
eBook South Korea’s Foreign Aid 1st Edition By Hyo-sook Kim
$ 29
Peds Hesi study guide (NURS5104G0)
$ 18.5
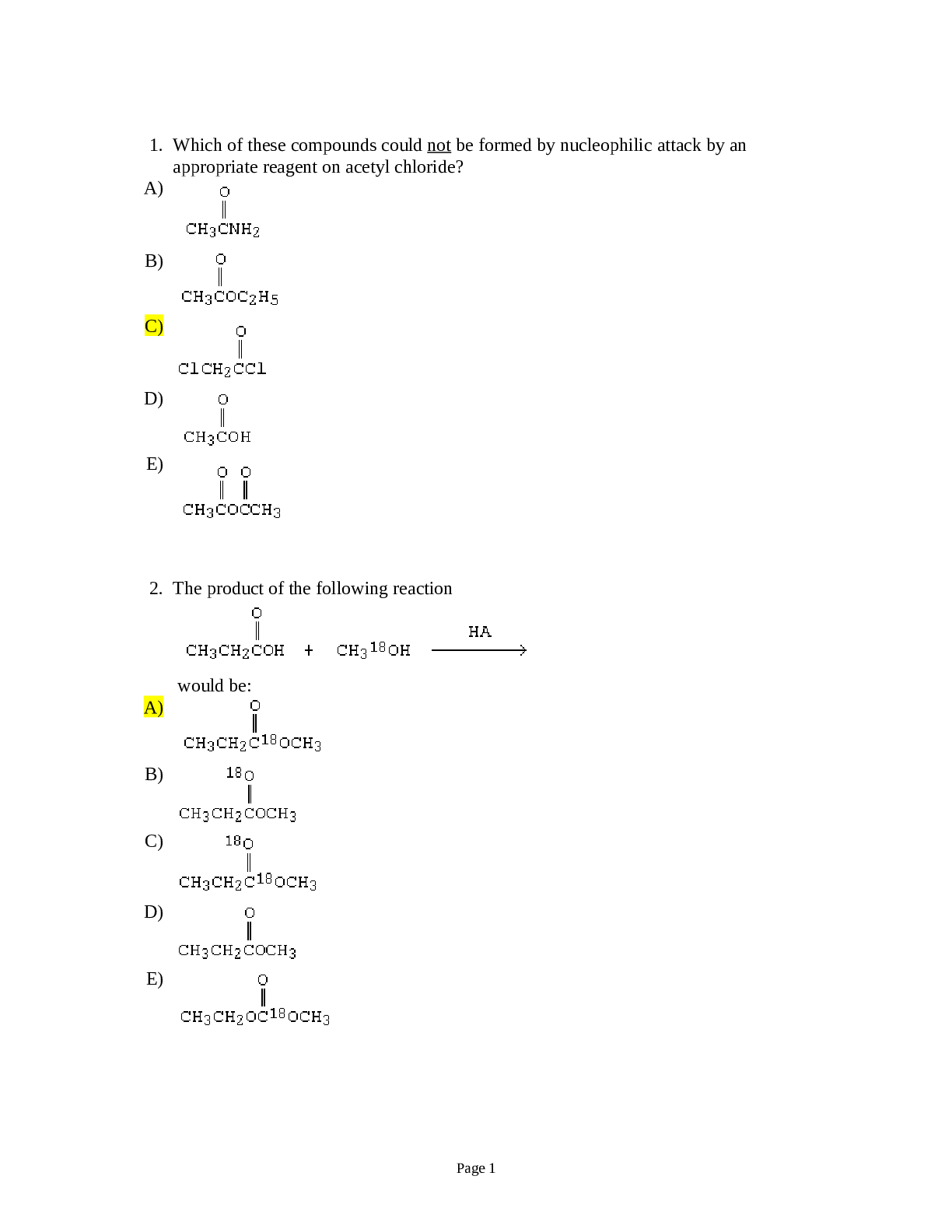
Florida Atlantic University - CHM 2211CHM2211_Practice Final-1.
$ 10

Ati Leadership - Proctored (Complete) Questions With Answers
$ 15

NUR 108 Final exam questions and answers.
$ 15

(WGU D239) ACCT 6100 Advanced Tax Concepts - Objective Assessment Guide Q & S 20242025
$ 12

