Computer Networking > EXAM > Ethical Hacking Final Exam (University of Maryland, College Park CMIT 350). 0ver 180 Q&A (All)
Ethical Hacking Final Exam (University of Maryland, College Park CMIT 350). 0ver 180 Q&A
Document Content and Description Below
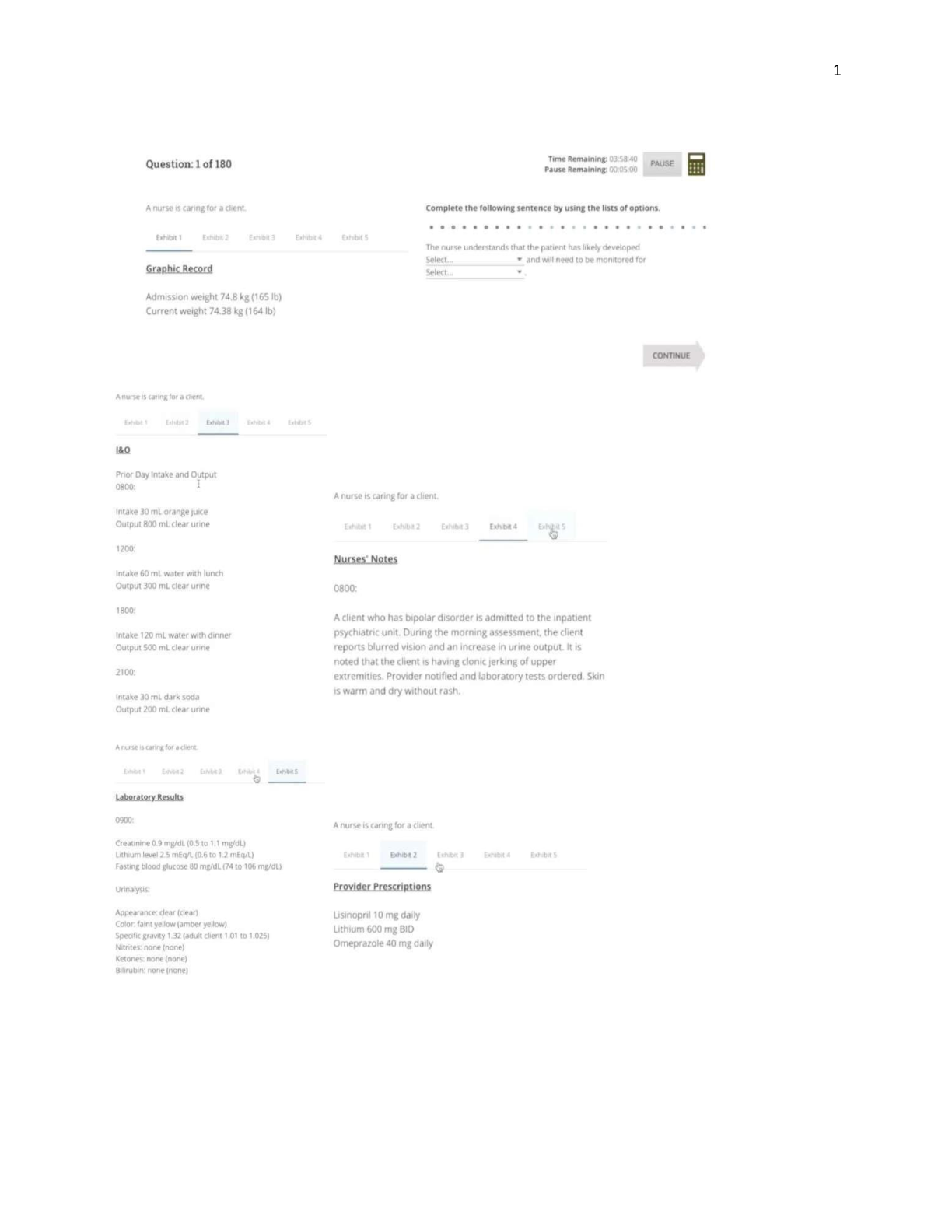
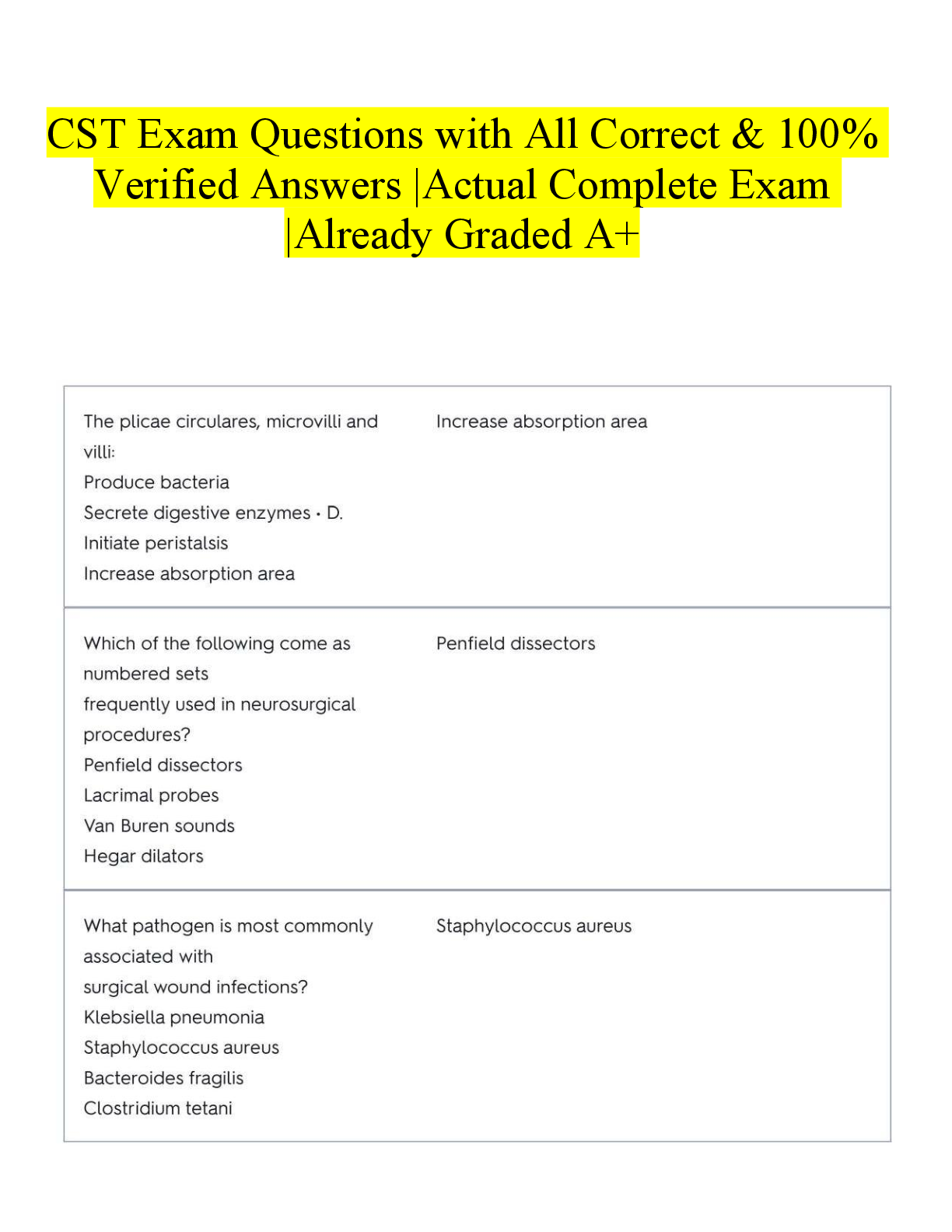
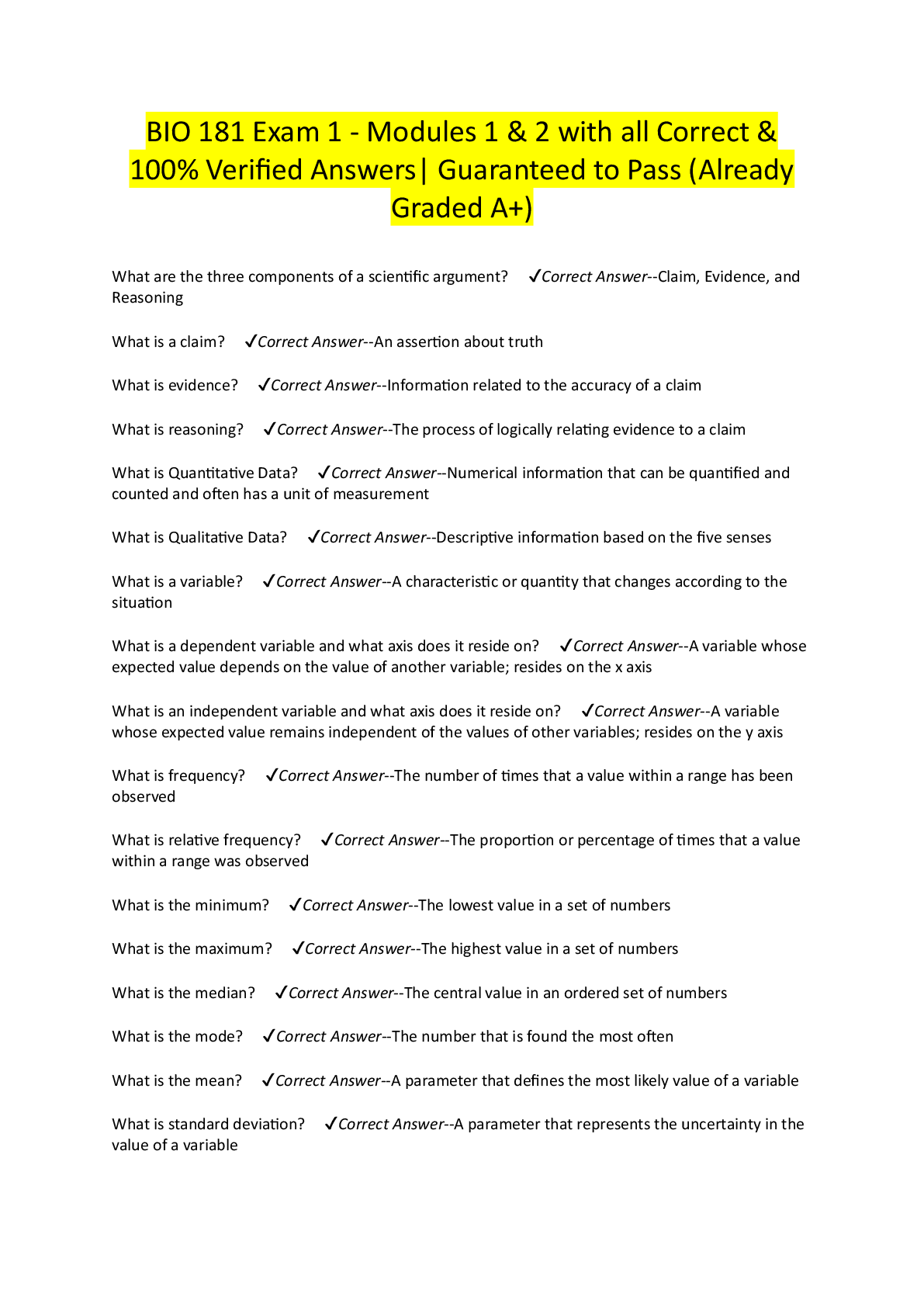
Ethical Hacking Final Exam Question 0. This vulnerability scanner is from Microsoft: Question options: Nessus Core Impact Cloud Scan MBSA Question 1 _________ is a command-line tool that is b ... undled with both Windows and UNIX operating systems and is used for querying DNS information. Question 1 options: Whois Traceroute Netstat Nslookup Question 2 Which type of information cannot be found in a resource record (RR)? Question 2 options: MX ARP PTR SOA Question 3 _________________ is a network scanning technique used to discover which range of IP addresses map to live computers.Question 3 options: Port scanning Ping sweep Probe scanning Fingerprinting Question 4 An attacker is interested in discovering ports that might be open on a target system. The attacker decides to port scan the IP address of the system but also wants to make the scan as stealthy as possible. Which of the following techniques would be the best choice in this scenario? Question 4 options: TCP connect scan SYN scan ICMP echo scan List scan Question 5 During the Reconnaissance Phase of an attack, the attacker may resort to looking through an organization’s trash for discarded sensitive information. This technique is known as ________________. Question 5 options: social engineering breaking and entering dumpster diving passive reconnaissance Question 6 Which of the following are objectives of scanning? (Select all that apply.) Question 6 options: a) b) c) d) To discover live hosts, IP address, and open ports of live hostsTo discover operating systems and system architecture To discover services running on hosts To discover vulnerabilities in live hosts Question 7 The Simple Service Discovery Protocol (SSDP) will (choose 3): Question 7 options: Not work behind a firewall Can be vulnerable to denial of service Uses multicast addresses Controls Communication for the Universal Plug and Play Service Save Question 8 Which port scanning method is considered the most reliable in terms of accurately reporting port status on a target system? Question 8 options: TCP connect() scan SYN scan ACK scan XMAS scan Question 9 The following tools are used for footprining (choose 3): Question 9 options: Recong-ng Aircrack-ng Maltego FOCA Question 10_______________ is a spoofing technique that allows an attacker to choose the path a packet will take through the Internet. Question 10 options: SYN scanning Tracerouting Source routing HTTP tunneling Question 11 If you want to mask (or spoof your IP Address, use this type of scan: Question 11 options: IDLE, IPID Scan UDP Scan ACK Flag Probe Scan Stealth Scan Question 12 Attackers can use an ACK scan to learn the type of firewall or firewall rule sets that might be guarding a target system. Based on the packet information below, which port is considered to be filtered? Packet 1: Attackers can use an ACK scan to learn the type of firewall or firewall rule sets that might be guarding a target system. Based on the packet information below, which port is considered to be filtered? Packet 1: Server IP port 20: F: RST TTL: 68 win:0 Packet 2: Server IP port 21: F: RST TTL: 56 win:0 Packet 3: Server IP port 22: F: RST TTL: 68 win:0 Packet 4: Server IP port 23: F: RST TTL: 68 win:0 Question 12 options: 20 21 22 23Question 13 If you want to perform active banner grabbing on a target web server, which of the following tools would be most suitable? Question 13 options: Netstat Telnet Nslookup NbtStat Question 14 Which of the following Flags will indicate that there is a new sequence number: Question 14 options: ACK URG SYN PSH Save Question 15 Footprining tools will help gather the following information about a target (choose 3): Question 15 options: DNS Records Host Names IP Addresses Process Lists Save Question 16 Once an attacker gains access to a target system, he will attempt to _____________ in order to continue exploiting the system. Question 16 options:target other systems maintain access port scan fingerprint Question 17 Binging is an example of a Footprinting tool which uses __________ to perform queries: Question 17 options: .Net Framework DNS Reverse Lookups Bing API Question 18 Based on the information below, identify the type of port scan and whether the port is open or closed. CLIENT SERVER 82.27.51.100:6347 --- FIN/URG/PSH -----> 10.31.64.21:25 82.27.51.100:6347 <--- NO RESPONSE ---- 10.31.64.21:25 Question 18 options: SYN Scan, Port is closed FIN Scan, Port is closed Idle Scan, Port is open XMAS Scan, Port is open Save Question 19 You receive a number of calls from customers who cannot access your corporate website. You decide to investigate by logging in to your routers, and the logs show that network traffic is unusually high. You also notice that almost all the traffic is originating from a specific address. Using several traceroute tools to find out where the suspect IP originates from, you discover that the IP is coming from somewhere in Europe. Thinking that the network is under a denial-of-service attack, you must find out more about the originating IP address. What Internetregistry would you examine to find information about the IP address? Question 19 options: RIPE NCC APNIC ARIN LACNIC Question 20 The following can be utilized as traceroute tool: Question 20 options: nslookup TTL (Time to Live) pingpath Path Analyzer Pro Save Question 1 According to your text, components of a Cloud Broker include which of the following? (choose all that apply) Question 1 options: Service Negotiation Service Intermediation Service Aggregation Service Arbitration Question 2Select the three IP Protocols that Snort Supports for Suspicions behavior according to your text. Question 2 options: ICMP TCP UDP ARP Question 3 An Intrusion Detection System (IDS) (choose all that apply) Question 3 options: Monitors inbound traffic Will perform actions to stop the attacker in their tracks Signals an alarm Monitors outbound traffic Question 4 Some of the Limitations of Cloud Computing services include (select all that apply): Question 4 options: Control LimitsContracts Inflexible Storage Limits Question 5 Which of the following are signs of file system intrusion? (choose all that apply) Question 5 options: Reduced Bandwidth Rogue SUID Entries Connection Requests Double Extensions Question 6 According to your text, ways to detect an Intrusion with an (IDS) include (choose all that apply): Question 6 options: Protocol Anomaly Detection Anti-Virus AlertsAnomaly Detection Signature Detection Question 7 The Major 5 actors of the NIST Cloud Computing Reference Architecture include which of the following? (choose two) Question 7 options: Cloud Auditor Cloud Broker CloudShareOne Cloud Database Question 8 According to the text, characteristics of Virtualization in cloud computing technology include (select all that apply): Question 8 options: Partitioning Isolation Wireless CapableEncapsulation Question 9 In this Cloud Deployment model, the provider makes services such as applications, servers, and data storage available. Question 9 options: Community Cloud Hybrid Cloud Private Cloud Public Cloud Question 10 According to your text, which of the following are Cloud Deployment Models? (choose all that apply) Question 10 options: Community Cloud Public Cloud Hybrid Cloud Private CloudQuestion 11 What are the advantages of Software as a Service (SaaS)? (choose all that apply) Question 11 options: Internet Dependency Security Low Cost Easy Administration Question 12 Some of the Virtualization vendors include (select all that apply): Question 12 options: VMware vSphere VMware vCloud Suite Virtual Box Microsoft Question 13 Which of the following is a tool that can be used to check for modified or trojanzied file? Question 13 options: chkdskfsck scandisk tripwire Question 14 An organization can implement this Cloud Deployment model within the corporate firewall. Question 14 options: Community Cloud Public Cloud Private Cloud Hybrid Cloud Question 15 Which of the following are signs of network intrusions? (choose all that apply) Question 15 options: Sudden Influx of DataRepeated Service Probes File Size Modifications Missing Files Question 16 Some of the Characteristics of Cloud Computing services include (select all that apply): Question 16 options: Resource Pooling Virtualization Technology Measured Services Distributed Storage Question 17 Which of the following are disadvantages of signature detection? (choose all that apply) Question 17 options: Signature Detection False PositivesFalse Alerts Administrative Alerts Question 18 Which of the following is a Cloud Consumer model that includes storage, service management, and content delivery? Question 18 options: PaaS SaaS IaaS SAN Question 19 According to the text, the three different types of Virtualization include which of the following? Question 19 options: Network Virtualization Storage Virtualization SAN VirtualizationQuestion 20 According to your text, these are the 3 types of cloud services. Question 20 options: Infrastructure as