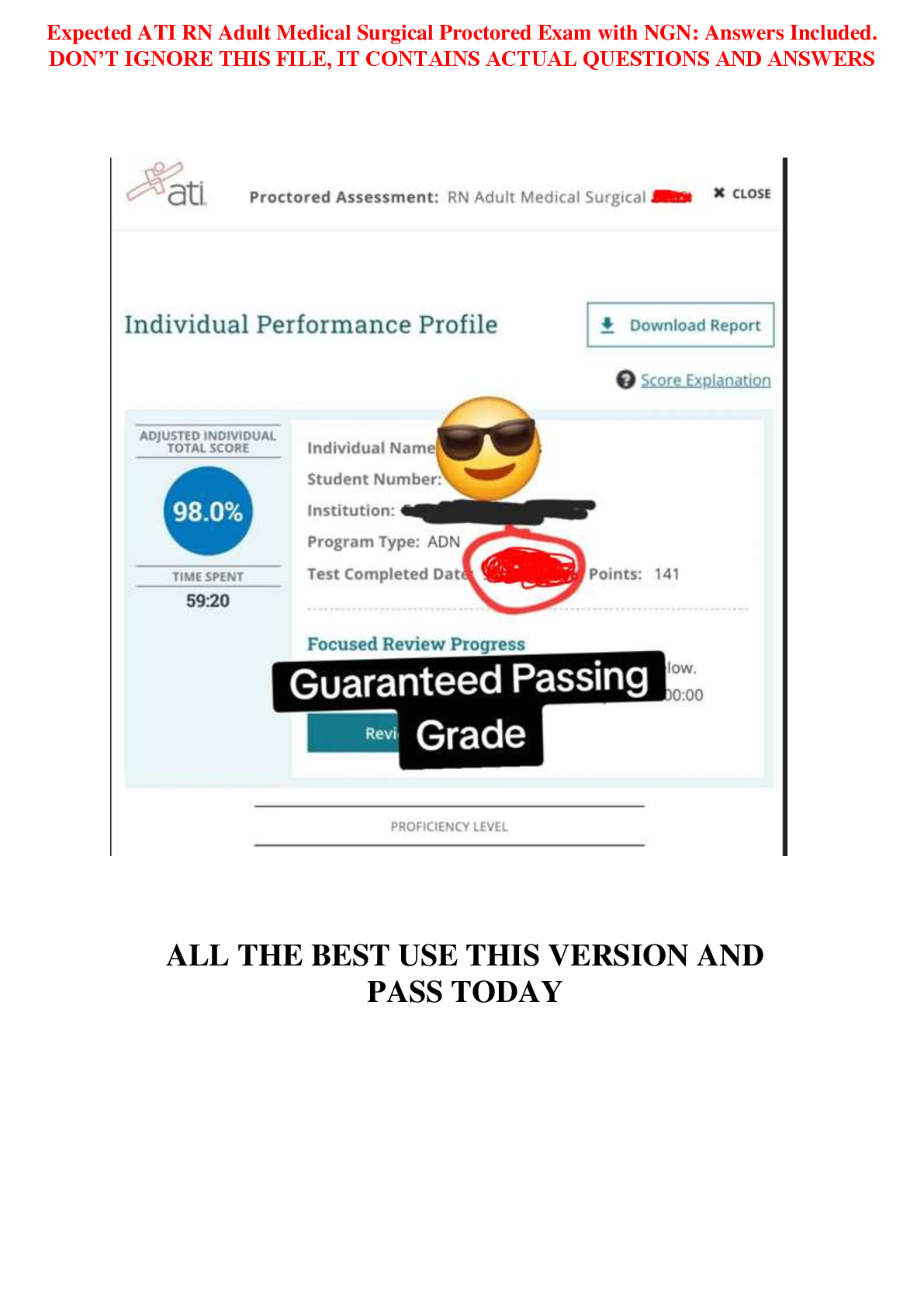
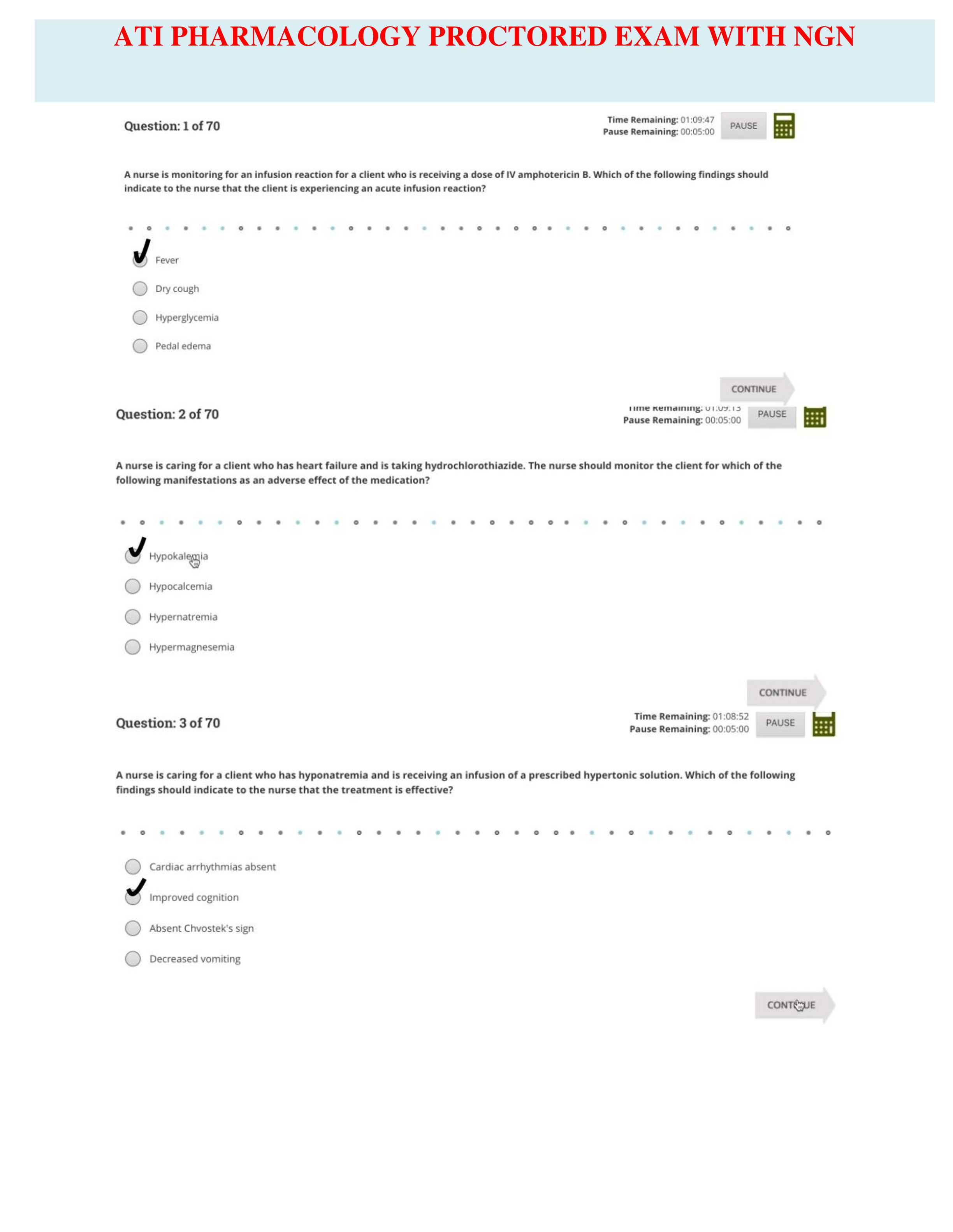
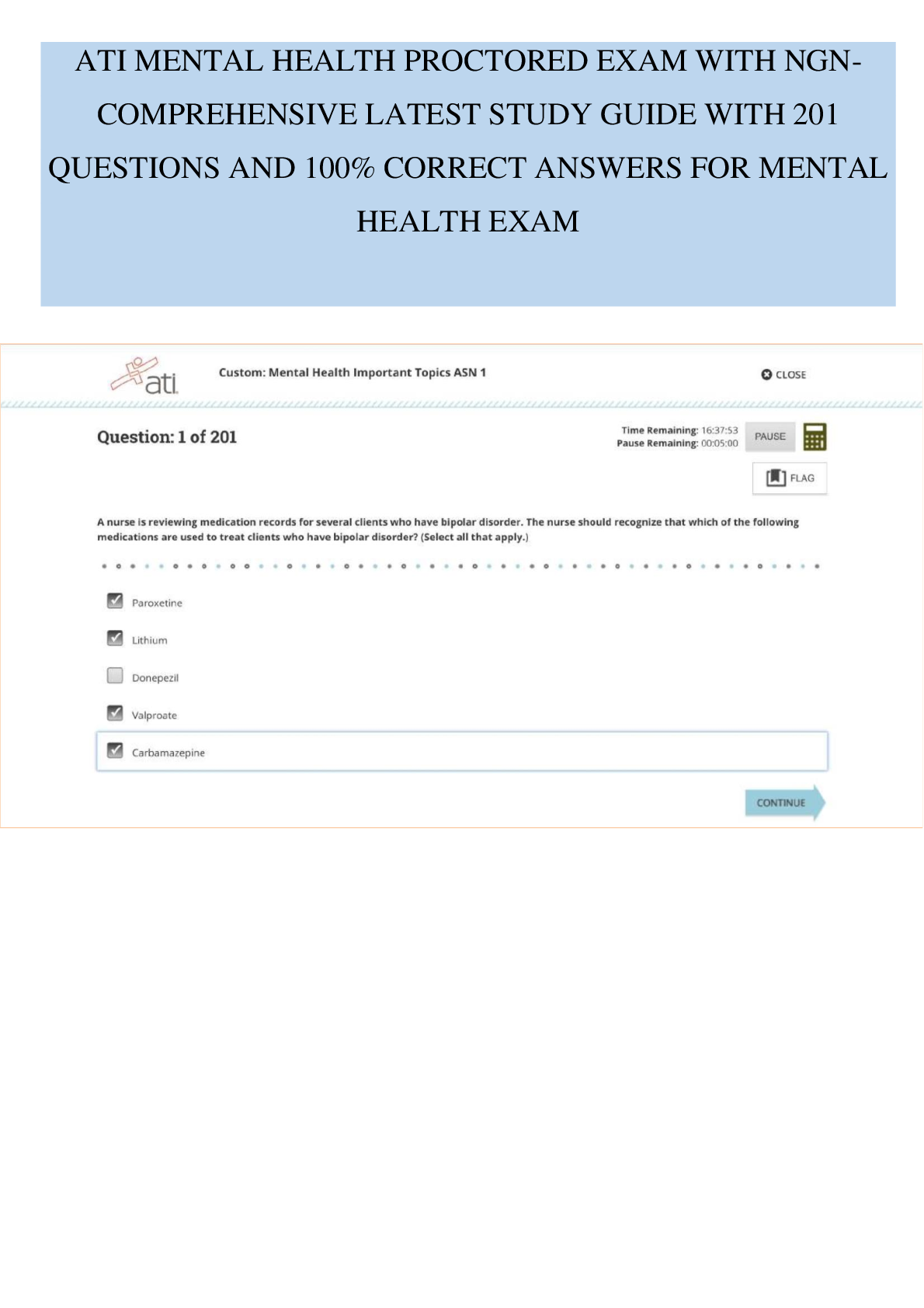
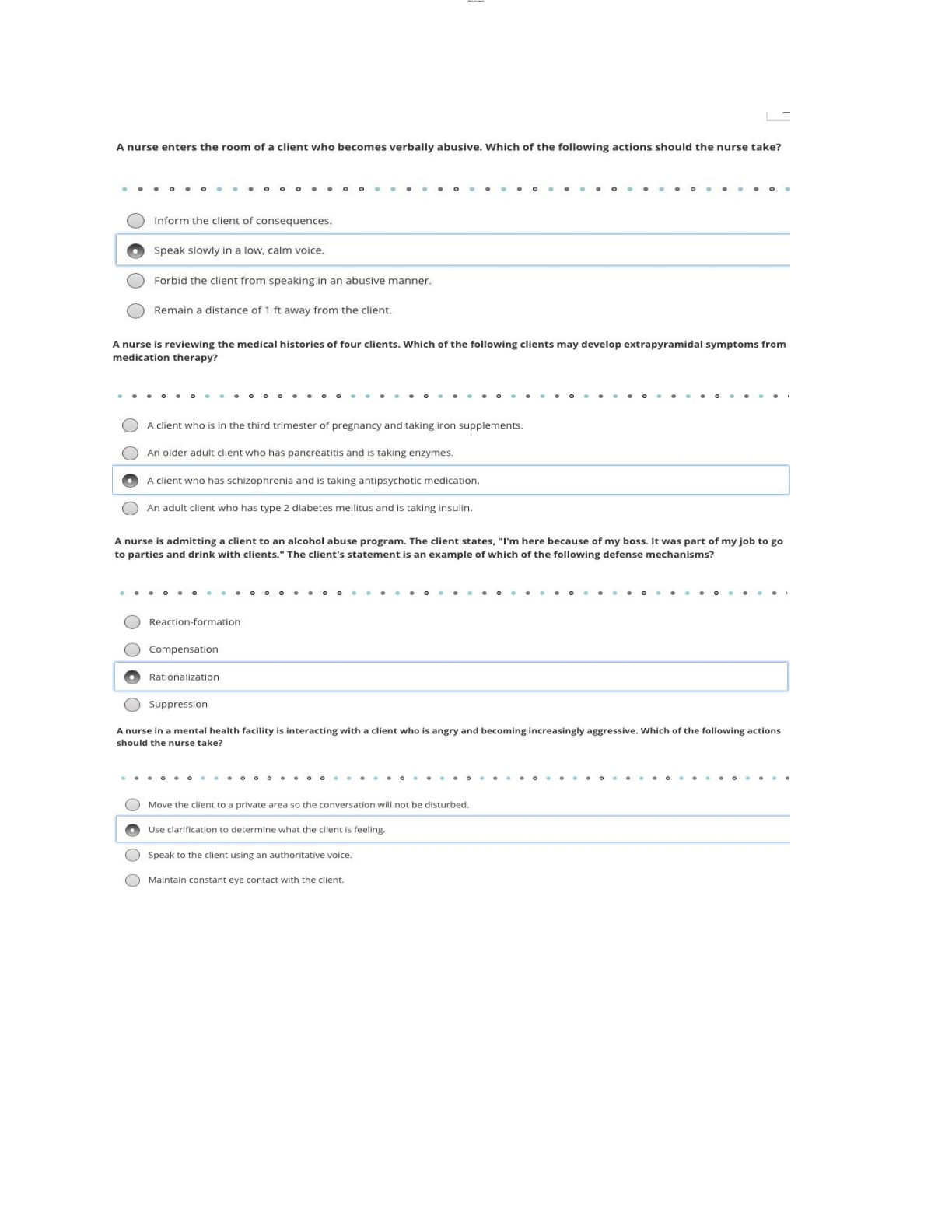
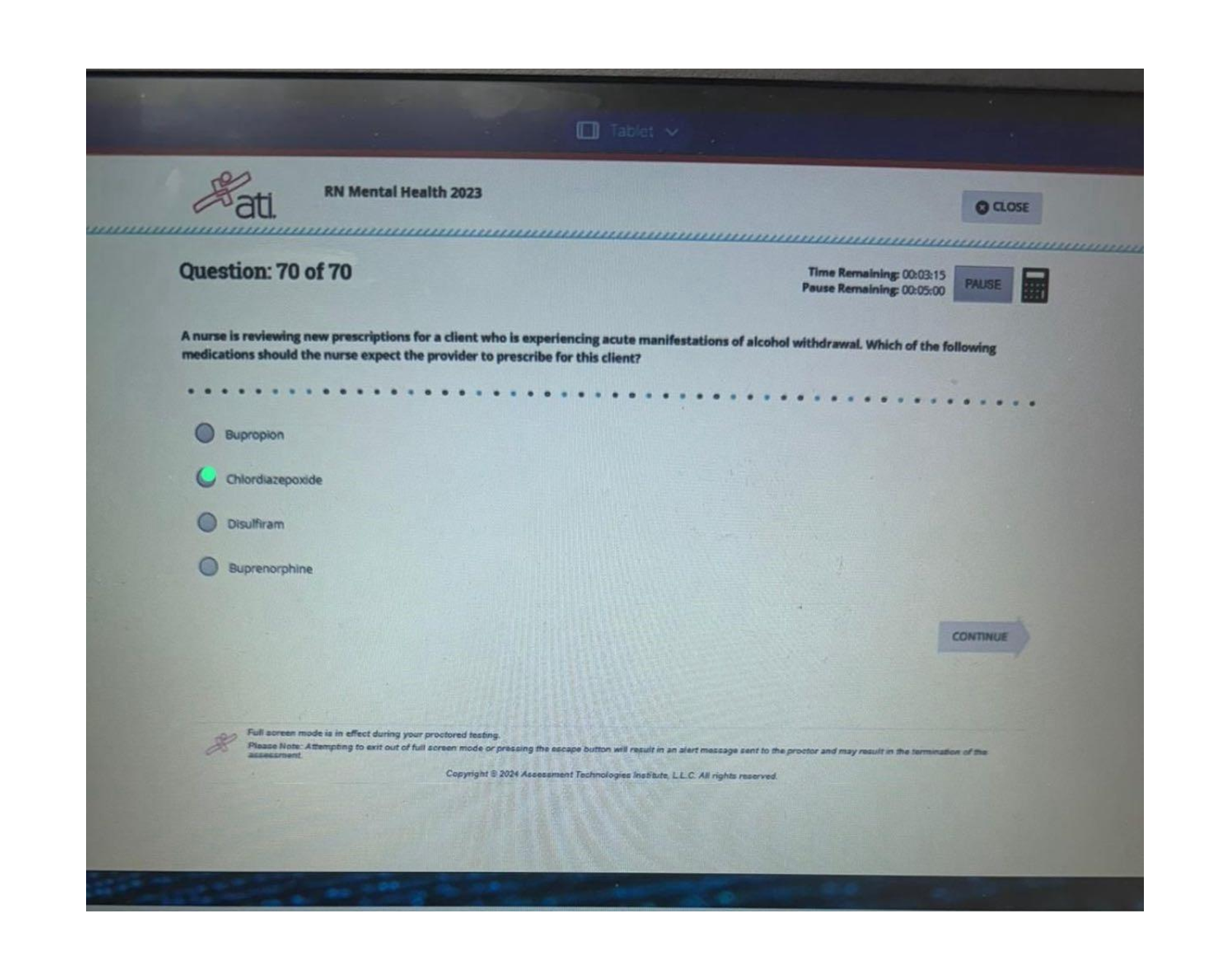
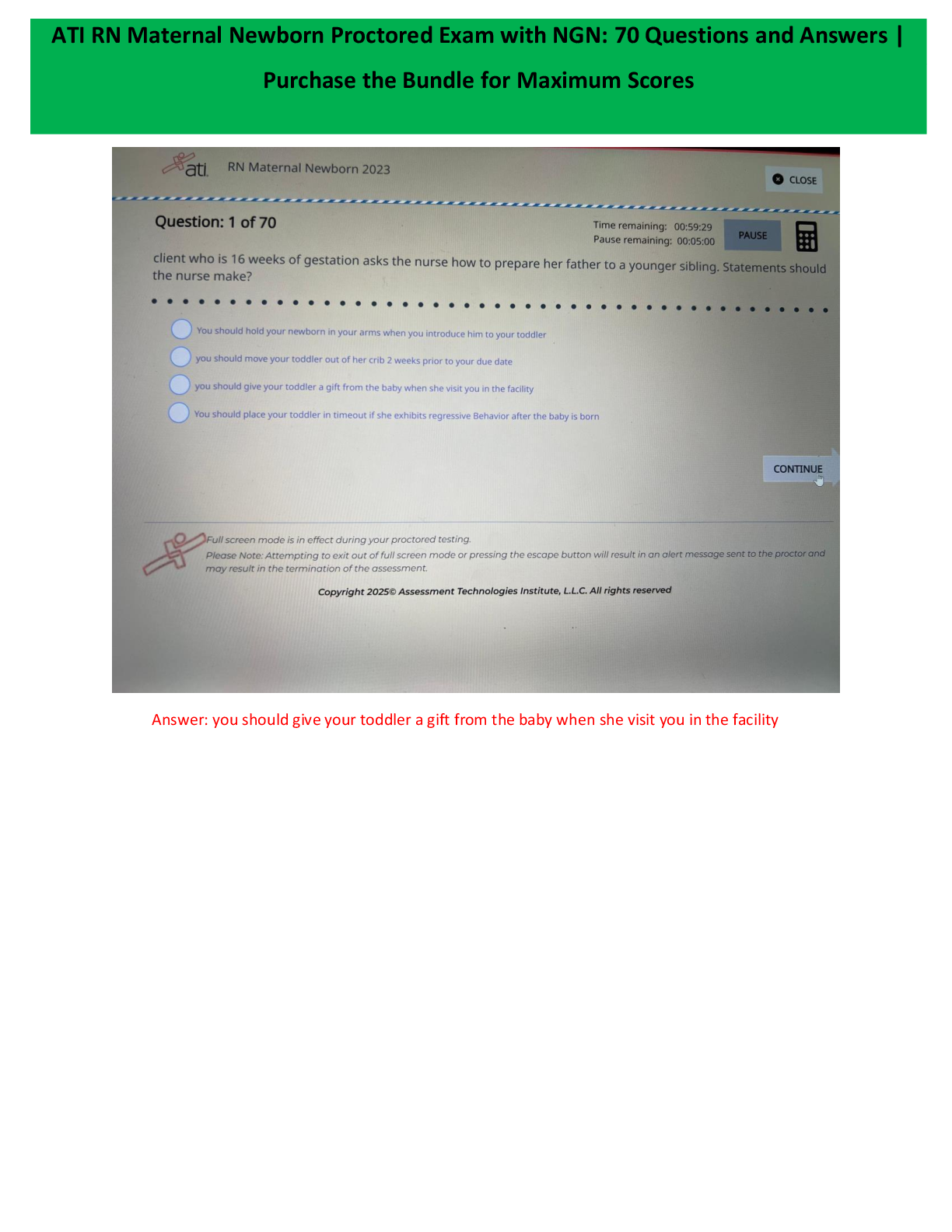
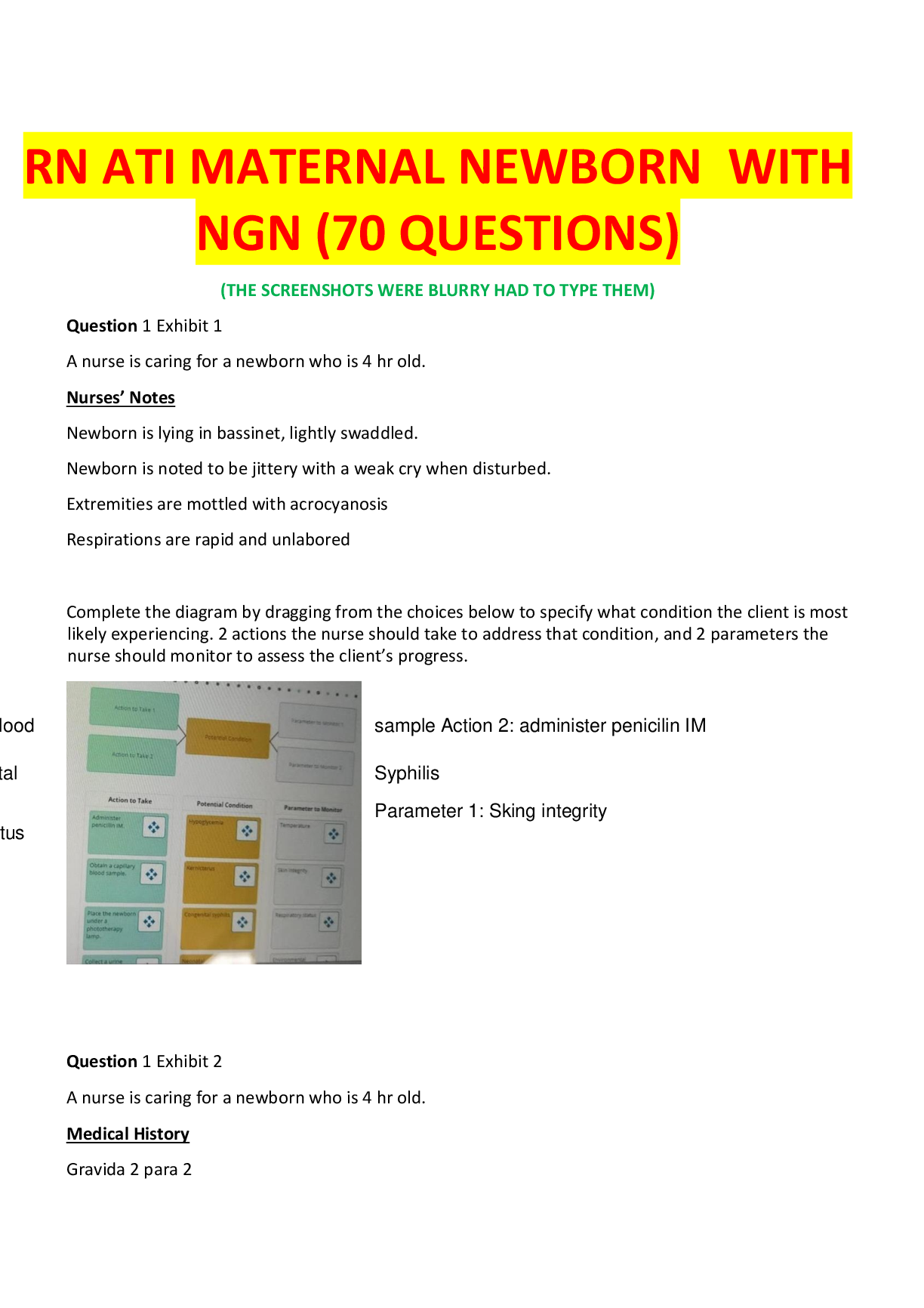
