Computer Science > QUESTIONS & ANSWERS > WGU C840 - Digital Forensics Questions and Answers Latest Updated 2022 (All)
WGU C840 - Digital Forensics Questions and Answers Latest Updated 2022
Document Content and Description Below
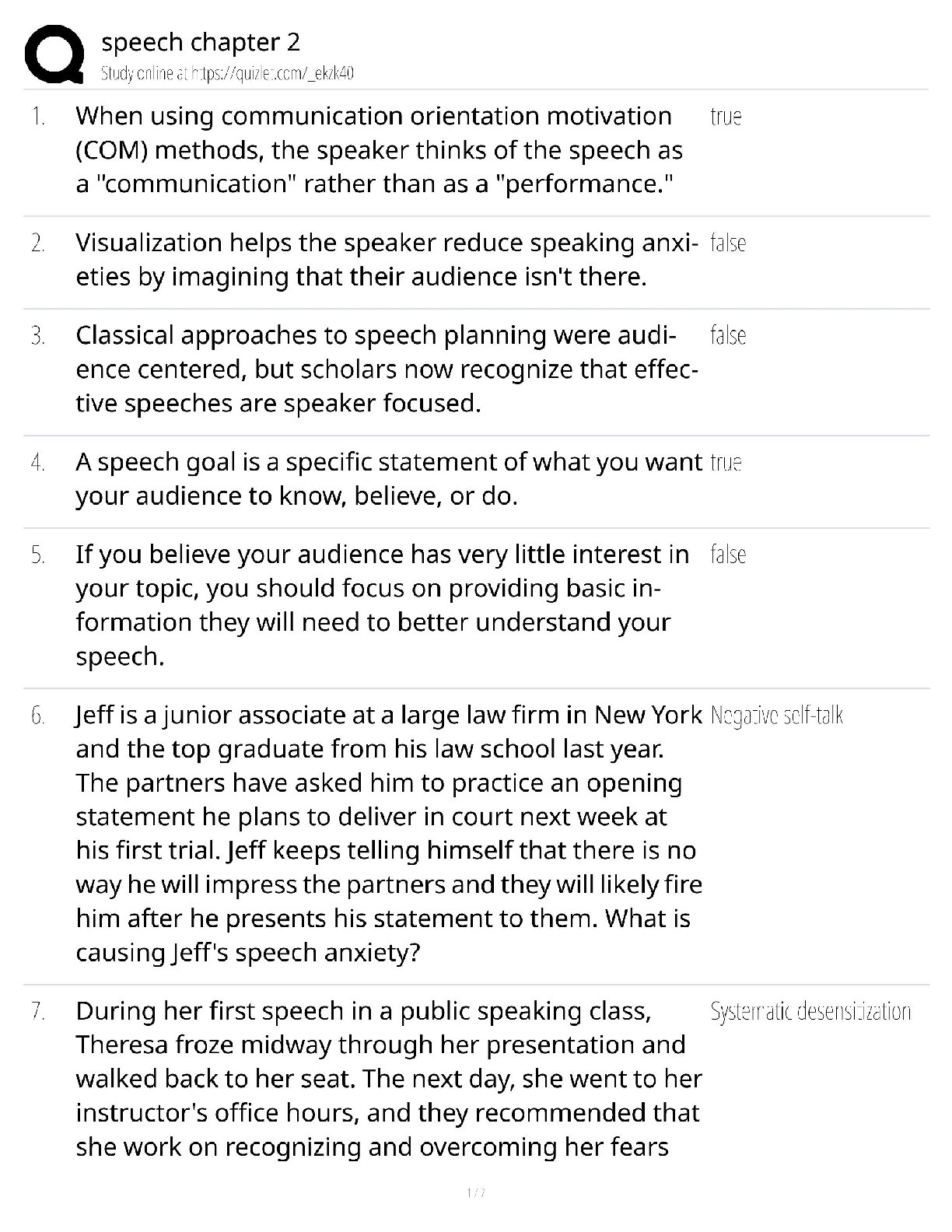
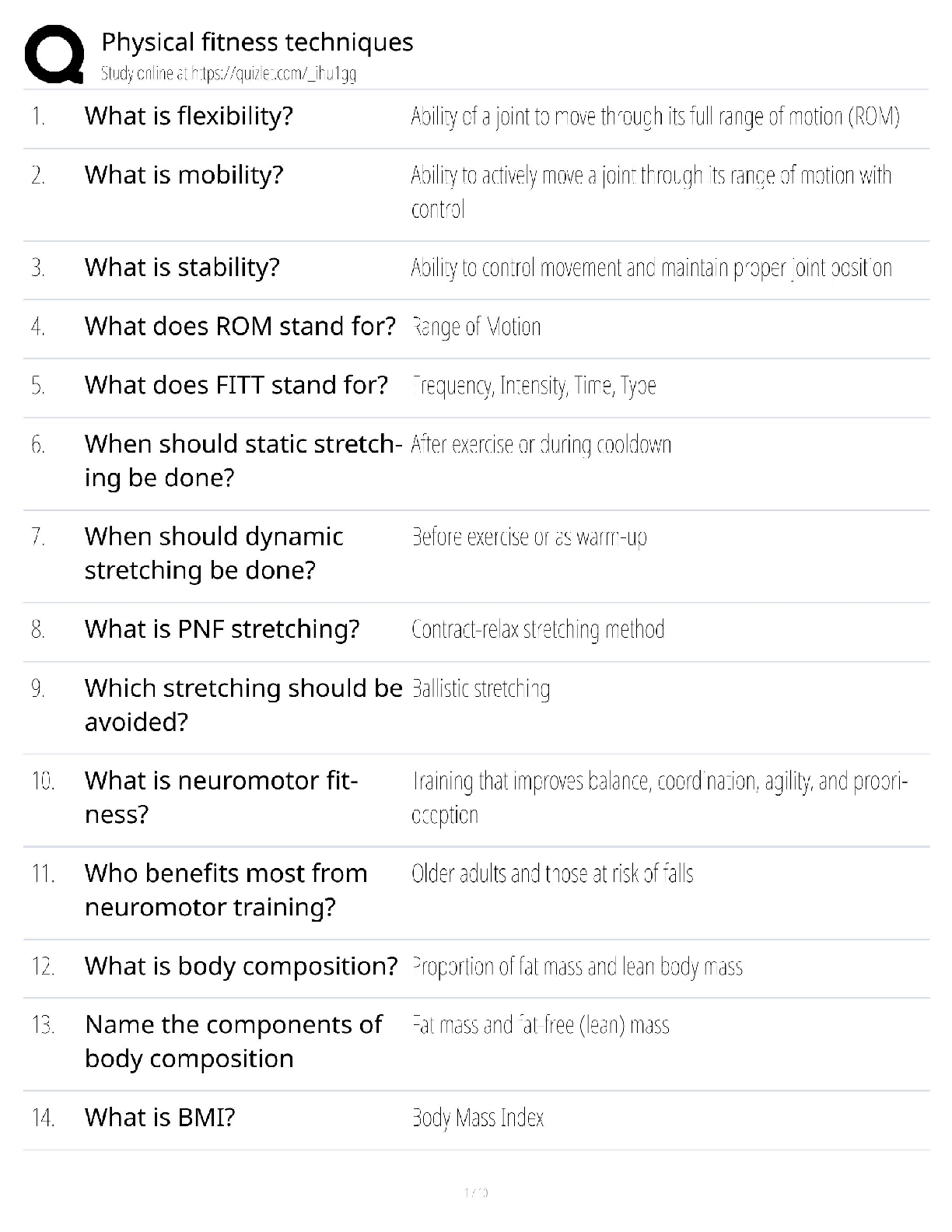
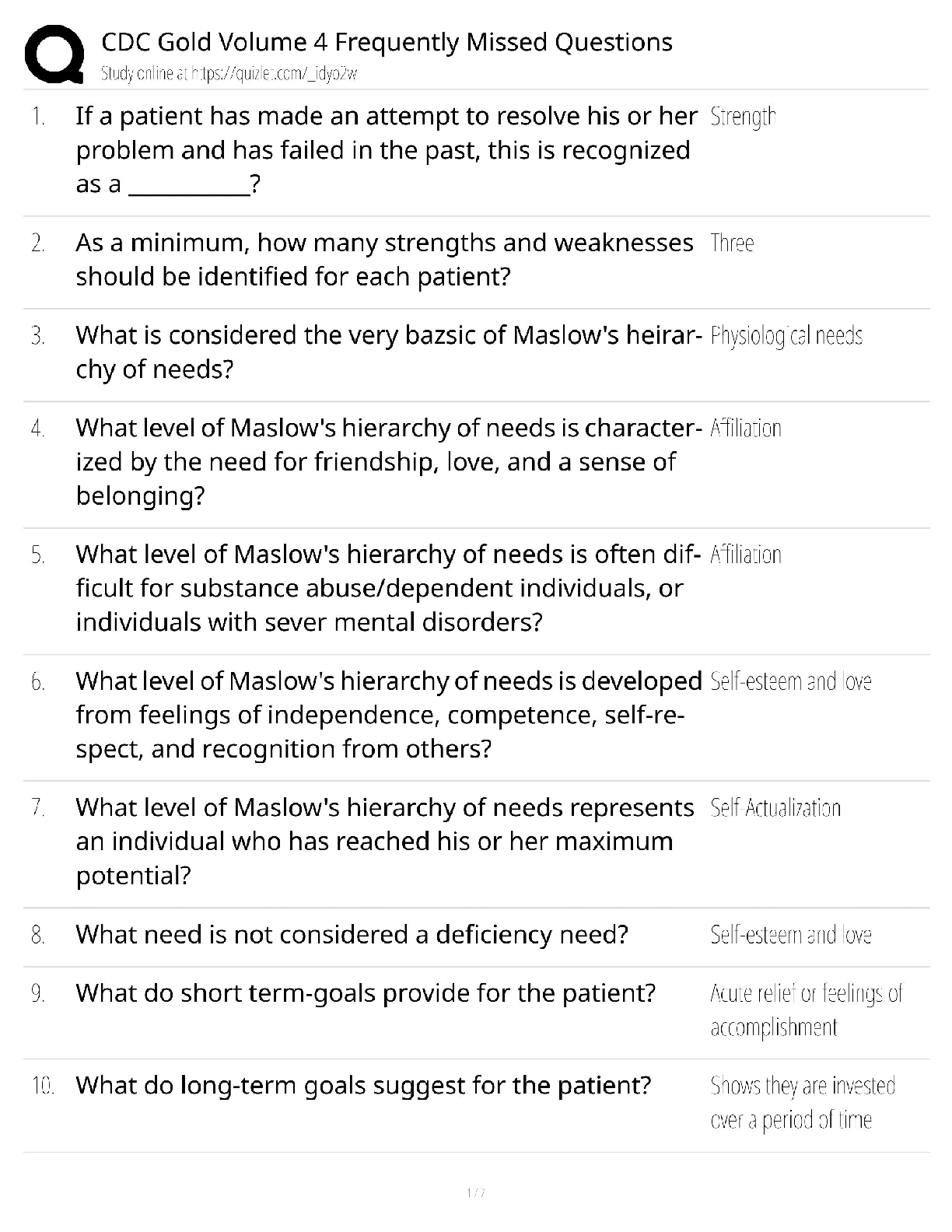
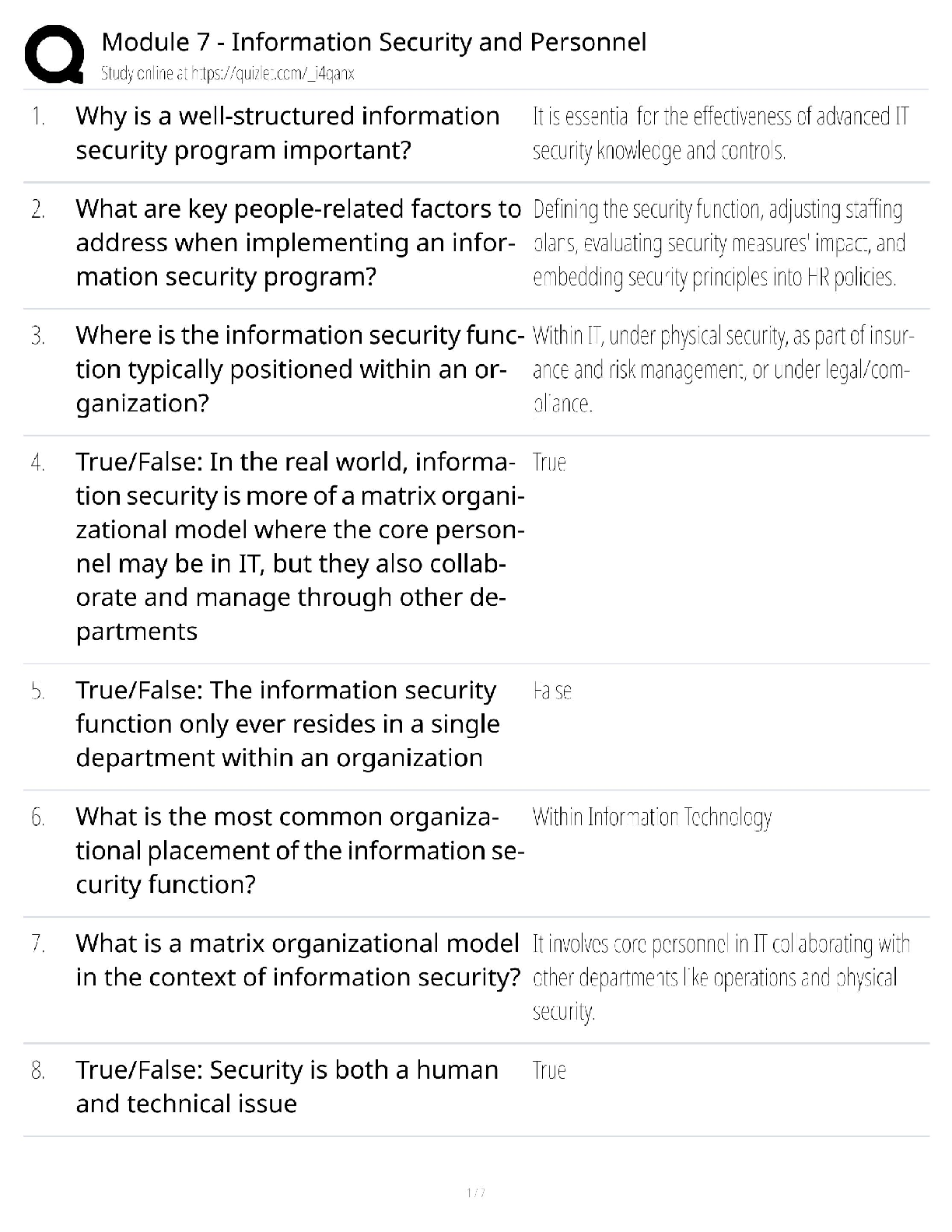
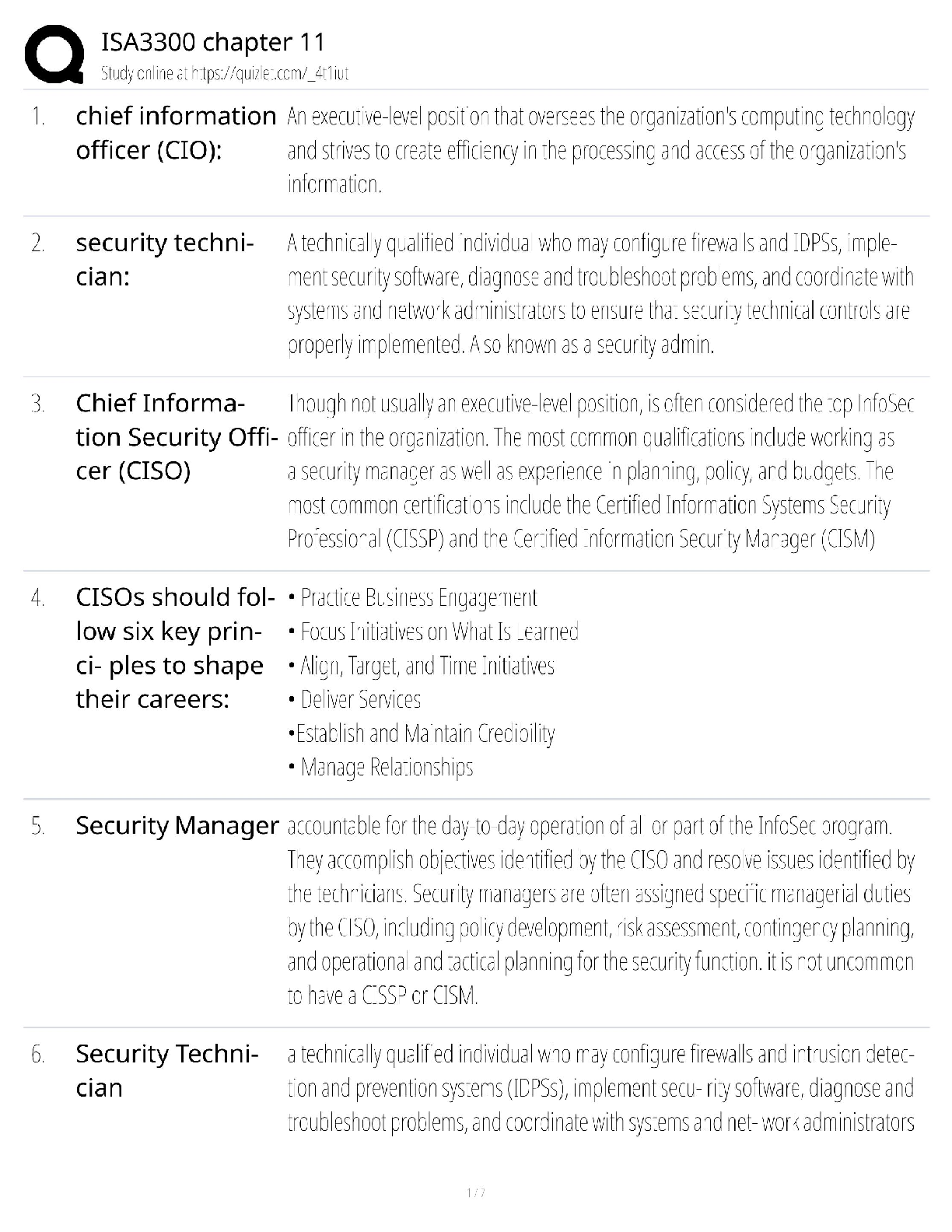
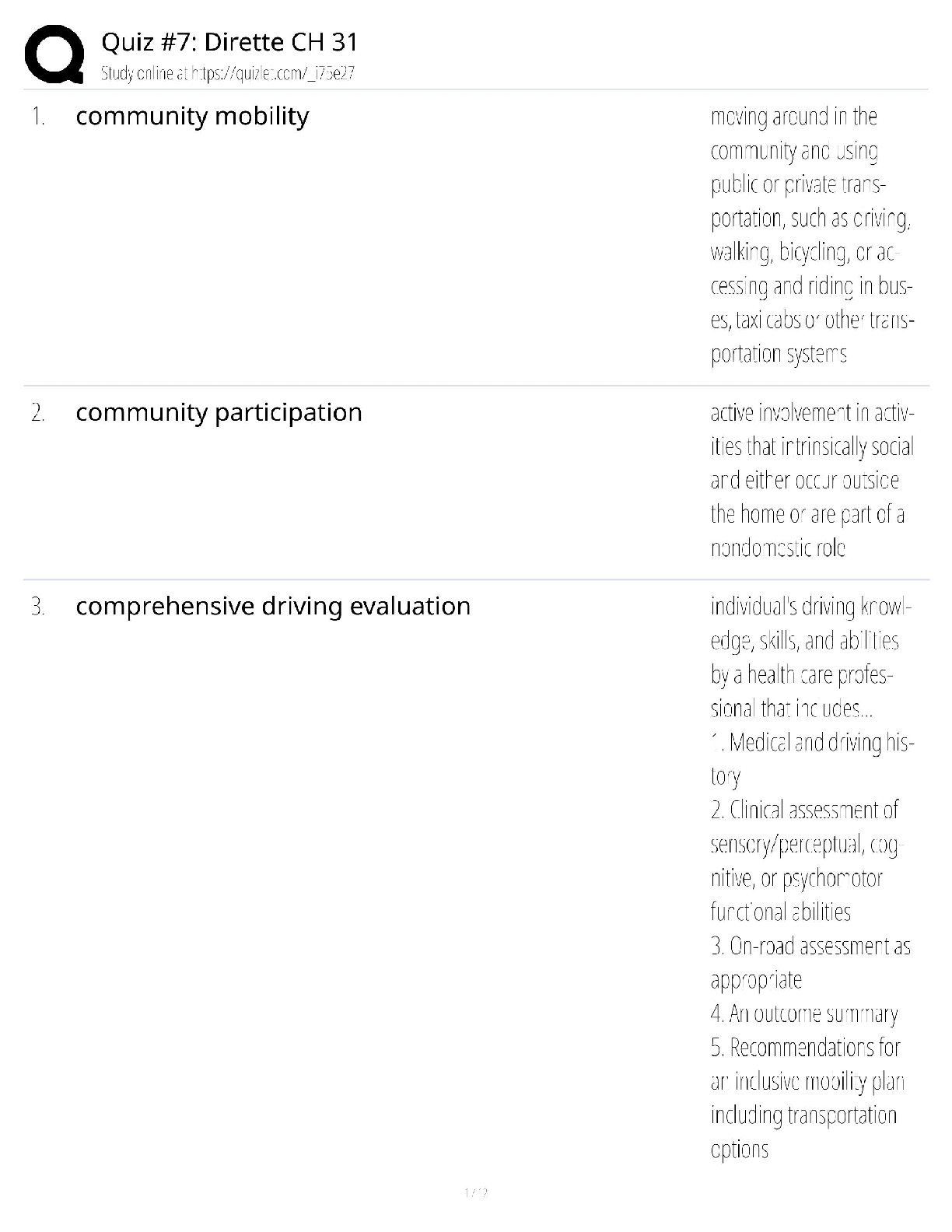
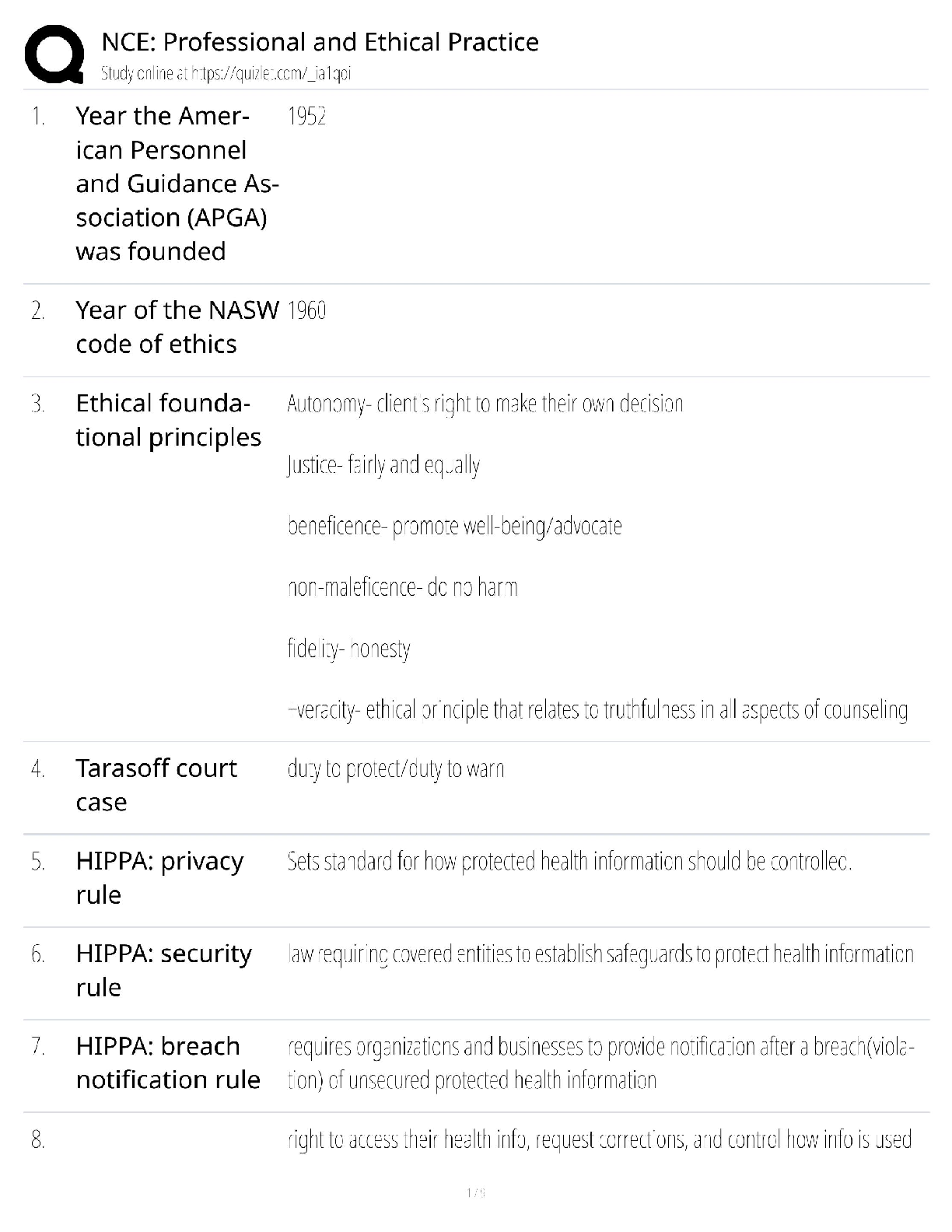
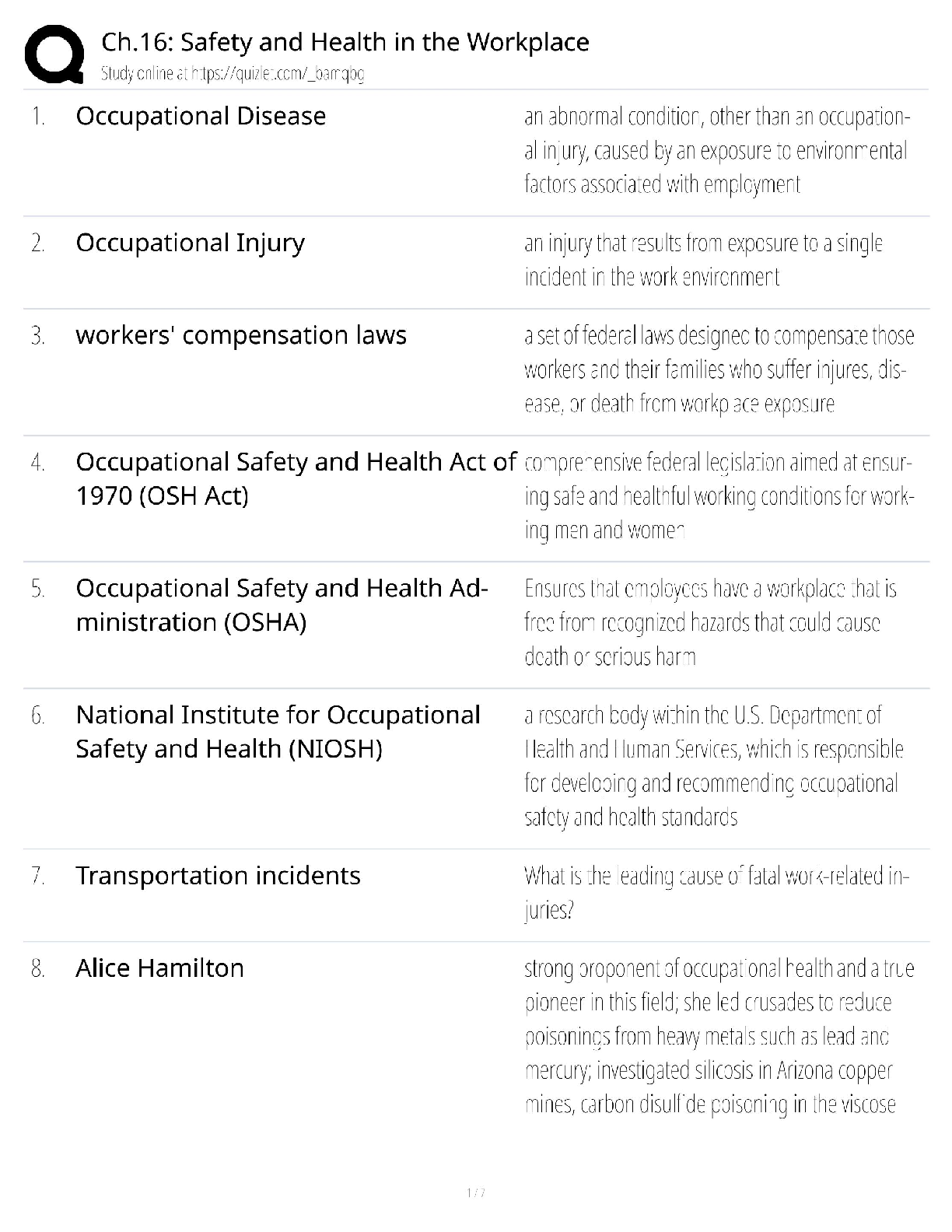
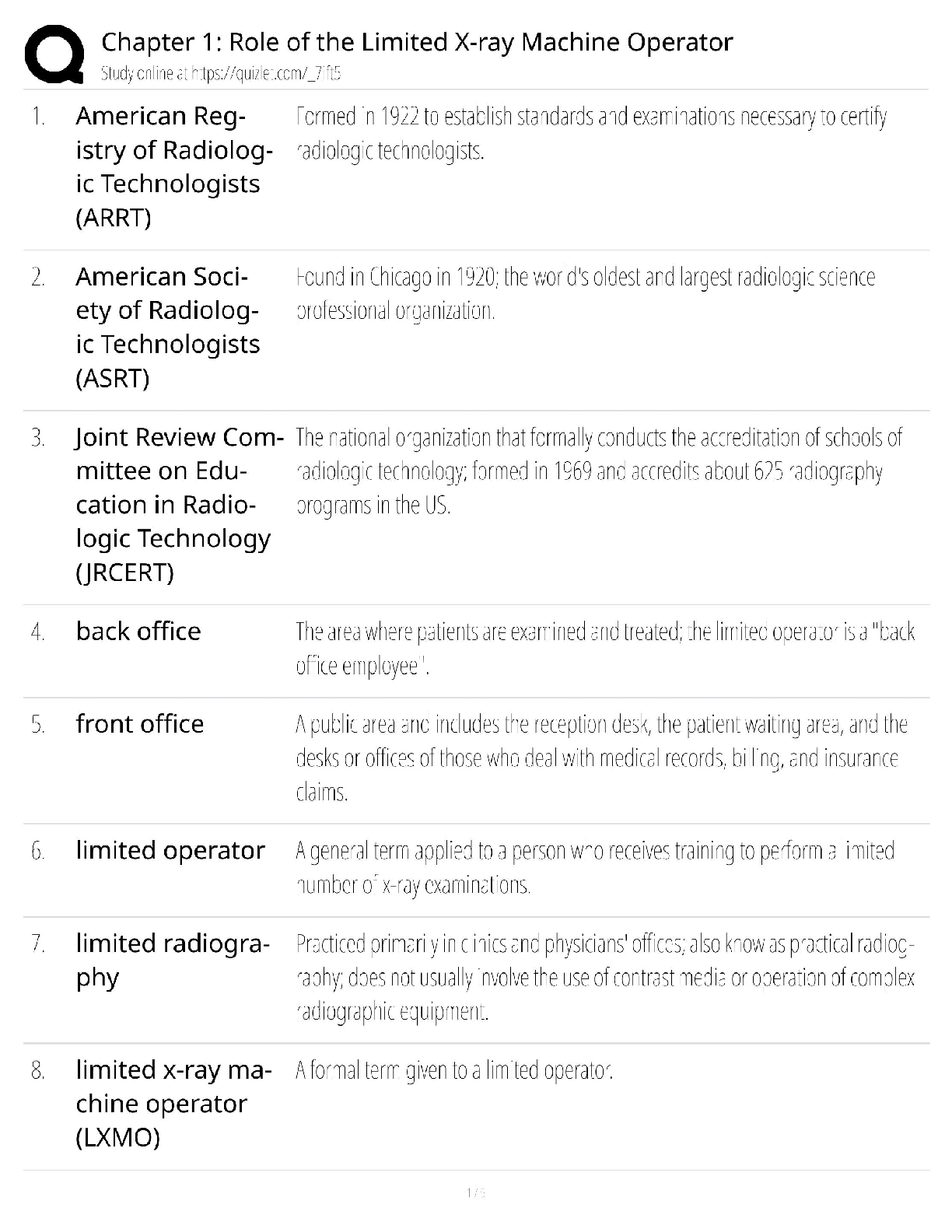
WGU C840 - Digital Forensics Questions and Answers Latest Updated 2022 The most common computer hard drives today are __________. ✔✔SATA A __________ is used to send a test packet, or echo pack ... et, to a machine to determine if the machine is reachable and how long the packet takes to