a Service Platform as a Service Virtualization as a Service Software as a Service Question 1 Which of the following apply to SSL Strip? (choose all that apply) Question 1 options: It forces HTTP It removes HTTPS It exploits the Client Connection It exploits the Server Question 2 Mobile Devices are replacing which of the following? (choose all that apply)Question 2 options: PDA labtop desktop GPS Question 3 Database Attacks include which of the following? (choose all that apply) Question 3 options: HOS Command Execution Data Dumping Privilege Escalation SQL Injection Question 4 According to the text, which of the following is a form of MITM Attack? Question 4 options: API Hooking Checksum EvasionSSL Strip Packet Sniffing Question 5 Mobile Physical Based Attacks include (choose all that apply): Question 5 options: Rooting No passcode Jail-Breaking Carrier Loaded Software Question 6 Which of the following are secure coding techniques? (choose all that apply) Question 6 options: Debugger Detection Jail-Break Detection Certificate Pinning ChecksumQuestion 7 Which of the following are methods to connect smartphones to a network? (choose all that apply) Question 7 options: Bluetooth Wi-Fi 3G/4G Wired Connection Question 8 Fake Defender deleted apk files from which of the following locations? (choose all that apply) Question 8 options: /users/Download /mnt/extSdCard/Download /mnt/external_sd/Download /home/Download Question 9The Android Runtime includes which of the following? (choose all that apply) Question 9 options: Dalvik Virtual Machine Bind IPC driver core libraries Flash memory driver Question 10 Phone based SMS attacks include which of the following? (choose all that apply) Question 10 options: Phreaking Baseband Attacks SMiShing RF Question 11 Which of the following are Android options to save persistent data? (choose all that apply) Question 11 options: Network ConnectionSQLite Databases External Storage Internal Storage Question 12 The Android relies on this version of the Linux kernel. Question 12 options: 2.6 3.6 3.10 3.0 Question 13 SPAM can include which of the following? (choose all that apply) Question 13 options: TLS SMSMMS IM Question 14 According to OWASP, which of the following are among the top ten mobile risks? (choose all that apply) Question 14 options: Client Side Injection Insecure Data Storage Bluetooth WEP and WPA1 Question 15 According to the text, the following will protect a system by limiting the ability to access resources: Question 15 options: Android Rooting Jail break detection app sandboxingJail Breaking Question 16 Mobile Network Based Attacks include (choose all that apply): Question 16 options: Packet Sniffing SSL Strip Rogue Access Points Man-in-the-Middle Attacks Question 20 According to OWASP, strong encryption channels, such as which of the following, should be used. (choose all that apply) Question 20 options: AES 3DES DES RC4 Question 1 User DataGram Protocol can be used for any of the following (choose 3):Question 1 options: Streaming Audio Teleconferening Reliable Communication Video Question 2 According to the text, having several Organizational units makes a company vulnerable to Question 2 options: attack: True Question 4 Social Engineering techniques include (select all that apply): Question 4 options: Research on a Target Company Exploiting the Victim Selecting a Victim Developing a Relationship Question 5 Which of the following Windows Utilities can be utilized to enumerate hosts? Question 5 options: net Use net start net view net stop Question 6 Which of the following below accurately describes Transmission Control Protocol (choose 3): Question 6 options: Supports Retransmission of lost DataConnection-less oriented protocol Can terminate a connection Provides acknowledgment Question 7 Typically SMB over TCP uses this port for transmission: Question 7 options: 137 139 161 445 Question 8 The NETBIOS Name can be up to: Question 8 options: is 24 characters is 15 characters is 16 characters is 128 characters Question 9 SMTP uses which port: Question 9 options: UDP Port 161 TCP Port 25 UDP Port 993 TCP Port 110 Question 10 SMTP commands include (select all that apply): Question 10 options:HELO DATA MGET RESET Question 11 IP Network Browser can determine this on a Cisco Device (select all that apply): Question 11 options: IOS Version ARP Tables Passwords Cards Installed Question 12 The psexec utility can be utilized to perform the following actions: Question 12 options: List Processes Launch an Interactive Command Session Get System Information Show open files Question 13 NETBIOS uses (choose all that apply): Question 13 options: TCP Port 22 UDP Port 137 UDP Port 138 TCP Port 139 Question 14 Which of the following are SNMP enumeration tools (Choose 3)? Question 14 options:Nmap Getif Spiceworks Softperfect Question 15 This port for the Global catalog Service: Question 15 options: 389 25 3389 3268 Question 16 Commonly used SNMP enumeration tools include: Question 16 options: nmap hping3 IP Network Browser Angry IP Scanner Question 17 NETBOIS Name Resolution is supported in IPv6: Question 17 options: False Question 18 (5 points) SNMP protocol responds to managers on: Question 18 options: UDP Port 162 TCP Port 162 UDP Port 161 TCP Port 161Question 19 This command provides you with netbios statistics: Question 19 options: netstat nbtstat netbtstat net use Question 20 Typically, NBNS uses this port for transmission: Question 20 options: TCP Port 137 UDP Port 137 TCP Port 139 UDP Port 139 tion 3 Network Time Protocol (NTP) enumeration commands include (Choose 3)? Question options: Net time ntpdate ntptrace ntpq uestion 4 Social Engineering techniques include (select all that apply): Question options: Research on a Target Company Exploiting the Victim Selecting a Victim Developing a Relationship uestion 12 The psexec utility can be utilized to perform the following actions: Question options: List ProcessesLaunch an Interactive Command Session Get System Information Show open files uestion 14 Which of the following are SNMP enumeration tools (Choose 3)? Question options: Nmap Getif Spiceworks Softperfect uestion 18 SNMP protocol responds to managers on: Question options: UDP Port 162 TCP Port 162 UDP Port 161 TCP Port 161 uestion 20 Typically NBNS uses this port for transmission: Question options: TCP Port 137 UDP Port 137 TCP Port 139 UDP Port 139 Question: To crash a webserver, attacker target (choose all that apply): Question options: rver Memory twork Bandwidth PU tabasestion 5 According to your text, most of the webservers run: Question options: crosoft IIS ache ogle GINX stion 6 Password cracking tools include (choose all that apply): Question options: utus in dra reshark stion 9 Which of the following is an Internet Relay Chat bot? Question options: rk Comet bSeven ergyMech tbus stion 20 Webserver footprinting can be down with (choose all that apply): Question options: Telnet Netcraft ID Serve httprecon Question 1 The three phases used to carry out a session fixation attack are (choose 3):Question 1 options: set up phrase fixation phrase tear-down phrase entrance phrase Question 2 According to the text, a major Denial of Service Attack caused major problems for Question 2 options: Target 780th Military Intelligence Brigade DALnet IRC Network Question 3 This tool will allow you to spoof a MAC address: Question 3 options: inverse arp smac Question 4 There are many purposes of malware, including the following (Choose 2): Question 4 options: Making a Computer Useless Disable Networking Functions Obtaining Passwords Remove the Default LAN Route Question 5 Which of the following uses direct client to client (DCC)?Question 5 options: Internet Browser Email Clients such as Outlook Express Internet Relay Chat File Sharing with Mapped Drives Question 6 What were the two dominant attack strategies identified in Symantec's Threat Report? Question 6 options: Distributed Denial of Service Focused Attack Broader Strokes Advanced Persistent Threats Save Question 7 In this type of Session hijacking, a hacker sits back and watches Traffic: Question 7 options: active passive stateless stateful Save Question 8 ( An attacker may use packet sniffing tools such as these to intercept traffic, (choose all that apply): Question 8 options: nmap wireshark smartsnif hping3 Question 9This tool can help detect arp spoofing: Question 9 options: smac inverse arp xarp rarp Save Question 10 Session hijacking takes advantage of: Question 10 options: flaws in HTTPS inexperienced end users flaws in TCP/IP flaws in encryptions Question 11 In application level hijacking, (choose all that apply): Question 11 options: takes over of an HTTP session packet capturing of UDP traffic packet capturing of TCP traffic session ID's are obtained Question 12 In network level hijacking, (choose all that apply): Question 12 options: takes over of an HTTP session packet capturing of UDP traffic packet capturing of TCP traffic session ID's are obtained Question 13 This is an example of a Trojan that can be utilized for Website Defacement:Question 13 options: HTTrack WGET Restorator CrimePack Question 14 A man in the middle attack is an example of this: Question 14 options: active passive stateless stateful Question 15 Session hijacking refers to an attack when an attacker: Question 15 options: takes over a valid TCP session takes