Military Science > QUESTIONS & ANSWERS > C725 exam 1. Explain the elements of the CIA Triad and give an example of each. (All)
C725 exam 1. Explain the elements of the CIA Triad and give an example of each.
Document Content and Description Below
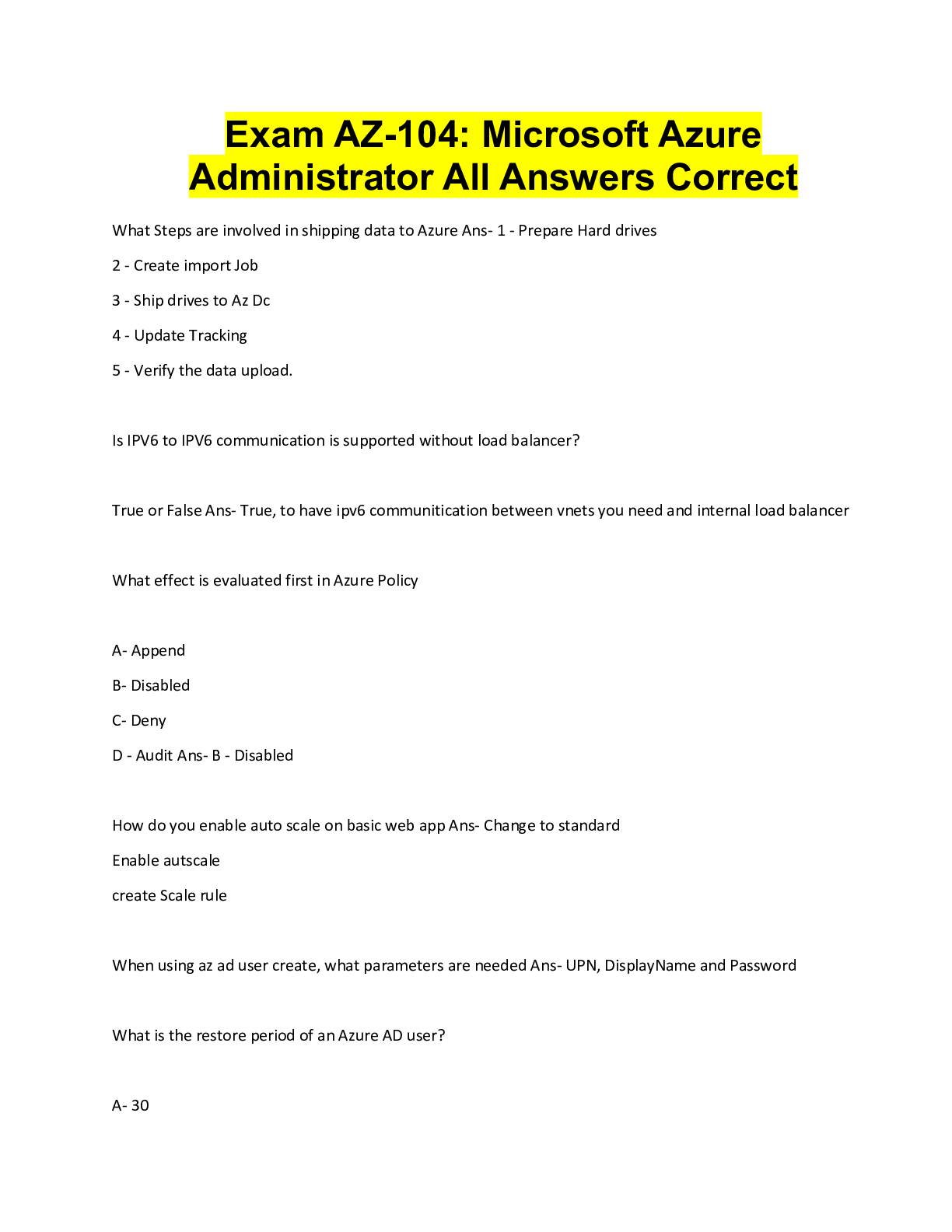
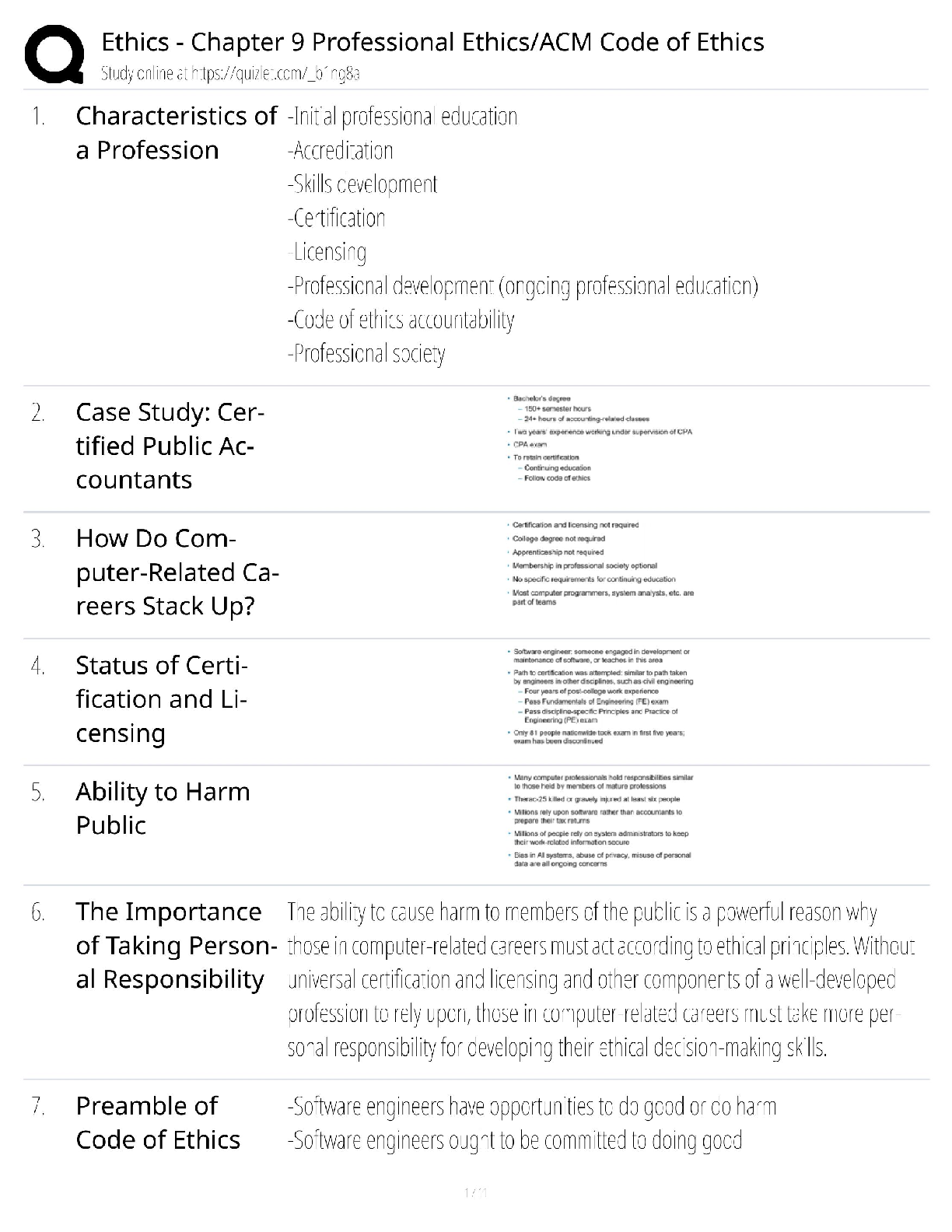
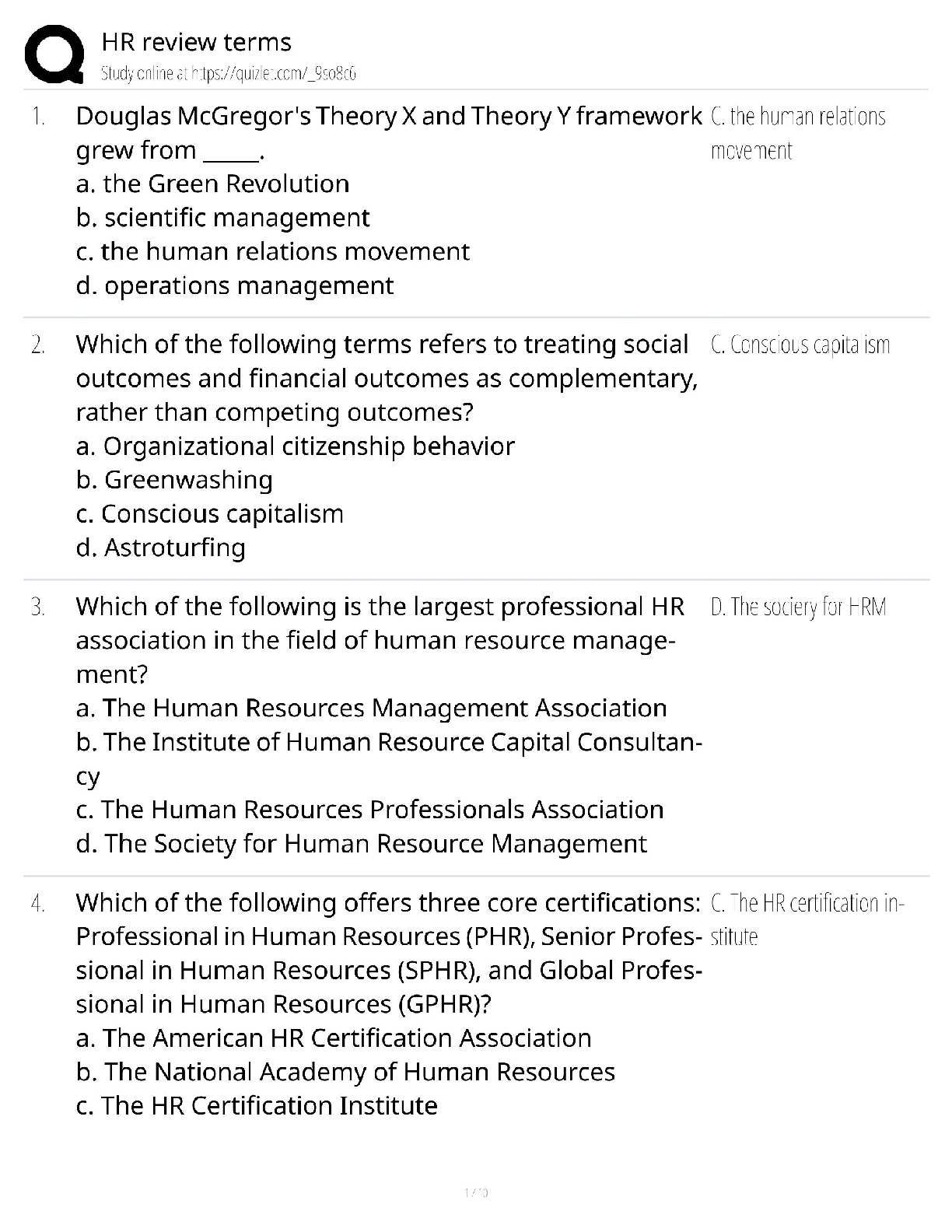
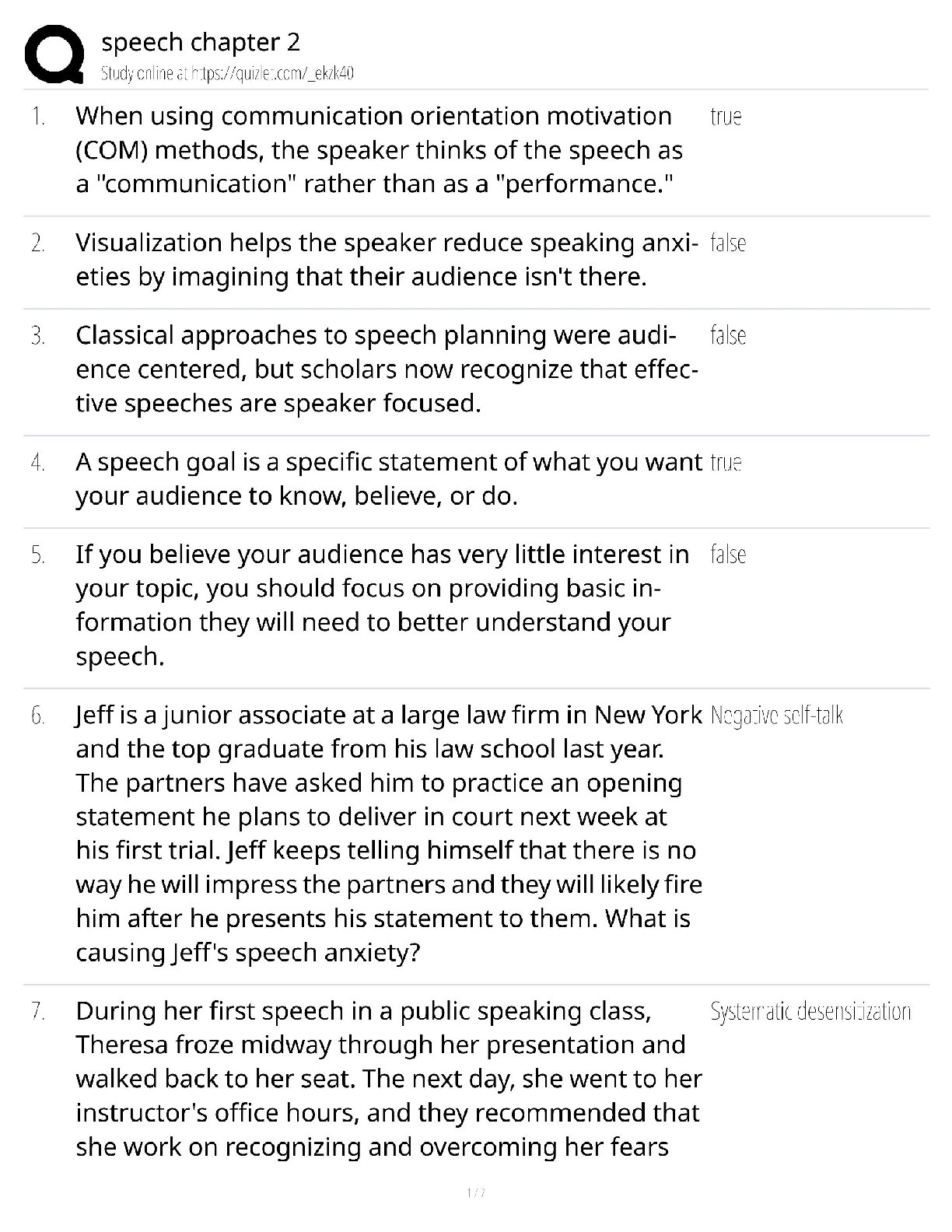
C725 exam 1. Explain the elements of the CIA Triad and give an example of each. What is the CIA triad? CIA refers to Confidentiality, Integrity and Availability. Confidentiality of information, int ... egrity of information and availability of information. Many security measures are designed to protect one or more facets of the CIA triad. Let us discuss one by one.. Confidentiality: When we talk about confidentiality of information, we are talking about protecting the information from disclosure to unauthorized parties. Information has value, especially in today’s world. Bank account statements, personal information, credit card numbers, trade secrets, government