Computer Science > QUESTIONS & ANSWERS > WGU C840 Digital Forensics Questions and Answers Latest Update Already Passed (All)
WGU C840 Digital Forensics Questions and Answers Latest Update Already Passed
Document Content and Description Below
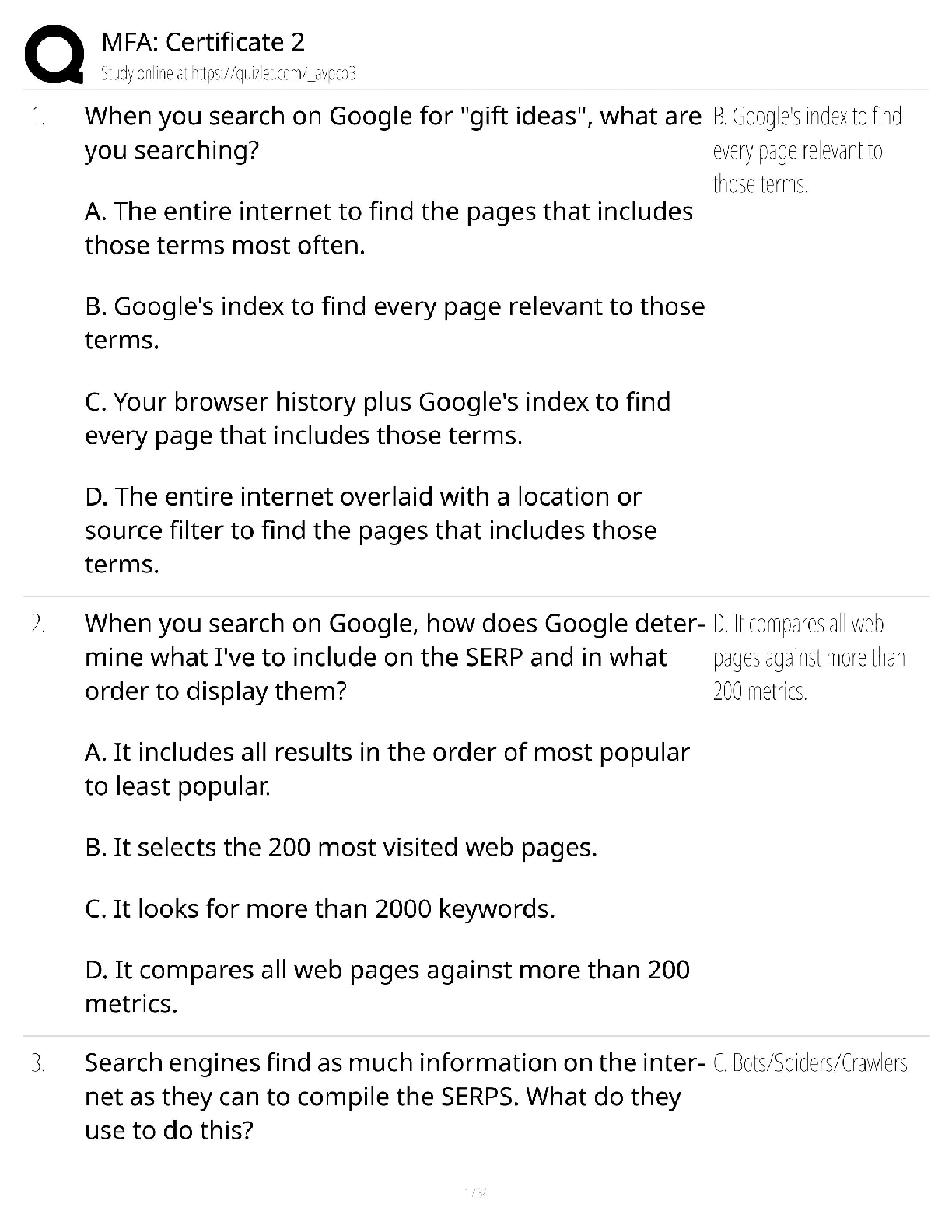
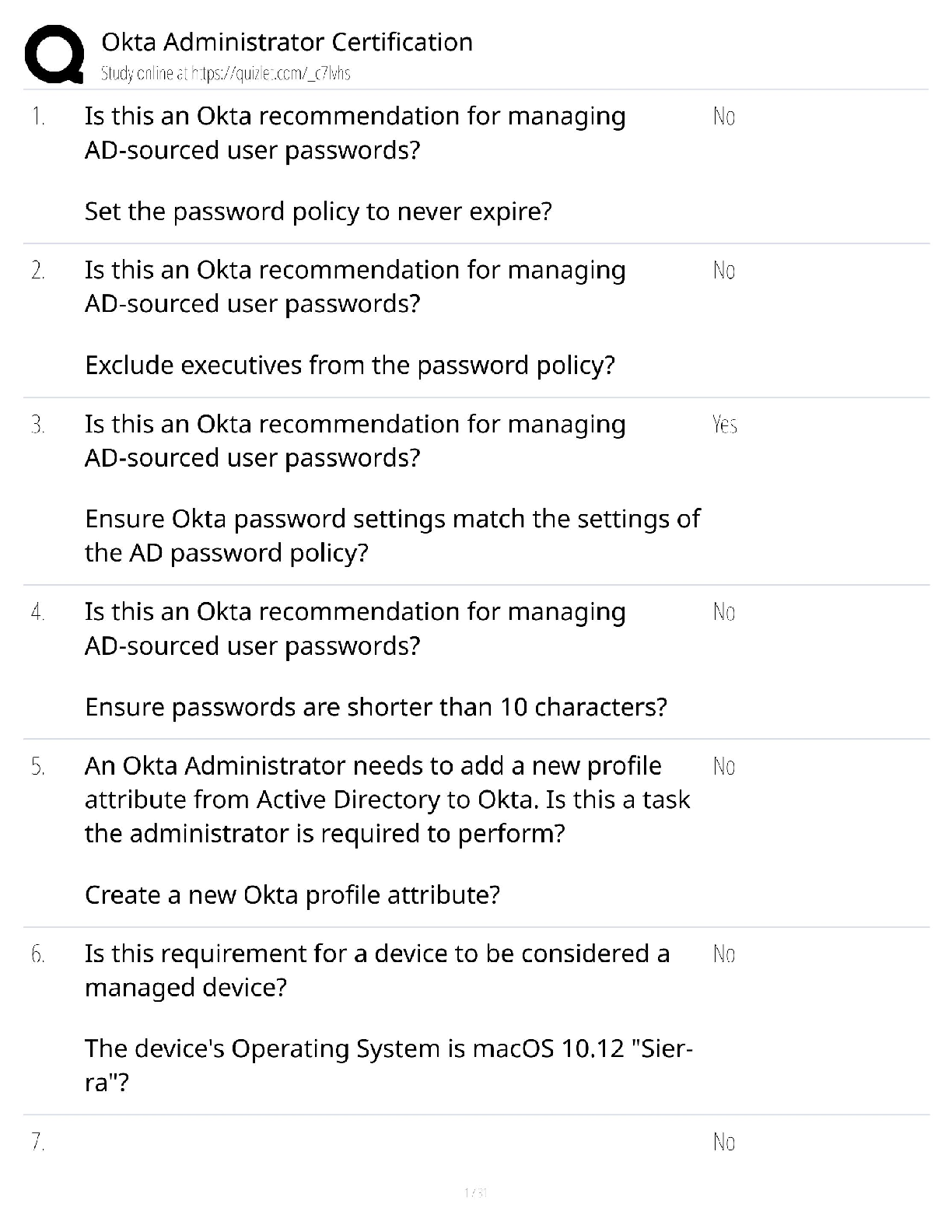
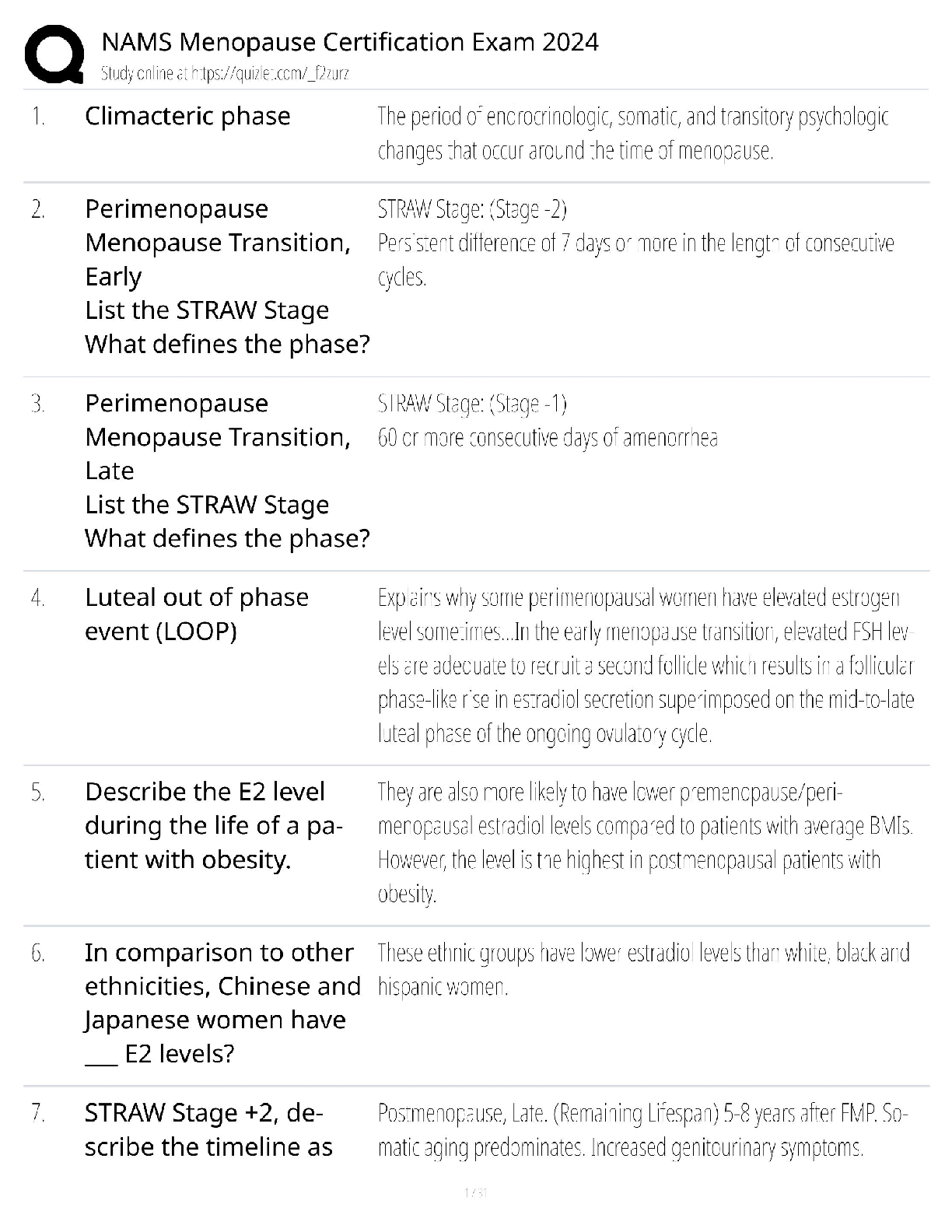
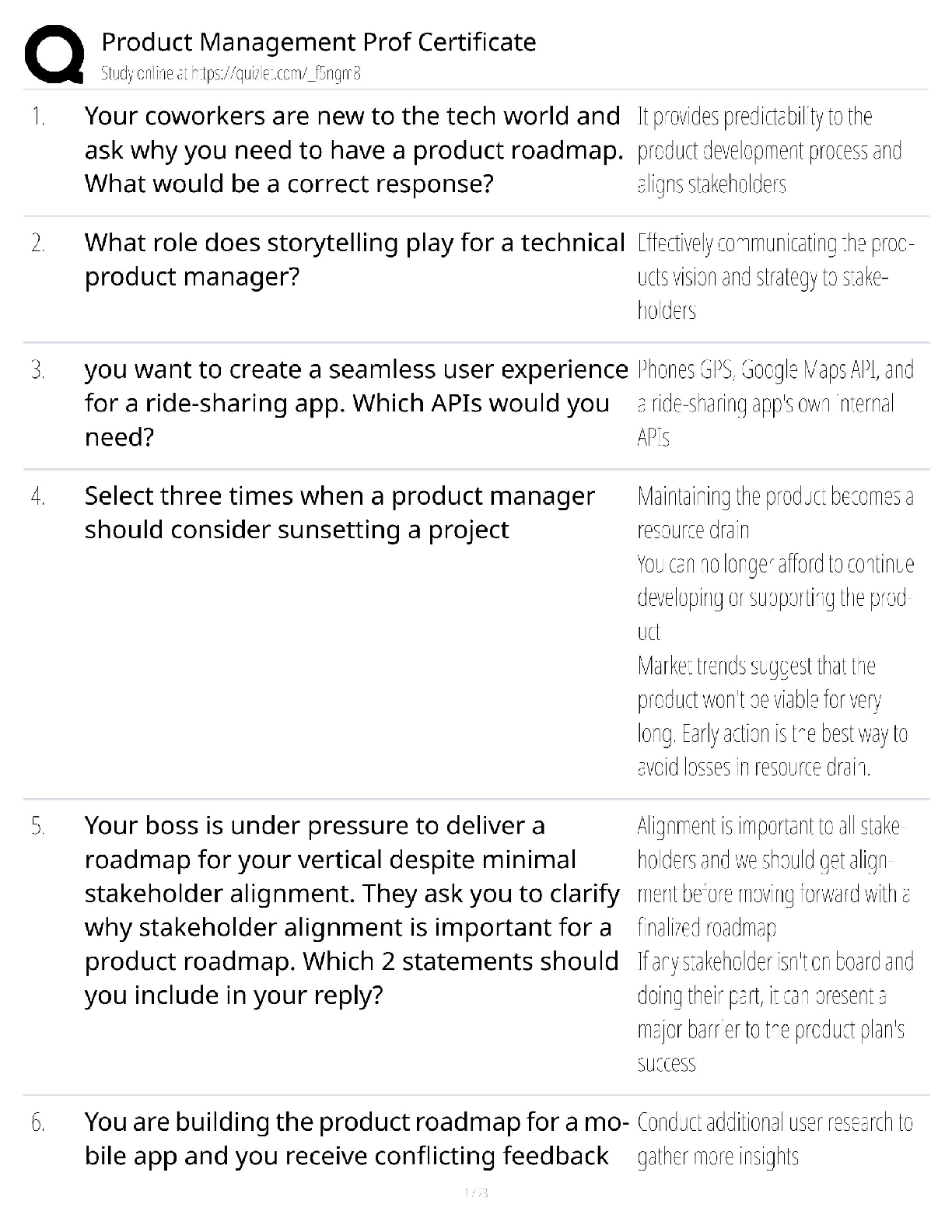