over a valid UDP session takes over a valid TCP or UDP session takes over a valid ICMP session Question 16 One example of a wrapper program that can be used to hide a Trojan: Question 16 options: Obfuscator Trojan Warrior Malware Toolbox Kriptomatic Question 17What is the best course of action to remove Autorun for Removable Disks and CD Drives for in Windows? Question 17 options: Tape the USB ports Use Group Policy Question 18 (5 points) According to your text, examples of malware include (Choose 3): Question 18 options: Crypter Ransomware Botnet Metasploit Question 19 This will help prevent DNS spoofing attacks (choose all that apply): : Question 19 options: primary zones secondary zones SSH SSL Question 20 Session hijacking refers to an attack when an attacker takes over a valid TCP session: Question 20 options: True Question 1The Second part of the TCP 3 way handshake is a: Question 1 options: SYN ACK SYN-ACK FIN Question 2 Which of the following Flags will indicate that there is a new sequence number: Question 2 options: ACK URG SYN PSH Question 3 Which of the following is NOT a TCP flag: Question 3 options: ICMP SYN ACK RESET Question 4 The following tools are used for footprining (choose 3): Question 4 options: Recong-ng Aircrack-ng Maltego FOCA Question 5 According to the text, the first step in scanning is to Question 5 options:look for vulnerabilities Launch a buffer Overflow Create a custom packet Identify live systems Question 6 Netbios uses the following ports (Check all that apply): Question 6 options: 137 138 139 140 Question 7 The following can be utilized as traceroute tool: Question 7 options: nslookup TTL (Time to Live) pingpath Path Analyzer Pro Question 8 SNMP uses the following ports (Check all that apply): Question 8 options: 161 162 445 22 Question 9 The TCP 3 way handshake terminates after a choose 2 :Question 9 options: SYN ACK RESET FIN Question 10 How many bytes of the TCP/IP Packet are for protocol header information? Question 10 options: 16 32 8 56 Question 11 This tool will allow you to create a custom network packet: Question 11 options: ColaSoft Wireshark Snort TCPDUMP Question 12 ICMP and Port Scanning are the same. Question 12 options: False Question 13 Angry IP Scanner allows you to send the output to (Check all that apply): Question 13 options: CSVTXT XML IP-Port List file Question 13 Angry IP Scanner allows you to send the output to (Check all that apply): Question 13 options: CSV TXT XML IP-Port List file Question 15 ( An IPv4 address is: Question 15 options: 32 bits 16 bits 64 bits 128 bits Question 16 How many bytes of the TCP/IP Packet are for the data: Question 16 options: 16 32 8 56 Question 17 If you want to mask (or spoof your IP Address, use this type of scan: Question 17 options: IDLE, IPID ScanUDP Scan ACK Flag Probe Scan Stealth Scan Question 18 A ping scan is also an: Question 18 options: ICMP Scan UDP Scan ACK Flag Probe Scan Stealth Scan Question 19 (5 points) The website zaba search provides what type of information to users? Question 19 options: Operating System Webserver software Version IP Addresses Phone Numbers and Addresses Question 20 An IPv6 address is: Question 20 options: 32 bits 16 bits 64 bits 128 bits Question 6 The following is one of the most reliable forms of TCP scanning: Question options:MAS Scan erse TCP Flag Scan nnect Scan**** lf-open Scan stion 9 The Simple Service Discovery Protocol (SSDP) will (choose 3): Question options: t work behind a firewall n be vulnerable to denial of service es multicast addresses ntrols Communication for the Universal Plug and Play Service stion 10 After an ICMP scan, if a host is live it will send back: Question options: CK MP Echo Request MP Echo Reply N-ACK stion 17 The following tools are used for footprining (choose 3): Question options: Recong-ng Aircrack-ng Maltego FOCA A spoofing attack includes, (choose all that apply): Question options: takes over of an HTTP session relies on the legitimate user pretends to be another user uses stolen credentialA hijacking attack includes, (choose all that apply): Question options: takes over of an HTTP session relies on the legitimate user pretends to be another user uses stolen credentials u estion 2 Which of the following is a tool that will allow you decrypt traffic? Question options: Aircrack-ng Packetforge-ng Airodump-ng Airdecap-ng Question 6 Which version of Wired Equivalent Privacy (WEP) uses a 104-bit key size? Question options: 128 bit WEP 64 bit WEP 256 bit WEP 152 bit WEPQuestion 7 An SSID (select all that apply): Question options: Is part of the frame header Will be encrypted if WEP or WPA/WPA2 is utilized Is Case Sensitive Can be up to 32 characters Question 9 SQL Databases include (Choose all that apply): Question options: MS Access Oracle My SQL Microsoft SQL Question 11 Which of the following are part of the aircrack-ng suite? (Choose all that apply) Question options:Packetforge-ng Aircrack-ng Airdecap-ng Airodump-ng Question 12 This Bluetooth attack occurs because an oversized ping packet: Question options: Blue Bugging Blue Cracking Bluesmacking Blue Snarfing Question 14 An SSID is NOT (Choose one)? Question options: Case Sensitive up to 32 characters encrypted if WEP or WPA/WPA2 is utilizedpart of the frame header Question 15 This Bluetooth attack tries to get sensitive data: Question options: Blue Bugging Blue Snarfing Bluesmacking Blue Cracking Question 17 Wired Equivalent Privacy (WEP) keys can be (Choose all that apply): Question options: 512 bits 256 bits 104 bits 40 bitsQuestion 18 Phonesnoop is a (Choose all that apply): Question options: Android hack Wi-Fi hack Bluetooth hack Blackberry hack Question 20 Which of the following uses Orthogonal Frequency Division Multiplexing? (choose all that apply) Question options: 802.11g 802.11b 802.11a 802.11n Among all smartphones, which is most likely to be hacked? Question options: iPhoneWindows Phone Blackberry Android What is the block (word) size used by SHA-512 algorithm? Question options: 32-bit 256-bit 128-bit 64-bit Question 10 0.75 / 1 point Which of the following are SNMP enumeration tools? (choose all that apply) Question options: Softperfect Nmap GetifSpiceworks Question 23 0.75 / 1 point Which of the following companies offer Cloud Computing services? (choose all that apply) Question options: Google Dropbox Salesforce Facebook Question 24 0 / 1 point Which of the following conditions shows the presence of a honeypot? Question options: Ports show a particular service running and allow a three-way handshake connection Scan shows that no scanned port is live on the network Ports show a particular service running but deny a three-way handshake connection Ports do not show any particular service running Question 27 0 / 1 pointWhich of the following is a mutation technique used for writing buffer overflow exploits in order to avoid IDS and other mechanisms? Question options: Pad the beginning of the intended buffer overflow with a long run of NOP instructions makes a buffer to overflow on the lower part of heap, overwriting other dynamic variables Randomly replace the NOPs with functionally equivalent segments of code (e.g.: x++; x-; ? NOP NOP) Assuming that a string function is exploited, send a long string as the input Question 29 0 / 1 point What virus modifies the directory table entries so they point to the virus code instead of the actual program? Question options: Macro Viruses Cluster Viruses Encryption Viruses Boot Sector Viruses Question 32 0 / 1 point Which of the following IDS detection techniques detects the intrusion based on the fixed behavioral characteristics? Question options:Signature recognition Anomaly detection All of the above Protocol anomaly detection Question 34 0 / 1 point Permutation Scanning involves which of the following? Question options: Looking for new vulnerable machines on the local subnet Using information from infected machines Using a psudorandom function Collecting a list of possibly vulnerable machines Question 35 0.75 / 1 point Which of the following are phone based SMS attacks? (choose all that apply) Question options: Phreaking RFSMiShing Baseband Attacks Question 37 0 / 1 point Which of the following enumeration techniques does an attacker use to obtain list of computers that belongs to a domain? Question options: SMTP enumeration SNMP enumeration Netbios enumeration NTP enumeration Question 49 0.75 / 1 point When an attacker is performing a denial of service and a SYN attack is initiated which of the following occurs? (choose all that apply) Question options: Sends a large number of ACK packets to the target Uses a fake source address Sends a large number SYN requests to the target Uses the actual source addressQuestion 51 0.5 / 1 point According to OWASP, strong encryption channels, such as which of the following should be used? (choose all that apply) Question options: RC4 3DES AES DES Question 62 0 / 1 point Which of the following flags will indicate that there is a new sequence number? Question options: URG PSH SYN ACK Question 75 0.75 / 1 pointFootprining tools will help gather the following information about a target. (choose all that apply) Question options: Process Lists Host Names IP Addresses DNS Records Question 77 0 / 1 point When a distributed reflective denial of service attack (DRDoS) is used which two of the following occurs? Question