Software Engineering > EXAM REVIEW > CIS105 FINAL NOTE AND STUDY GUIDE. All the Essential and Necessary information to pass CIS Exam (All)
CIS105 FINAL NOTE AND STUDY GUIDE. All the Essential and Necessary information to pass CIS Exam
Document Content and Description Below
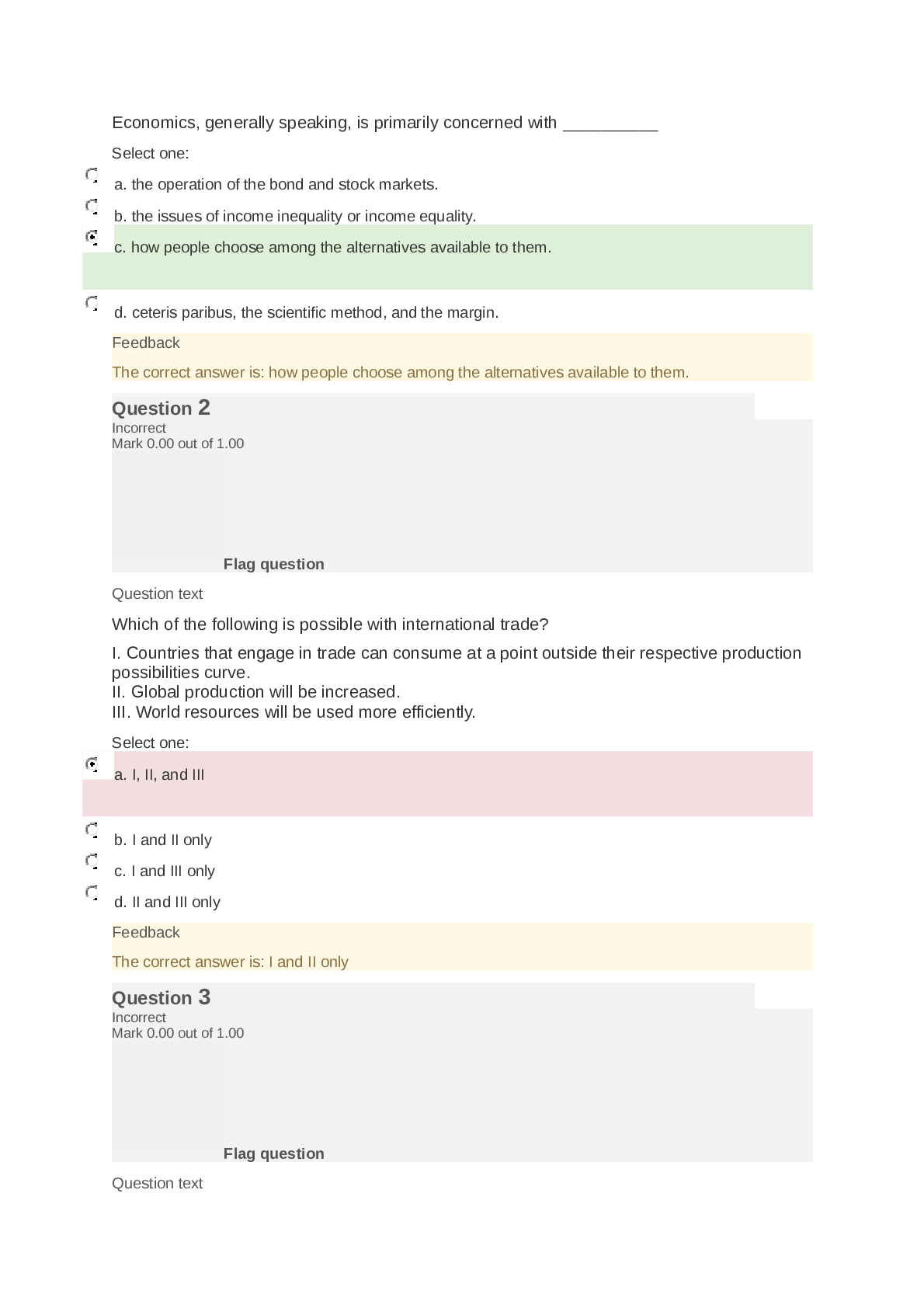
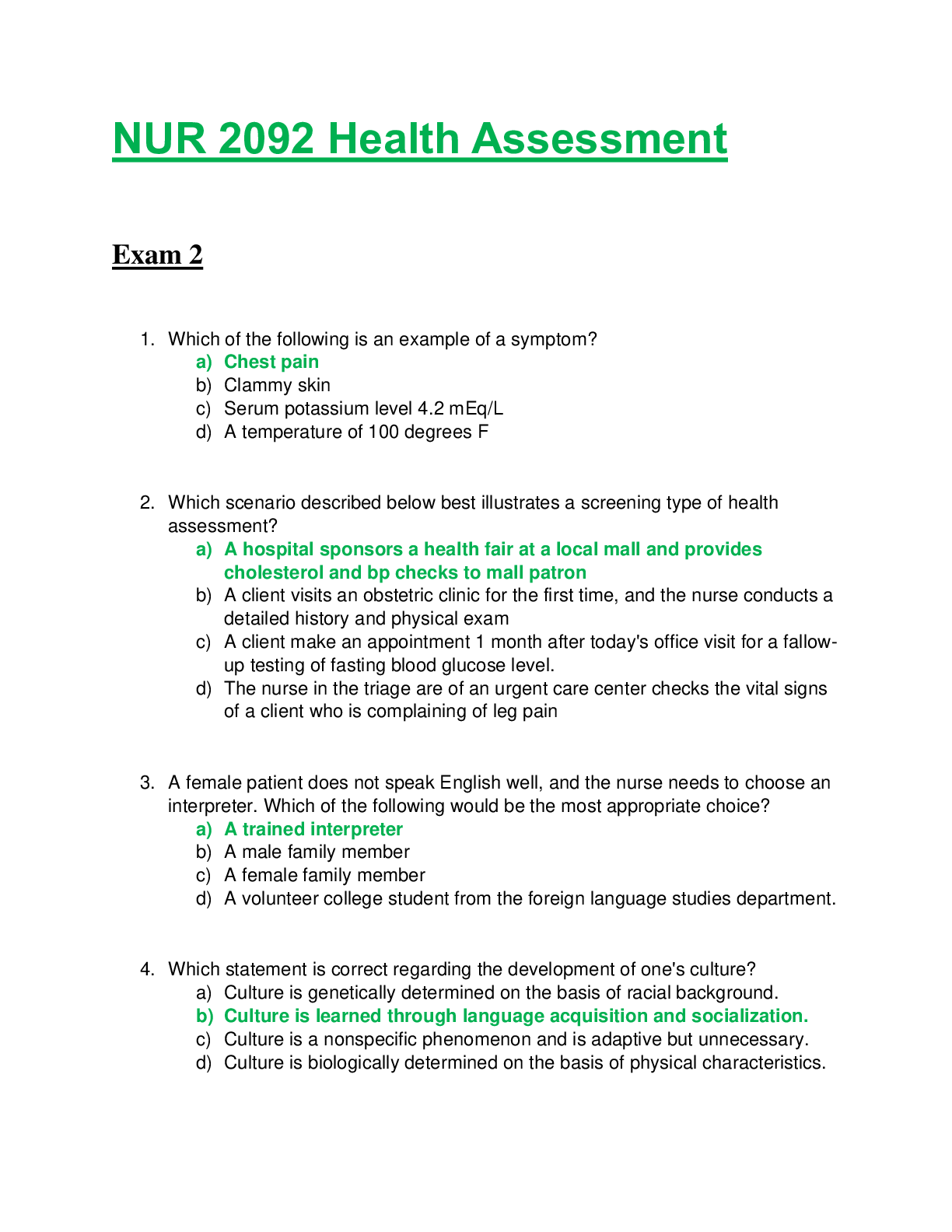
CH: 6 Why computer works? System software load the operating system When computer start from scratch (restart) warm boot When computer turn off ordinary exist When computer ... turn on *********** BIOS “Basic Input/ Output System” (Also called “Firmware”): is Responsible for loading operating system. Ram “Random Access Memory”: Primary storage, fastest storage, requires electricity to not lose data, save to secondary storage or to cloud. The data in ram is saved to secondary storage, usually a hard drive or spinning media. A hard drive is: a secondary storage, a filing cabinet, does not need electricity to retain data, is what makes up most of the cloud ******** And keyboards need programs to run as well, and those programs are called device drivers. Computers only understand 1 and 0 which is called machine language or machine code. Everything has to be translated either into machine code or out of machine code (within input devices or output devices) EX: keyboard (input device) , microphone (input device), monitor ( output device) , speaker ( output device), webcam ( input device). All translating into the language. The advantage of putting laundry in dryer and then Grapping all laundry of dryer speed and save time. DisadvantageDisorganized,, so the mother fore goes to defragmentation. Your hard drive gets disorganized and to organize it we use: Defragmentation “Defrag”takes information on your hard drive and moves it to the inner concentric tracks of a hard drive. Defrag organize hard drive by moving data and information to the inside concentric tracks of the hard drive Defrag does not make your hard drive go faster, but Defrag does however have your hard drive more efficient. CH: 8 computer network: two or more computers connected together to share resources (those resources are files and folders, software, hardware, internet) Don’t forget that internet is considered resource of a network. Where can I catch a printer and scanner? I catch it to a server, so that everybody can use the printer and scanner the printer and scanner are called peripheral devices anything connected to a network is called a node a computer with no network at all including no internet is considered garbage the main advantage of network collaboration there are 4 things that make up every network: 1- Network Interface Controller card “NIC”: plugged into the motherboard to interface and connect with other computers. NIC card has a MAC address on it, and has 32- bit unique identifier number. 2- protocol: TCP/IP: controls how data and information is shared between computers.CIS105 FINAL NOTE 3- Cables: Cables connect servers to client which can sometimes be replaced through wireless connections (cable all clients in one server) Cable network is way safer than wireless network 4- Hub: typically, the central location of a network (server) that serves to run the network smoothly. Rules for transferring information from box to box on a network (Network protocols): 1- Transmission control protocol/ internet protocol (TCP/IP): 80% of all networks use TCP/IP. TCP/IP breaks big files down into many small packets. a packet is 8000 KB. TCP/IP is a guaranteed protocol will not let you look at the downloading file until it is completely downloaded 2- User Datagram Packets (UDP) breaks large files into packet (8000KB). However, UDP user datagram packets. user datagrams packets will let me look at the files as it is downloading ( like a video ) EX of UDP : YouTube technically, COULD you run YouTube with TCP/IP? YES, WOULD you? NO Network Operating systems (NOS) are like stand-alone operating systems The 4 things Network Operating systems (NOS) will do : 1- automatic hardware detection. The NOS recognize it when it becomes part of the network. 2- supports multi-processing which allows several processes to occur at one time 3- recognize who is using the network 4- provides security network administrator the most trusted person on network Network topology: the logical interconnection between nodes. Basically, the way a network is arranged and laid out (connect all together) 3 different topologies: 1- Bus Topology (Linear bus topology): includes a backbone. 2- Star Topology: The most common topology 3- Ring Topology: Circular topology. Types of computer networks: (arranged from smallest to biggest ) 1- local area network (LAN) : a small network typically confined by a single building. Often by smaller businesses. 2- campus area network (CAN): connects two or more LANs which are located on universities or large businesses. LANs are assigned to business area like accounting 3- Metropolitan area network (MAN): A computer network that connects CANs and LANs into a larger network that covers entire city. 4- Wilde area network (WAN): connects LANs, Cans, and MANs and can cover an entire country 5- Peer to peer (P2P): Generally connect computers to each other ( EX LimeWire, BitTorrrent) 6- internet: The world’s largest network interconnecting public, private, commercial, and government networks. The most common topology isCIS105 FINAL NOTE World wide web (WWW) is part of the internet. The internet is the world’s largest network. Password: a secret word or combination of keyboard characters typed in by the user to authenticate their identity to a network and gain appropriate access Strong passwords: requires a user to use: 1- upper case characters, 2- lower case characters,3- numbers, 4- special characters Passphrase: it is not memorable password! it is memorable STRONG password. (EX: UofA sucks << and make sure to look at upper case, lower case, number and special character) Do you let anyone browse in your business web? NO Firewall can guarded internet or network. Firewall : hardware and software working together. The hardware is called a proxy server that determines who is allowed on a network, and who is not CH: 9 What military service started the internet? Air force What is ARPANET means? Advanced research Project Agency Network Where was the internet invented? UCLA university Tim Berners- Lee did not invent the internet! Tim Berners- Lee invented the world wide web “WWW” Tim Berners- Lee invented HTML “Hypertext Markup Language” & HTTP “Hypertext transfer protocol” , & WWW “world wide web” HTML is a platform neutral language, standard language, read by a browser, weak HTTP how computers receive data from one computer to