reach the machine. ✔✔ping Suspects often overwhelm forensic analysts with false positives and false leads. This is referred to as__________. ✔✔data fabrication Which of the following is the definition of the Daubert Standard? ✔✔The Daubert Standard dictates that only methods and tools widely accepted in the scientific community can be used in court. The __________ protects journalists from being required to turn over to law enforcement any work product and documentary material, including sources, before it is disseminated to the public. ✔✔Privacy Protection Act of 1980 It has been claimed that __________ of all computers connected to the Internet have spyware. ✔✔80% __________ is/are the cyber-equivalent of vandalism. ✔✔DoS attacks Which of the following is the definition of logic bomb? ✔✔malware that executes damage when a specific condition is met Rules of evidence can be defined as __________. ✔✔rules that govern whether, when, how, and why proof of a legal case can be placed before a judge or jury Use of __________ tools enables an investigator to reconstruct file fragments if files have been deleted or overwritten. ✔✔bit-level Identification, preservation, collection, examination, analysis, and presentation are six classes in the matrix of __________. ✔✔the DFRWS framework What is meant by file slack? ✔✔the unused space between the logical end of file and the physical end of file Information that has been processed and assembled so that it is relevant to an investigation and supports a specific finding or determination is the definition of __________. ✔✔digital evidence __________ is a Linux Live CD that you use to boot a system and then use the tools. It is a free Linux distribution, making it extremely attractive to schools teaching