WGU Master's Course C726 -
Cybersecurity Architecture and
Engineering
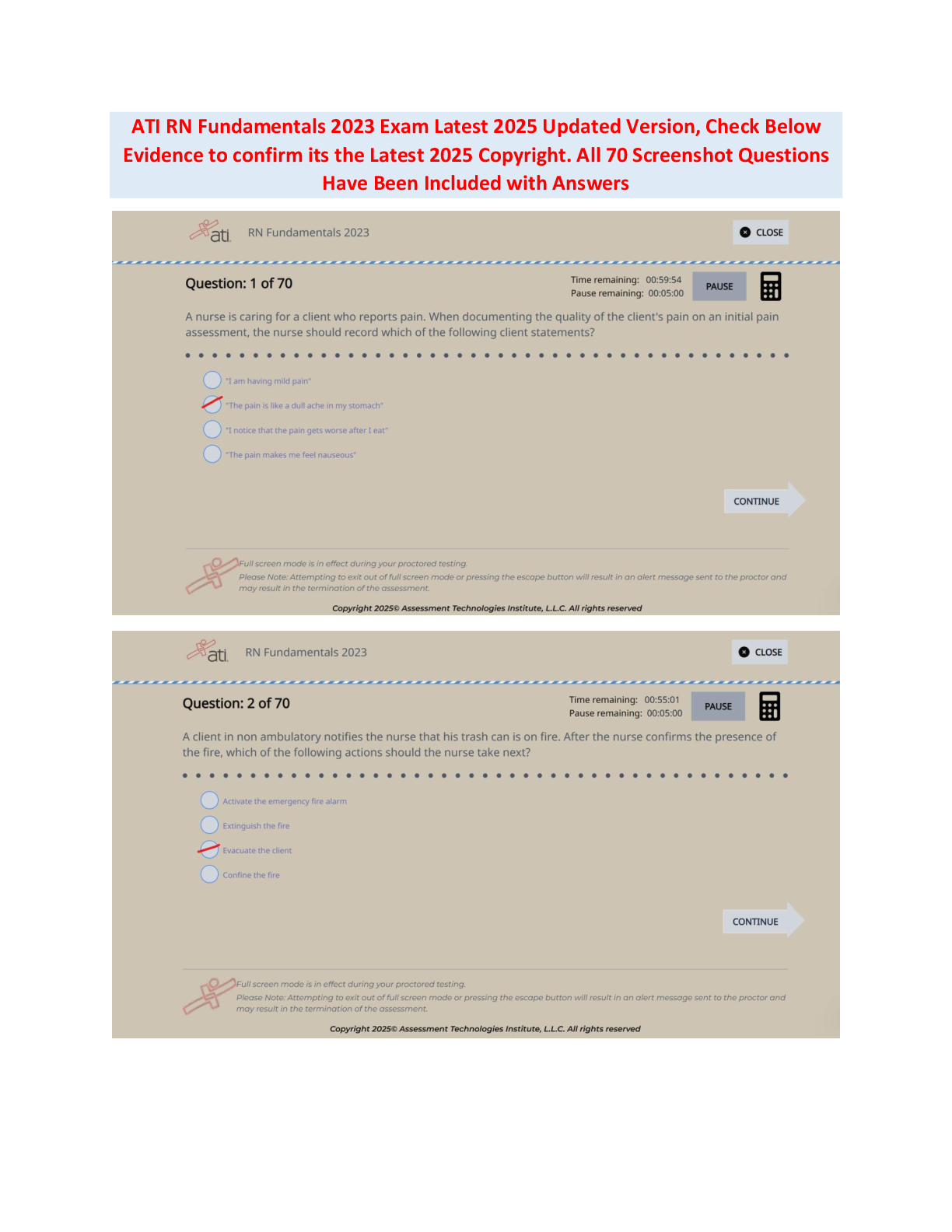
Which Orange Book level is considered mandatory protections and is based on the BellLaPadula security model?