another. Once HTML and HTTP were in place, the WWW was born in 1990 as browsing software. The first browser was called World Wide Web The internet is a “client/ server” network IP address “ Internet Protocol Address” to see where things are in the internet, it is 32-bit number ( 32-bit number looks like >> 1 to 3 possible numbers) Websites have addresses called URL: it is uniform resource locator ( NOT UNIVERSAL ) http://www.yahoo.com identifying the parts: Yahoo domain name, .com domain code. Common domain codes: .com commercial, .edueducational, .mil military, .govgovernmental, .orgorganization, .netnetwork Web Pages: are written in HTML, within server, are requested by a client. you do not visit the Internet; the internet visits the client. Hyperlinks: are a clickable navigation element to access another IP address. The most important aspects of a website are: 1- content (most important) 2-interactivity, 3- design Browsers are presenting in GUI “Graphical User Interface” Which browser is the best browser? NONE Browser features: 1- Bookmarks (favorites)CIS105 FINAL NOTE 2- Caching where the internet history is,,, cashing exist on client. 3- Cookie has a ligament purpose. Example of Internet Service providers ( ISP) cox.com and comcas.com Example of internet hosting service Godaddy.com Search engine : Google.com keyword search engine, DogPile.com Metasearch engine E-Commerce: three ways to have e-commerce on the web is: 1- Business-to-business (B2B) 2- Business-to-Consumer (B2C) 3- Consumer-to-Consumer (C2C) EX: Ebay Virtual store >> provides agility All 5 securities are category of >> Malware Worst Viruses >> DoS Voids >> Uses internet as infrastructure Voids >> subset of telephony “elephony” Business website alternative >> do it yourself 3 examples: Wordpress.com or workpress.com Web.com Wix.com Blog terminology came from >> came from web log HTML >> standard, platform neutral, works on any platform, weak, represented with elements, closed by brackets Websites live on web servers Clients request a web page from a web server >> The server serves a web page copy to the clients Client is a system >> attracts property, attracts reservation, attracts university student Fat client >> very very powerful, very very expensive, trouble distribution >> has to be within the building Thin client >> uses a browser, uses HTML as pack in program, inexpensive, very very well distributed worldwide, extremely weak. Which one is better? NoneCIS105 FINAL NOTE Why would you put competitor name in your own websites medatax? to pop up as well 3 websites: 1- Static website >> rarely changes its content, also called brochure website 2- Dynamic website >> uses server side processing website EX: Facebook and red, create HTML send to me as a client Advertisment >> made by graphical file 3 ways to pay for it: 1- CPC cost 2- cost per thousand 3- cost per action Social network advertising >> convectional advertising result from a search engine called serps >> “search engine result page” Chapter Information and ………….: Every business does the same 5 functional behavior regardless of the size of business: 1- accounting >> gaap >> “Generally Accepted Accounting Principle” SOX >> gaap and sox attempt the counter fradual report in accounting 2- giggle way >> part of human resources 3- …………. >> Firm specific human capital 4- Marketing department >> products, promotion, placement, pricing >> systematic and becabel >> looking in idea 5- Production department >> tangible >> good Intangible >> service All 5 must collaborate >> collaboration provided information technology 1. Discussion board >> First in discussion board “Thread” 2. Cheapest way to collaborate and oldest >> discussion board 3. Texting 4. Project management >> EX: Microsoft project or process 5. Knowledge management system >> knowledge transfer EX of KM: googled ox and spreadsheet Report data and information >> reporting is informational output to make business decision 2 kinds of business decision: - Tactical >> lower employee, only include information from organization, internal information - Strategic >> higher employee, use information internal to organization and externalCIS105 FINAL NOTE Most report are periodic >> given interval Some reports produced whenever needed >> demand report “ad hoc report” All reports are from transaction processing system “TPS report” >> most detailed Low of employee >> use TPS report >> summarize in 4 lines More detailed >> more low >> more detailed report >> tactical more summarized report >> strategic TPS report >> database Take actual number and subtracted from forecast number >> result is called variance Actual – previous >> variance Worse >> both are suck Database: well thought out collection of files >> the most important is table Data put in tables >> tables have columns called fields and rows called records The left most field or column >> index field or key field >> avoided data doublocation Most important in Database >> Querying Result of querying >> Make business decision Database without exception >> always distributed, always in network Entity relationships diagram or Entity relationship model The result of ERD >> schema Avoid data input errors >> we use data validation The most common query language >> Structured query language Select title field from the book table >> where the price field is greater than a hundred >> then order it by a title field Awful woman in bank >> the fault is from Zacc You can delegate authority but you Can’t delegate responsibility >> admiral hymon RickoverExam 1: hese are the key terms. Information technology is the study, design, development, implementation, support, and management of computer-based information systems particularly and hardware Without people, computers are just plastic boxes. People who use computers are end-users. Computer competency is the knowledge that enables a person to understand a computing system and its relationship to business. Best practice is the process, technique, or method that is most effective at arriving at a desired outcome. Computer application is something with practical use and expected outcome Moore's law, computing power doubles every 18 months Mainframe: super/large computers mid range computers: smaller than mainframe, but similar in effectiveness microcomputers: simply computers, or boxes (desktops, laptops,handhelds) Operating system is most important of system software. it becomes a platform for application software to work Cache: is small, quick memory because it stores/copied information from the most regularly used part in main memory. It decrease the time it takes to access memory. RAM: is a storage that allows stored data to be accessed in any random order without