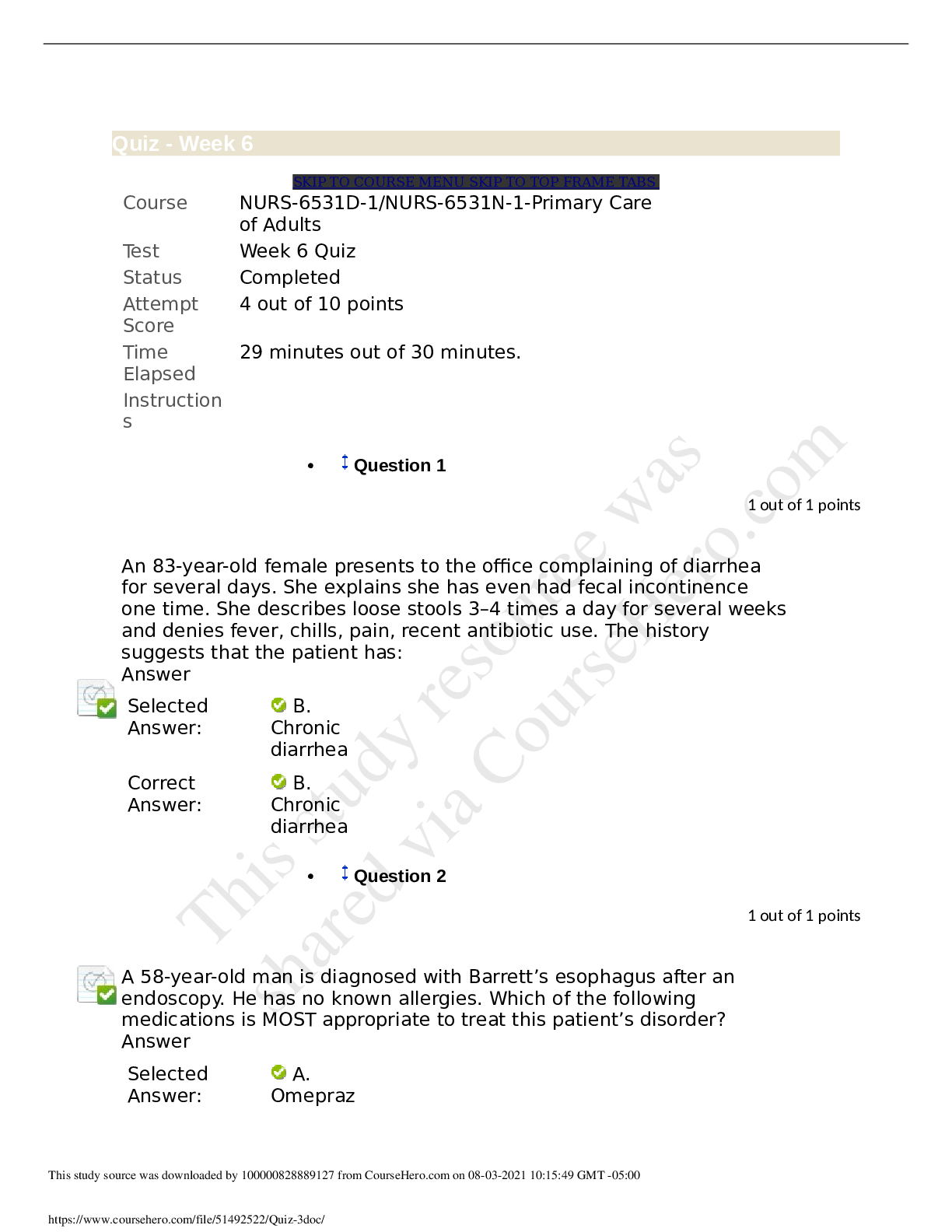
Sociology > QUESTIONS & ANSWERS > WGU C836 pre assessment questions and answers latest updated 2022 (All)
WGU C836 pre assessment questions and answers latest updated 2022
Document Content and Description Below
WGU C836 pre assessment questions and answers latest updated 2022 Port scanner ✔✔Which tool can be used to map devices on a network, along with their operating system types and versions? SQL I... njection ✔✔Which web attack is a server-side attack? Availability ✔✔A company has had several successful denial of service (DoS) attacks on its email server. Which security principle is being attacked? SQL Injection ✔✔Which web attack is possible due to a lack of input validation? Encryption ✔✔Which file action implements the principle of confidentiality from the CIA triad? Integrity ✔✔An organization plans to encrypt data in transit on a network. Which aspect of data is the organization attempting to protect? Integrity ✔✔Which aspect of the CIA triad is violated by an unauthorized database roll back or undo? Availability ✔✔A company's website has suffered several denial of service (DoS) attacks and wishes to thwart future attacks. Which security principle is the company addressing? Availability ✔✔An organization has a requirement that all database servers and file servers be configured to maintain operations in the presence of a failure. Which principle of the CIA triad is this requirement implementing? Operations ✔✔A company's website policy states that "To gain access to the corporate website, each employee must provide a valid user name and password, and then answer one of six security questions accurately." Which type of security does the policy address? Attribute-based ✔✔A company wants to update its access control policy. The company wants to prevent hourly employees from logging in to company computers after business hours. Which type of access control policy should be implemented? Relocate the algorithm to encrypted storage. ✔✔A new software development company has determined that one of its proprietary algorithms is at a high risk for unauthorized disclosure. The company's security up to this point has been fairly lax. Which procedure should the company implement to protect this asset? Restrict account permissions. ✔✔How can an [Show More]
Last updated: 3 years ago
Preview 1 out of 6 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
.png)
WGU C836 BUNDLED EXAMS COMPLETE QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
WGU C836 BUNDLED EXAMS COMPLETE QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
By Nutmegs 3 years ago
$20
13
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
6
Written in
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
113

.png)