Question 1. 1. (TCO 1) Information security is a process that protects all of the following except _____.
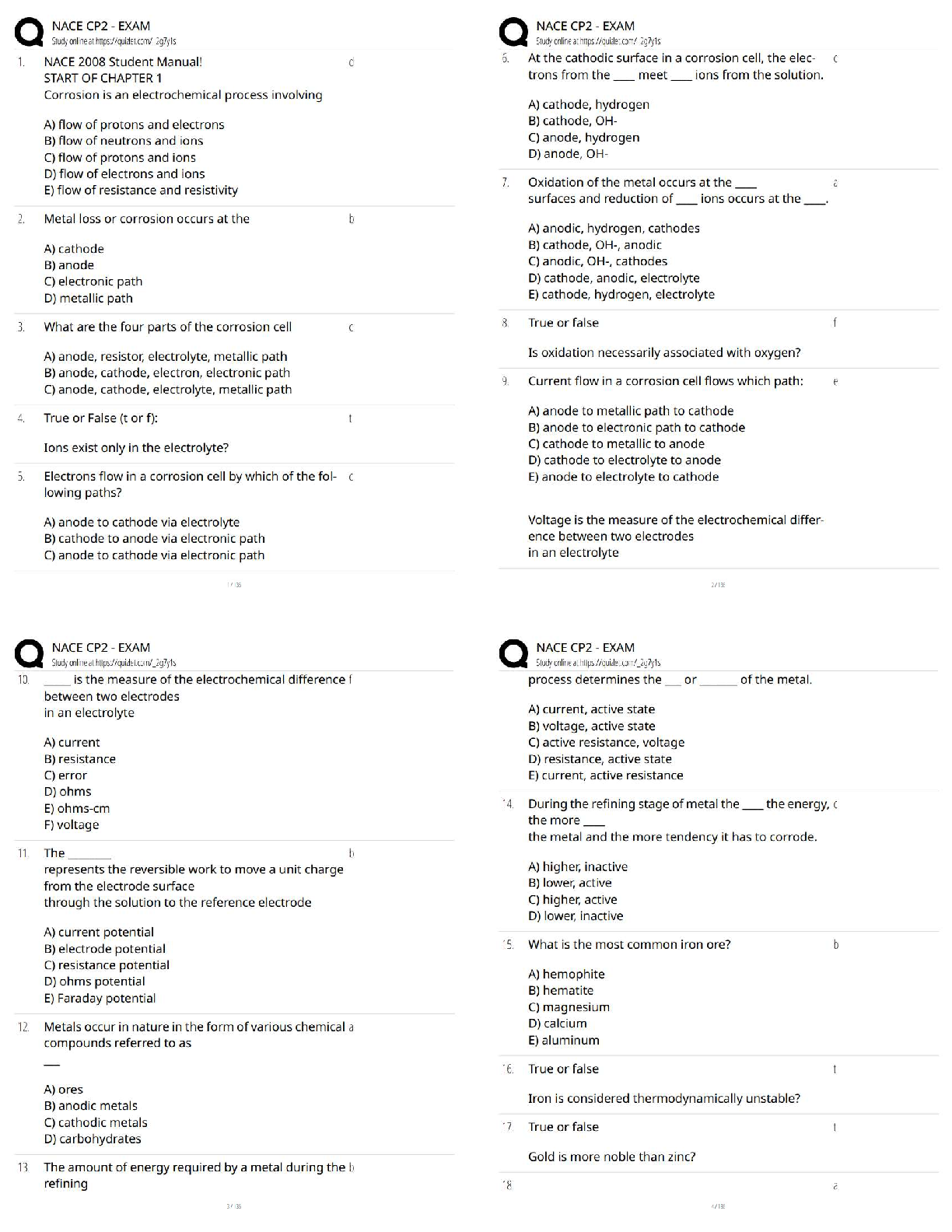
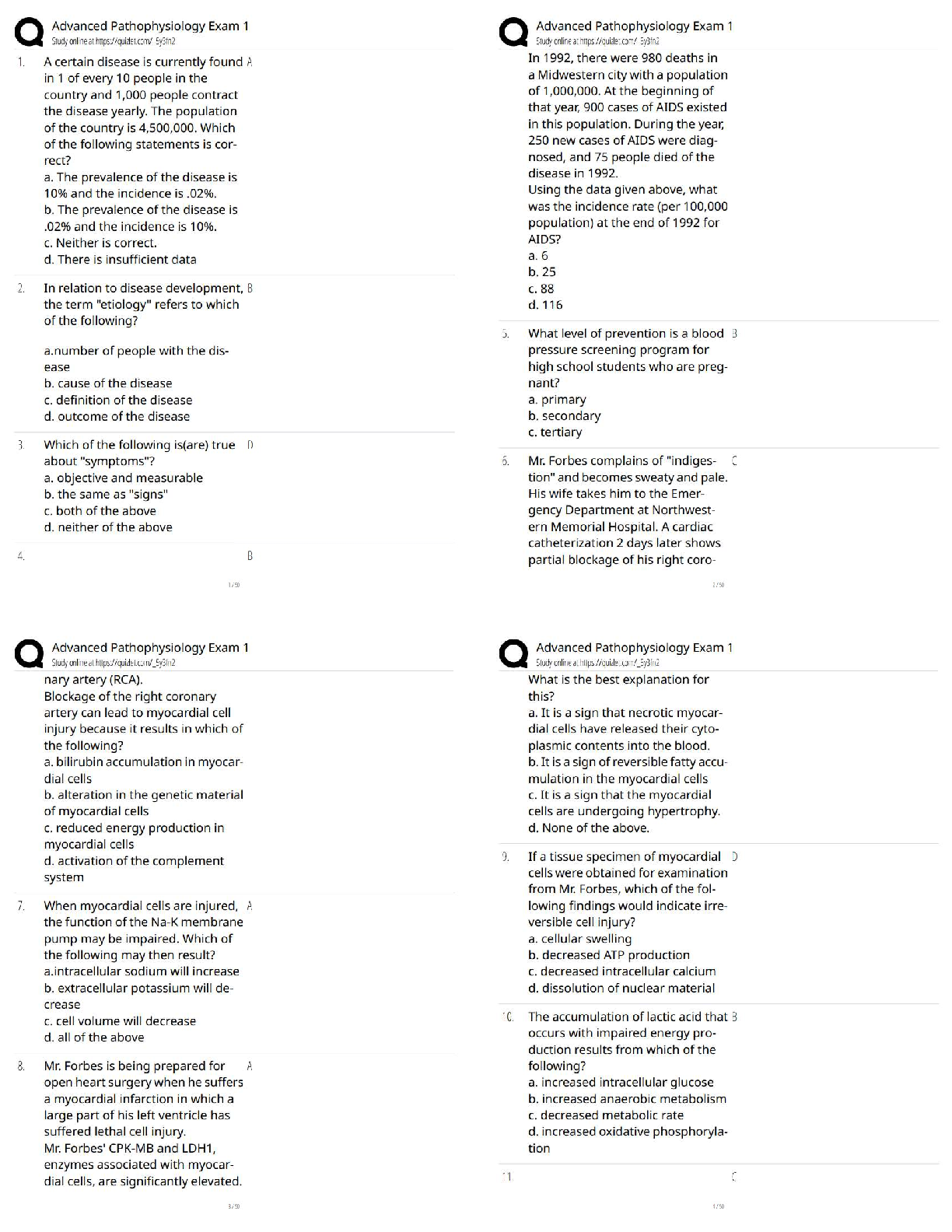
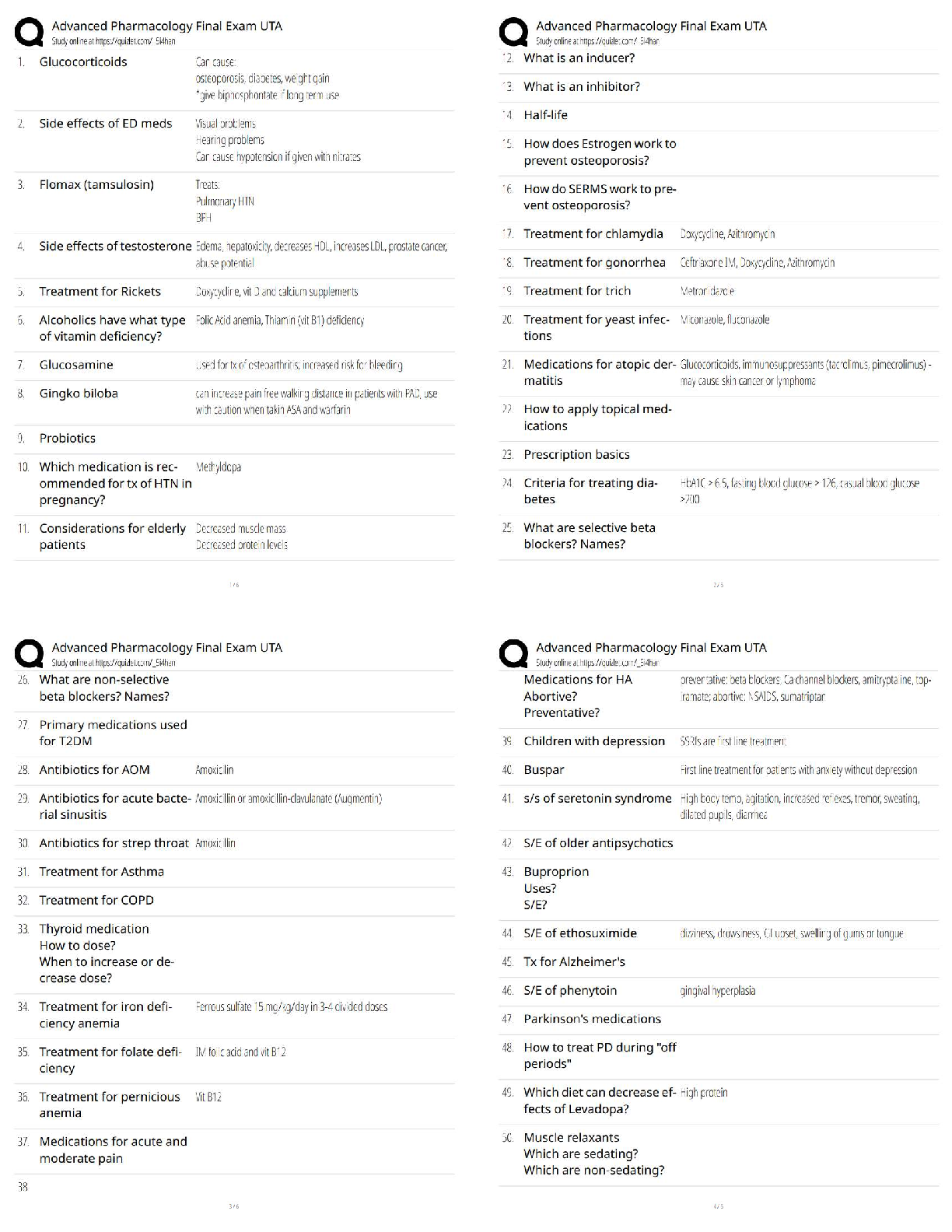
(Points : 5)
personal privacy
payroll integrity
service availability
readiness
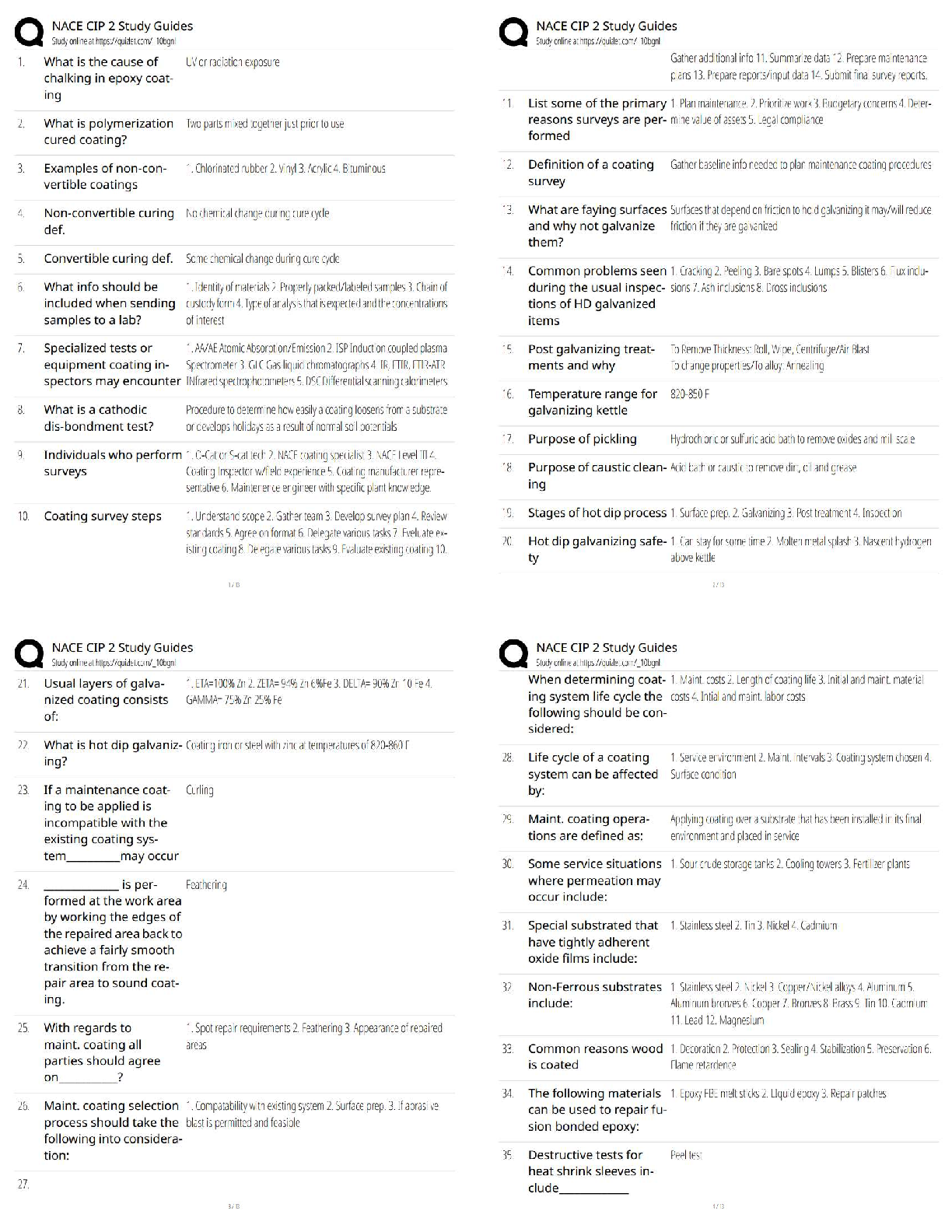
hardware integrity
answer:-
...
Question 1. 1. (TCO 1) Information security is a process that protects all of the following except _____.
(Points : 5)
personal privacy
payroll integrity
service availability
readiness
hardware integrity