forensics or laboratories on a strict budget. ✔✔BackTrack What name is given to data that an operating system creates and overwrites without the computer user taking a direct action to save this data? ✔✔temporary data __________ is offline analysis conducted on an evidence disk or forensic duplicate after booting from a CD or another system. ✔✔Physical analysis What was designed as an area where computer vendors could store data that is shielded from user activities and operating system utilities, such as delete and format? ✔✔host protected area A one-sided DVD (or digital video disc) can hold __________ gigabytes. ✔✔4.7 What version of RAID are the following descriptors? Striped disks with dedicated parity combine three or more disks in a way that protects data against loss of any one disk. Fault tolerance is achieved by adding an extra disk to the array and dedicating it to storing parity information. The storage capacity of the array is reduced by one disk. ✔✔RAID 3 or 4 The art and science of writing hidden messages is the definition of what? ✔✔steganography __________ is perhaps the most widely used public key cryptography algorithm in existence today. ✔✔RSA Windows 2000 and newer operating systems' file systems utilize __________. ✔✔NTFS A port is a number that identifies a channel in which communication can occur. There are certain ports a forensic analyst should know on sight. Which port uses IRC chat rooms? ✔✔Port 194 (which can use TCP or UDP. TCP guarantees delivery of data packets on port 194 in the same order in which they were sent. UDP on port 194 provides an unreliable service and datagrams may arrive duplicated, out of order, or missing without notice.) What is grep? ✔✔a popular Linux/UNIX search tool What is meant by zero-knowledge