options: The source Address will be spoofed Traffic to the secondary hosts will originate from the intermediate hosts Traffic will be directed to intermediate hosts Traffic will be directed to secondary victims Question 78 0 / 1 point BlackShades Net can best be described as a: Question options: BotWrapper DDoS Tool RAT Question 80 0 / 1 point Buffer overflow attacks allow an attacker to modify the ___________ in order to control the process execution, . Question options: Target rainbow table Target remote access Target SAM file Target process's address space Question 81 0.25 / 1 point What does the term phalshing refers to? (choose all that apply) Question options: Can be known as bricking A type of permanent Denial of Service Something that can cause a device to render hardware inoperableAn email attack in which the user is enticed to click on links Question 82 0.75 / 1 point SYN flooding takes advantage of which of the following? (choose all that apply) Question options: Holding the incomplete connection for a period up to one second A flaw in how the three-way handshake can be implemented Not replying to SYN/ACKs A flaw in some firewalls which do not restrict ICMP traffic by default Question 84 0 / 1 point With this Cloud Deployment model, the provider makes services such as applications, servers, and data storage available. Question options: Hybrid Cloud Community Cloud Private Cloud Public Cloud Question 88 0.75 / 1 pointSigns of Intrusions include which of the following? (choose all that apply) Question options: Slow Performance Strange Processes Missing Logs System Crashes Question 94 0 / 1 point What happens when the CAM table is full? Question options: It does not affect the switch functioning Additional ARP request traffic will not be forwarded to any port on the switch The switch will stop functioning and get disconnected from network Additional ARP request traffic will flood every port on the switch Question 95 0.5 / 1 point What does SSL Strip do? (choose all that apply) Question options: Force HTTPRemove HTTPS Exploit the Client Connection Exploit the Server Question 97 0 / 1 point Which of the following protocols are susceptible to sniffing? Question options: SNMP FTP NNTP Telnet Question 101 0.5 / 1 point Which of the following characteristics applies to the Simple Service Discovery Protocol (SSDP)? (choose all that apply) Question options: Not work behind a firewall Can be vulnerable to denial of service Controls Communication for the Universal Plug and Play ServiceUses multicast addresses Question 103 0.25 / 1 point The Management Information Base (MIB) includes which of the following? (choose all that apply) Question options: User Accounts OID Numbers Scalar and Tabular Objects File and Folder Permissions Question 107 0.5 / 1 point Some of the Infrastructure as a service vendors include: (choose all that apply) Question options: Go Grid Amazon EC2 Sungrid Windows SkyDrive Question 108 0.75 / 1 point What are the 3 techniques that can be utilized to propagate malicious code?Question options: Back Chaining Autonomous Back Dating Central Source Question 109 0 / 1 point Which rootkit modifies the boot sequence to load themselves instead of the original virtual machine monitor? Question options: Boot loader level rootkit Library level rootkits Kernel level rootkit Hypervisor level rootkit Question 111 0.75 / 1 point With Cross Site Scripting, attackers can inject malicious ____. (choose all that apply) Question options: HTML VBScriptFlash JavaScript Question 123 0.75 / 1 point Which of the following are characteristics of Cloud Computing services? (choose all that apply) Question options: Distributed Storage Virtualization Technology Measured Services Resource Pooling Network level hijacking includes (choose all that apply) packet capturing of UDP traffic packet capturing of TCP traffic Select the countermeasures of a Virus and Worms. Install anti-virus software Regular scansDo not accept disks or programs you don’t know. Your Supervisor is concerned about the use of port 139 in your environment. What measure do you recommend? Disable File and Print Sharing According to the text, a Denial of Service Attack caused major problems for: DALnet IRC Network The characteristics of these Trojans include the ability to open and close the CD-ROM tray (check all that apply): NetBus SubSeven With a session fixation attack, the attacker uses a: valid SID Which of the following is an example of a wrapper program that can be used to hide a Trojan? Kriptomatic When predicting a session token you must use: Captures Cross-site Request Forgery is also known as: a one click attack This tool will allow you to spoof a MAC address: smac A hijacking attack includes (choose all that apply): pretends to be another user takes over of an HTTP session uses stolen credentials How should you enable DHCP to enable DHCP snooping? (choose all that apply) per vlan globally Select the anti-virus tools from the list below.Kaspersky Anti-Virus McAfee AntiVirus BitDefender ESET Smart Security Which of the following uses direct client to client (DCC)? Internet Relay Chat This will help prevent DNS spoofing attacks (choose all that apply): SSH SSL What are the three phases used to carry out a session fixation attack? entrance phrase set up phrase fixation phrase What is the best course of action to remove Autorun for Removable Disks and CD Drives in Windows? Use Group Policy What are the components of IPsec? E-banking Internet Key Exchange (IKE) Oakley Detecting Session Hijacking uses different tools. Which are the methods used? Select all that apply. Intrusion Detection Systems (IDS)Packet Sniffing Software Intrusion Protection System Which of the following are countermeasures that can be used for Trojans? 1. Commonly used SNMP enumeration tools include which of the following? ip network browser 2. NetBIOS uses which of the following? UDP port, TCP port 22, UDP port 137, and TCP port 139 3. The SMTP protocol provides 3 built in command? finger, expen, rcpt to, vrfy 4. Which of the following ntp enumeration commands? ntptrace, nettime, ntpq 5. Microsoft windows store hashed passwords in the ? SAM file 6. The psExec utility can be utilized to perform which of the following actions? launch an interactive command session 7. Typically smb over tcp uses this for for transmission? 445 8. Which port does ldap use? 389 9. Aes uses ____ select all iterated block cipher, key size stream cipher, 64bits, 128 bits lock, symmetric key algorithm, asymmetric key algorithm 10.Which of the following MIB files contains information about server services? Lnmib2.mib 11.The three built in commands SMTP provides are__ Rcpt to, verfy, expn 12.Symmetric encryption uses the __same__key__ to encrypt and decrypt 13.The pstools includes which of the ? Psdumpram, psloglist, pslists, psexec 14.Where in windows are password stored? SAM 15.Typically nbns uses this port for transmission? Udp port 137 16.Tls uses the __RSA_algorithm 17.Ip network browser can betermine cisco devices? Passwords, cards installed, arp tables 18.According to text, having several organization units makes a company vulnerable to attack? True 19.Attackers cover their tracks online by using tools like .MRU -blaster 20.Snmp proctocol responds to managers on which port? Udp port 1625 / 5 points Fake Defender deleted apk files from which of the following locations? (choose all that apply) /mnt/extSdCard/Download /home/Download /mnt/external_sd/Download /users/Download Question 2 5 / 5 points According to OWASP, strong encryption channels, such as which of the following, should be used. (choose all that apply) AES 3DES DES RC4 Question 3 5 / 5 points With Cross Site Scripting, attackers can inject malicious ____. (choose all that apply) VBScript Flash JavaScript HTML Question 5 / 5 points4 Phone/SMS-based attacks include which of the following? (choose all that apply) Baseband Attacks RF Phreaking SMiShing Question 5 5 / 5 points Which of the following is not a Phishing countermeasure best practices? Do not click on any links included in an SMS message Never call a number left in an SMS message Quickly respond to the SMS message with a warning Enable “block texts from the internet” feature from your provider Question 6 0 / 5 points Mobile device pairing on open connections allows attackers to eavesdrop and intercept data transmission using which the following techniques? Select all that apply. BlueJacking BlueBugging BlueSnarfing BlueProxyQuestion 7 3.75 / 5 points Which of the following apply to SSLStrip? (choose all that apply) It forces HTTP It removes HTTPS It exploits the Server It exploits the Client Connection Question 8 3.75 / 5 points Insufficient or no vetting of apps can lead to which of the following? (choose all that apply) fake apps rooting Malicious apps jail-breaking Question 9 5 / 5 points Bluetooth devices in these modes are at greater risk (choose all that apply): promiscuous discovery monitor open Question 5 / 5 points10 According to the text, which of the following is a form of MITM Attack? Packet Sniffing Checksum Evasion SSLStrip API Hooking Question 11 0 / 5 points The Android relies on this version of the Linux kernel. 