Computer Science > QUESTIONS & ANSWERS > WGU Information Security and Assurance - C725 Questions and Answers Latest Updated 2022 (All)
WGU Information Security and Assurance - C725 Questions and Answers Latest Updated 2022
Document Content and Description Below
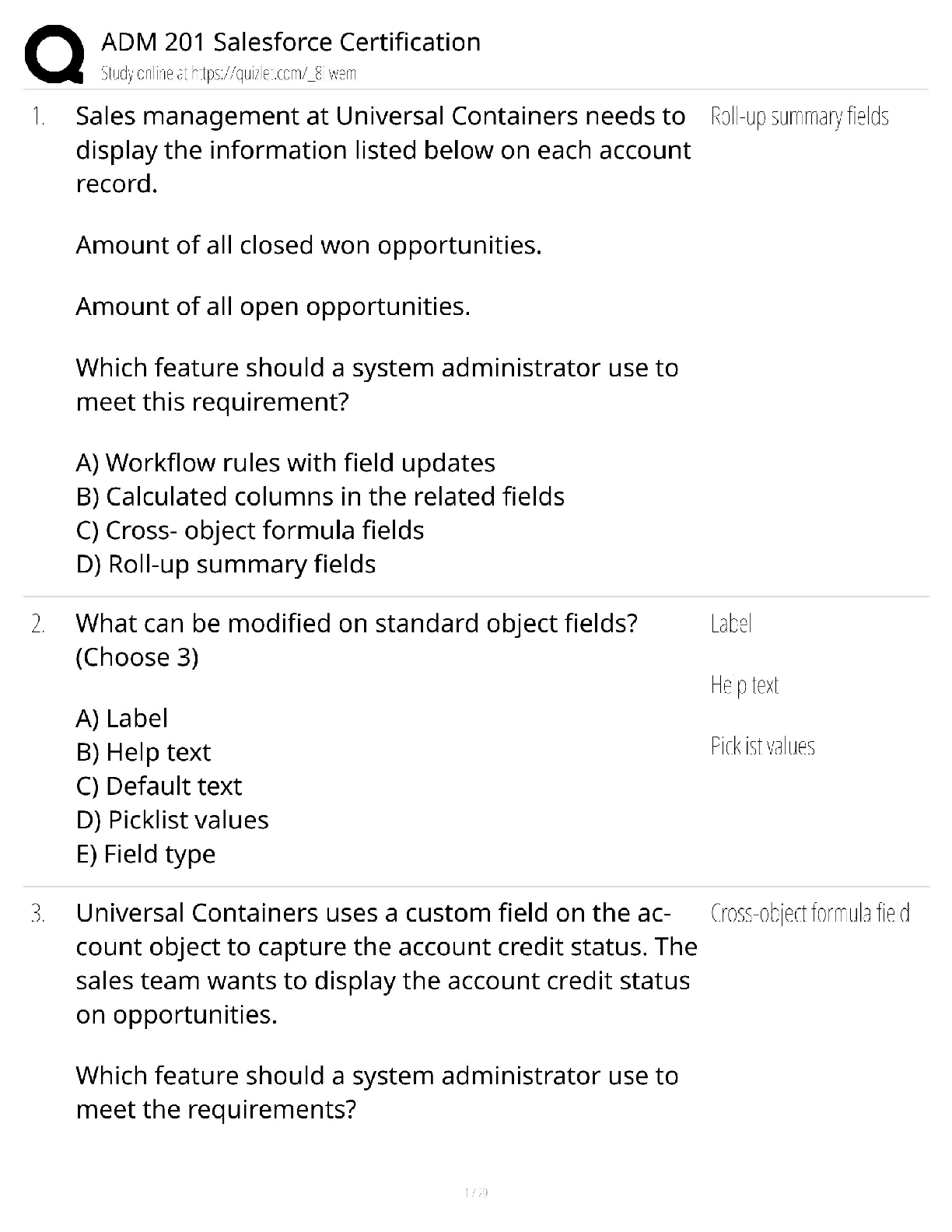
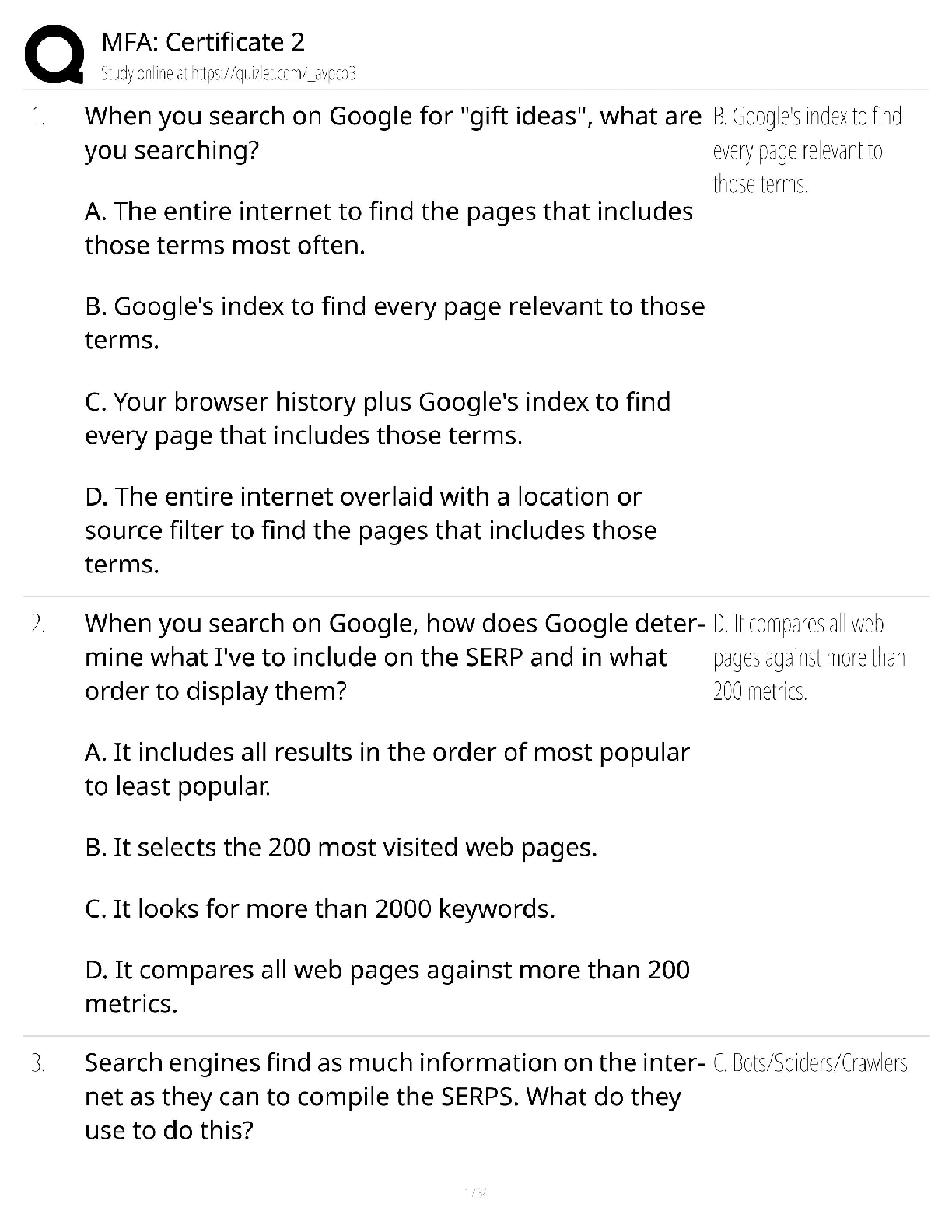
WGU Information Security and Assurance - C725 Questions and Answers Latest Updated 2022 Which two passwords are the weakest? Pa$$w0Rd%^78 Love@$MySon80 C@1Il@VEm1 Password1234 ✔✔Love@$MySon ... 80 Password1234 Which groups typically report to the chief security officer (CSO)? ✔✔Security engineering and operations What is the formula for computing single loss expectancy ✔✔SLE = AV x EF [Single Loss Expectancy = Asset Value x Exposure Factor] A violation of the "separation of duties" principle arises when the security systems software is accessed by which of the following individuals? ✔✔Systems programmer An example of the separation of duties of a computer operation is when a company has one environment for the software developers, another for quality assurance testing, and a third for production, or the environment that end users access, to perform their duties. As software is deemed ready, it is promoted from environment to environment by systems and security administration personnel, not the programmer. This separation of duties prevents a programmer from launching into production software that can perpetrate fraud or cause damage to production data or resources. What is the formula for computing annualized loss expectancy? ✔✔ALE=SLE x ARO Single Loss Expectancy x Annual Rate of Occurrence What is the first thing you should do when a disaster Strikes? ✔✔Ensure the people are safe. Provide two examples of devices that might be used to harden a system ✔✔Computer-safe fire suppression system and uninterruptible power supplies What are some of the elements that should be included