documents. Every one has information they wish to keep a secret. Protecting such information is a very major part of information security. A very key component of protecting information confidentiality would be encryption. Encryption ensures that only the right people (people who knows the key) can read the information. Encryption is VERY widespread in today’s environment and can be found in almost every major protocol in use. A very prominent example will be SSL/TLS, a security protocol for communications over the internet that has been used in conjunction with a large number of internet protocols to ensure security. Integrity: Integrity of information refers to protecting information from being modified by unauthorized parties. Information only has value if it is correct. Information that has been tampered with could prove costly. For example, if you were sending an online money transfer for $100, but the information was tampered in such a way that you actually sent $10,000, it could prove to be very costly for you. As with data confidentiality, cryptography plays a very major role in ensuring data integrity. Commonly used methods to protect data integrity includes hashing the data you receive and comparing it with the hash of the original message. However, this means that the hash of the original data must be provided to you in a secure fashion. More convenient methods would be to use existing schemes such as GPG to digitally sign the data. Availability:C725 exam Availability of information refers to ensuring that authorized parties are able to access the information when needed. Information only has value if the right people can access it at the right times. Denying access to information has become a very common attack nowadays. Almost every week you can find news about high profile websites being taken down by DDoS attacks. The primary aim of DDoS attacks is to deny users of the website access to the resources of the website. Such downtime can be very costly. Other factors that could lead to lack of availability to important information may include accidents such as power outages or natural disasters such as floods. How does one ensure data availability? Backup is key. Regularly doing off-site backups can limit the damage caused by damage to hard drives or natural disasters. For information services that is highly critical, redundancy might be appropriate. Having a off-site location ready to restore services in case anything happens to your primary data centers will heavily reduce the downtime in case of anything happens. 2- Explain Defense in Depth Defense in depth is an informaton assurance (IA) concept in which multple layers of security controls (defense) are placed throughout an informaton technology (IT) system. Its intent is to provide redundancy in the event a security control fails or a vulnerability is exploited that can cover aspects of personnel, procedural, technical and physical for the duraton of the system's life cycle. [Show More]
Last updated: 3 years ago
Preview 1 out of 19 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$11.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 13, 2022
Number of pages
19
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 13, 2022
Downloads
0
Views
184