CompTIA Security+ Study Test Bank
$ 10

ACCT 212 Week 4 Midterm Exam Version 3
$ 10
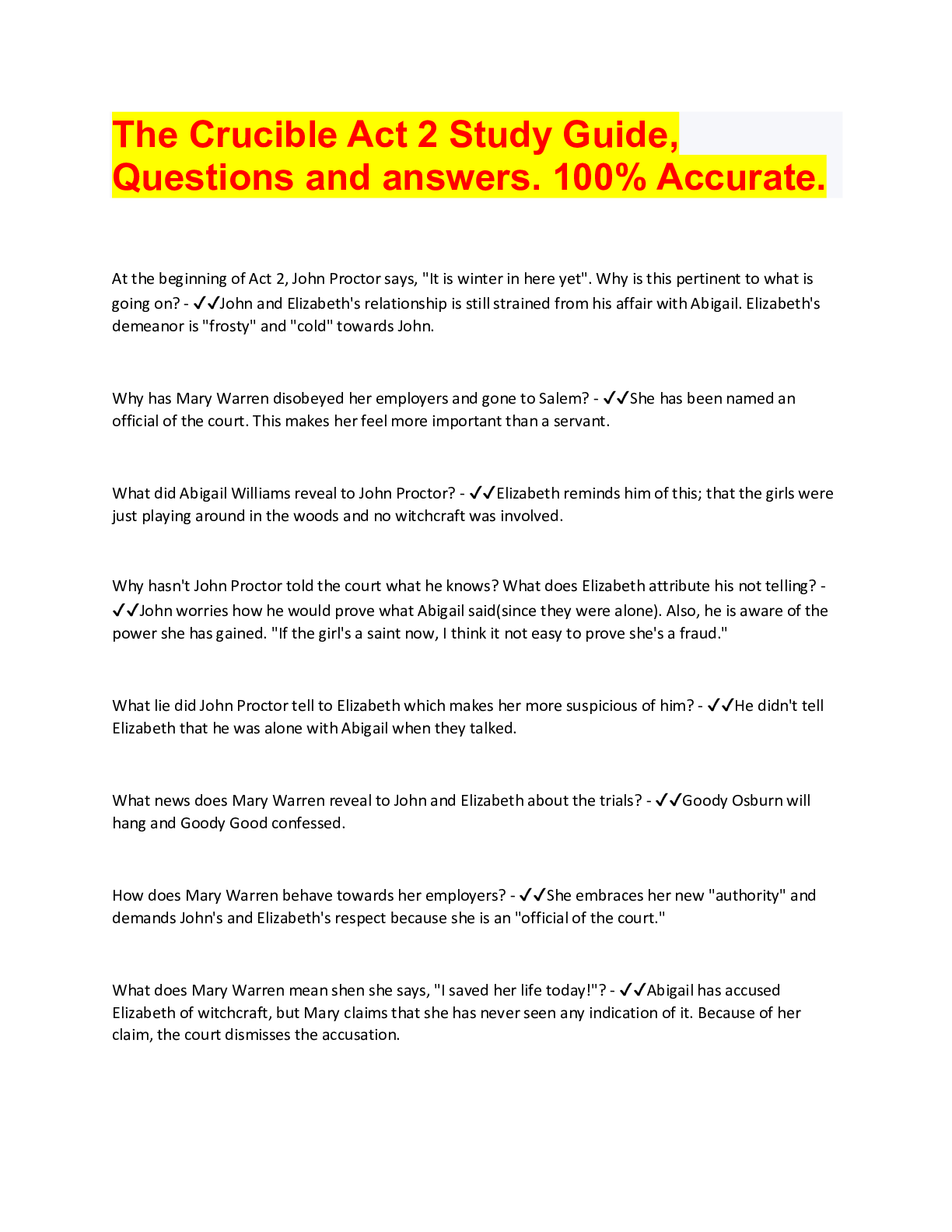
The Crucible Act 2 Study Guide, Questions and answers. 100% Accurate.
$ 4

IHUMAN clinical makeup work UNFOLDING Reasoning Case Study: STUDENT,100% CORRECT
$ 13

ABERCROMBIE & FITCH: IS IT UNETHICAL TO BE EXCLUSIVE?
$ 10
.png)
AMCA Questions and Answers Already Passed
$ 10
.png)
NCLEX Cardiovascular Medications 100% complete Question and Answers
$ 15.5

ATI PN Comprehensive Online Practice 2022/2023 A
$ 45.5

Nursing questions
$ 43

FINA 4358 MODULE 5 ASSIGNMENT QUESTIOND AND ANSWERS | VERIFIED GUIDE
$ 10

HR 2440-Test bank-(elaborations) BUS 310 Human Resource Management
$ 14

NURSING MISC 2021 Cranial Nerves Assessment Chart and Cheat Sheet
$ 12

Rio Salado Community CollegeGBS 220Assignment 10
$ 11

Health Sciences - NURS 220 Module 2 Pharmacology 2021 Revised Study Guide Exam Elaborations Questions and Answers Download to SCORE A
$ 10.5