in emergency response guidelines? ✔✔Immediate response procedures, notification procedures, and secondary response procedures. What is the first step that individuals responsible for the development of a business continuity plan should perform? ✔✔Business organization analysis The business organization analysis helps the initial planners select appropriate BCP team members and then guides the overall BCP process. What disaster recovery principle best protects your organization against hardware failure? ✔✔Redundancy Redundant systems/components provide protection against the failure of one particular piece of hardware. A company consults a best practices manual from its vendor while deploying a new IT system. Which type of document does this exemplify? ✔✔Guildlines What is the main objective of separation of duties? ✔✔To ensure that no single individual can compromise a system Separation of duties is the prevention of conflict of interest, wrongful acts, fraud, abuse, and errors. Also, it is the detection of control failures that include security breaches, information theft, and circumvention of security controls. If a programmer is restricted from updating and modifying production software, what is this an example of? ✔✔Least privilege The principle of least privilege, a concept in computer security, provides minimal user profile privileges based on users' job necessities. What is Fail-Secure system controls? ✔✔Fail-secure system controls preserve the state of the system before the crash and prevent further damage [Show More]
Last updated: 3 years ago
Preview 1 out of 6 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
WGU C725 Bundled Exams Questions and Answers with Complete Solutions
WGU C725 Bundled Exams Questions and Answers Latest Updated 2022 Rated A
By Nutmegs 3 years ago
$20
13
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
6
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
191








.png)