IT330 Final Exam
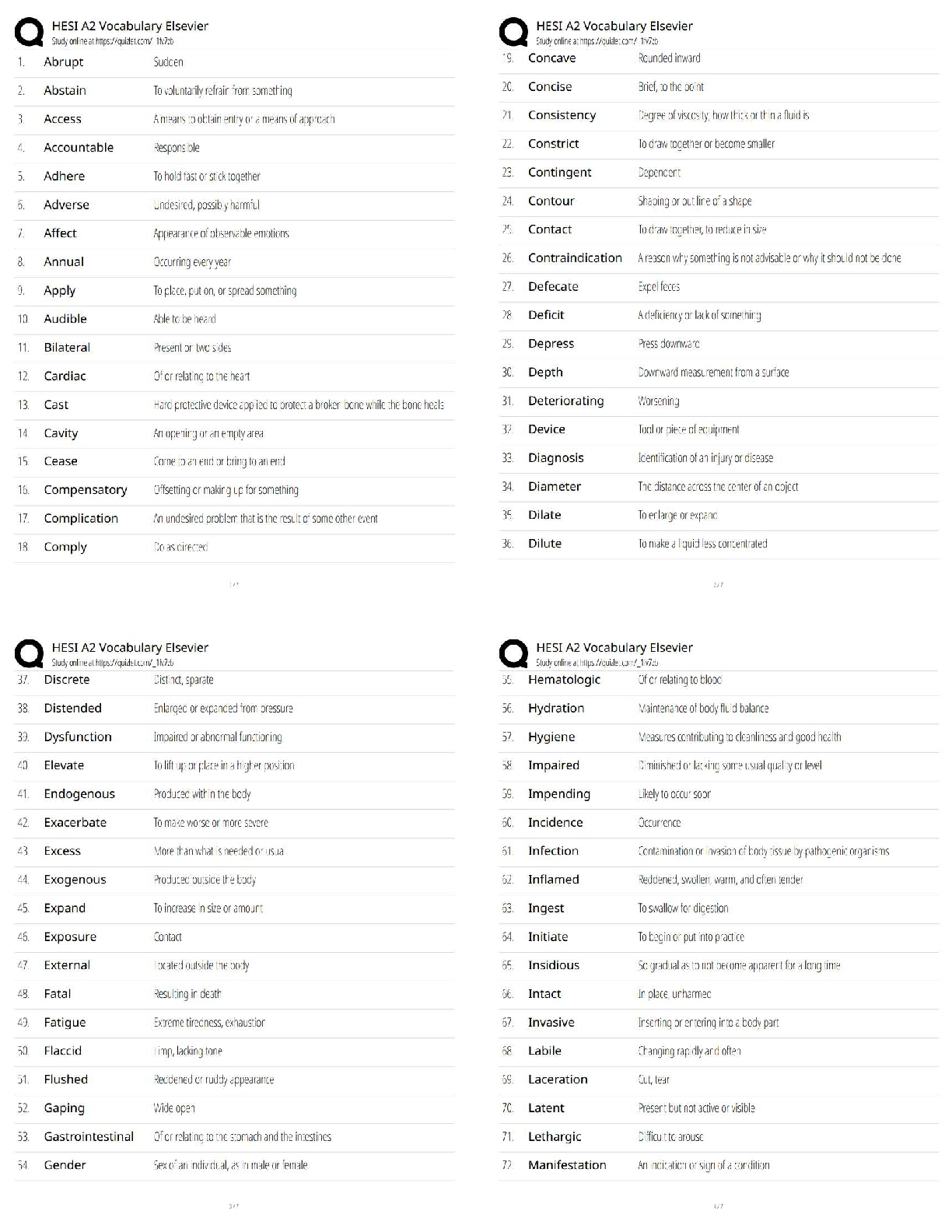
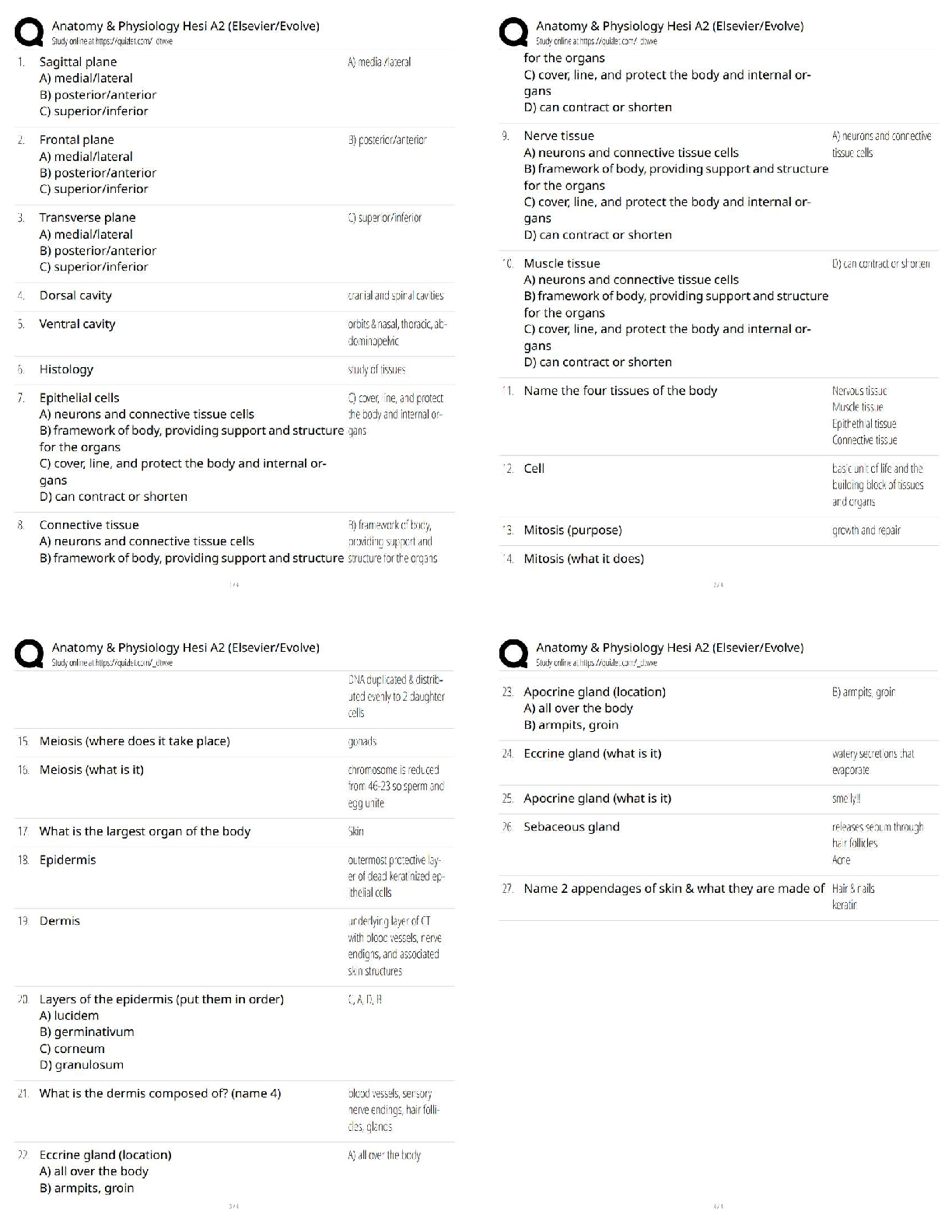
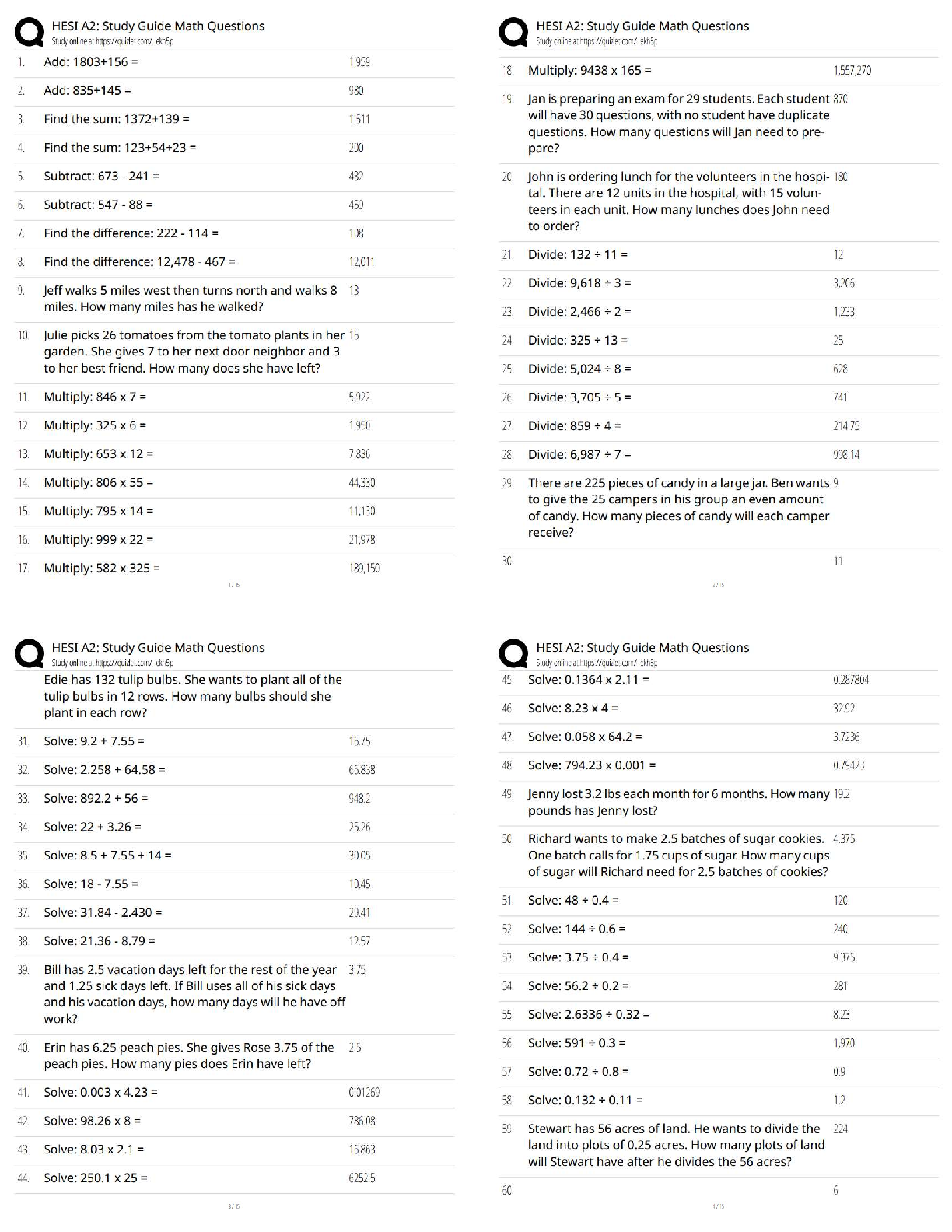
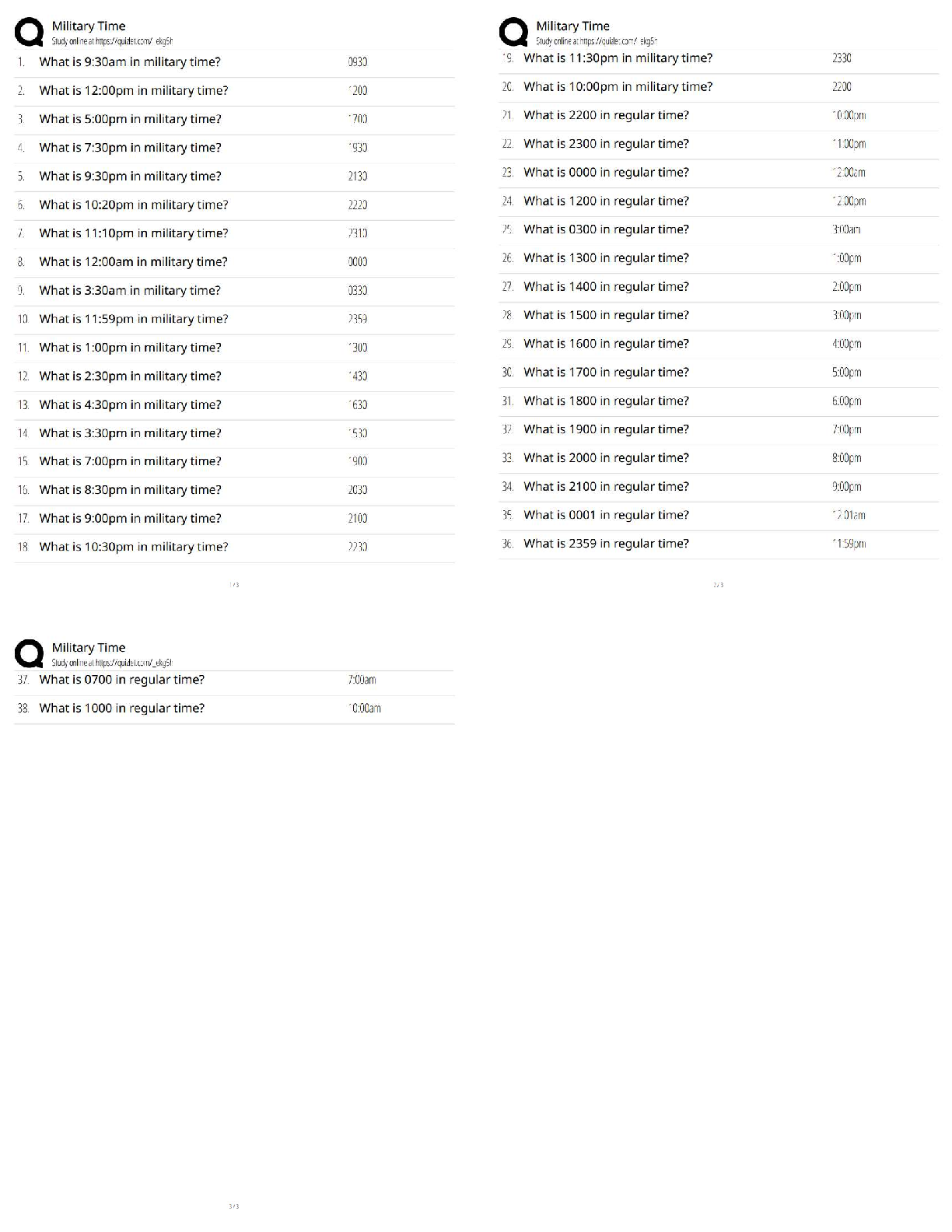
All of the following are typical RACF security services, except?
A. Identifies logon users via a USERID and password
B. Each RACF USERID has a unique password
C. Password is one way encrypted so no o
...
IT330 Final Exam
All of the following are typical RACF security services, except?
A. Identifies logon users via a USERID and password
B. Each RACF USERID has a unique password
C. Password is one way encrypted so no one else can get your password, not even the
administrator