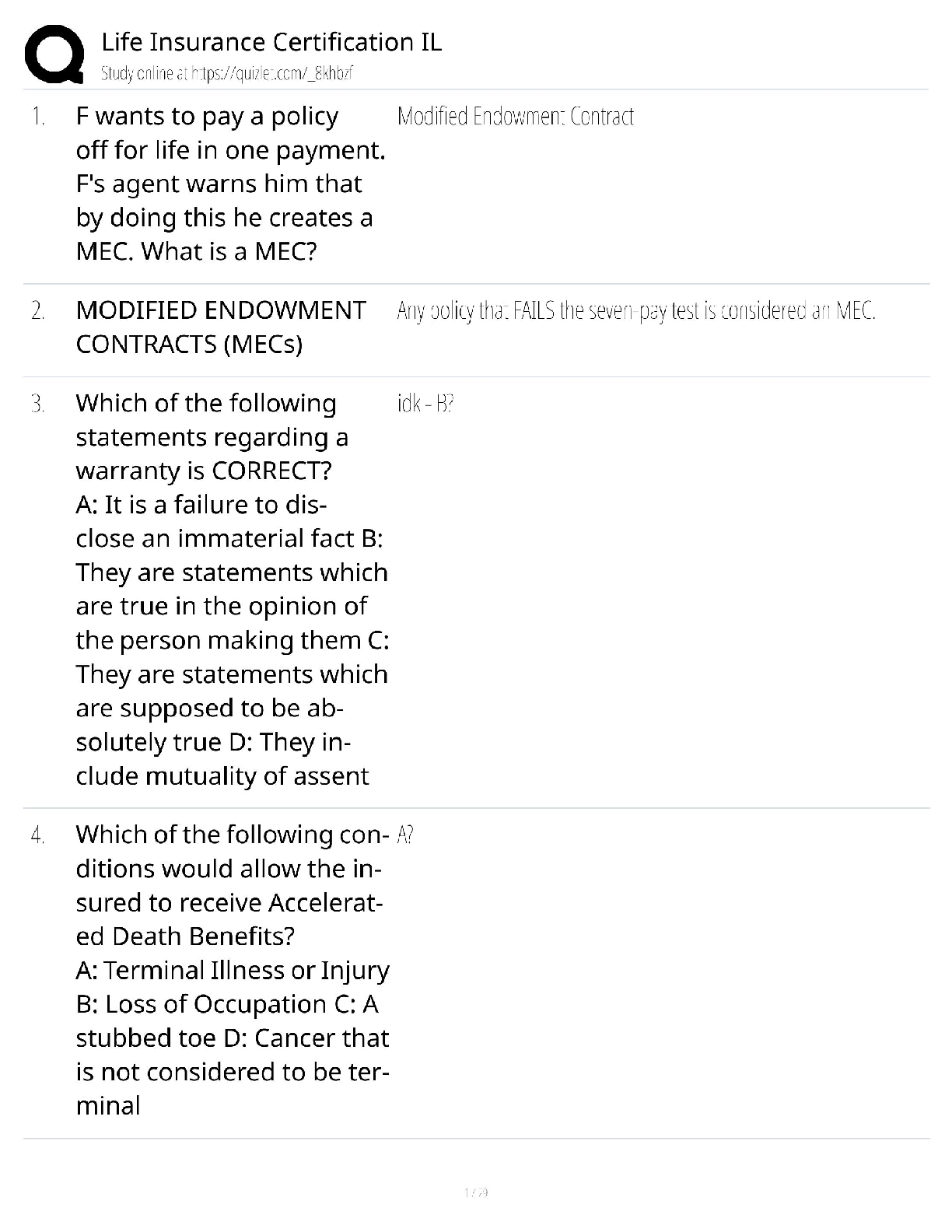
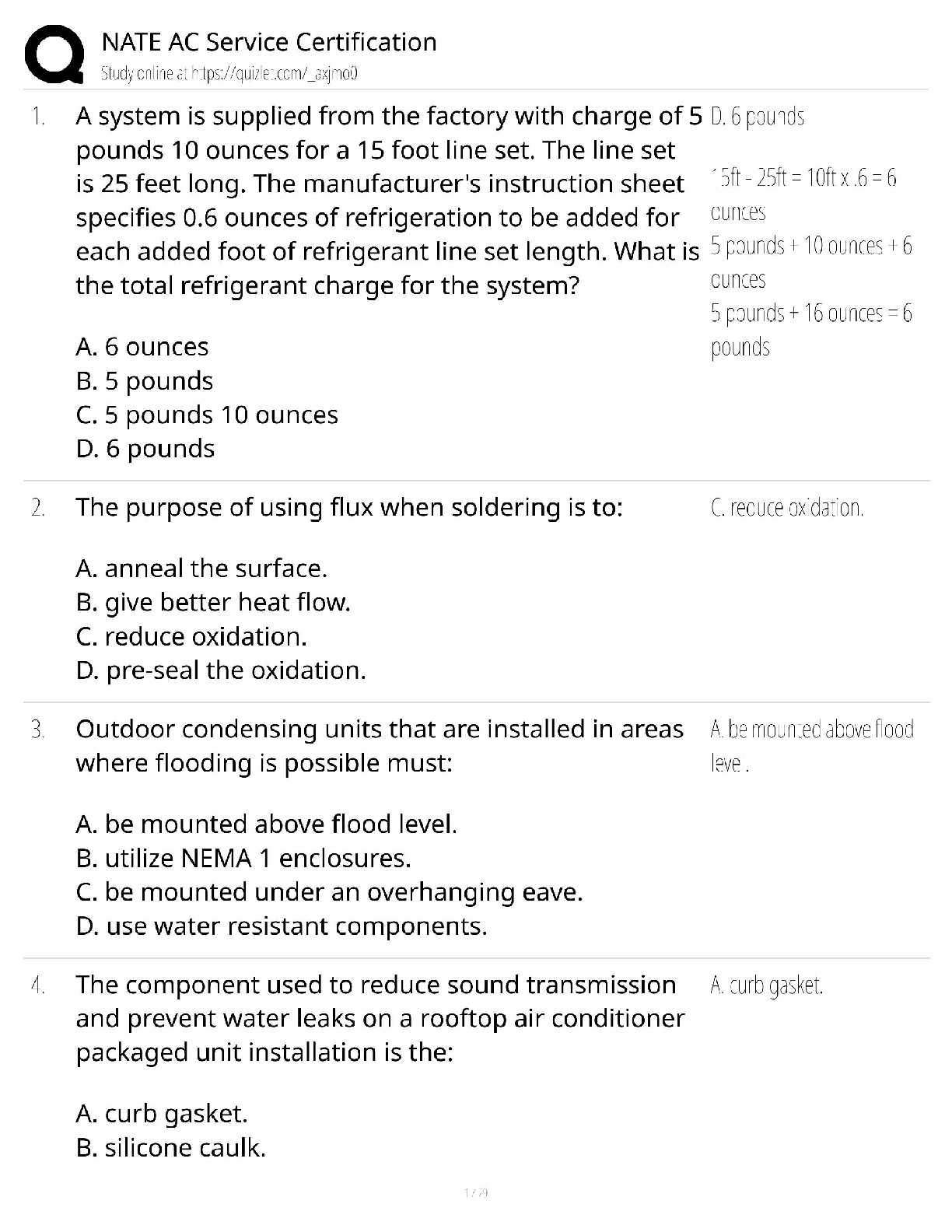
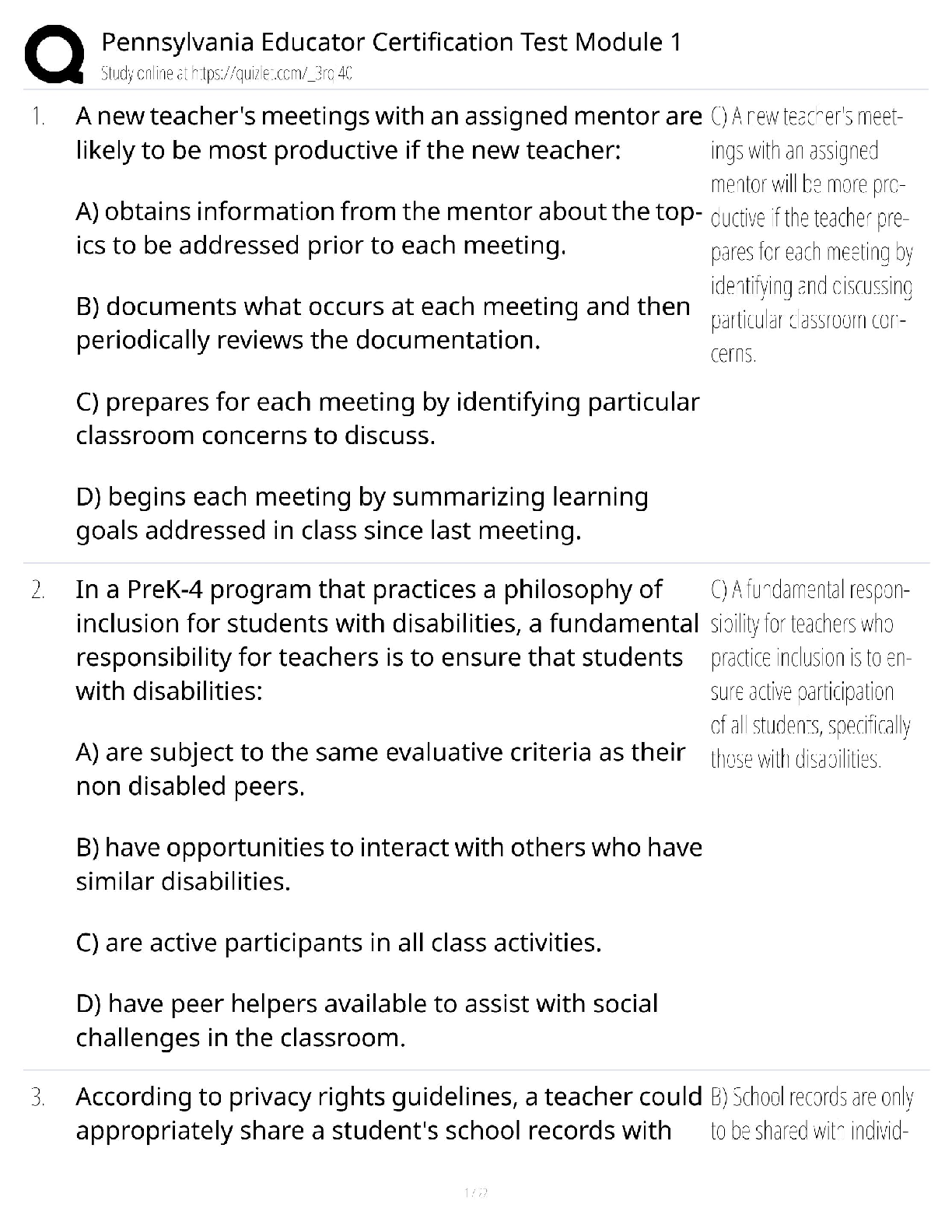
WGU C840 Digital Forensics Questions and Answers Latest Update Already Passed expert report ✔✔A formal document prepared by a forensics specialist to document an investigation, including a lis ... t of all tests conducted as well as the specialist's own curriculum vitae (CV). Anything the specialist plans to testify about