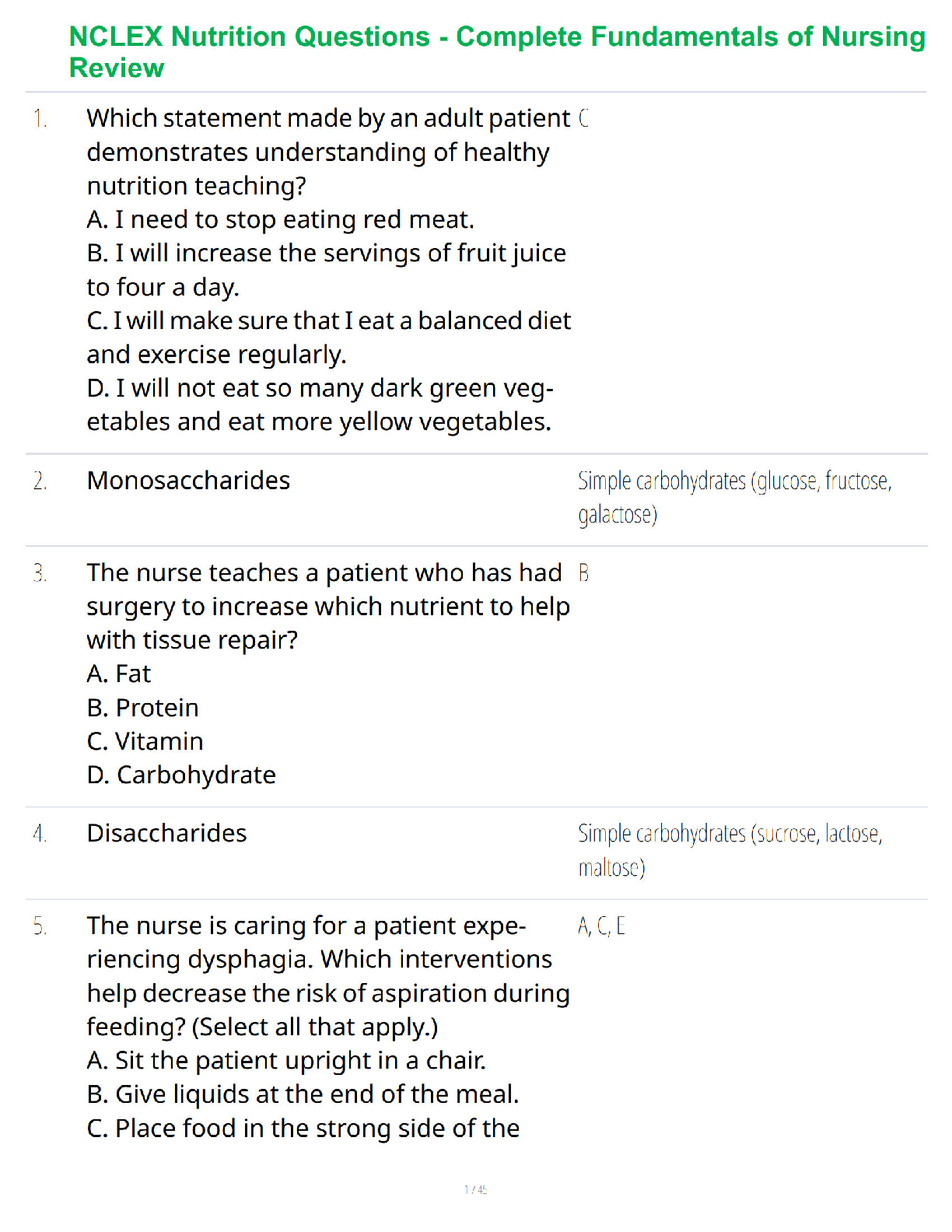
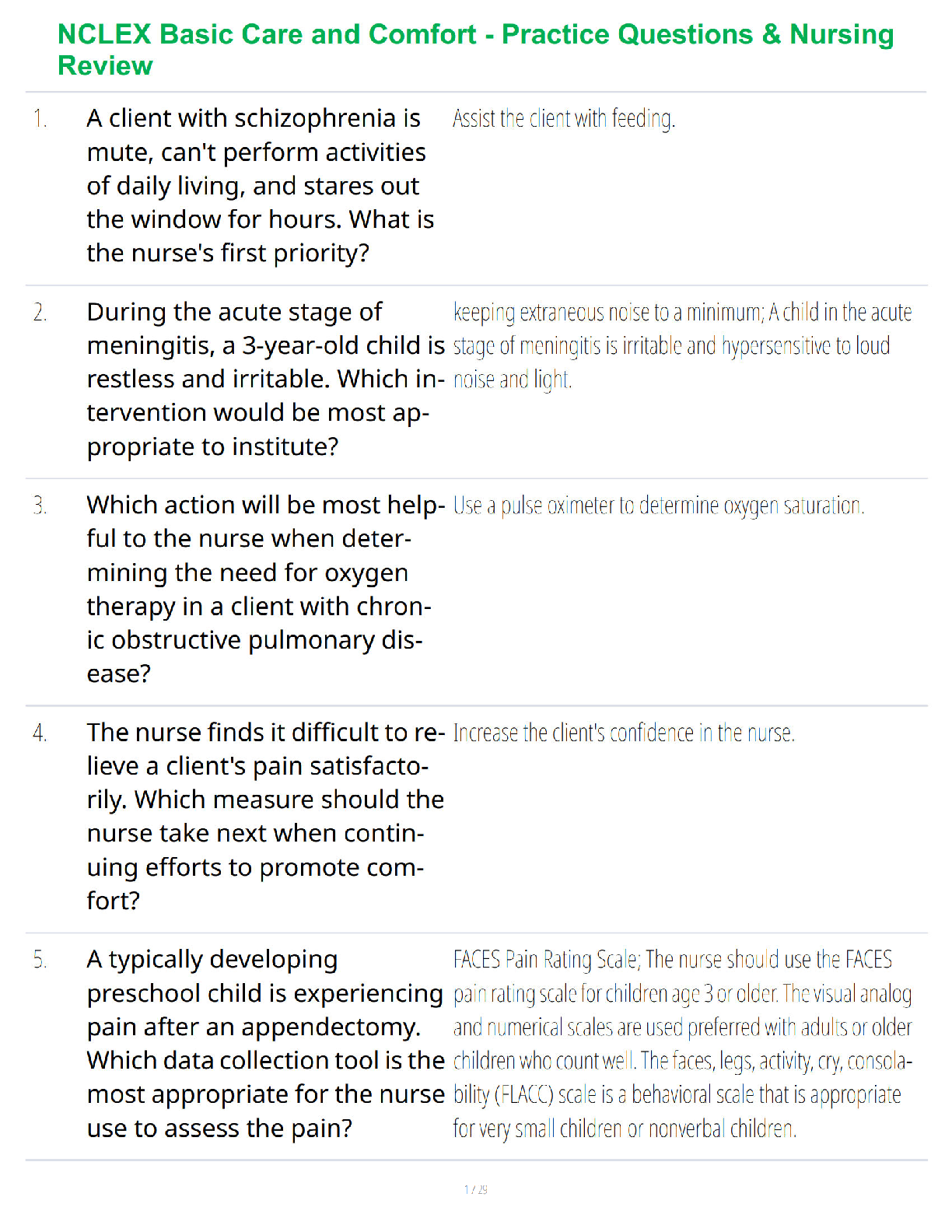
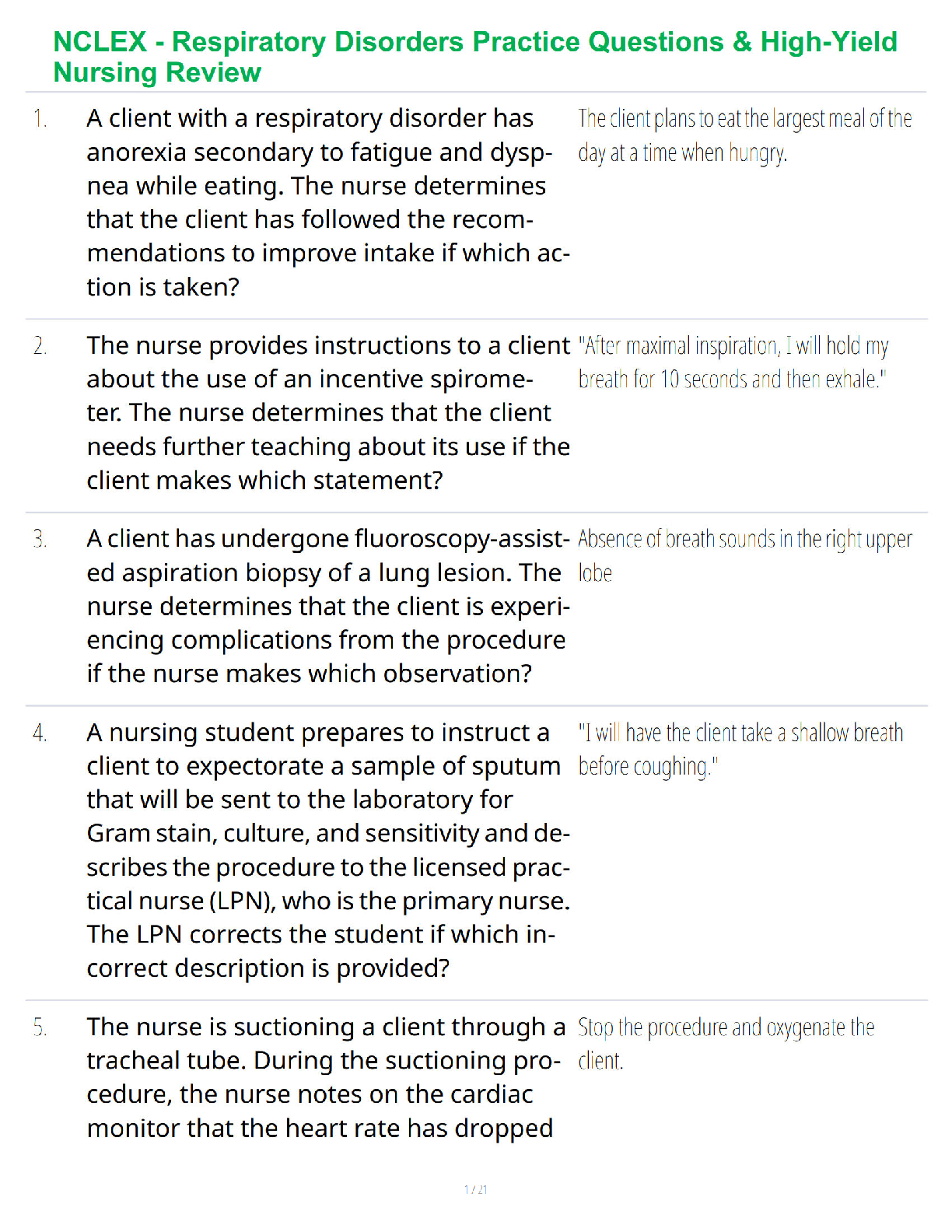
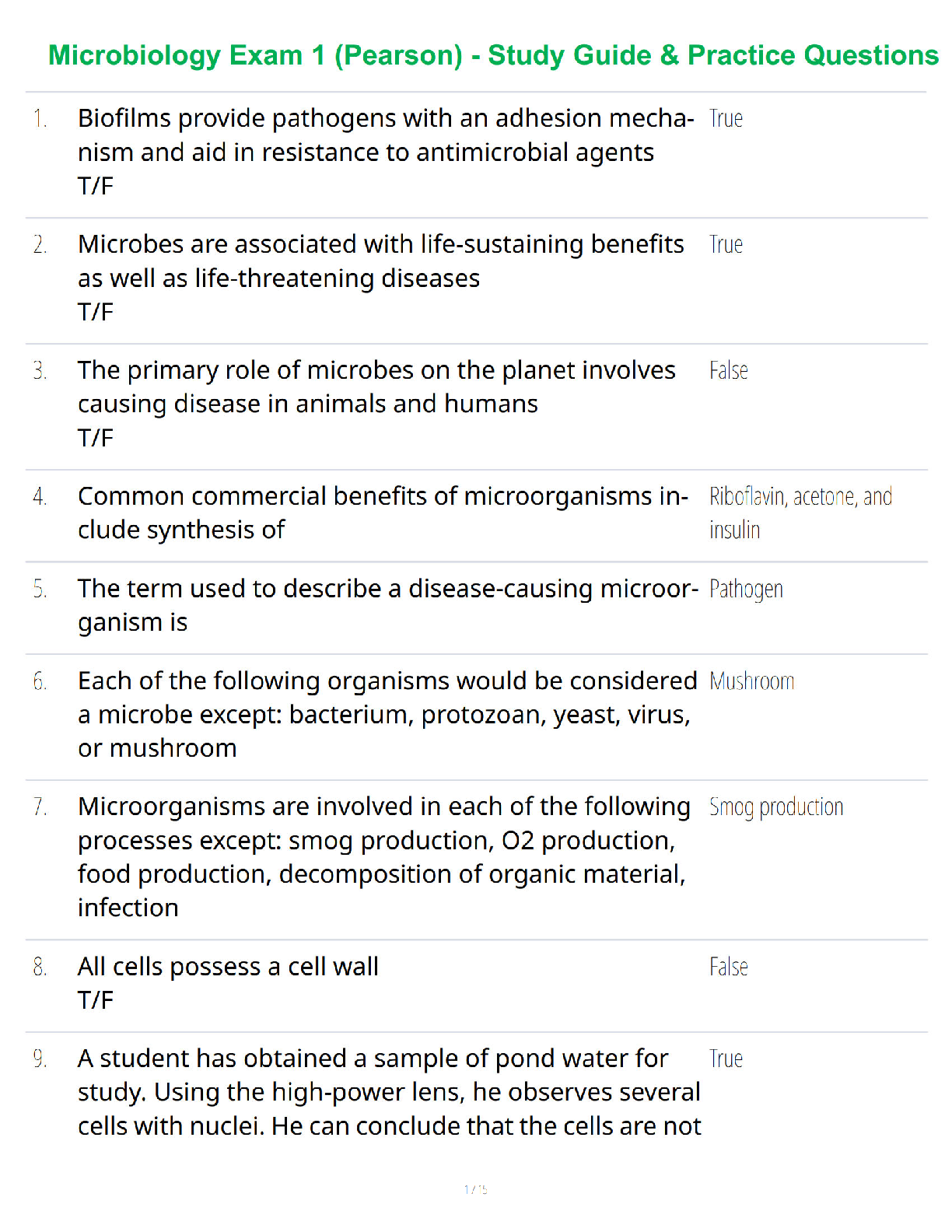