A A
B C
C D
D B - ✔✔D
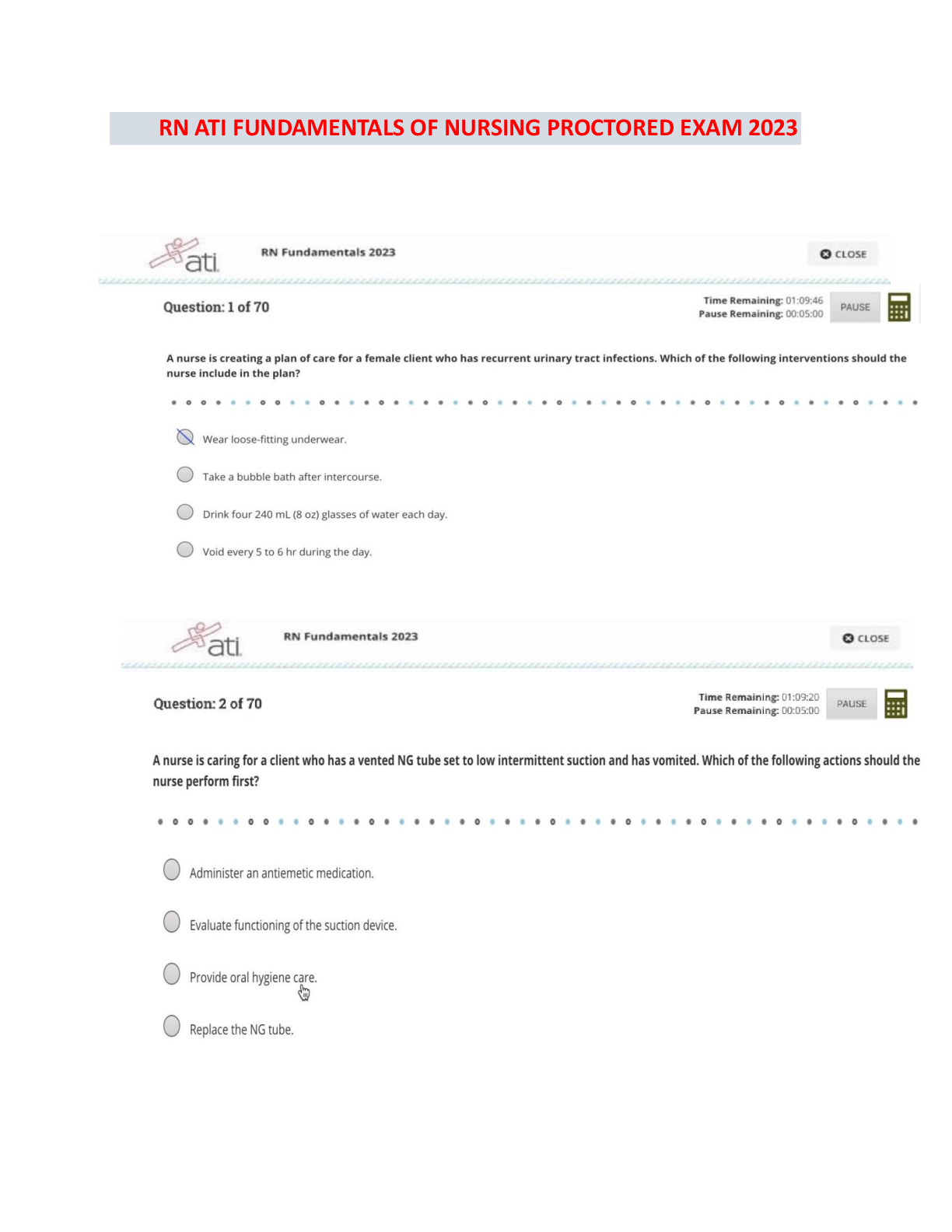
During an X
...
WGU Master's Course C726 -
Cybersecurity Architecture and
Engineering
Which Orange Book level is considered mandatory protections and is based on the BellLaPadula security model?
A A
B C
C D
D B - ✔✔D
During an XOR operation, two bits are combined. Both values are the same.
What will be the result of this combination?
A 1
B 0
C OR
D X - ✔✔B
Which section of the Minimum Security Requirements for Multi-User Operating System
(NISTIR 5153) document addresses end-to-end user accountability?
A access control
B audit
C data integrity
D system integrity - ✔✔B
Which encryption algorithm is based on the Diffie-Hellman key agreement?
A Knapsack
B International Data Encryption Algorithm
C El Gamal
D HAVAL - ✔✔C
What is meant by the term fail-safe?
A system's ability to switch over to a backup system in the event of a failure
B system's ability to preserve a secure state before and after failure
C system's ability to recover automatically through a reboot
D system's ability to terminate processes when a failure is identified - ✔✔DYou need to store some magnetic storage devices in a temporary storage facility.
At which temperature could damage start to occur?
A 350 degrees Fahrenheit
B 100 degrees Fahrenheit
C 90 degrees Fahrenheit
D 175 degrees Fahrenheit - ✔✔B
You need to decrypt a file that is encrypted using asymmetric encryption.
