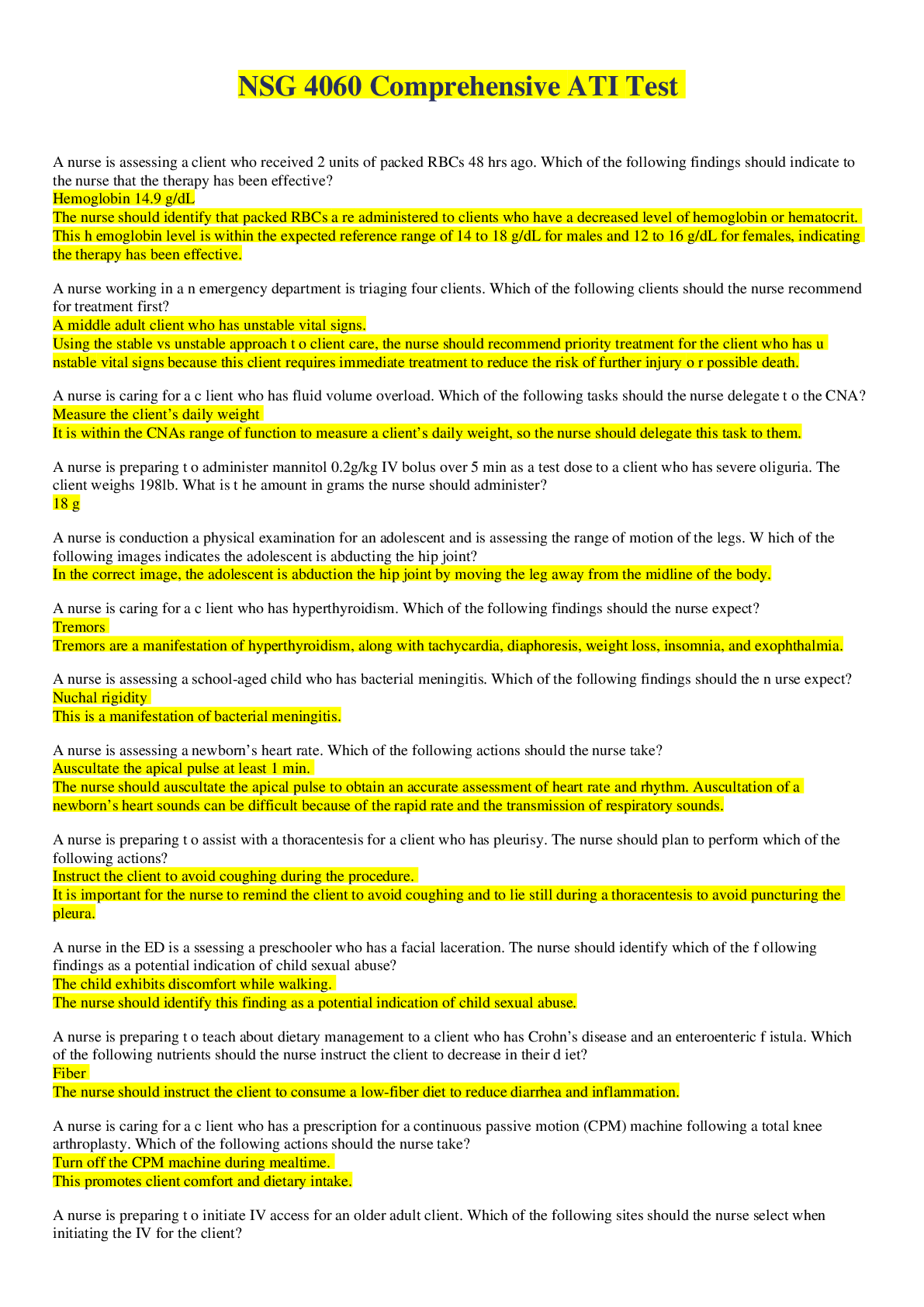
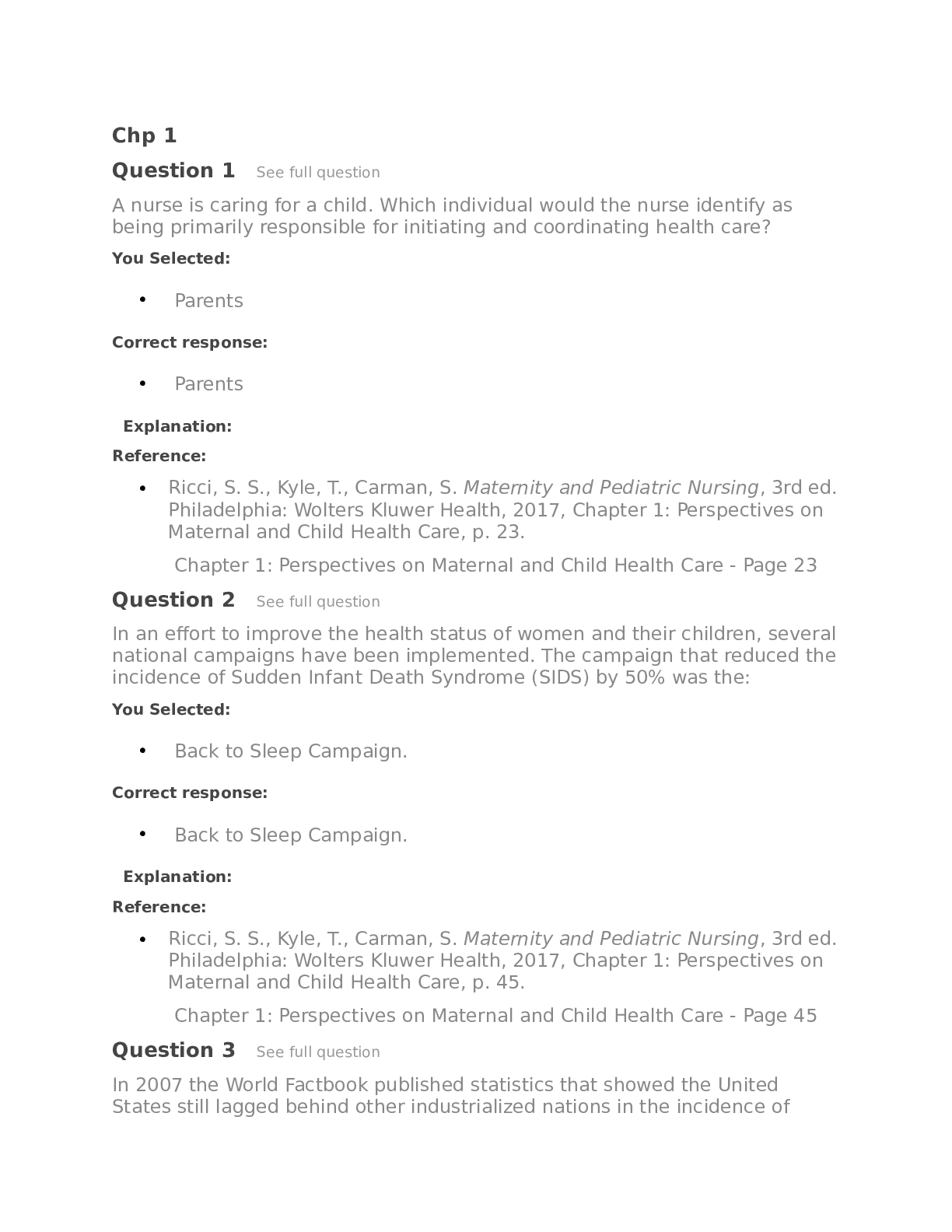
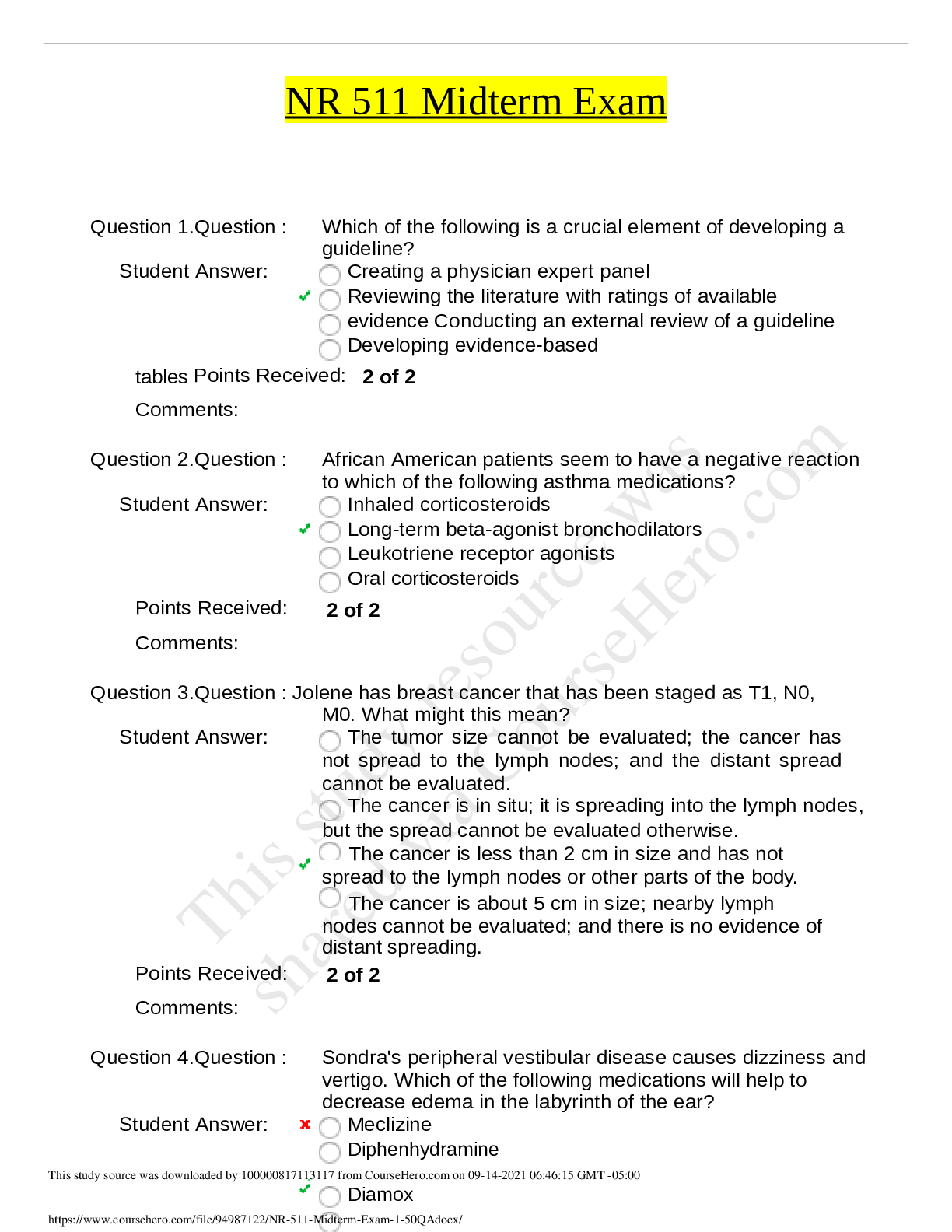
Sociology > QUESTIONS & ANSWERS > WGU C836 OA Study Guide (Overly Informative) Questions and Answers Rated A+ (All)
WGU C836 OA Study Guide (Overly Informative) Questions and Answers Rated A+
Document Content and Description Below
WGU C836 OA Study Guide (Overly Informative) Questions and Answers Rated A+ CIA Triad ✔✔Confidentiality, Integrity, Availability Parkerian hexad ✔✔Where the CIA triad consists of confident... iality, integrity, and availability, the Parkerian hexad consists of these three principles, as well as possession or control, authenticity, and utility Confidentiality ✔✔Refers to our ability to protect our data from those who are not authorized to view it. Confidentiality can be compromised by the loss of a laptop containing data, a person looking over our shoulder while we type a password, an e-mail attachment being sent to the wrong person, an attacker penetrating our systems, or similar issues. Integrity ✔✔Refers to the ability to prevent our data from being changed in an unauthorized or undesirable manner. This could mean the unauthorized change or deletion of our data or portions of our data, or it could mean an authorized, but undesirable, change or deletion of our