answer:- readiness
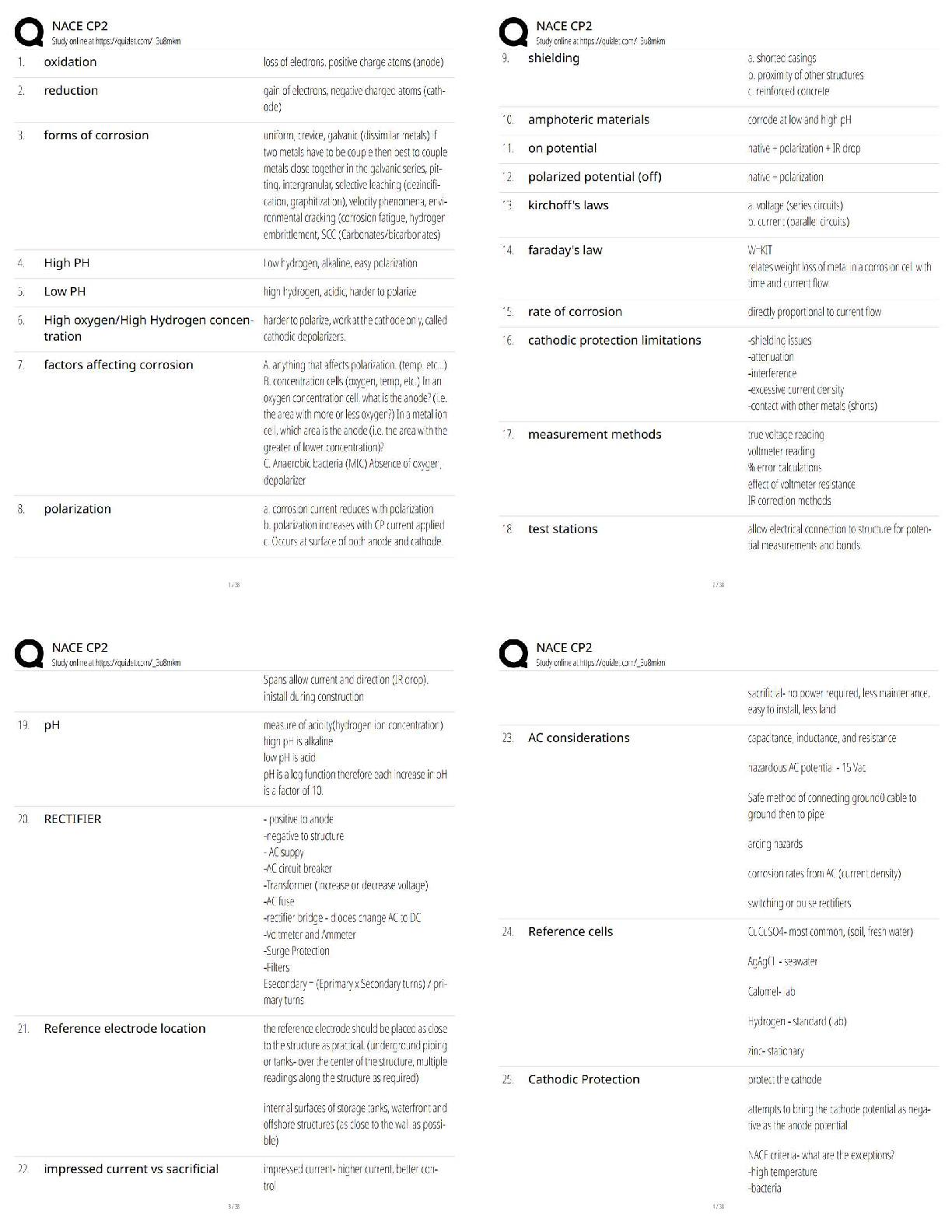
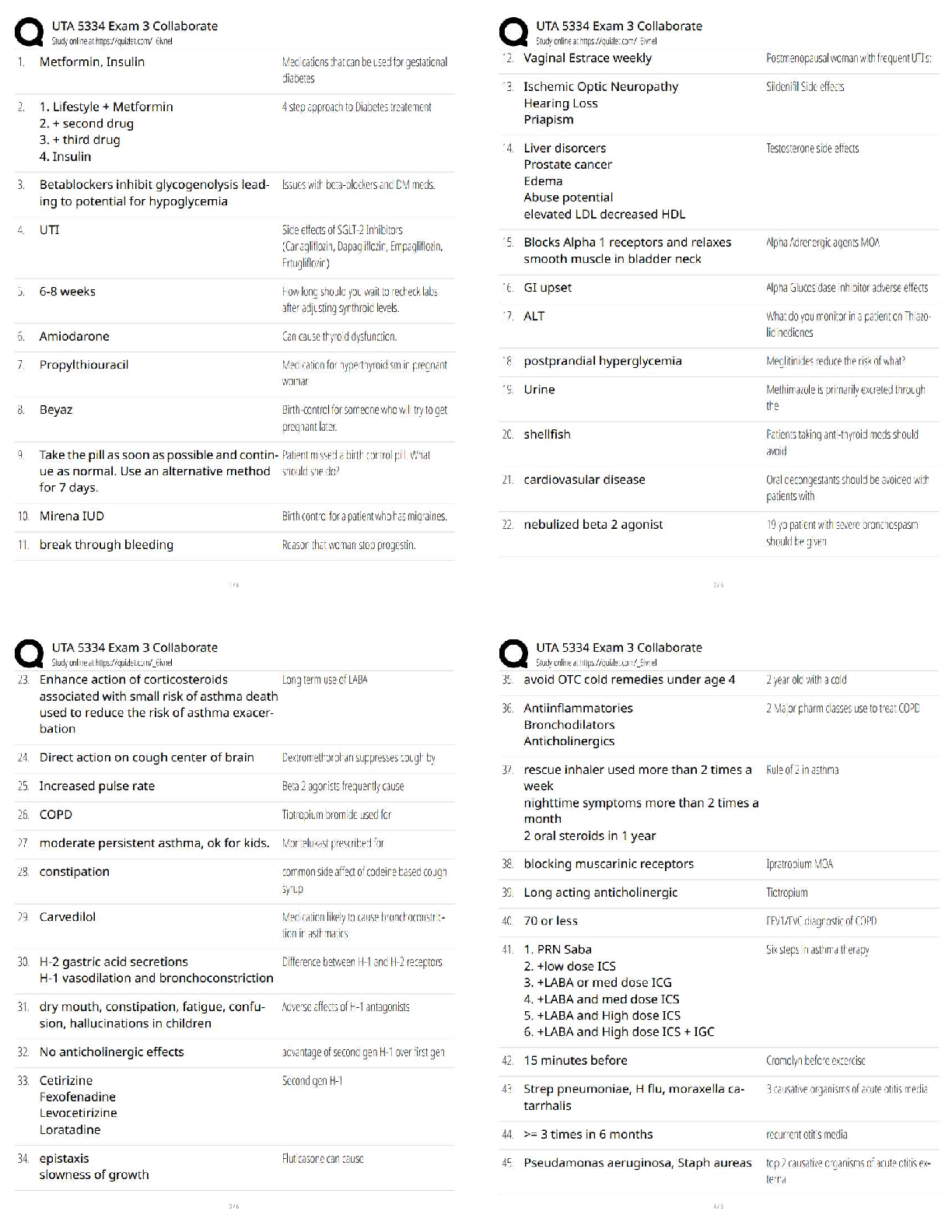
Question 2. 2. (TCO 2) The _____ of the 17 NIST control _____ can be placed into the 10
IISSCC _____ comprising the common body of knowledge for information security. (Points : 5)
technologies, domains, families
controls, families, domains
domains, families, technologies
principles, domains, families
controls, domains, principles
Answer:- controls, families, domains
Question 3. 3. (TCO 2) What are the classes of security controls? (Points : 5)
Detection, prevention, and response