SEC 280 Final Exam. (Version 2) Questions And Answers. 1. (TCO 5) Unsolicited commercial e-mail is known as _____. (Points : 4)
hoax e-mail
worm
spam
spork
Question 2.2. (TCO 5) Two tools that can be used to encrypt
...
SEC 280 Final Exam. (Version 2) Questions And Answers. 1. (TCO 5) Unsolicited commercial e-mail is known as _____. (Points : 4)
hoax e-mail
worm
spam
spork
Question 2.2. (TCO 5) Two tools that can be used to encrypt e-mail are _____. (Points : 4)
MIME/S and PGP
PGP and S/MIME
PSP and MIME/S
PGP and SIME
Question 3.3. (TCO 5) One of the largest security problems with IM programs is _____. (Points : 4)
their inability to share files
the lack of support for encryption
the lack of support for video
the lack of support for hiding online presence
Question 4.4. (TCO 6) What is the name of the process that controls access to information based on
the sensitivity of that information and whether or not the user is operating at the appropriate
sensitivity level and has the authority to access that information? (Points : 4)
MAC
DAC
RBAC
RBOC
Question 5.5. (TCO 6) A network administrator wants to be sure that when users change their
passwords, they do not reuse a previous password. What domain password policy will need to be
configured? (Points : 4)
Enforce password history
Maximum password age
Minimum password age
Minimum password length
Question 6.6. (TCO 6) A network administrator wants to specify the number of days a password must
be used before it can be changed again. What domain password policy will need to be configured?
(Points : 4)
Enforce password history
Maximum password age
Minimum password age
Minimum password length
Question 7.7. (TCO 6) Which of the following can a user control on their system? (Points : 4)
Cookies
Running JavaScript
Running ActiveX
Selection of hyperlinks
Question 8.8. (TCO 6) Which is a 100% secure method to download applications from the Internet?
(Points : 4)
Signed applets
SSH
HTTPS
None of the above
Question 9.9. (TCO 6) SSMTP uses TCP port (Points : 4)
25.
110.