D. Prevents connections from outside the network to access sensitive applications -
firewall.
E. A USERID is revoked after a preset number of invalid password attempts - ✔✔D
In RACF, a _____________ describes the security characteristics of a user, a group, or
resource.
A. user account
B. security entry
C. profile
D. SAF - ✔✔C
In order for a resource to be RACF-protected, it must
A. have a RACF profile
B. have a password
C. limit access to local connections
D. define users and groups who may access the resource - ✔✔A
The security role which is responsible for reviewing security policy, violation and
exposures is ______.
A. Security administrator
B. Security auditor
C. System operator
D. Systems programmer
E. System Administrator - ✔✔B
Which of the following statements BEST describes z/OS's storage protection function?
A. Limit access to sensitive datasets and libraries to authorized users and programs.
B. Prevents unauthorized reading or alteration of storage
C. Protects virtual address spaces from unauthorized access or alteration.
D. Encrypts removable storage devices using the storage protection key. - ✔✔B
Which of the following statements BEST describes the concept of "console security"?
A. Specifies which z/OS commands operators can execute at a designated console.
B. Specifies z/OS USERIDS may login to a designated console.
C. Specifies groups and userids that logon to a designated console.
D. Specifies the time of day one may logon to a designated console.
E. All of answers are correct. - ✔✔A
Which of the following is NOT an example of a RACF protected resource?
A. datasets and tapes
B. JES or TSO
C. IMS or CICS transactions
D. Console and system commands
E. Users and groups - ✔✔E
A security policy should ______.
A. determine which RACF functions to use
B. identify the level of RACF protection
C. identify which data to protect
D. identify administrative structures and users
E. include all of the presented options - ✔✔E
Concerning the security of application programs, which of the following statements is
FALSE?