What should be used to decrypt the file?
A public key
B plaintext
C message digest
D private key - ✔✔D
Which statement is true of the Rijndael algorithm?
A Rijndael uses variable block lengths and variable key lengths.
B Rijndael uses fixed block lengths and fixed key lengths.
C Rijndael uses variable block lengths and fixed key lengths.
D Rijndael uses fixed block lengths and variable key lengths. - ✔✔A
You are responsible for managing the virtual computers on your network.
Which guideline is important when managing virtual computers?
A Update the operating system and applications only on the host computer.
B Implement a firewall only on the host computer.
C Install and update the antivirus program only on the host computer.
D Isolate the host computer and each virtual computer from each other. - ✔✔D
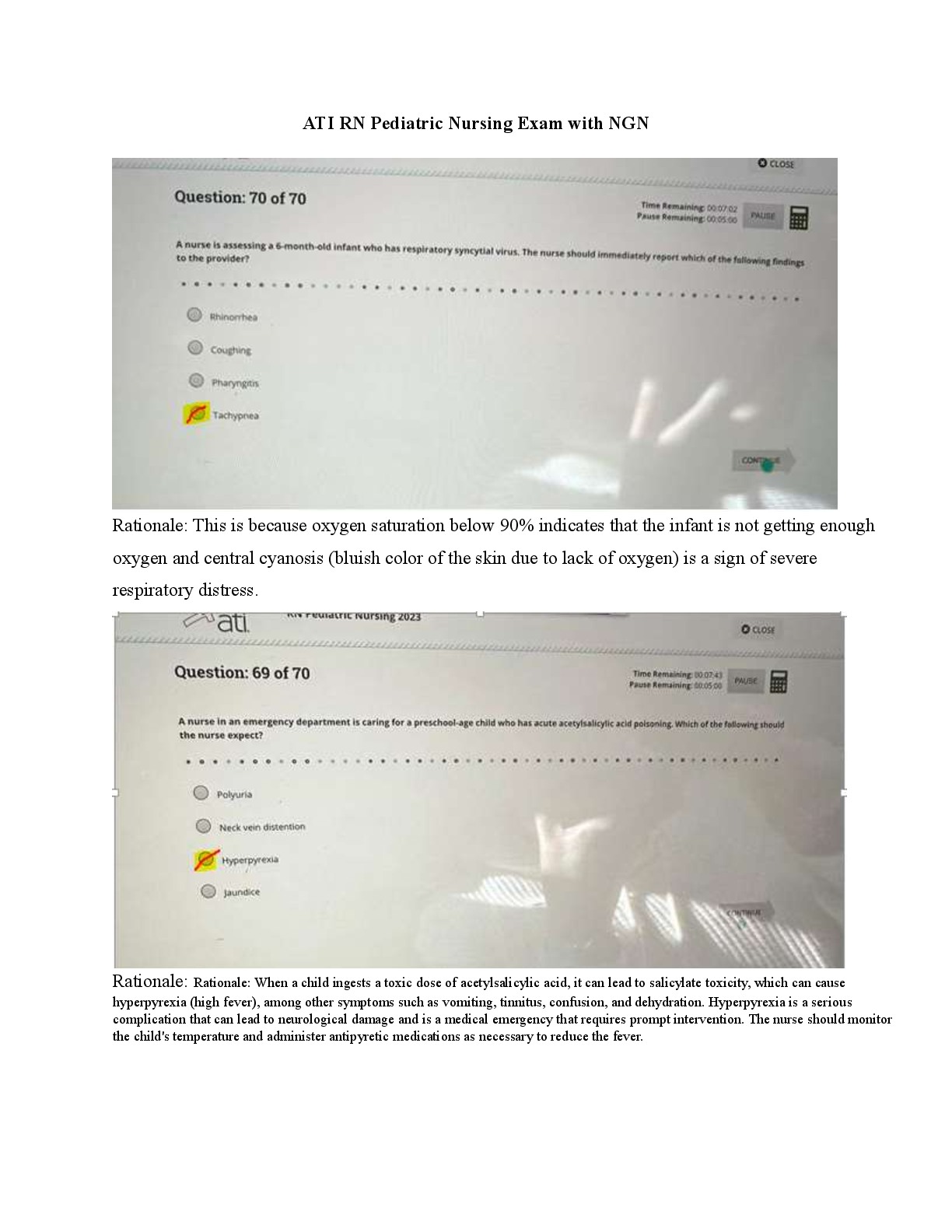
Given two messages, M1 and M2, what is the LEAST likely outcome when using the
same one-way hash function, H, to encrypt the messages?