physical movement of the storage media. Registers: extremely fast, very small amounts of memory used to quicken the implementation of computer programs by providing access to commonly used calculated values Virtual memory is the memory the OS uses to coordinate, track, and efficiently allocate the use of cpucache, registers, ram, and disk storage System unit is the main body of a computer. it contains the motherboard Microcomputer=box=case=chassis.it encloses the main components of computer Speed is measured by clock rate which is the cycles per second that a computer can perform its most basic tasks. It's measured in gigahertz Bus lines: are pathways (or roads in our analogy) that transfer data and power between components inside of a computer, and sometimes between computers. They are controlled by software that enables them to connect peripheral devices like computer cards and printers 8 bits=1 byte. A bit is a binary digit (0 or 1) Microcomputers use the ASCII coding scheme. Primary Storage is volatile, not permanent like RAM. secondary storage is non-volatile. saves information for ever. motherboard is a primary circuit board which holds and connects computer components. a circuit board (also called a printed circuit board/ PCB) is a logical and economical way to replace what would be loose wiring by applying copper wires directly to a sheet of nonproductive plastic Operating systems are referred asplatforms Process=job/task a computer performs. When a computer has more than 1 process, it's multitasking. Disk storage is non-volatile, secondary storage that is recorded to a physical device, like a hard drive or optical disk with a read/write apparatus FAT is like a table of contents for the disk. It directs the read/write arm of the hard drive to where data exists and accesses it. File management is a way to store and organize a user's work represented by computer files to the memory of a computer. When a computer is connected to one or more computers, it is called a network TCP/IP is a set of rules for transferring information from one computer to another. They break up files into packets and passes them from one comp to another. a data backup refers to making copies of data. archiving is when data that is no longer used on a daily basis is stored electronically, if it needs to be accessed someday. storage is the ways a computer can store data and information. capacity: how much information it can hold open source: software in which the source code is made available to the program's users access time: the amount of time that lapses between a request for information from memory and the delivery of the information hard drive is a secondary storage that uses rigid disks that have magnets. storage: a general term for computer components that offer nonvolatile retention of computer data and program instructions Volatile memory are susceptible to loses. Disappears forever if the power fails. nonvolatile memory are not susceptible to loss, data is preserved memory: circuitry that stores information temporarily so that it is readily available to the CPU device driver: a program file that contains specific information needed by the OS so that a specific brand or model of device will function physical storage media: represent ones and zeros with positive or negative electromagnetic charges magnetic disks, dvd