3.0 2.6 3.10 3.6 Question 12 5 / 5 points Which of the following is the 3D Graphics Library of Android? SSL SGL Media Framework OpenGL Question 13 1.25 / 5 points According to OWASP, which of the following are among the top ten mobile risks? (choose all that apply)Bluetooth Client Side Injection WEP and WPA1 Insecure Data Storage Question 14 5 / 5 points Which of the following tools can be used to attack Blackberry devices. BBproxy Bjacker BBscan BBAttacker Question 15 5 / 5 points Which of the following tools is used for session hijacking on Android devices? DroidSheep DroidJacking Zitmo Droid PCAP Question 16 5 / 5 points The Android Runtime includes which of the following? (choose all that apply)core libraries Dalvik Virtual Machine Bind IPC driver Flash memory driver Question 17 5 / 5 points _______________ helps protect systems and users by restricting the resources an app can access on a mobile platform. Jailbreaking Sandboxing App Stores SSL Question 18 5 / 5 points Which of the following are app stores? (choose all that apply) BlackBerry App World ITunes Store Fandango Google Play Question 19 5 / 5 points Network-based points of attack include (choose all that apply): Packet SniffingRogue access points Man-in-the-Middle Attacks SSLStrip Question 20 5 / 5 points Android___________ is a utility for capturing raw 802.1 frames on and Android device. PCAP DroidSheep Capture WireShark CMIT Quiz 1 Is a worm for window XP that downloads and executes malicious files on the compromised computer and spreads through removable storage devices? a. HTTP W32.Drom b. W32/VBAut-B c. W32/QQRob-AND d. W32/Silly FDC- BK Monitors and audit databases for security issues in real time a. Selective Audit (may be) b. AppDetective c. AppRadar d. Flex TracerWhich of the following attack would you choose to seize control of a legitmate user’s web application session while the session is still in progress? a. Session hijacking b. DOS attack c. Password Sniffing d. Spoofing Viruses search all drives and connected network shares to locate files with an EXE or SCE extensions a. W32/Madang-Fam b. W32/Hasnot-A c. W32/Fujacks-AK d. W32/Fjacks-E In order for traffic to get back to the attacker during session hijacking, a process called -------- is used that allows the sender to specify a particular route for the IP packet to take to the destination. a. desynchronization b. Source routing c. Spoofing d. TCP routing A ----- attack occurs when a attacker sends an oversized packet to a victim’s device. a. Bluesmacking b. Blueprinting c. BTVoiceBugging d. Bluesnarfing ---- can monitor a simple mail transfer protocol (SMTP) server regularly after connecting to it. a. CheckOk b. SMTPCheck c. SMTPmom d. SLCheck Which of the following definitions best describes a wrapper? a. A wrapper is a packet-crafting techniques used to perform stealthy port scans. b. A wrapper is an encryption tool used to hide messages inside image files c. A wrapper is a method of hiding a virus inside an executable file d. A wrapper is a tool used to bind a Trojan to a legitimate file.------ hijacking is a hacking technique that uses spoofed packets to take over a connection between a victim and a target machine. a. ACK b. Blind c. TCP/IP d. Network-level Which of the following is not a Microsoft Internet information services vulnerability a. ::$Data vulmerability b. UFS integer overflow vulnerability c. Showcode.asp vulnerability d. WebDAV/R PC exploits The ----- scripts allows a remote user to view the code of server-side scripts. a. Showlogin.asp b. Showcode.asp c. RemoteAccess.asp d. Remotelogin.asp ----- is acomand-line tool that is bundled with both windows and UNIX operating systems and is used to querying DNS information a. Whois b. Traceroute c. Netstat d. NsLookup Which type of information cannot be found ina resource record (RR)? a. MX b. ARP c. PTR d. SOA ---- is a network scanning technique used to discover which range of IP address map to live computers a. Port scanning b. Ping Sweep c. Probe scanning d. Fingerprinting An attacker is interested in dscovering ports that might be open on a target system. The attacker decides to port scan the IP address of the system but also wants to make the scan as stealthy as possible. Which of the following techniques would be the best choice in this scenario? a. TCP connect scanb. SYN scan c. ICMP echo scan d. List scan During the reconnaissance phase of an attack, the attacker may resort to looking though an organization;s trash for discarded sensitive information. This technique is known as a. social engineering b. breaking and entering c. dumpster diving d. passive reconnaissance Which of the following are objectives of scanning (select all that apply) All The simple service discovery protocol will (choose 3) a. Not work behind a firewall b. Can be vulnerable to denial of service c. Uses multicast addresses d. Controls communication for the universal plug and play service Which port scanning method is considered the most reliable in terms of accurately reporting port status on a target system? a. TCP connect () scan b. SYN Scan c. ACK scan d. Xma Scan The following tools are used for foot printing (choose 3) a. Recong-ng b. Aircrack-ng c. Maltego d. FOCA ---- is a spoofing technique that allows an attacker to choose the path a packet will take through the internet a. SYN Scanning b. Source Routing c. Tracerouting d. Http tunneling If you want to mask (or spoof your IP address, use this tyoe if scan) a. IDLE, IPID scan b. UDP Scan c. ACK Flag Probe Scan d. Stealth ScanCMIT 321 QUIZ 2 Version 2 Question 1 (5 points) IP Network Browser can determine this on a Cisco Device (select all that apply): Question 1 options: Passwords ARP Tables IOS Version Cards Installed Save Question 2 (5 points) Symmetric Encryption uses the _____________ to encrypt and decrypt. Question 2 options: Same keys Two Key Pairs method Different keys None of the above Save Question 3 (5 points) NETBIOS Name Resolution is supported in IPv6:Question 3 options: False True Save Question 4 (5 points) Sending an email with a link to a malicious website is called _____? Question 4 options: Hacking Phishing Impersonation Enumeration Save Question 5 (5 points) The SMTP Protocol provides 3 built in commands. What are they? Question 5 options: EXPN FINGER RCPT TO VRFY Save Question 6 (5 points) Attackers attempt to enumerate ______ Question 6 options:Domain Name System Routing Tables Application Banners All of the above B and C only Save Question 7 (5 points) Typically SMB over TCP uses this port for transmission: Question 7 options: 161 137 139 445 Save What are some characteristics that make LM hashes vulnerable to offline attacks? (Select all that apply.) Question 3 options: They are short. They are converted to lower case. They are converted to upper case. If the password is 10 characters long, it is split into a password of six variable characters and another hash of four charactersSave Previous PageNext Page In this type of password attack, the attacker has some information about the password. For example, the attacker knows the password contains a two- or threedigit number. Question 5 options: hybrid nontechnical rule-based precomputed hashes Which of the following Windows Utilities can be utilized to enumerate hosts? Question 6 options: net Use net view net view net stop ______________ has a unique process for discovering and fixing security holes. The entire methodology is controlled through an efficient administrative tool that enables you to compress settings to manipulate a network or conduct a full-hammer assault. Question 7 options: Found Scan AppScanCyberCop Scanner Hackshield SNMP uses ___________________ to define the information that a managed system offers. Question 8 options: a) Management Information Bases (MIBs) b) Simple Network Management Protocol c) SNMPUTIL d) object identifiers Which of the following Management Information Base (MIB) files contains information about server services : Question 9 options: DCHP.MIB HOSTMIB.MIB WINS.MIB LNMIB2.MIB What hidden share can be tested for evidence of null-session vulnerabilities? Question 10 options: ADMIN$ NULL$C$ IPC$ Network Time Protocol (NTP) enumeration commands include (Choose 3)? Question 11 options: Net time ntpdate ntptrace ntpq Which one of the following makes the SNMP protocol a target used by hackers to gather useful information about target hosts? Question 12 options: It uses the UDP protocol. It transmits its community string in clear text. It comes configured by default on all devices. It cannot be disabled. The SMTP Protocol provides 3 built in commands, including: Question 13 options: VRFY EXPN RCPT TOFINGER Save Previous PageNext Page The SMTP Protocol provides 3 built in commands, including: Question 13 options: VRFY EXPN RCPT TO FINGER Save Previous PageNext Page This tool uses the command line to identify and report the protocol statistics of current TCP/IP connections using NBT (NetBIOS over TCP/IP). Question 20 options: DumpSec Net View Nbtstat enum Save Previous PageNext Page ________________ has a unique process for discovering and fixing security holes. The entire methodology is controlled through an efficient administrative tool that enables you to compress settings to manipulate a network or conduct a full-hammer assault.Question 7 options: Found Scan AppScan CyberCop Scanner HackshieldSNMP uses ___________________ to define the information that a managed system offers. Question 8 options: SNMP uses ___________________ to define the information that a managed system offers. Question 8 options: a) Management Information Bases (MIBs) b) Simple Network Management Protocol c) SNMPUTIL d) object identifiers Save Previous PageNext Page Which of the following Management Information Base (MIB) files contains information about serv services : Question 9 options: DCHP.MIB HOSTMIB.MIBWINS.MIB LNMIB2.MIB What hidden share can be tested for evidence of null-session vulnerabilities? Question 10 options: ADMIN$ NULL$ C$ IPC$ Network Time Protocol (NTP) enumeration commands include (Choose 3)? Question 11 options: Net time ntpdate ntptrace ntpq Which one of the following makes the SNMP protocol a target used by hackers to gather useful information about target hosts? Question 12 options: It uses the UDP protocol. It transmits its community string in clear text. It comes configured by default on all devices.It cannot be disabled. 