Management, technical, and operational
Administrative, technical, and physical
Administrative, technical, and procedural
answer:- Detection, prevention, and response
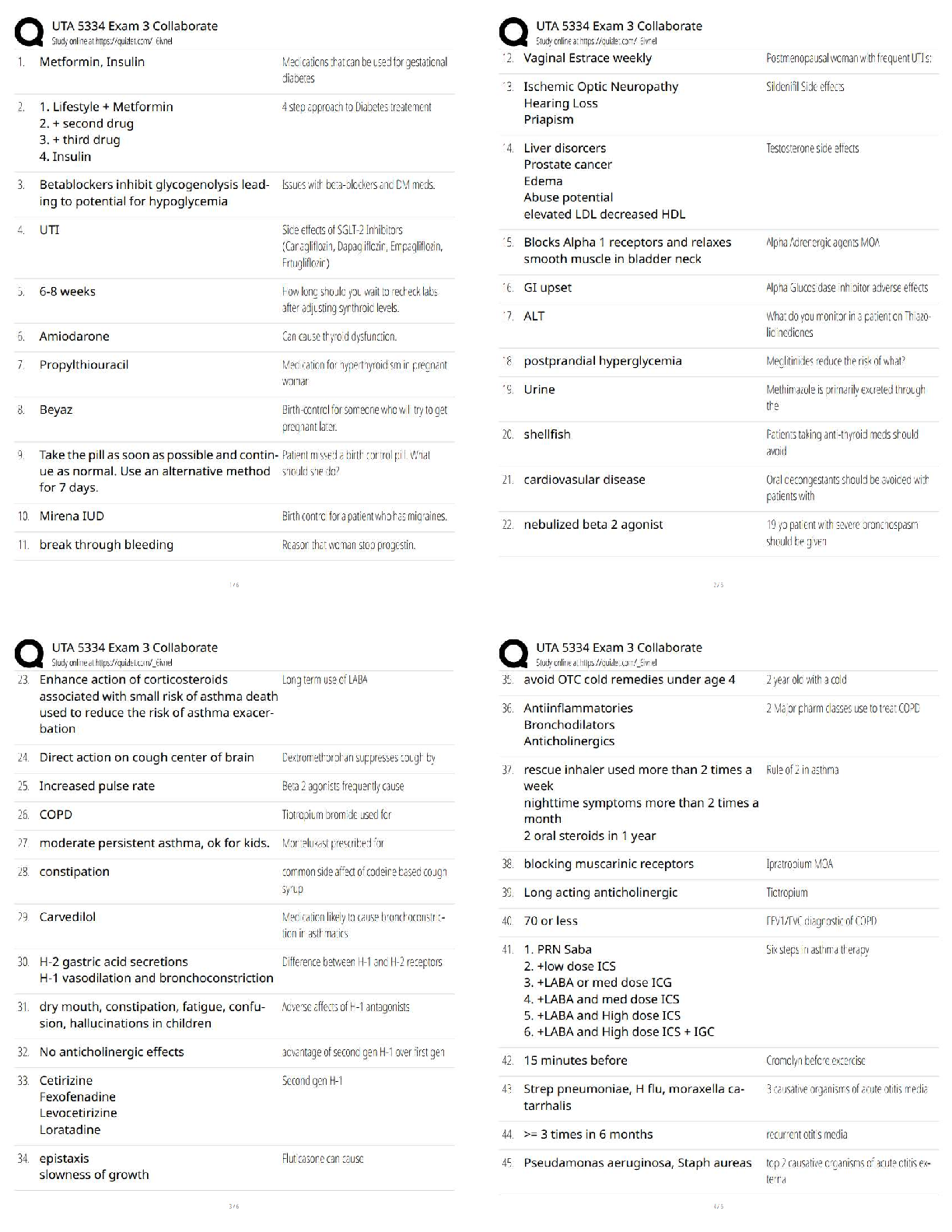
Question 4. 4. (TCO 3) Security policies, regardless of level, should ensure that _____ of assets is
distinguished, _____ of people is maintained, and that _____ is managed because that is the enemy of
security. (Points : 5)
sensitivity, separation of duties, technology
This study source was downloaded by 100000831988016 from CourseHero.com on 05-09-2022 15:38:46 GMT -05:00