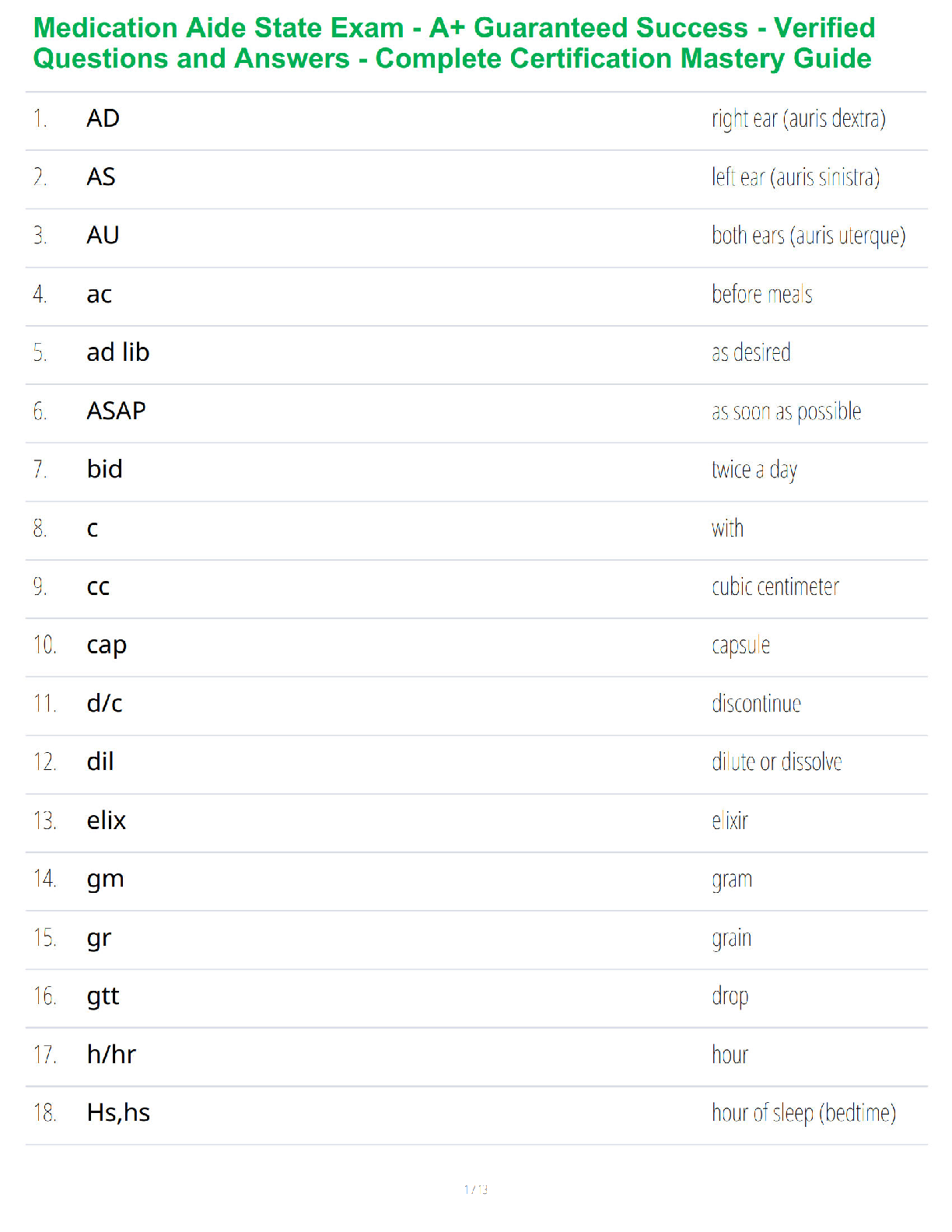
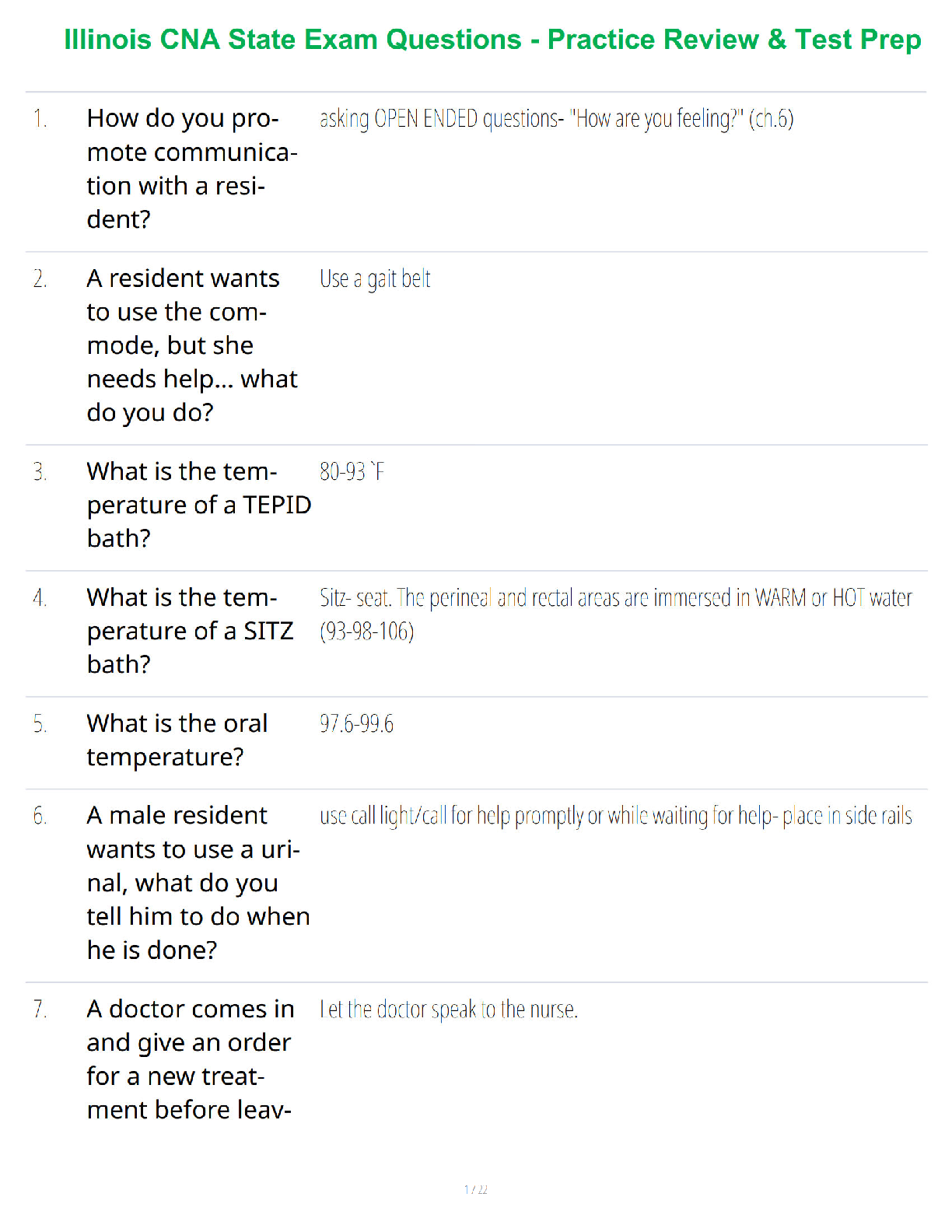
NR 509 Final Exam Study Guide.
$ 7

ASTB Mechanical Comprehension, Questions and answers, 100% Accurate, rated A
$ 7

Pathophysiology Notes: Modules 1, 2, & 3
$ 7

EDEXCEL A LEVEL JUNE 2022 CHINESE QUESTION PAPER 1
$ 1

North Carolina State University CH102 Prelab 10 Acid-Base Studies (All Answers are Correct)
$ 5

SEC 572 Week 8 Final Exam - Latest 2019/20 complete solution guide, Devry.
