Computer Science > QUESTIONS & ANSWERS > SOPHIA PATHWAY Unit 3 Milestone 3 Questions With 100% Correct Answers (Latest Update) (All)
SOPHIA PATHWAY Unit 3 Milestone 3 Questions With 100% Correct Answers (Latest Update)
Document Content and Description Below
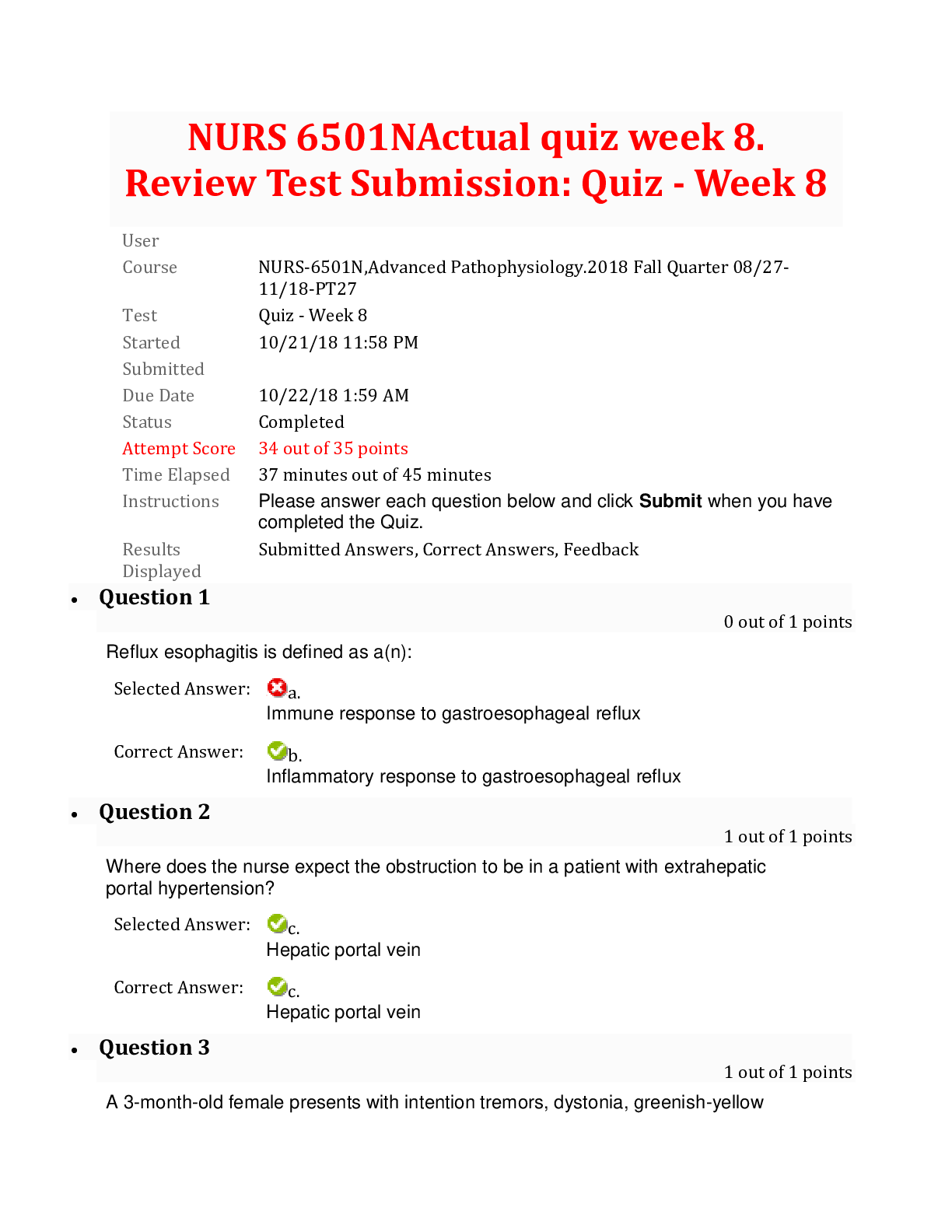
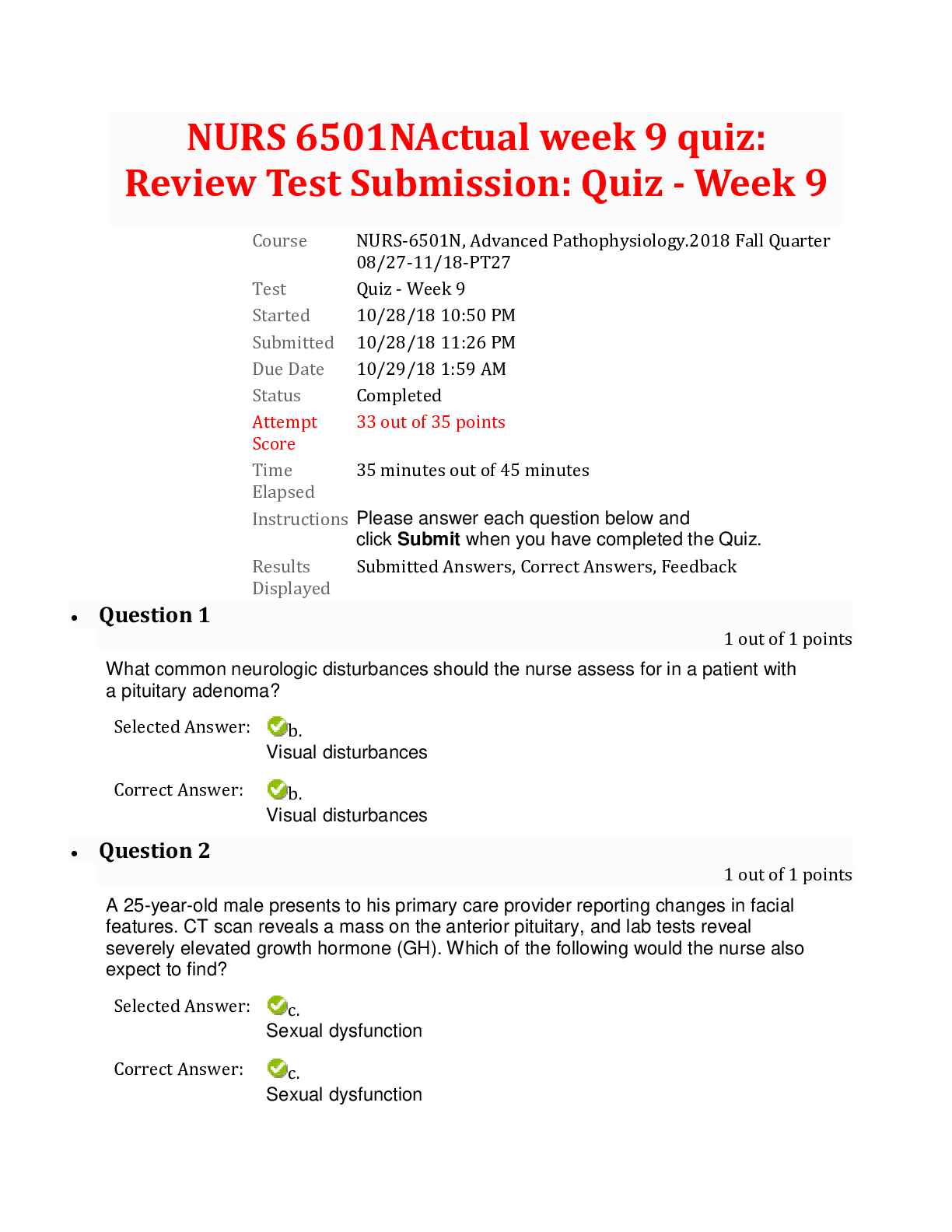
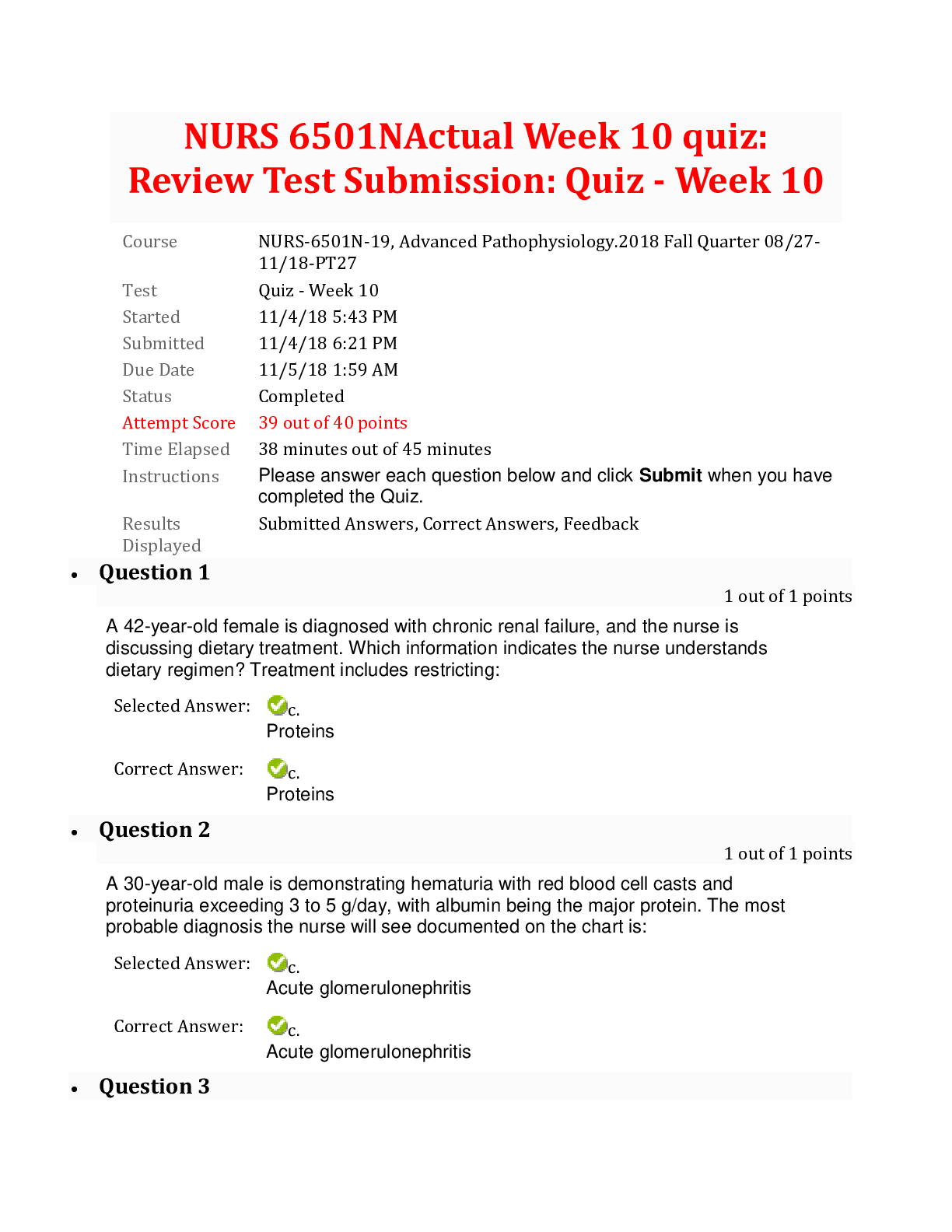
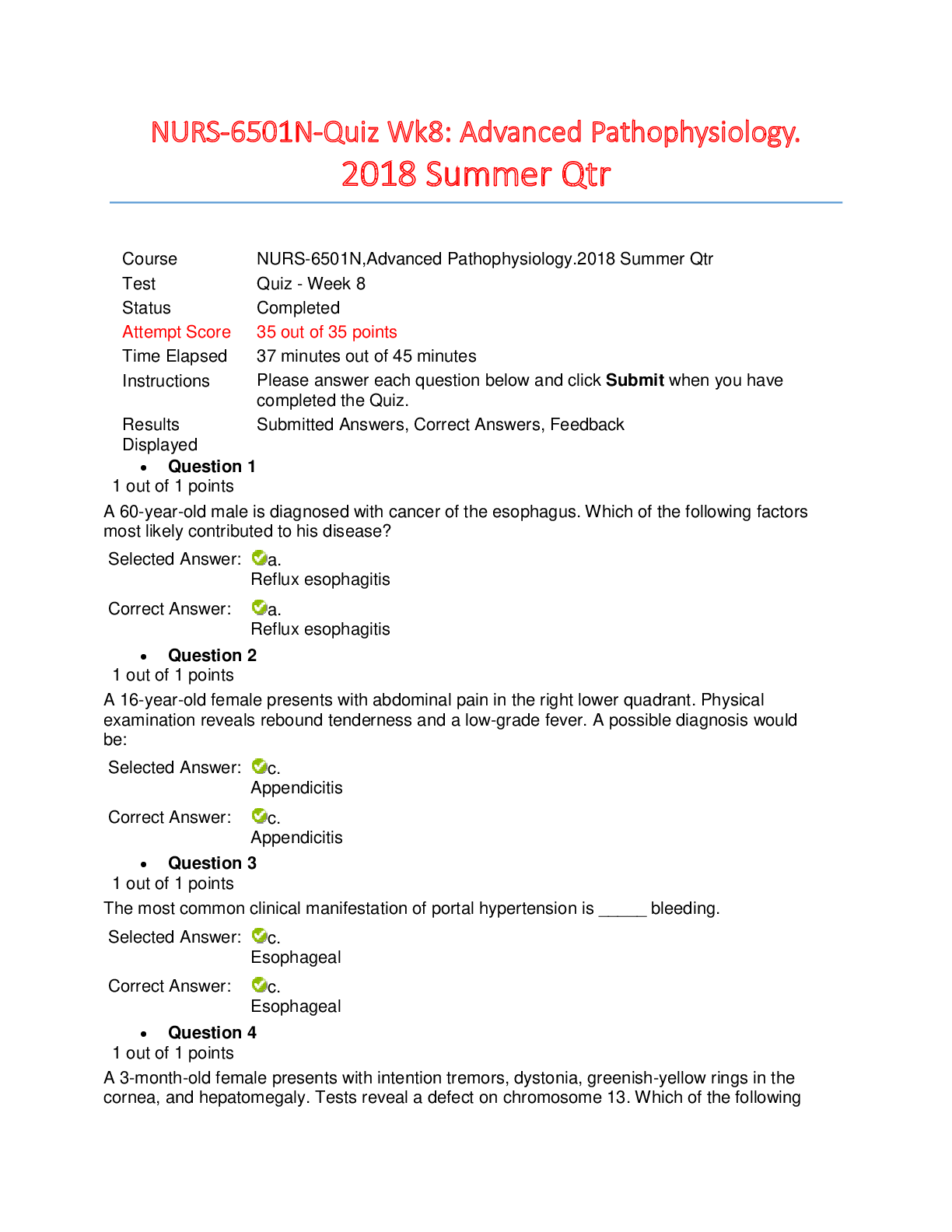
The standard interface technology for wireless networks is __________. The hardware component necessary for computers to connect to these networks is a __________. transmission control protoco... l; IP wireless-internet protocol; TCP wireless-defined networking; WAP wireless fidelity; WAP 2 While Kari was searching the Internet, her computer was infected by a virus. What problem can Kari expect as a result? The code will install software that looks useful but compromises her system's security. A toolbar will be installed that redirects her Web browser to pirated sites. Her keystrokes will be recorded and used by hackers to steal her personal and financial information. The virus will attach itself to the computer's