Programming > QUESTIONS & ANSWERS > New York University CSCI-SHU MISC Introduction to Programming and Problem Solving . CS6823+Sample Fi (All)
New York University CSCI-SHU MISC Introduction to Programming and Problem Solving . CS6823+Sample Final_1 AnswersNetwork Security Sample Final #1 Answers
Document Content and Description Below
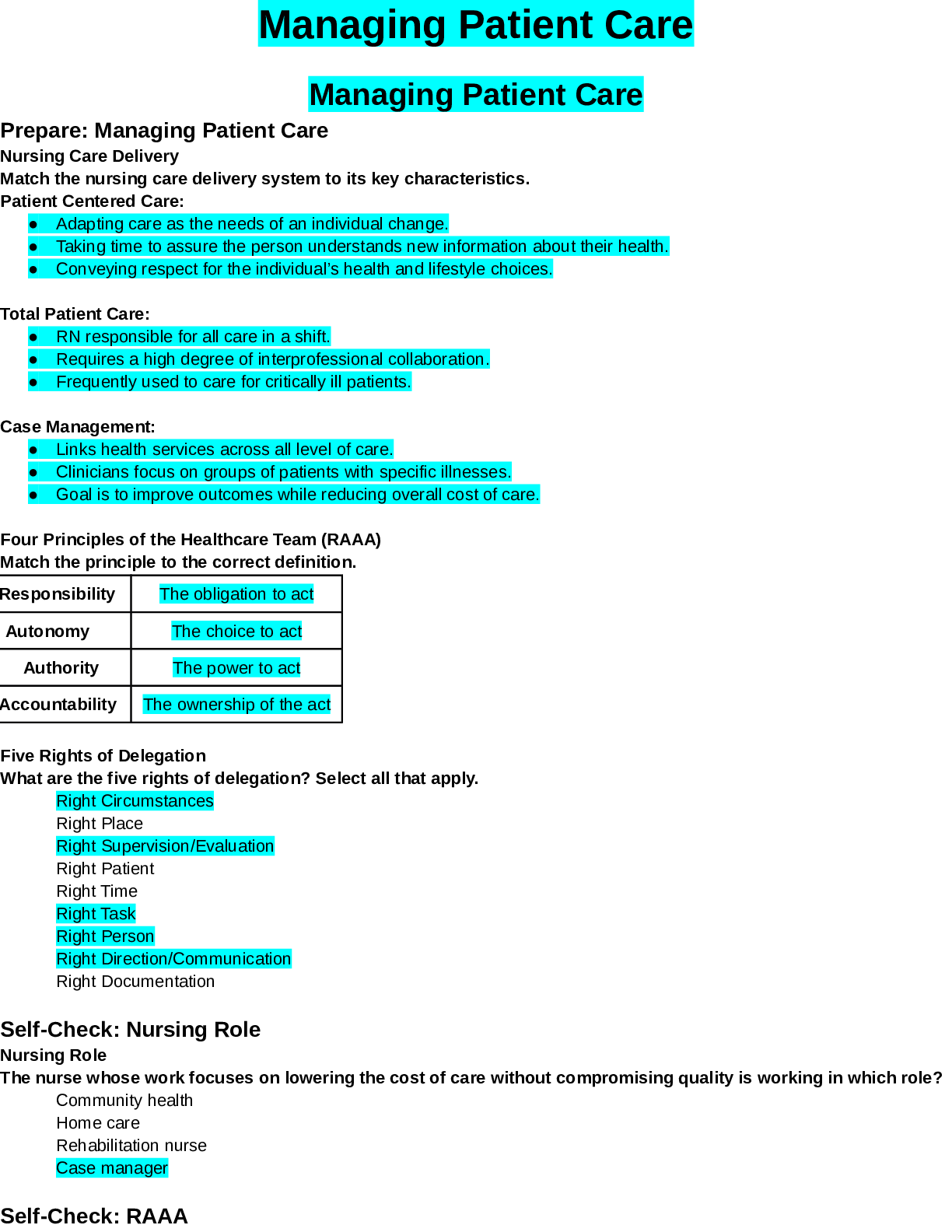
New York University CSCI-SHU MISC CS6823+Sample Final_1 AnswersNetwork Security Sample Final #1 Answers 1. SSL/TLS: 1a. [4 pts] Suppose that in the SSL Full Handshake, as shown, the Finished mes ... sages do not contain a checksum of all previous handshake messages. Describe two ways that an attacker can take advantage of this flaw. Although the attacker can MITM the connection, the Attacker still cannot see the data as the attacker cannot forge a valid certificate, but he can change some messages: 1. Version rollback attack – force the client to offer an earlier version of SSL which has more vulnerabilities 2. CipherSpec rollback – force the client to offer weaker version of cipherspecs so it can be broken easier. 1b. [4 pts] Describe each algorithm of this ciphersuite its purpose in SSL/TLS: TLS_DHE_RSA_WITH_AES_128_CBC_SHA DHE – client/server uses DH to exchange keys for each session. CLIENT SIDE SERVER SIDE 2. IPSec: 2a-2d. [6 pts] Identify the IPSec protocol and mode for each of the four items. 2e. [2 pts] What major protocol changes are required for IPSec to be used with The internal subnet 10.10.111.0/24 includes the HTTP Proxy Gateway and the SIEM Server. The DMZ includes the Web, SFTP, and DNS servers. There are two firewalls: an interior firewall that protects the internal network, and an exterior firewall that protects the DMZ. Write the IPTable commands for both firewalls to implement the following security policy on the interior firewall and exterior firewall. All the rules must work together. Place your final answers on the attached sheets. Stateful rules required for full points. 3. IPTables: 3a. [9 pts] Both firewalls need to send syslog messages (TCP 6514) to the SIEM (10.10.111.10) from the eth0 interface. Syslog messages are initiated from the firewalls to the SIEM. No host may access the firewalls and the firewalls may not access any other host aside from the SIEM. 3b. [8 pts] All HTTP traffic (TCP 80) initiated from the 10.10.111.0 network to the Internet must go through the HTTP Proxy Gateway. The Internet is not allowed to reach the internal network. 