$ 9.5

NGRK 520 Beginner Greek 1 Exam 2 (100% correct answers) REVISED
$ 17
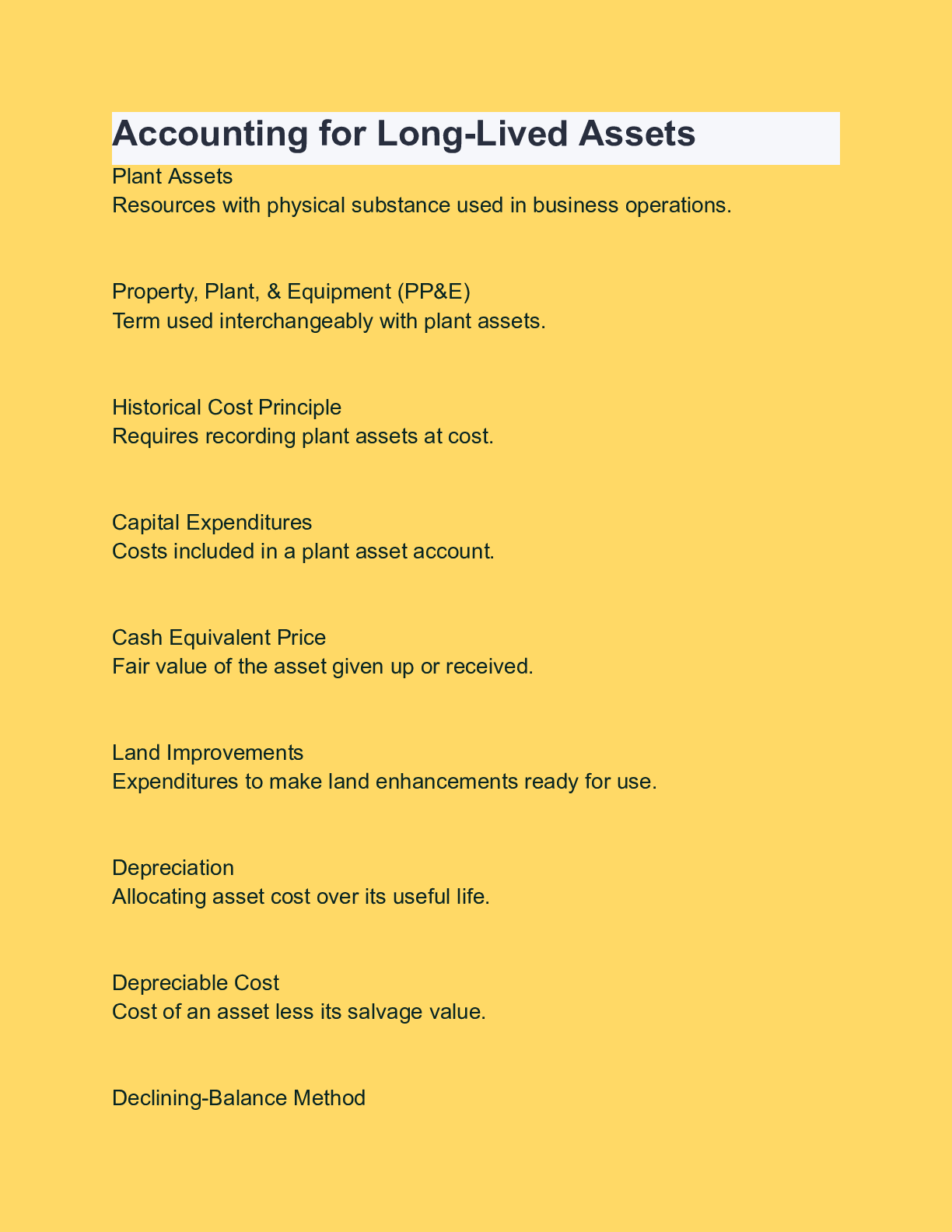
Accounting for Long-Lived Assets
$ 7

[eBook-PDF] Reinforced Concrete Design by Somnath Ghosh ISBN13: 9781032076669
$ 26.5
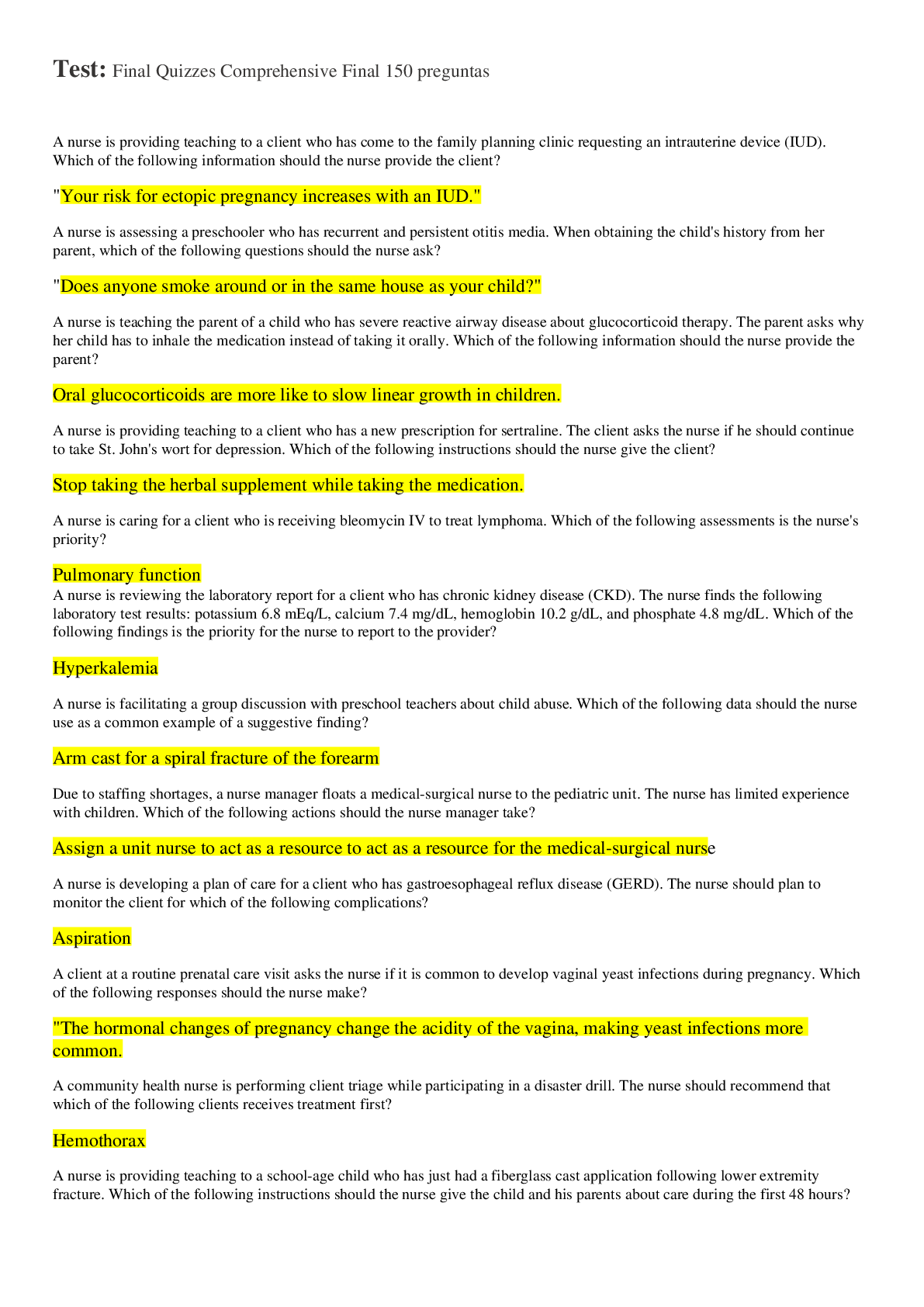