AVID Certification Test
$ 10

Principles of Microeconomics, A Streamlined Approach, 4th Edition By Robert H. Frank, Ben Bernanke, Kate Antonovics, Ori Heffetz (eBook PDF)
$ 25
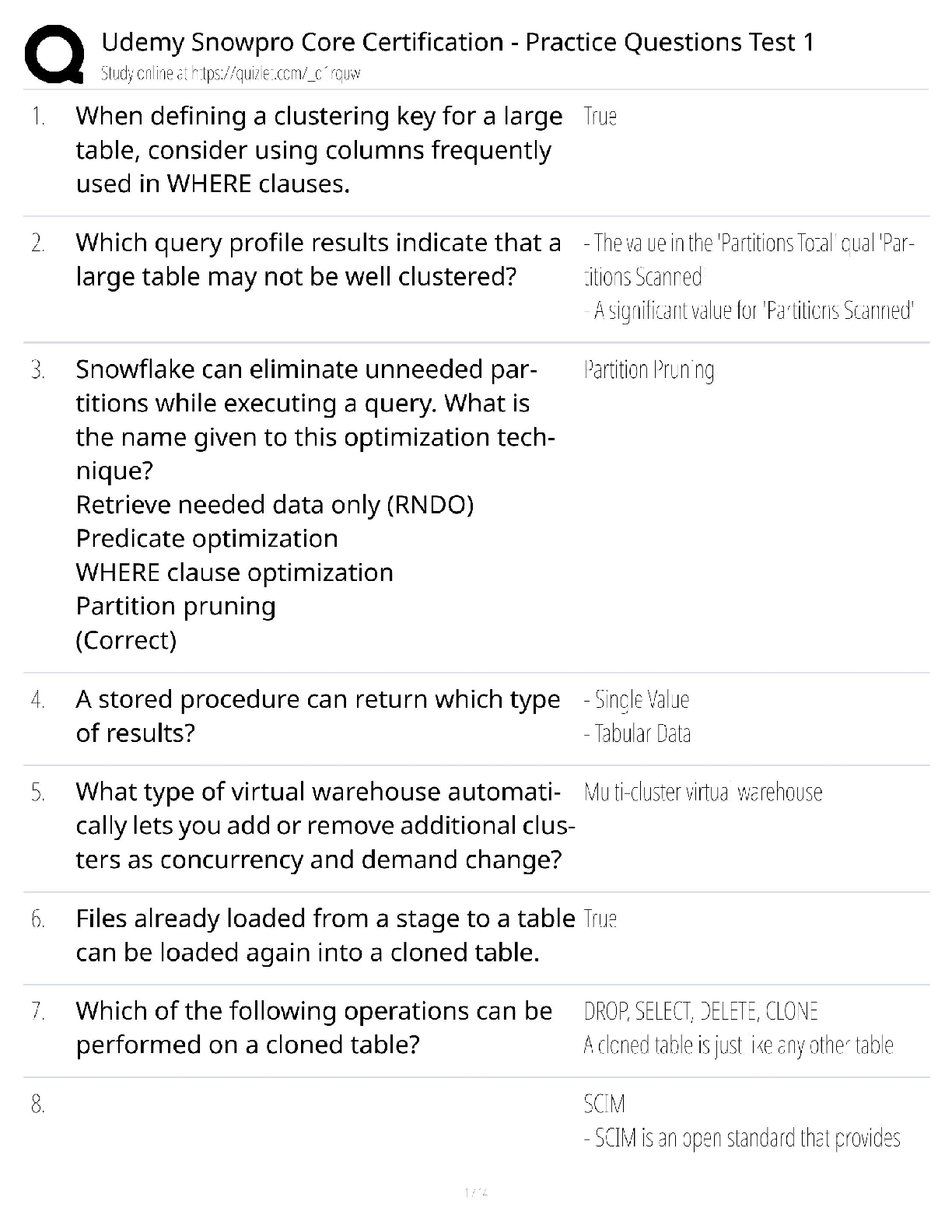
SnowPro Core Certification - Practice Test 1 (2025) / Udemy-Style Questions / Warehouse Optimization & Security / Score 90%+
$ 11

Sophia Macro Unit 1 Challenge 2 Latest 2022 Rated A
$ 10

Pathophysiology Quiz 1 Prep Guide
$ 6.5

[eBook] [PDF] Pharmacology Made Incredibly Easy 5th Edition By Cherie R. Rebar, Nicole M. Heimgartner, Carolyn J. Gersch
$ 25