3c. [8 pts] The Internal network has full access to the DMZ, but the Internet can only initiate connections to the servers in the DMZ in these specific ports: Web (TCP 80), SFTP (TCP 22), and DNS (UDP 53) Interior Firewall iptables -A INPUT -m conntrack --ctstate ESTABLISHED -j ACCEPT 4. Snort: Explain the purpose of the following SNORT rules and why the rule works 4a. [2pts] alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:”ICMP PING NMAP”; dsize: 0; itype: 8;) 4b. [2pts] alert tcp $HOME_NET any -> any 80 (msg:”Bit Torrent Client download"; uricontent:"BitTorrent"; uricontent:"\.exe";) 4c. [2pts] Alert tcp $HOME_NET any -> $EXTERNAL_NET any (msg:"Bit Torrent client usage"; content:"|00 00 40 09 07 00 00 00|"; offset:0; depth:4; ) 5. DHCP: 10.40.111.0/24 is a subnet that uses DHCP to assign IP addresses. The switch is configured with port security enabled. Be sure to state pertinent details about the packet, such as the source MAC, source IP, destination MAC, and destination IP. DHCP Discovery (Broadcast) DHCP Offer (Unicast) DHCP Request (Broadcast) DHCP Ack (Unicast) 5a. [6 pts] What would the Attacker have to do using the DHCP protocol to set up a MITM attack between the Client and the Internet? In other words, to have access to all the traffic going to/from the Internet and to/from the Client? 5b. [3 pts] What would the Attacker have to do using the DHCP protocol to deny any clients from joining the network? 6. Authentication: Apple iMessage is a messaging service for Apple devices that supports text and photos. Message sizes can be up to several megabytes for photos. Apple claims that iMessages have end-to-end encryption between devices and thus Apple cannot read the messages. When iMessage is enabled, the device generates a public/private key pair on the device, and sends the public key to Apple for storage. Since Apple is the delivery service, all devices authenticate to Apple. 6a. [3 pts] Describe one possible way in which the device and Apple can mutually authenticate to each other 6b. [3 pts] Describe one possible way in which messages can be sent between two devices by using public/private keys after authenticating to Apple. 6c. [3 pts] What’s the root of trust in this communication system? In other words, does this system require unconditional trust of something? 6d. [3 pts] Since the public key is stored by Apple, how can Apple perform a MITM attack? ACME Corporation has a WEP Wi-Fi network for employees only. The WEP AP is configured with a strong random password, MAC address filtering, and preshared key for authentication. Suppose Trudy is parked outside ACME. 7a. [3 pts] How can Trudy bypass the MAC address filtering? 7b. [6 pts] Explain an attack that Trudy can use to deploy a rogue AP to the network without obtaining the WEP key. 8a. [6 pts] Recall the process of reconnaissance where nmap can be used to scan a large range of IPv4 addresses to find targets. Describe three methods to find IP addresses in an IPv6 network. 8b. [4 pts] Discuss two reasons why IPv6 Privacy Extension should be di [Show More]
Last updated: 3 years ago
Preview 1 out of 12 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$9.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
12
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
60