Final Quizzes Comprehensive Final 150 Questions, 2021 Update Study Guide, Correctly Answered Questions, Test bank Questions and Answers with Explanations (latest Update), 100% Correct, Download to Score A
$ 10
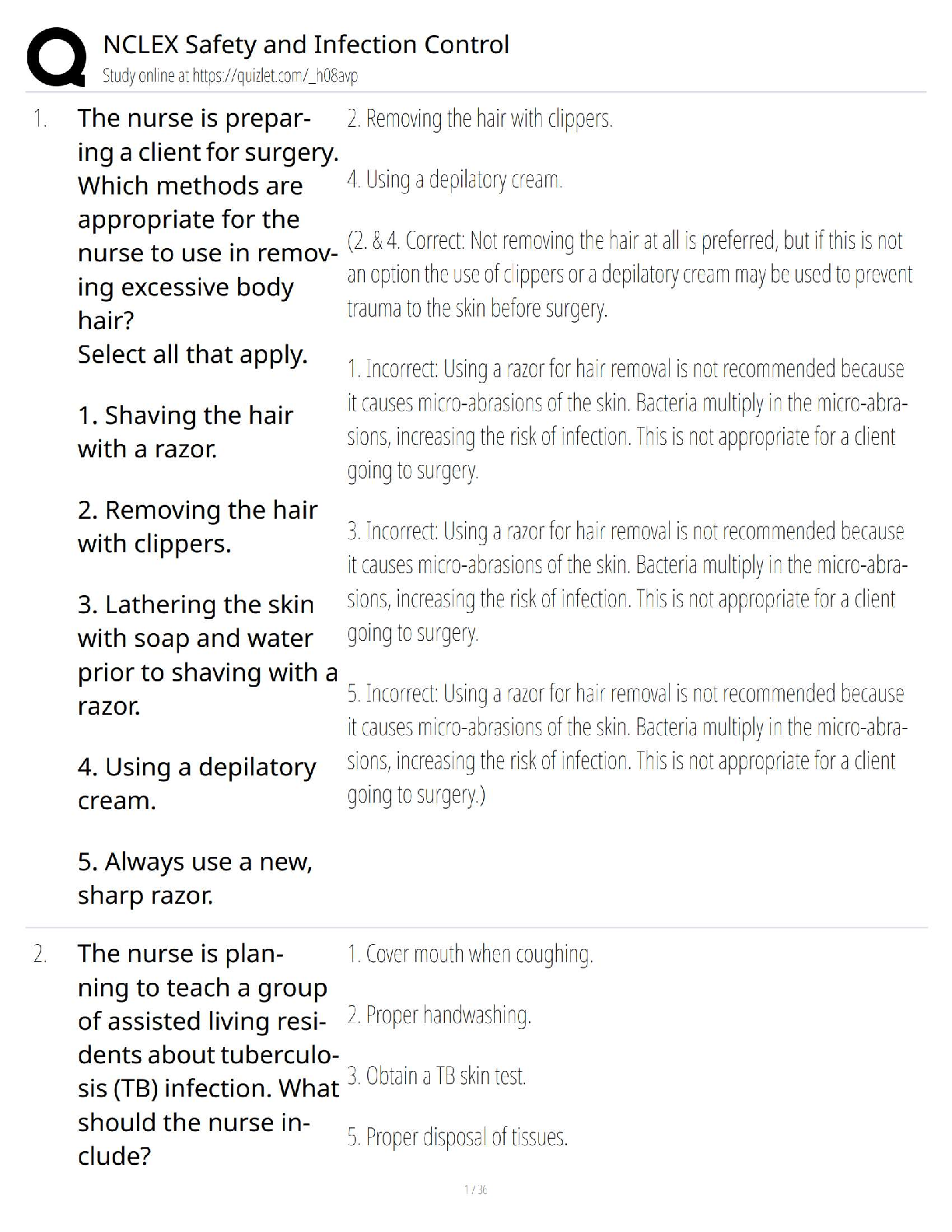