RAM, then attach itself to executable files in RAM. 3 Victor and Ellen are software engineers working on a popular mobile app. Victor has been in his position for 10 years longer than Ellen, who is a recent graduate. During the development of a new feature, Ellen expressed her concern that VIctor's proposed code would create instability in the app. Victor told Ellen he would address her concern with their supervisor. When Victor met privately with his supervisor, he claimed that he had discovered the problem, and that Ellen had dismissed it. Which principle of the Software Engineering Code of Ethics has Victor violated? Principle 8: Self Principle 7: Colleagues Principle 3: Product Principle 6: Profession 4 Select the true statement about COPPA. The COPPA regulations state that websites may not collect information from minors under the age of 13. The COPPA regulations apply to websites that collect information from children. The COPPA regulations require that parents of children under the age of 13 be given instructions on how to maintain privacy. The COPPA regulations restrict a child's access to harmful content. - Protecting Minors from Online Dangers 5 Select the sign of computer addiction that indicates a lack of control. While driving his car, Mitch rear-ended another car when he was checking his social media account. After moving to a new town, Sal spends most of his time online to keep his mind off the friends he misses. Ever since his mother died, Charlie stays up late every night playing an online game. Even though she knows that she should, Jacqueline cannot stop playing her favorite online game. Computer Addiction 6 Kirby visited a sweepstakes website and agreed to download a new program. Later, when he tried to use a word processing program, his document files became corrupted. How can Kirby try to remove the offending program and prevent future attacks? Kirby should run an antivirus program. Kirby should install a biometric reader. Kirby should use WPA network encryption. Kirby should change the password on his computer. Network Security 7 Select the FALSE statement about the history of the Internet. The Internet means “an interconnected network of networks.” ARPANET began transmission in 1969, when it connected computers at UCLA, Stanford, MIT, and the University of Utah. The U.S. government created ARPA in response to the successful launch of a satellite by the Soviet Union. The invention of HTML enabled computers on different networks to communicate with each other. The World Wide Web 8 Which of the following can be controlled by copyright? The team logo for a minor league baseball team A new type of engine for pickup trucks The slogan for a business A writer’s new murder mystery on the New York Times bestsellers list Copyright, Trademark and Intellectual Property 9 Select the true statement about HTML. HTML stands for hidden transfer markup language. The web consists of documents written in HTTP and transmitted by HTML. An HTML tag initiates a protocol known as HTTP. The final product transmitted to a browser is in HTML. Website Development 10 In which of the following scenarios can a trademark be applied? [Show More]
Last updated: 2 years ago
Preview 1 out of 20 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Nov 23, 2021
Number of pages
20
Written in
Additional information
This document has been written for:
Uploaded
Nov 23, 2021
Downloads
0
Views
142

.png)