data. To maintain integrity, we not only need to have the means to prevent unauthorized changes to our data but also need the ability to reverse authorized changes that need to be undone. Availability ✔✔refers to the ability to access our data when we need it. Loss of availability can refer to a wide variety of breaks anywhere in the chain that allows us access to our data. Such issues can result from power loss, operating system or application problems, network attacks, compromise of a system, or other problems. When such issues are caused by an outside party, such as an attacker, they are commonly referred to as a denial of service (DoS) attack. Possession or Control ✔✔Refers to the physical disposition of the media on which the data is stored. This enables us, without involving other factors such as availability, to discuss our loss of the data in its physical medium An example is data store be on multiple devices and there could be numerous versions. Authenticity ✔✔Attribution as to the owner or creator of the data in question. Authenticity can be enforced through the use of digital signatures. Utility ✔✔Refers to how useful the data is to us. Interception ✔✔Interception attacks allow unauthorized users to access our data, applications, or environments and are primarily an attack against confidentiality. Interception might take the form of unauthorized file viewing or copying, eavesdropping on phone conversations, or reading e-mail, and can be conducted against data at rest or in motion. Properly executed, interception attacks can be very difficult to detect. Affects Confidentiality Interruption ✔✔Interruption attacks cause our assets to become unusable or unavailable for our use, on a temporary or permanent basis. Interruption attacks often affect availability but can be an attack on integrity as well. In the case of a DoS attack on a mail server, we would classify this as an availability attack. Affects Integrity and availability Modification ✔✔Modification attacks involve tampering with our asset. If we access a file in an unauthorized manner and alter the data it contains, we have affected the integrity of the data contained in the file. [Show More]
Last updated: 3 years ago
Preview 1 out of 20 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
.png)
WGU C836 BUNDLED EXAMS COMPLETE QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
WGU C836 BUNDLED EXAMS COMPLETE QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
By Nutmegs 3 years ago
$20
13
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
20
Written in
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
142

.png)














.png)
.png)