A H(M1) = H(M2)
B H(M1) is not equal to H(M2)
C H(M1) > H(M2)
D H(M1) < H(M2) - ✔✔A
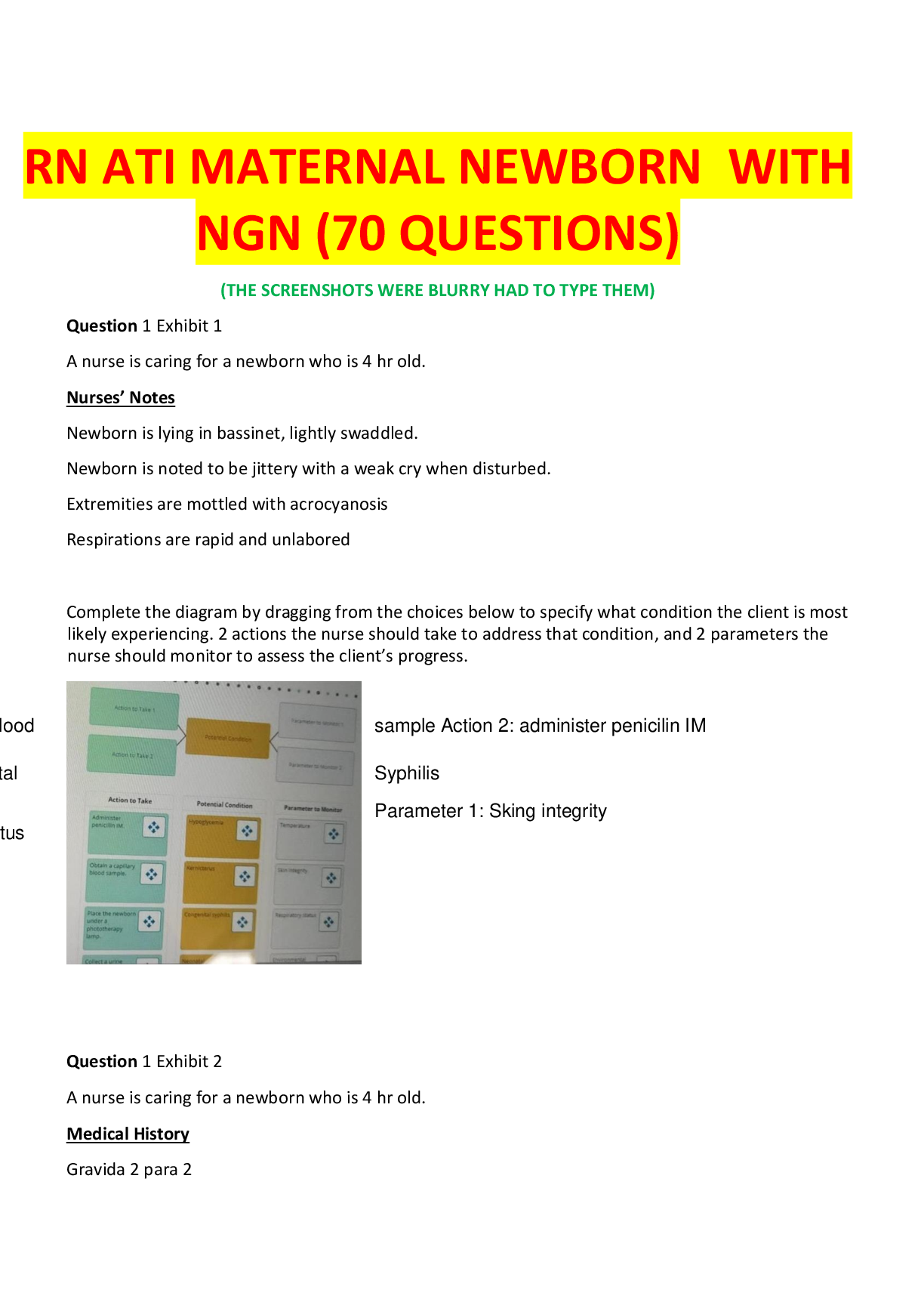
Your organization has decided to implement the Diffie-Hellman asymmetric algorithm.
Which statement is true of this algorithm's key exchange?A Authorized users exchange public keys over a secure medium.
B Unauthorized users exchange public keys over a nonsecure medium.
C Authorized users exchange secret keys over a nonsecure medium.
D Authorized users need not exchange secret keys. - ✔✔C
[Show More]









.png)
.png)