1. If you want to mask (spoof) your IP address, what type of scan should you use? IDLE IPID scan 2. Tracert counts the number of ________ to a destination IP address. Hops 3. Which of the following can be utilized as a traceroute tool? Path Analyzer Pro 4. Which of the following are tools used for footprinting? FOCA Maltego 5. Footprinting tools will help gather the following information about a target? IP Addresses, DNS Records 6. Which of the following flags will indicate that there is a new sequence number? SYN 7. Which of the following characteristics applies to the simple service discovery?Controls communications for the universal plug and play service Uses multicast addresses Can be vulnerable to denial of service 8. Which of the following is one of the most reliable forms of TCP scanning? Connect scan 9. Which of the following below accurately describes transmission control protocol? Provides acknowledgment Can terminate a connection 10. The psexec utility can be utilized to perform which of the following actions? Launch an interactive Command session 11. Which of the following windows utilities can be utilized to enumerate hosts? Net view 12. The management information base (MIB) includes which of the following? OID Numbers Scalar and Tabular Objects 13. Which of the following management information base (MIB) files contain information about server services? LNMIB2.MIB 14. Which of the following are SNMP enumerator tools?Softperfect Spiceworks 15. Which of the following are LDAP enumeration tools? JXplorer LEX 16. Which of the following are network time protocol(NTP) enumeration commands? Ntpq Ntptrace Ntpdate 17. The SMTP protocol provides 3 built in commands, including which of the following? RCPT TO EXPN VRFY 18. According to your text, examples of malware include which of the following? BOTNET Ransomware Crypter 19. Of the following, which two are purposes of malware?Obtaining passwords Making computers useless 20. Which of the following uses direct client to client (DCC)? Internet relay chat 21. The autorun feature of removable disks and cd drives can be a threat to network security. What is the best course of action to remove autorun for removable disks and CD drives in windows? Use group policy 22. Your supervisor is concerned about the use of port 139 in your environment. What measures do you recommend taking to deal with the security risk? Disable file and disk sharing 23. What were the two dominant attack strategies identified in Symantec’s threat report? Broader Strokes Focused Attack 24. Which of the following trojans include the ability to open and close the CD-ROM tray? SubSeven NetBus25. Which of the following is an example of a wrapper program that can be used to hide a trojan? Kriptomatik 26. Which of the following is an example of a trojan that can be utilized for website defacement? Restorator 27. When an attacker is performing a denial of service and a SYN attack is initiated which of the following occurs? Uses a fake source address Sends a large number of SYN requests to the target 28. SYN flooding takes advantage of which of the following? Not replying to SYN/ACKs A flaw in how the three-way handshake can be implemented 29. When a distributed reflective denial of service attack (DRDoS) is used which two of the following occurs? The source address will be spoofed Traffic will be redirected to intermediate hosts 30. Which of the following is an internet relay chat bot EnergyMech31. Permutation Scanning involves which of the following? Using a psudorandom function 32. What are three techniques that can be utilized to propagate malicious code? Autonomous Back Chaining Central Source 33. Central source propagation commonly utilized what two protocols? FTP RPC 34. According to the text, by 2018, what percentage of enterprises will specify Wi-Fi as the default connection? 40% 35. The MAC address of an access point is referred to as the? BSSID 36. Which of the following is transmission method of digital data that uses a pseudo random noise spreading code? DSSS 37. Which of the following 802.11 standards uses Orthogonal Frequency Division Multiplexing?802.11a 802.11g 802.11n 38. which of the following is true about 802.11i standard? It defines WPA-2 enterprise and personal 39. All the following are true about SSID except which of the following? Will be encrypted in WEP or WPA/WPA2 is utilized 40. Which of the following applies to an SSID? Is part of the frame header Is case sensitive Can be up to 32 characters 41. Wi-Fi Chalking includes which of the following? War walking War flying War chalking War driving 42. Which of the following is an antenna based on the principal of a satellite dish and can pick up Wi-Fi signals from 10 miles away? Parabolic43. Which version of wired equivalent privacy (WEP) uses a 104-bit key size? 128 bit WEP 44. Which of the following companies offer cloud computing services? Salesforce Dropbox Facebook Google 45. Which of the following are characteristics of cloud computing services? Measured Services Virtualization Technology Distributed storage Resource pooling 46. What are some of the limitations of cloud computing services? Control limits Inflexible Contracts 47. Some of the infrastructure as a services vendors include? Sungrid Windows skydriveGo grid Amazon EC2 48. What are 2 advantages to having software as a service? Easy Administration Low cost 49. According to your text, what are the 3 types of cloud services? Software as a service Platform as a service Infrastructure as a service 50. According to your text, which of the following are cloud deployment models? Hybrid cloud Public cloud Community cloud Private cloud 51. With this cloud deployment model, the provider makes services available to the public over the internet. Public cloud 52. An organization can implement this cloud deployment model within the corporate firewall.Private cloud 53. Which cloud deployment model is a multi-tenant infrastructure shared among organizations with common characteristics? Community cloud 54. The advantages of using a community cloud deployment include which of the following? Compliance to regulations Shared resources 55. Which two of the following are among the five major actors of the NIST Cloud computing reference architecture? Cloud broker Cloud auditor 56. Which of the following are service models available to cloud consumers? SaaS IaaS PaaS 57. Which cloud consumer model includes database, business intelligence, and application deployment? PaaS58. Which cloud consumer model includes storage, service management, and content delivary? IaaS 59. Which cloud consumer model includes human resources and enterprise resources management? SaaS 60. According to your text, components of a cloud broker include which of the following? Service arbitration Service aggregation Service intermediation 61. Of the following options, which are virtualization vendors? Microsoft Virtual Box VMware vSphere VMware vCloud Suite 62. According to your text, characteristics of virtualization in cloud computing technology include which of the following? EncapsulationIsolation Partitioning 63. According to the text, the three different types of virtualization include? Server virtualization Network virtualization Storage virtualization 64. Which of the following applies to an intrusion detection system(IDS)? Signals an alarm Monitors outbound traffic Monitors inbound traffic 65. Which of the following are some of the main functions of an intrusion detection system? Performs packet analysis Performs packet sniffing Gathers and analyses information from a network 66. You should place your intrusion detection system (IDS) in this location on the network? Outside the firewall Inside the firewallDMZ 67. According to your text, which of the following are ways to detect an intrusion with an (IDS)? Protocol anomaly detection Anomaly detection Signature detection 68. Which of the following are disadvantages of signature detection? False alerts False positives 69. Signs of intrusion include which of the following? Strange processes Slow performance System crashes Missing logs 70. Which of the following are signs of file system intrusion? Double extensions Rogue SUID Entries 71. Which two of the following are signs of network intrusion? Sudden influx of dataRepeated Service Probes 72. Which of the following is a tool that can be used to check for modified or trojanized files? Tripwire 73. Select the three IP protocols that