Information Technology > QUESTIONS & ANSWERS > SPēD SFPC: General Questions and Answers Already Graded A (All)
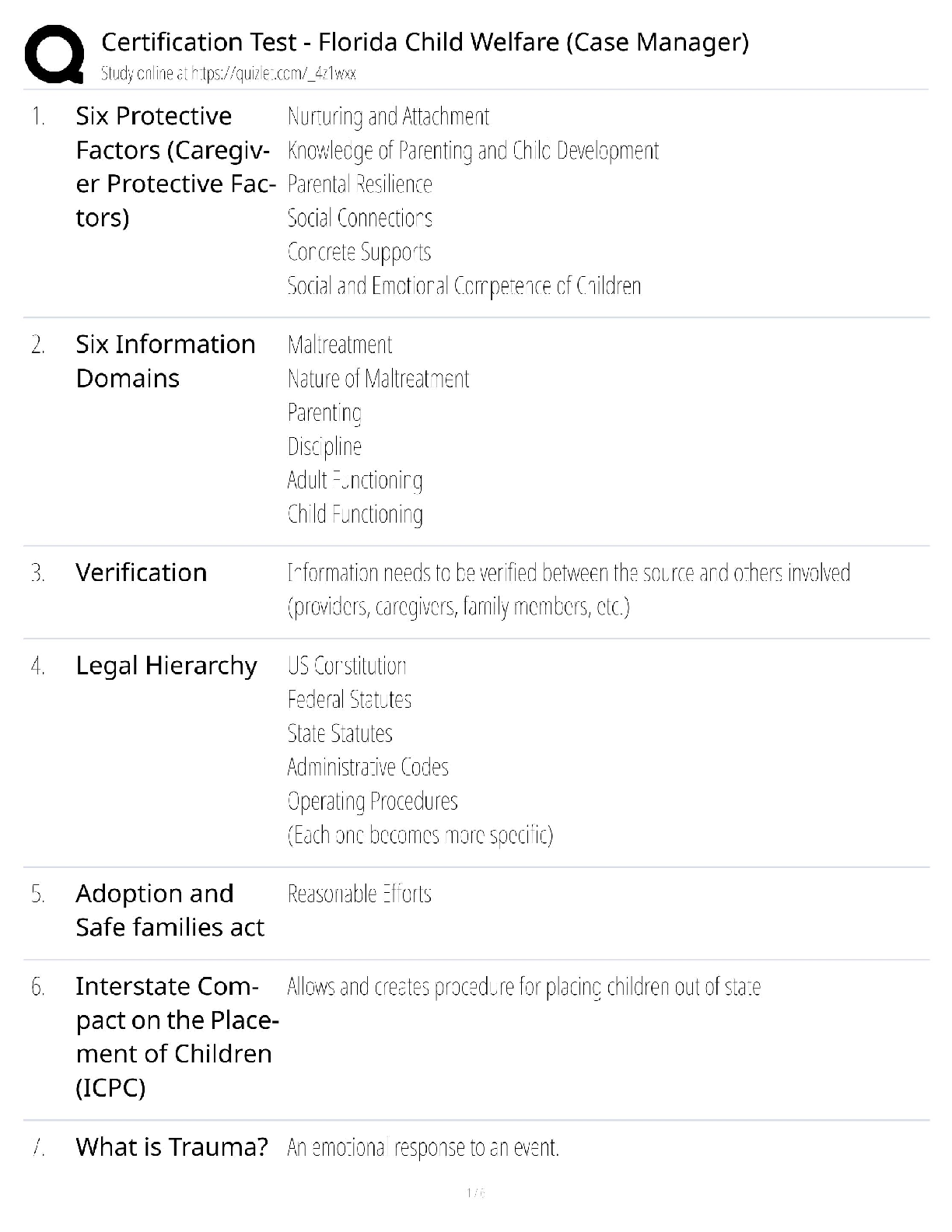
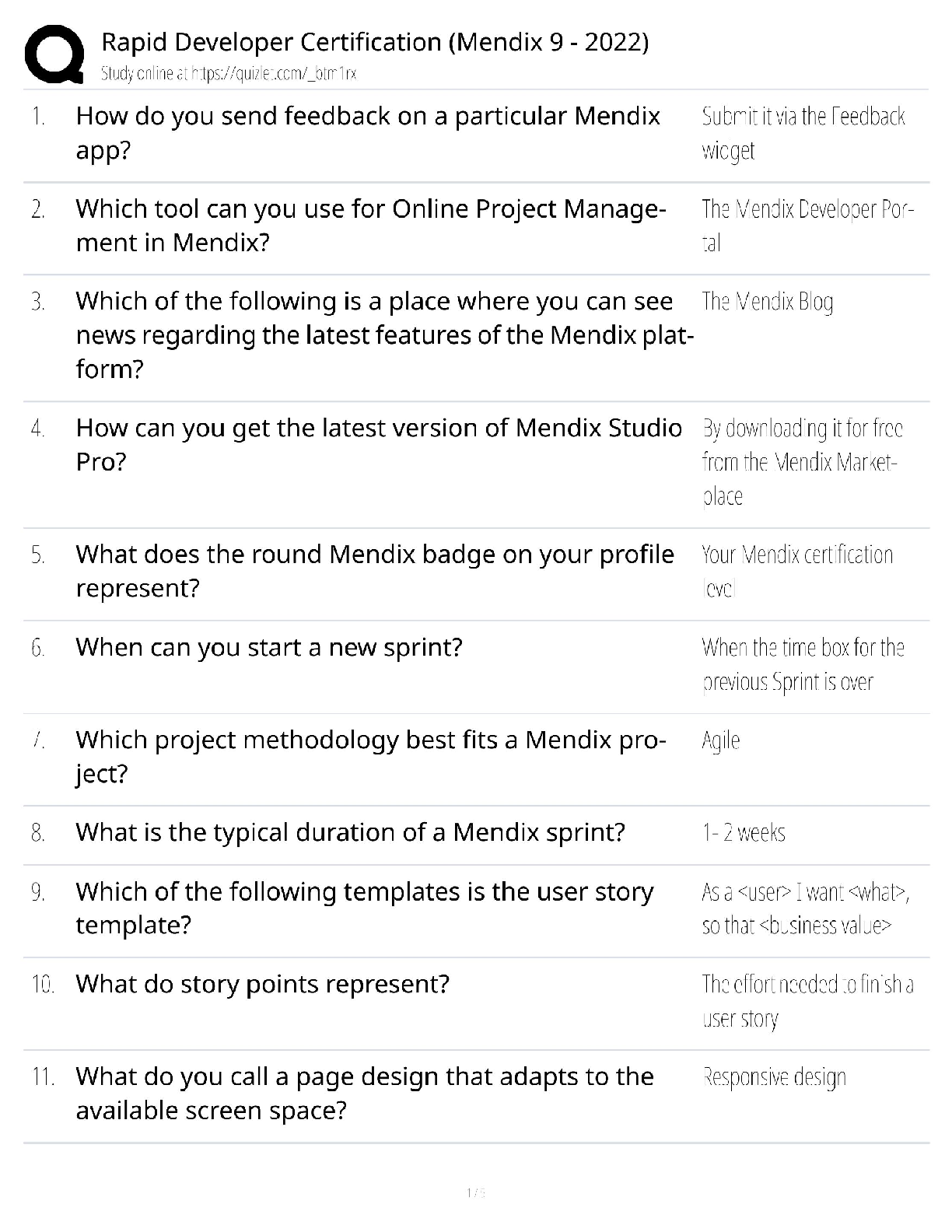
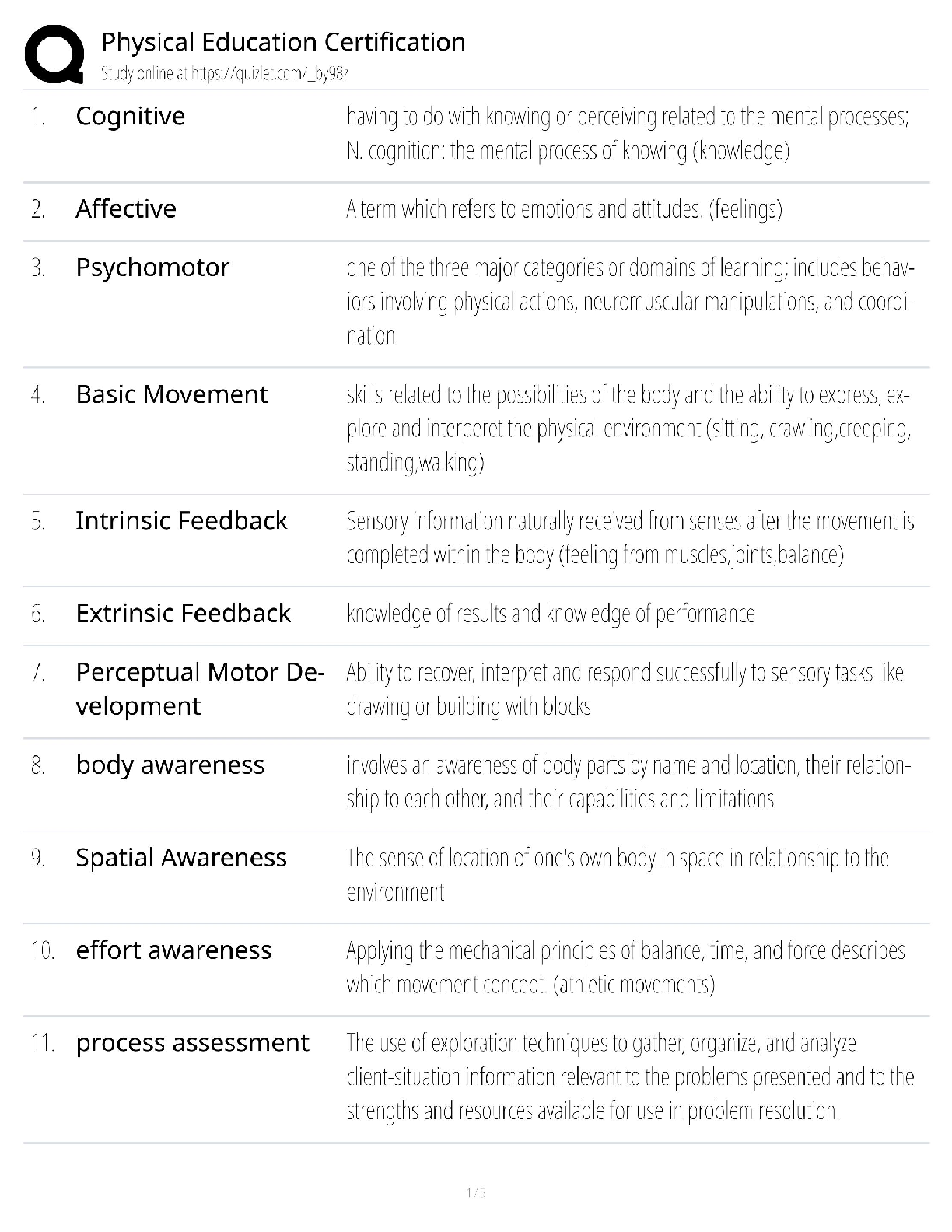
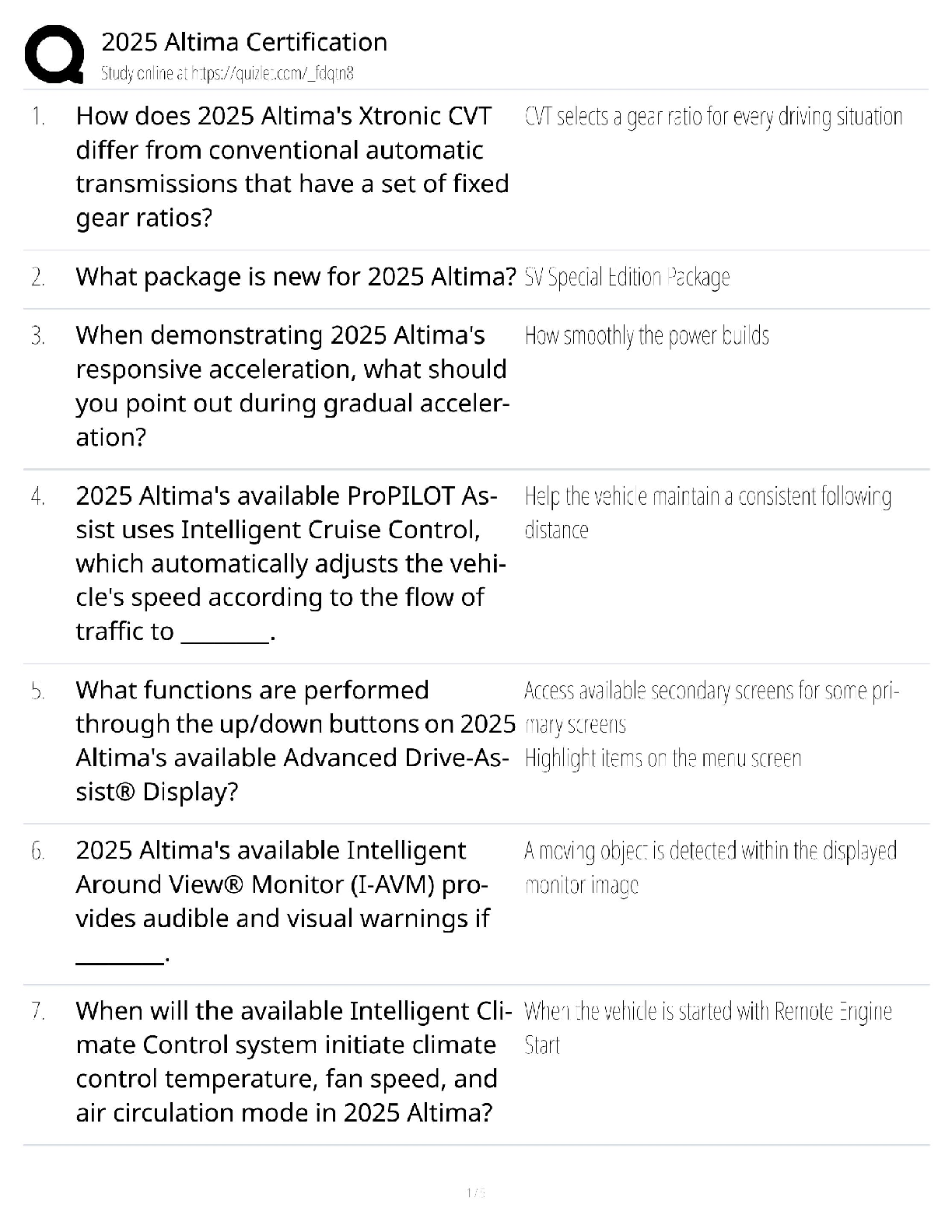
SPēD SFPC: General Questions and Answers Already Graded A
Document Content and Description Below
SPēD SFPC: General Questions and Answers Already Graded A Principle incident/events required to be reported to DoD counterintelligence (CI) organizations Correct Answer-espionage, sabotage, terror ... ism, cyber Indicators of insider threats Correct Answer-1. Failure to report overseas travel or contact with foreign nationals 2. Seeking to gain higher clearance or expand access outside the job scope 3. Engaging in classified