rom, cd, hdd, flash, floppy, etc.. magnetic tape: non--volatile, is an old data storage media packaged on reel-to-reel cartridges. Capacity is unlimited. used for large data. It's SLOW UDP is a network protocol. LikeTCP/IP, but it doesn't guarantee that all packets will be sent. Used for YouTube firmware or system software is the software that manages and controls the physical hardware of a computer so an application can work. Proprietary platforms (OS) cannot be accessed or modified. Non-proprietary platforms can be accessed. Exam2: These are the defined terms. Application software performs tens of thousands of specific tasks the end-user needs, like creating a budget for accounting, creating a resume, or making a professional presentation. They are the programs that help an end-user do a particular task. System software or firmware is software that manages and controls the physical hardware of a comp.. so app. Software can work Productivity suites are business application software. Also software suites. They have 3-5 app. Software (Word, Spread, Data, Presentation, Project) GUI or graphical user interfaces are the most common aspect of an OS because they present data and info in a graphical manner. The GUI on the background is the desktop environment. It consists of windows, menus, ribbons, toolbars, and folders. System software's ability to support multiple software is called MULTITASKING. (Chap 5&6) Spreadsheets have grid of info, capable of calculating and graphing and doing what if analysis.Intersection of a column and row is a cell. Cell is la bled by is column/row location. Cell holds text of numeric. Text are labels or notes. Numeric holds formulas, numbers, and function. Word Processors allow users to make documents. Can also make webpageor intranet. Intranet is an organization to communicate essential info of operations like hr, policies, knowledge Database: software that is contains collection of files which consist of records (row) of data separated by field (columns) that can be queries (questioned) to produce subsets. Corporations store their history in data warehouses. They are relationaldatabases which is called corporate memory. These use database software of historical data. Data can be shared through Cut and Paste (static), Object embedding (static), Object Linking (dynamic) How COMP starts. Loads platforms into memory (aka Booting). Loading a comp for first time is cold boot. Restarted comp is a warm boot. Electricity goes through comp and comp searches for basic input/output system (BIOS). BIOS finds hdd, starts instructions and load OS. OS takes control and configures hardware to settings stored in a database calledregistry. Then system utilities are loaded. It authenticates too. BIOS is embedded in to a computer chip. It runs the same program every time it's turned on (chap 6) System software manages application software by loading it into RAM ::::::::::::::::::::::::::::::::::::::::CONTENT CONTINUED IN THE ATTACHMENT::::::::::::::::::::::::::::::::::::::::::::::::::: [Show More]
Last updated: 3 years ago
Preview 1 out of 52 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$11.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Dec 08, 2020
Number of pages
52
Written in
All
Additional information
This document has been written for:
Uploaded
Dec 08, 2020
Downloads
0
Views
179





ddtete3.png)