Snort supports for suspicious behavior according to your text? UDP TCP ICM 74. Which of the following are methods to connect smartphones to a network? Wired connection 3G/4G Bluetooth Wi-Fi 75. According to OWASP, the top ten mobile risks include which two of the following? Client side injection Insecure data storage 76. Mobile devices are replacing which of the following devices?PDA Desktop Laptop GPS 77. According to OWASP, which of the following should be applied to transport channels? SSL TLS 78. According to OWASP, strong encryption algorithms, such as which of the following should be used? 3DES AES 79. According to OWASP, which of the following are secure coding techniques? Debugger detection Certificate pinning Checksum Jail-breaking detection 80. Which of the following are mobile network based attacks? Rogue access pointsPacket sniffing SSL Strip Man-in-the-middle attacks 81. According to the text, which of the following is a form of MITM attack? SSL strip 82. According to the text, which of the following will protect by limiting the ability to access resources? App sandboxing 83. Which of the following are phone based SMS attacks? SMiShing Baseband attacks RF 84. What does SSL strip do? Force HTTP Remove HTTPS Exploit the Client Connection 85. With cross site scripting, attackers can inject malicious? Flash HTMLVBScript JavaScript 86. Which of the following are types of database attacks? Privilege escalation OS command execution Data dumping SQL injection 87. According to the text, among all smartphones, which is most likely to be hacked? Android 88. What is a network of many hacked smartphones called? Botnet 89. A lack of vetting of apps can lead to which two of the following results? Malicious apps Fake apps 90. App stores include? Google play Itunes Blackberry App World 91. Which of the following can be used to spam mobile devices?SMS MMS IM 92. Which of the following can a hacker use to gain control of a device? Blue Bugging 93. Which modes on Bluetooth devices add greater risk? Discovery Open 94. Android includes media support for which of the following? AAC ARM H.264 95. Android options to save persistent application data include which of the following? Internal storage External storage SQLite Databases Network connection 96. Which of the following is the 3D Graphics Library of android?OpenGL 97. Which version of the linux kernel does android rely upon? 2.6 98. Which two of the following are included in android runtime? Core libraries Dalvik Vitual Machine 99. Which of the following are enabled by rooting? Deleting systems files Removing bloatware Tethering Low level access to hardware 100. Which of the following are risks of rooting? Voiding the warranty Bricking Malware Poor performance 101. Fake defender deleted apk files from which two of the following locations? /mnt/external_sd/Download/mnt/extSdCard/Download 102. Sophos mobile security features include? Privacy Protection and Security Loss and Theft Protection Spam Protection Antivirus anti-malware 103. Black hat Hackers are? Individuals with extraordinary computing skills, resorting to malicious or destructive activities 104. What is the first hacking phase that hackers perform to gather information about a target prior to launching an attack? Reconnaissance 105. Which of the following techniques is used to simulate an attack from someone who is unfamiliar with the system? Black box pen testing 106. Which scanning technique will bypass firewall rules, logging mechanisms, and hide themselves? Stealth scanning technique107. Which of the following scans only works if the operating systems TCP/IP implementation is based on RFC 793? NULL Scan 108. Which of the following is true about active stack fingerprinting? Is based on the fact that various vendors of OS implement the tcp stack differently 109. Which of the following sentences is true about a proxy? Protects the local network from outside access 110. Which of the following IP spoofing detection techniques succeeds only when the attacker is in a different subnet? Direct TTL Probes Technique 111. Which of the following enumeration techniques does an attacker use to obtain list of computers that belongs to domain? NetBios enumeration 112. Which of the following ports does NTP use as its primary means of communication? UDP port 123 113. Which rootkit modifies the boot sequence to load themselves instead of the original virtual machine monitor? Hypervisor level rootkit114. Which of the following steganography techniques hides information in significant parts of the cover image such as cropping, compression, and some other image processing areas? Transform domain techniques 115. Which of the following viruses evades the anti-virus software by intercepting its requests to the operating system? Stealth/tunneling virus 116. Which of the following statements is true for lawful intercept? Network operator or service provider legally sanction access to private network data for monitoring? 117. Passive sniffing refers to? Sniffing through a hub 118. ARP spoofing involves constructing a large number of forged ARP request and reply packets to overload? Switch 119. Which of the following is a system of a DoS attack? Unavailability of a particular website 120. Which of the following factors contribute to a successful session hijacking?Weak session ID generation algorithm 121. Buffer overflow attacks allow an attacker to modify the_______ in order to control the process execution? Target Process’s address space 122. Which wireless standard has bandwidth up to 54 Mbps and signals in a regulated frequency spectrum around 5GHz? 802.11a 123. Which of the following is an antenna used in wireless base stations and provides a 360 degree horizontal radiation pattern? Omnidirectional antenna 124. WPA enhances WEP by changing temporal keys every_______? 10,000 packets 125. Packet filtering firewall works at which of these layers of the OSI model? Network layer 126. Which is the best location to place keyloggers? Keyboard hardware and the operating system 127. Which of the following techniques practiced by an attacker exploits human behavior to make attacks?Social engineering 128. Identify the correct statement for a software firewall? Software firewall is placed between the normal application and the networking components of the operating system 129. Identify the Nmap scan method that is often reffered to as half open scan? SYN Stealth 130. Which of the following protocols are susceptible to sniffing? Telnet 131. Identify the statement which is true for RC6 algorithm? Includes integer multiplication and the use of four 4-bit working registers 132. Which password cracking techniques will the attacker use if she gets some information about the password to crack? Rule based attack 133. What is the block (word) size used by SHA-512 algorithm? 64-bit 134. Which cryptographic attack refers to extraction of cryptographic secretes from a person by coercion or torture? Rubber Hose attack135. Which of the following firewall architectures is designed to host servers that offer public services? Screened subnet 136. Which of the following evasion techniques rely on Time to Live TTL fields of a TCP/IP packet? Insertion attack 137. Which of the following conditions shows the presence of a honeypot? Ports show a particular service running but deny a three-way handshake connection 138. What virus modifies the directory table entries so they point to the virus code instead of the actual program? Cluster virus 139. Which of the following wi-fi chalking methods refers to drawing symbols in public places to advertise open wi-fi? War chalking 140. What is the size of WEP initialization vector? 24-bit 141. Which of the following Bluetooth attacks refers to sending unsolicited messages over Bluetooth to Bluetooth-enabled?Bluejacking 142. Identify the attack which forces an unsuspecting user’s browser to send malicious requests they did not intend? Cross-site request forgery (CSRF) 143. Which of the following IDS detection techniques detects the intrusion based on the fixed behavioral Characteristics? Anomaly detection What is the block (word) size used by SHA-512 algorithm? Question options: 32-bit 256-bit 128-bit 64-bit Question 10 0.75 / Which of the following are SNMP enumeration tools? (choose all that apply) Question options: Softperfect NmapGetif Spiceworks Question 23 0.75 / Which of the following companies offer Cloud Computing services? (choose all that apply) Question options: Google Dropbox Salesforce Facebook Question 24 0 / Which of the following conditions shows the presence of a honeypot? Question options: Ports show a particular service running and allow a three-way handshake connection Question 27 0 / Which of the following is a mutation technique used for writing buffer overflow exploits in order to avoid IDS and other mechanisms? Question options: Pad the beginning of the intended buffer overflow with a long run of NOP instructionsmakes a buffer to overflow on the lower part of heap, overwriting other dynamic variables Randomly replace the NOPs with functionally equivalent segments of code (e.g.: x++; x-; ? NOP NOP) Assuming that a string function is exploited, send a long string as the input Question 29 0 / What virus modifies the directory table entries so they point to the virus code instead of the actual program? Question