analysis? ✔✔a technique for file system repair that involves recovering data from a damaged partition with limited knowledge of the file system What name is given to a protocol used to send e-mail that works on port 25? ✔✔Simple Mail Transfer Protocol (SMTP) Which of the following common header fields includes tracking information generated by mail servers that have previously handled a message, in reverse order? ✔✔received RFC 3864 describes message header field names. Message-ID of the message to which there is a reply refers to which of the following options? ✔✔references The Electronic Communications Privacy Act requires different legal processes to obtain specific __________ information, including information from retrieved e-mail messages and unretrieved stored e-mails. ✔✔content information There are specific laws in the United States that are applicable to e-mail investigations. __________ is a U.S. law that prescribes procedures for the physical and electronic surveillance and collection of "foreign intelligence information" between foreign powers and agents of foreign powers, which may include American citizens and permanent residents suspected of espionage or terrorism. ✔✔Foreign Intelligence Surveillance Act (FISA) __________ is a live-system forensic technique in which you collect a memory dump and perform analysis in an isolated environment. ✔✔Volatile memory analysis Which of the following is the definition of dump? ✔✔a complete copy of every bit of memory or cache recorded in permanent storage or printed on paper A number of tools and even some Windows utilities are available that can help you to analyze live data on a Windows system. Use __________ to view process and thread statistics on a system. ✔✔PsList What name is given to the result of acquiring a file as it is being updated? ✔✔slurred image Essentially, a __________ is a special place on the hard drive where items from memory can be temporarily stored for fast retrieval. ✔✔swap file The Windows Registry is organized into five sections. The __________ section contains those settings common to the entire machine, regardless of the individual user. ✔✔HKEY_LOCAL_MACHINE (HKLM) [Show More]
Last updated: 3 years ago
Preview 1 out of 11 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
WGU Course C840 - Digital Forensics in Cyber security Bundled Questions and Answers All Graded A+
WGU Course C840 - Digital Forensics in Cyber security Bundled Questions and Answers All Graded A+
By Nutmegs 3 years ago
$20
8
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
11
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
260








.png)