Saint COM530 module 2 quiz/Saint COM530 module 2 quiz
Document Content and Description Below
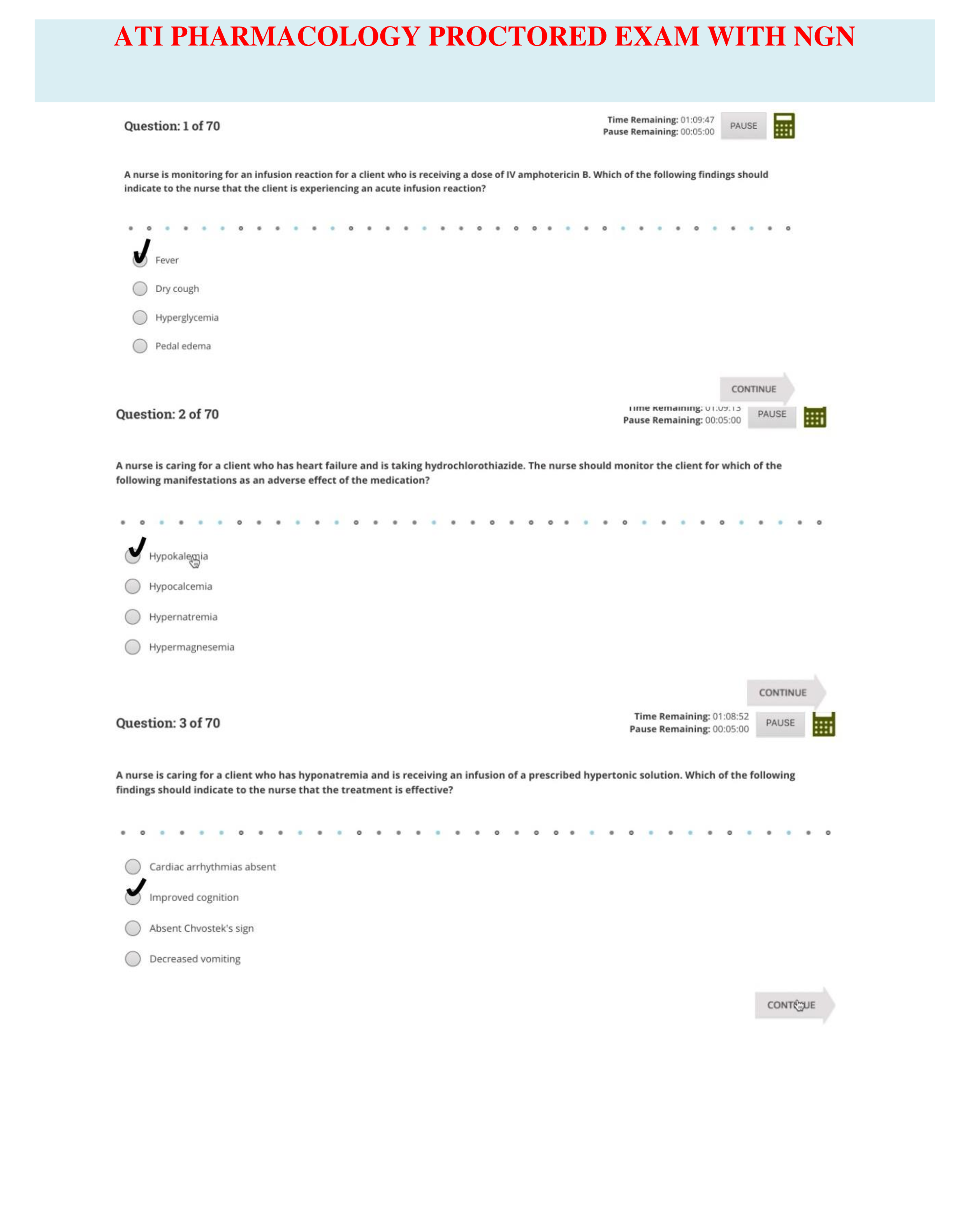
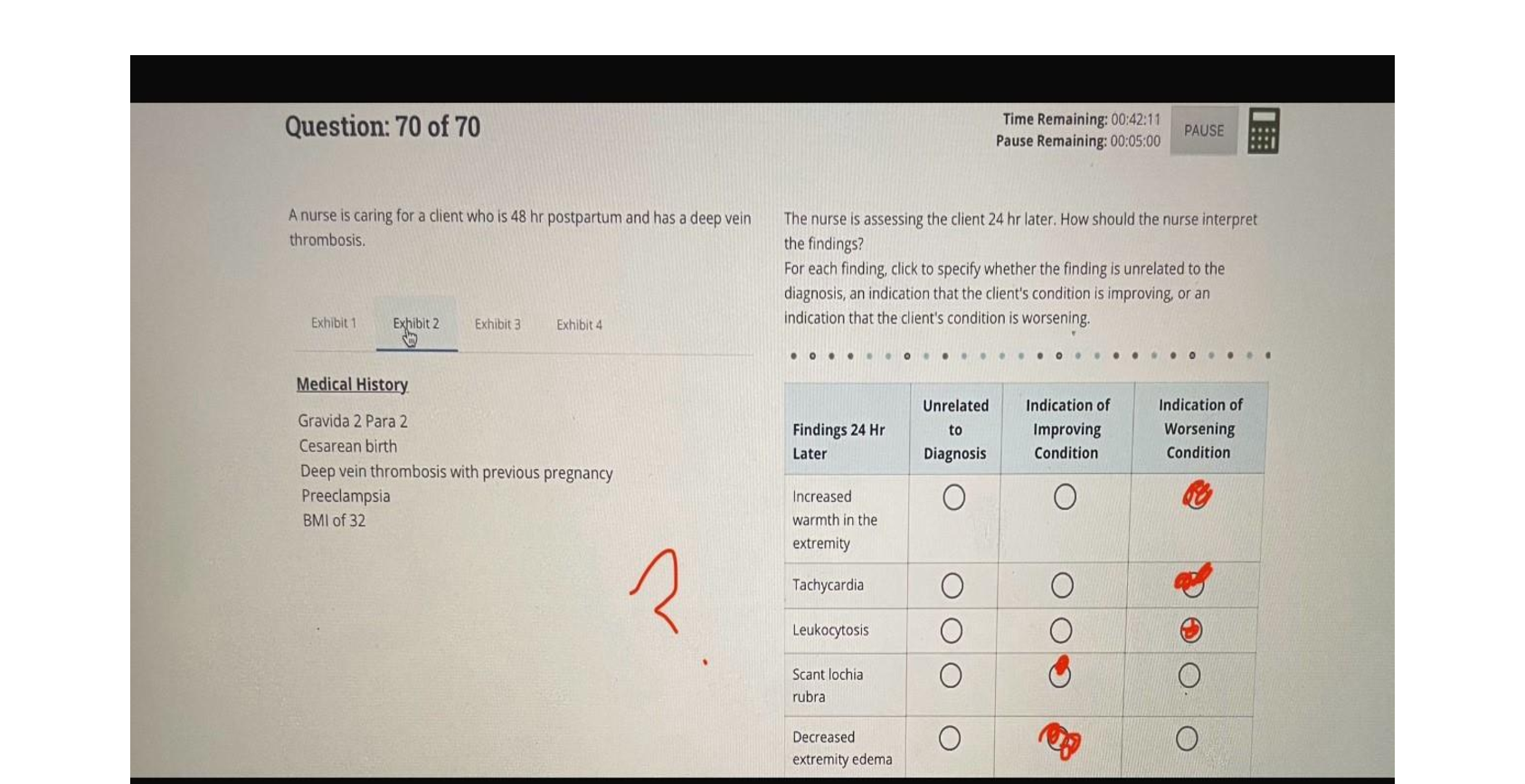
Question 1.1. An activist can best be described as which of the following? An unskilled programmer that spreads malicious scripts Consider themselves seekers of knowledge Use DoS attacks on websit ... es with which they disagree Deface websites by leaving messages for their friends to read Question 2.2. Which type of firewall policy calls for a firewall to deny all traffic by default? Permissive policy Perimeter policy Restrictive policy Demilitarized policy Question 3.3.What is a program that appears to do something useful but is actually malware? Virus Logic bomb Trojan Back door Question 4.4.In which form of authentication does the authenticating device generate a random code and send it to the user who wants to be authenticated? Basic [Show More]
Last updated: 3 years ago
Preview 1 out of 4 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$13.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
May 03, 2022
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
May 03, 2022
Downloads
0
Views
57