options: Macro Viruses Cluster Viruses Encryption Viruses Boot Sector Viruses Question 32 0 / Which of the following IDS detection techniques detects the intrusion based on the fixed behavioral characteristics? Question options: Signature recognition Anomaly detection All of the aboveProtocol anomaly detection Question 34 0 / Permutation Scanning involves which of the following? Question options: Looking for new vulnerable machines on the local subnet Using information from infected machines Using a psudorandom function Collecting a list of possibly vulnerable machines Question 35 0.75 / Which of the following are phone based SMS attacks? (choose all that apply) Question options: Phreaking RF SMiShing Baseband Attacks Question 37 0 / Which of the following enumeration techniques does an attacker use to obtain list of computers that belongs to a domain? Question options:SMTP enumeration SNMP enumeration Netbios enumeration NTP enumeration Question 49 0.75 / When an attacker is performing a denial of service and a SYN attack is initiated which of the following occurs? (choose all that apply) Question options: Sends a large number of ACK packets to the target Uses a fake source address Sends a large number SYN requests to the target Uses the actual source address Question 51 0.5 / According to OWASP, strong encryption channels, such as which of the following should be used? (choose all that apply) Question options: RC4 3DESAES DES Question 62 0 / Which of the following flags will indicate that there is a new sequence number? Question options: URG PSH SYN ACK Question 75 0.75 / Footprining tools will help gather the following information about a target. (choose all that apply) Question options: Process Lists Host Names IP Addresses DNS Records Question 77 0 /When a distributed reflective denial of service attack (DRDoS) is used which two of the following occurs? Question options: The source Address will be spoofed Traffic to the secondary hosts will originate from the intermediate hosts Traffic will be directed to intermediate hosts Traffic will be directed to secondary victims Question 78 0 / BlackShades Net can best be described as a: Question options: Bot Wrapper DDoS Tool RAT Question 80 0 / Buffer overflow attacks allow an attacker to modify the ___________ in order to control the process execution, . Question options: Target rainbow tableTarget remote access Target SAM file Target process's address space Question 81 0.25 / What does the term phalshing refers to? (choose all that apply) Question options: Can be known as bricking A type of permanent Denial of Service Something that can cause a device to render hardware inoperable An email attack in which the user is enticed to click on links Question 82 0.75 / SYN flooding takes advantage of which of the following? (choose all that apply) Question options: Holding the incomplete connection for a period up to one second A flaw in how the three-way handshake can be implemented Not replying to SYN/ACKs A flaw in some firewalls which do not restrict ICMP traffic by defaultQuestion 84 0 / With this Cloud Deployment model, the provider makes services such as applications, servers, and data storage available. Question options: Hybrid Cloud Community Cloud Private Cloud Public Cloud Question 88 0.75 / Signs of Intrusions include which of the following? (choose all that apply) Question options: Slow Performance Strange Processes Missing Logs System Crashes Question 94 0 / What happens when the CAM table is full? Question options:It does not affect the switch functioning Additional ARP request traffic will not be forwarded to any port on the switch The switch will stop functioning and get disconnected from network Additional ARP request traffic will flood every port on the switch Question 95 0.5 / What does SSL Strip do? (choose all that apply) Question options: Force HTTP Remove HTTPS Exploit the Server Question 97 0 / Which of the following protocols are susceptible to sniffing? Question options: SNMP FTP NNTPTelnet Question 101 0.5 / Which of the following characteristics applies to the Simple Service Discovery Protocol (SSDP)? (choose all that apply) Question options: Not work behind a firewall Controls Communication for the Universal Plug and Play Service Uses multicast addresses Question 103 0.25 / The Management Information Base (MIB) includes which of the following? (choose all that apply) Question options: User Accounts Scalar and Tabular Objects File and Folder PermissionsQuestion 107 0.5 / Some of the Infrastructure as a service vendors include: (choose all that apply) Question options: Go Grid Amazon EC2 Sungrid Windows SkyDrive Question 108 0.75 / What are the 3 techniques that can be utilized to propagate malicious code? Question options: Back Chaining Autonomous Back Dating Central Source Question 109 0 / Which rootkit modifies the boot sequence to load themselves instead of the original virtual machine monitor? Question options:Boot loader level rootkit Library level rootkits Kernel level rootkit Hypervisor level rootkit Question 111 0.75 / With Cross Site Scripting, attackers can inject malicious ____. (choose all that apply) Question options: HTML VBScript JavaScript Question 123 0.75 / Which of the following are characteristics of Cloud Computing services? (choose all that apply) Question options: Distributed Storage Virtualization Technology Measured ServicesResource Pooling Network Time Protocol (NTP) is designed to synchronize clocks of networked computers. Which of the following port NTP uses as its primary means of communication? UDP port 123 In order to compromise or to hack a system or network the hackers go through various phases of the hacking. What is the first hacking phase that hackers perform to gather information about a target prior to launching an attack? Reconnaissance Defense-in-depth is a security strategy in which several protection layers are placed throughout an information system. It helps to prevent direct attacks against an information system and data because a break in one layer only leads the attacker to the next layer. True Penetration testing is a method of actively evaluating the security of an information system or network by simulating an attack from a malicious source. Which of the following technique is used to simulate an attack from someone who is unfamiliar with the system? Black box pen testing Which of the following scanning technique attackers use to bypass firewall rules, logging mechanism, and hide themselves as usual network traffic? Stealth scanning technique Which of the following scan only works if operating system’s TCP/IP implementation is based on RFC 793? NULL scan OS fingerprinting is the method used to determine the operating system running on a remote target system. It is an important scanning method, as the attacker will have a greater probability of success if he/she knows the OS. Active stack fingerprinting is one of the types of OS fingerprinting. Which of the following is true about active stack fingerprinting? Is based on the fact that various vendors of OS implement the TCP stack differently Proxy is a network computer that can serve as an intermediary for connecting with other computers. Which of the following sentence is true about a proxy? Protects the local network from outside access IP spoofing refers to the procedure of an attacker changing his or her IP address so that he or she appears to be someone else. Which of the following IP spoofing detection technique succeed only when the attacker is in a different subnet? Direct TTL probes technique Enumeration is defined as the process of extracting user names, machine names, network resources, shares, and services from a system. Which of the following enumeration an attacker uses to obtain list of computers that belongs to a domain? Netbios enumeration Network Time Protocol (NTP) is designed to synchronize clocks of networked computers. Which of the following port NTP uses as its primary means of communication? UDP port 123 Rootkits are kernel programs having the ability to hide themselves and cover up traces of activities. It replaces certain operating system calls and utilities with its own modified versions of those routines. Which of the following rootkit modifies the boot sequence of the machine to load themselves instead of the original virtual machine monitor or operating system? Hypervisor level rootkitSteganography is a technique of hiding a secret message within an ordinary message and extracting it at the destination to maintain confidentiality of data. Which of the following steganography technique embed secret message in the frequency domain of a signal? Transform domain techniques A virus is a self-replicating program that produces its own code by attaching copies of it into other executable codes. Which of the following virus evade the anti-virus software by intercepting its requests to the operating system? Stealth/Tunneling virus Lawful intercept is a process that enables a Law Enforcement Agency (LEA) to perform electronic surveillance on a target as authorized by a judicial or administrative order. [Show More]
Last updated: 3 years ago
Preview 1 out of 128 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 10, 2022
Number of pages
128
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 10, 2022
Downloads
0
Views
209