https://www.coursehero.com/file/14106684/devry-security-and-privacy-360-exam-solution/
labels, responsibility, complexity
labels, accountability, technology
organization, accountability, complexity
sensitivity, separation of duties, complexity
answer:- sensitivity, separation of duties, technology
Question 5. 5. (TCO 4) Privacy legislation is written to protect _____. (Points : 5)
companies
managers
citizens
employees
All of the above
answer:_ All of the above
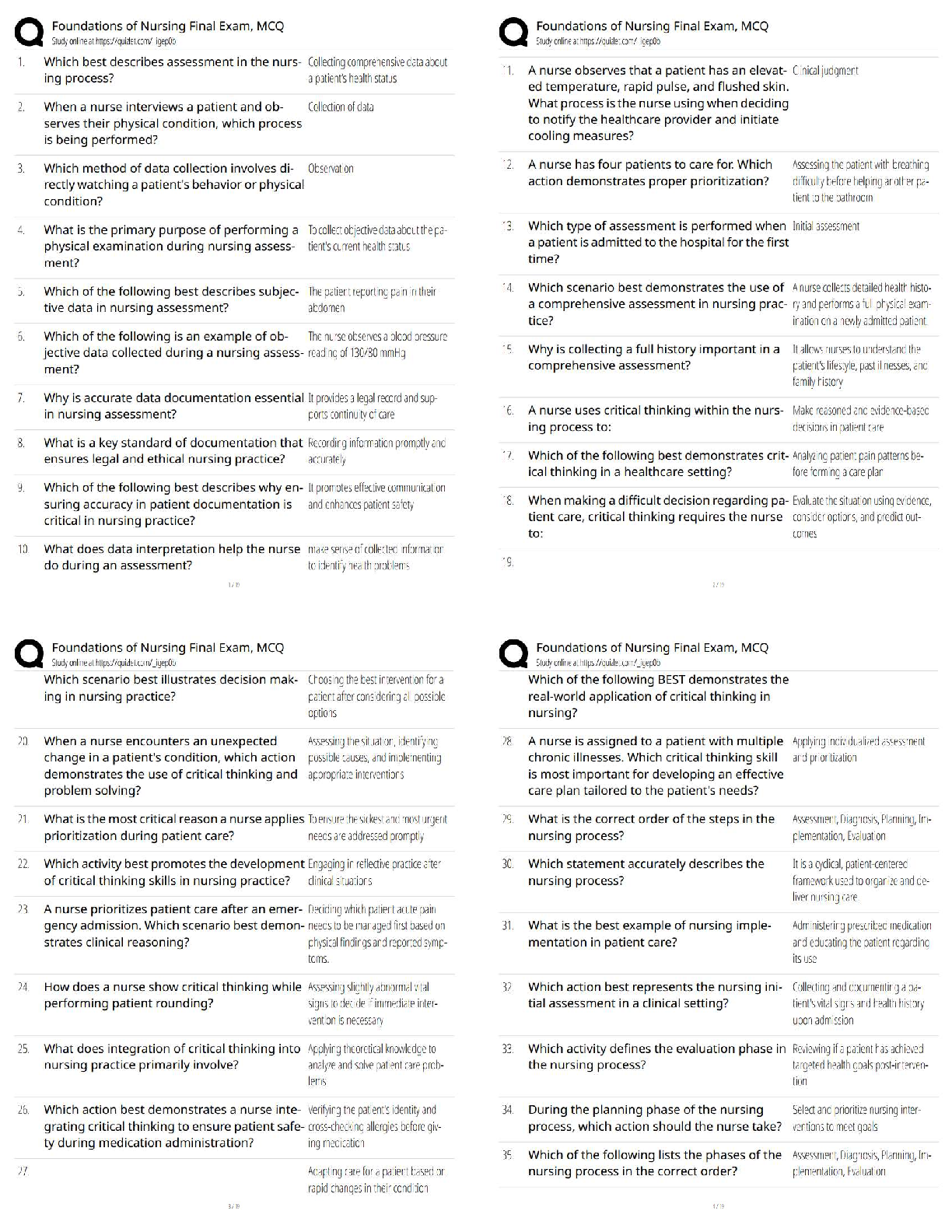
Question 6. 6. (TCO 5) Ideas can be evaluated using _____, which are _____ that are not meant to be