465.
456.
Question 10.10. (TCO 2) HTTPS uses TCP port (Points : 4)
433.
443.
344.
434.
Question 11.11. (TCO 2) When an attacker attempts to get credit card numbers using telephone and
voice technologies, it's called (Points : 4)
vishing.
telephishing.
phreaking.
voicing.
[Show More]
.png)





.png)


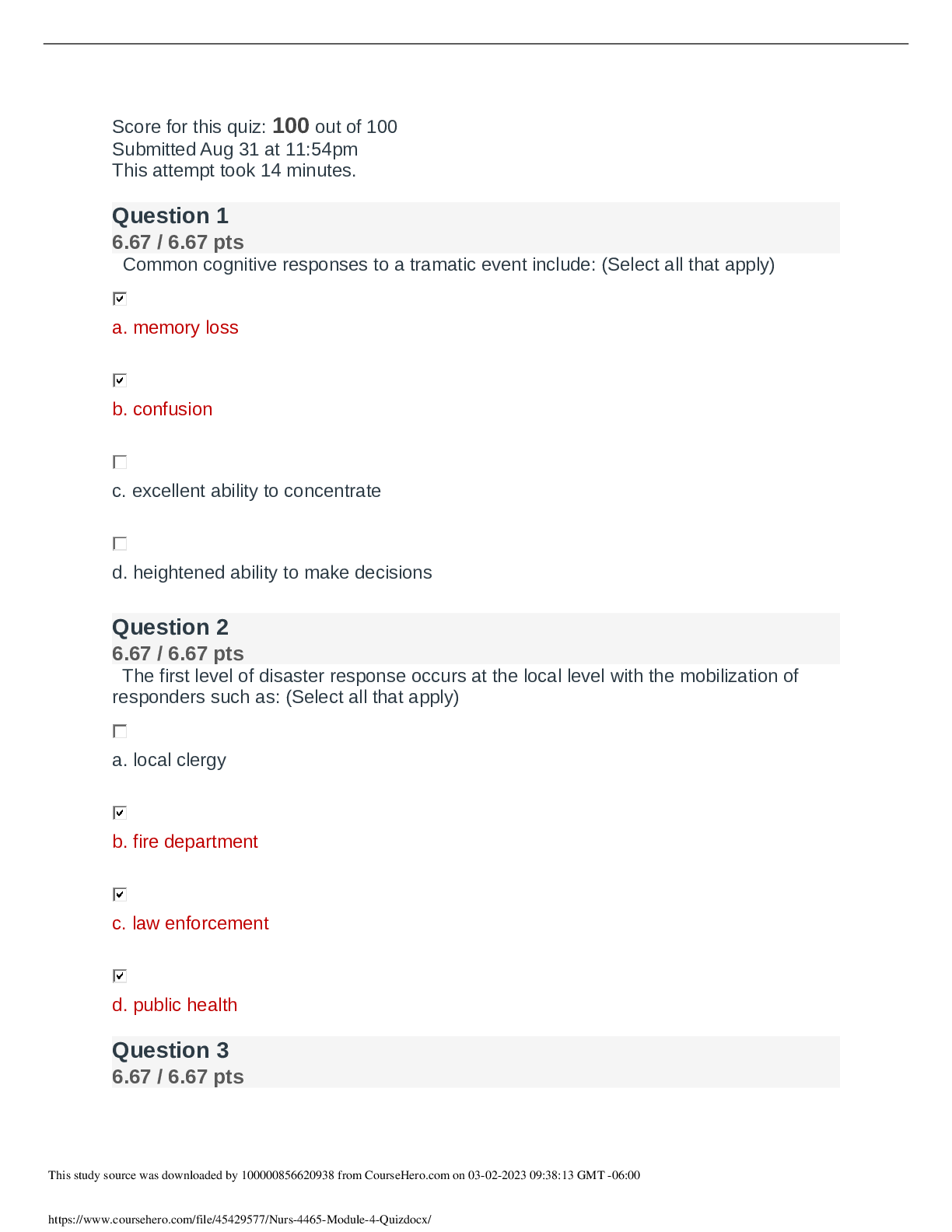

.png)