conversations without a need to know 4. Working hours inconsistent with job assignment or insistence on working in private 5. Exploitable behavior traits 6. Repeated security violations 7. Attempting to enter areas not granted access to 8. Unexplainable affluence/living above one's means 9. Anomalies (adversary taking actions which indicate they are knowledgeable to information) 10. Illegal downloads of information/files Elements that should be considered in identifying Critical Program Information Correct AnswerElements which if compromised could: 1. cause significant degradation in mission effectiveness 2. shorten the expected combat-effective life of the system 3. reduce technological advantage 4. significantly alter program direction or 5. enable an adversary to defeat, counter, copy, or reverseengineer the technology or capability Asset, threat, vulnerability, risk, countermeasures Correct Answer-Elements that a security professional should consider when assessing and managing risks to DoD assets The three categories of Special Access Programs Correct Answer-acquisition, intelligence, and operations and support Three different types of threats to classified information Correct Answer-Insider Threat, Foreign Intelligence Entities (FIE) and Cybersecurity Threat The concept of an insider threat Correct Answer-An employee who may represent a threat to national security. These threats encompass potential espionage, violent acts against the Government or the nation, and unauthorized disclosure of classified information, including the vast amounts of classified data available on interconnected United States Government computer networks and systems. The purpose of the Foreign Visitor Program Correct Answer-To track and approve access by a foreign entity to information that is classified; and to approve access by a foreign entity to information that is unclassified, related to a U.S. Government contract, or plant visits covered by ITAR. [Show More]
Last updated: 3 years ago
Preview 1 out of 5 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

SPēD SFPC BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
SPēD SFPC BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
By Nutmegs 2 years ago
$22
13
Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 07, 2022
Number of pages
5
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 07, 2022
Downloads
0
Views
125








.png)