_____. (Points : 5)
models, controls, solutions
controls, abstractions, solutions
models, abstractions, solutions
solutions, controls, abstractions
models, controls, abstractions
answer:- models, abstractions, solutions
Question 7. 7. (TCO 6) Many believe that the most important physical security control is _____.
(Points : 5)
closed-circuit television
a good security plan
an educated workforce
This study source was downloaded by 100000831988016 from CourseHero.com on 05-09-2022 15:38:46 GMT -05:00
https://www.coursehero.com/file/14106684/devry-security-and-privacy-360-exam-solution/
certified security staff
resources
answer:- an educated workforce
Question 8. 8. (TCO 7) The security principle that says that each user should have access to exactly
the information resources needed to do his/her job--no more and no less--is called _____. (Points : 5)
separation of duties
need to know
least privilege
minimal access
least common mechanism
answer:- least privilege
Question 9. 9. (TCO 8) Security recovery strategies should always seek to restore _____. (Points : 5)
system files
application data
user access
networks supporting the IT infrastructure
the known good state
answer:- user access
Question 10. 10. (TCO 9) Access controls manage the use of _____ by _____ in an information
system. (Points : 5)
files, people
information resources, programs
objects, subjects
computer time, people
computer cycles, applications
answer:- files, people
This study source was downloaded by 100000831988016 from CourseHero.com on 05-09-2022 15:38:46 GMT -05:00
https://www.coursehero.com/file/14106684/devry-security-and-privacy-360-exam-solution/
Question 11. 11. (TCO 10) As a generalization, symmetric cryptography is used to encrypt _____, and
asymmetric cryptography is used to encrypt _____. (Points : 5)
messages, identities
data, identities
data, signatures
data, messages
messages, signatures
answer:- data, signatures
Question 12. 12. (TCO 10) In a given city, there are a group of people who wish to communicate
through the use of asymmetric cryptography. They do not wish to work with any type of certificate
authority. Given this information, how would this be accomplished? (Points : 5)
Internal certificate authority
Private extranet
Public VPN provider
IPSec tunnels
Utilize PGP
answer:- Private extranet
Question 13. 13. (TCO 11) A
[Show More]












.png)