NCLEX / Safety & Infection Control Test Bank / 2025 Update / Score 100%
$ 6

Prophecy medical surgical-telemetry Exam 2023 Answers 100% Verified
$ 11.5
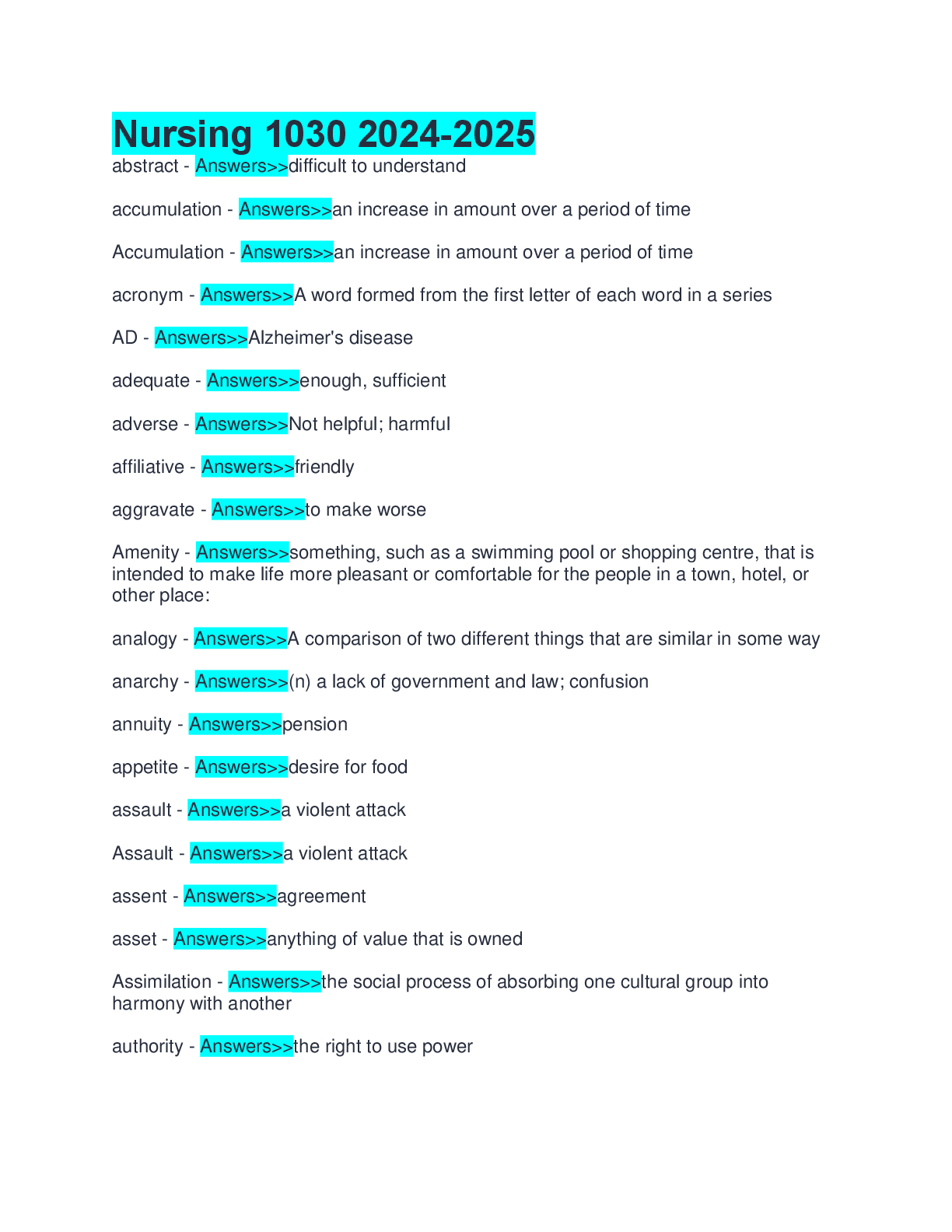
Nursing 1030 2024 2025
$ 25.5

2022/2023 FTEC 93 Airway FISDAP Questions & Answers 100%Correct/Verified Assured Success