A. Application programs may or may not be stored in an APF-library
B. Application programs are normally executed in problem state.
C. Application programs normally use a storage protection key between 0 and 7.
D. Applications programs are normally developed by IBM customers or third-parties. -
✔✔C
z/OS directly provides all of the following security and integrity controls beyond facilities
provided by the IBM Security Server or RACF, except?
A. Authorized Program Facility
B. Storage Protection
C. Cross-memory communication
D. MS Windows Firewall Technologies - ✔✔D
Which of the following statements concerning z/OS's storage protection is FALSE?
A. Information for each 4 KB page of real storage is protected from unauthorized use by
means of multiple storage protection keys.
B. Storage protection keys are used to encrypt the contents of real memory to prevent
un-authorized system or user programs from reading the contents of the page.
C. z/OS uses 16 storage protection keys.A specific key is assigned according to the
type of work being performed.
D. Storage protection keys 0 (the Master key) through 7 are used by the z/OS base
control program (BCP) and various subsystems and middleware products. If the
requestor key match between the requesting program and the BCP program the
requestor will be granted fetch access.
E. Storage protection keys 8 through 15 are assigned to user program, which are
isolated in private address spaces. - ✔✔B
Resource Access Control Facility (RACF) is a part of _______?
A. IBM Security Server
B. z/OS
C. System Authorization Facility (SAF)
D. Authorized Program Facility (APF)
E. TSO/E - ✔✔A
Concerning the security policies recommended for systems programs, which of the
following statements is FALSE?
A. System programs are normally stored in a RACF security database.
B. System programs are normally executed in supervisor state.
C. System programs normally use a storage protection key between 0 and 7.
D. System programs are normally provided by IBM-supplied or authorized third-parties.
- ✔✔A
The security concept which ensures that individuals don't have conflicting
responsibilities or are responsible for reporting on themselves or their superior is called
______?
A. security role management
B. authentication policies
C. separation of duties
D. enterprise identity mapping
E. RACF - ✔✔C
Which of the following statements BEST describes the concept of a "Problem State"?
A. It is normally any user program that is executed with a storage protection key of 0.
B. It is normally any program that users may access remotely.
C. It is normally any program that may be executed without a USERID.
D. It is normally any user program that is executed with storage protection key of 8. -
✔✔D
A hardcopy document or electronic set of security rules that are used to guide or
implement security is called a ________?
A. security policy
B. password restrictions
C. RACF profile
D. security provisioning - ✔✔A
Which of the following statements BEST describes z/OS's Authorized Program Facility
(APF)?
A. Ability to assign security permissions to authorized users .
B. Ability to identify system or user programs that can use sensitive system functions.
C. Ability to create ISPF panels to provide menu access for authorized users to
sensitive security tools.
D. Ability for authorized users to configure authentication and authorization.
E. All of the statements are TRUE. - ✔✔B
RACF can be configured to write to a security log when it detects _______?
A. Unauthorized attempts to enter the system
B. Access to resources
C. Issuing RACF commands
D. Any of the listed events. - ✔✔D
Which of the following statements concerning z/OS's cross-memory communication
protection is TRUE?
A. Cross-memory communication allows a program in one address space to
communicate with a program in another address space.
B. While storage protection keys and page protection bits are used to provide real
memory protection from other application's access, it does not protect communication
between programs, e.g., a program call.
C. Middleware products, e.g., DB2, often must communicate with other middleware
products and z/OS functions, e.g., TSO, Websphere Application server, JES, etc.
Cross-memory communication provides a means to pass control and data between
these systems.
D. Routine application programs seldom use cross-memory communication and are
adequately protected by z/OS.
E. All of the statements are TRUE - ✔✔E
ALLOC, CONTROL, WRITE, READ, and NONE are examples of which RACF concept?
A. RACF profiles
B. RACF permissions
C. RACF resource classes
D. RACF CONSOLE authority or command levels - ✔✔B
Which of the following statements concerning z/OS's Authorized Program Facility (APF)
is TRUE?
A. Ability to identity libraries which contain load modules which can access sensitive
system functions.
B. Restrict the use of sensitive system supervisor call (SVC) to APF-authorized
programs.
C. Prevent programs from counterfeiting a module in the module flow of an authorized
job step task.
D. Default APF-sensitive libraries include SYS1.LINKLIB, SYS1.SVCLIB, and
SYS1.LPALIB
E. All of the answers are TRUE. - ✔✔E
The security role which designs, plans an
[Show More]