ATI LPN COMPREHENSIVE PREDICTOR –CORRECTLY UPDATED STUDY GUIDE 2021
$ 18
.png)
CPT Exam Questions and Answers Graded A
$ 10
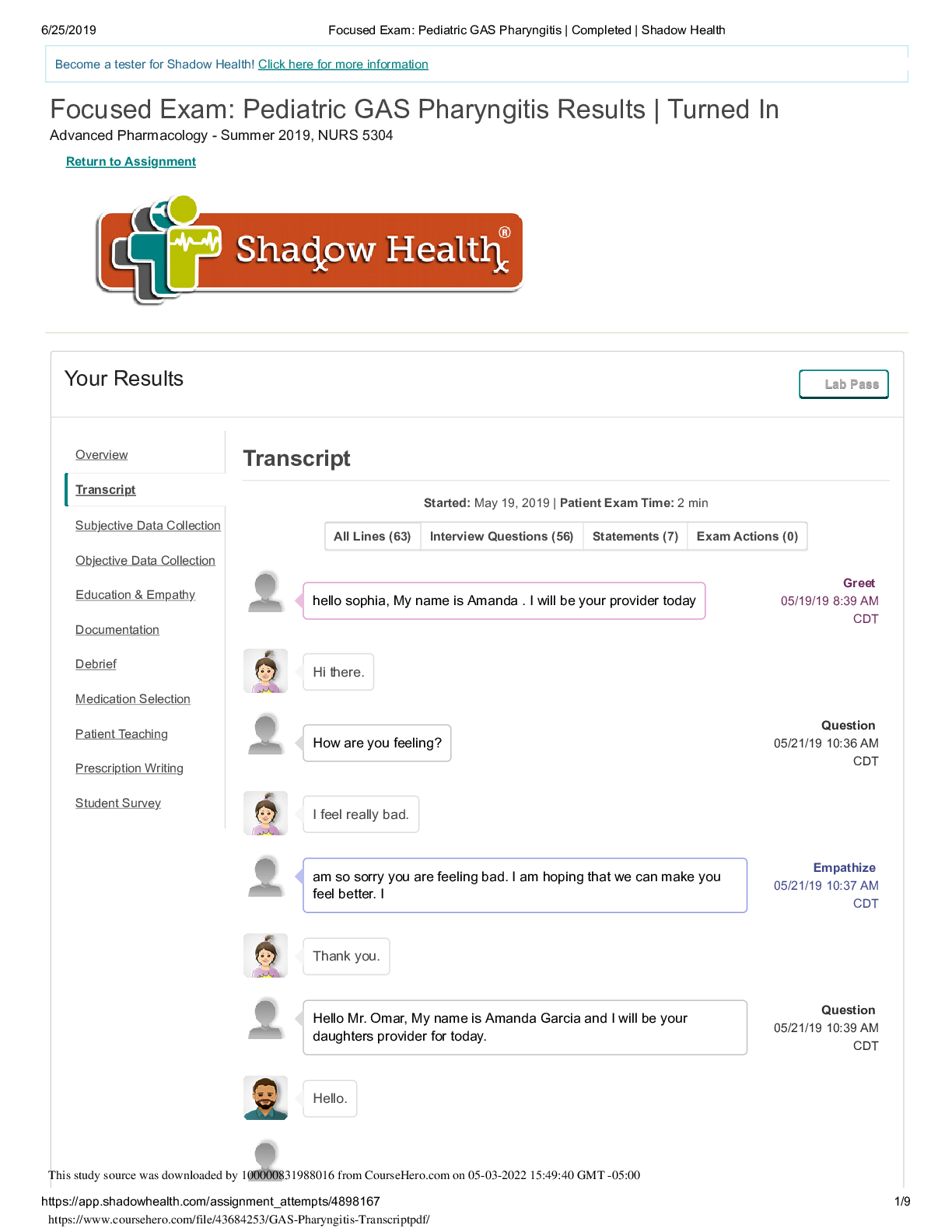
Focused Exam: Pediatric GAS Pharyngitis | Completed | Shadow Health, Transcript [sophia]
$ 12

AQA GCSE CHEMISTRY 8462/2H Higher Tier Paper 2 Question Paper 2021
$ 8
PEDS NR 328 Peds_Quiz_7
$ 5

BA 2900 (Introduction to Business) Midterm Exam Q & S 2024
$ 12

INTST 101 Introduction to International Studies Intst 101 Study Notes. - University of Waterloo.
$ 7.5

NR 601 Week 4 Midterm (Practice Questions and Answers)




