$ 12
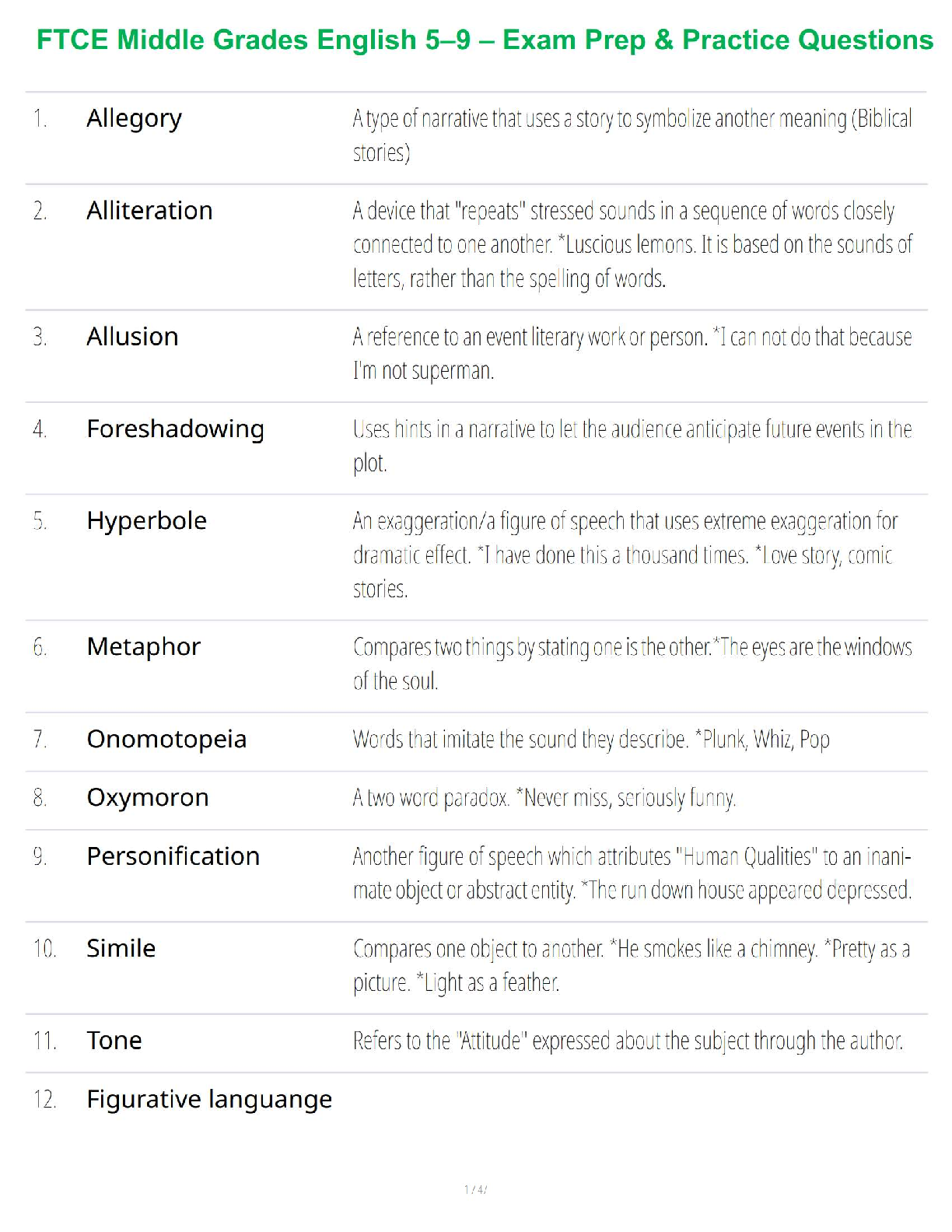
FTCE Middle Grades English 5–9 – Exam Prep & Practice Questions
$ 37

INTRA OPERATIVE CARE NCCT PRACTICE EXAM QUESTION AND ANSWERS
$ 33.5
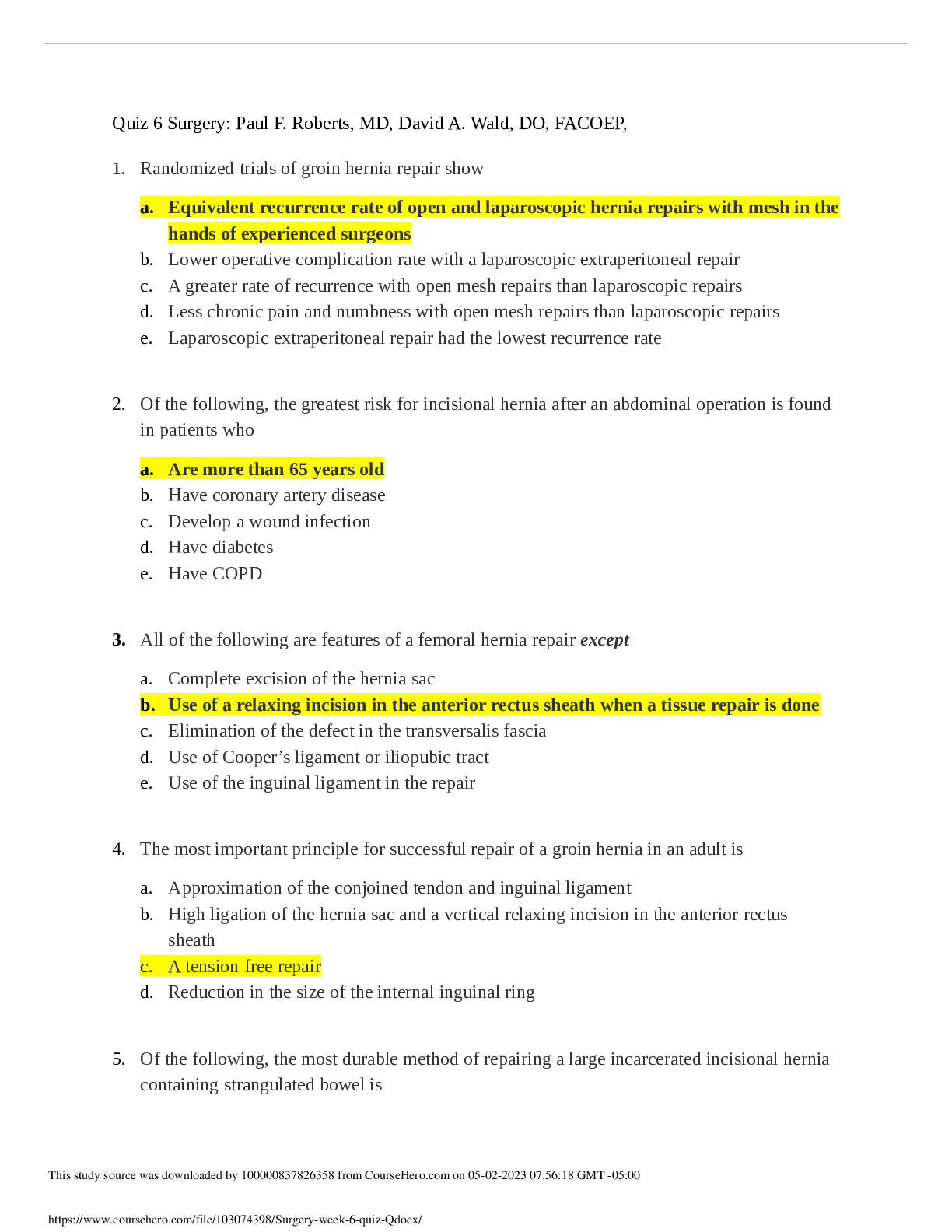
Surgery Week Quiz Series - Part 6 [GRADED A+]