at a trial must be included in the expert report. Testimonial evidence ✔✔Information that forensic specialists use to support or interpret real or documentary evidence; for example, to demonstrate that the fingerprints found on a keyboard are those of a specific individual. Daubert standard ✔✔The standard holding that only methods and tools widely accepted in the scientific community can be used in court. If the computer is turned on when you arrive, what does the Secret Service recommend you do? ✔✔Shut down according to the recommended Secret Service procedure. Communications Assistance to Law Enforcement Act of 1994 ✔✔The Communications Assistance to Law Enforcement Act of 1994 is a federal wiretap law for traditional wired telephony. It was expanded to include wireless, voice over packet, and other forms of electronic communications, including signaling traffic and metadata. Digital evidence ✔✔Digital evidence is information processed and assembled so that it is relevant to an investigation and supports a specific finding or determination. Federal Privacy Act of 1974 ✔✔The Federal Privacy Act of 1974, a United States federal law that establishes a code of Fair Information Practice that governs the collection, maintenance, use, and dissemination of information about individuals that is maintained in systems of records by U.S. federal agencies. Power Spy, Verity, ICU, and WorkTime ✔✔Spyware good fictitious e-mail response rate ✔✔1-3% Which crime is most likely to leave e-mail evidence? ✔✔Cyberstalking Where would you seek evidence that ophcrack had been used on a Windows Server 2008 machine? ✔✔In the logs of the server; look for the reboot of the system A SYN flood is an example of what? ✔✔DoS attack definition of a virus, in relation to a computer? ✔✔a type of malware that requires a host program or human help to propagate What is the starting point for investigating the denial of service attacks? ✔✔Tracing the packets China Eagle Union ✔✔The cyberterrorism group, the China Eagle Union, consists of several thousand Chinese hackers whose stated goal is to infiltrate Western computer systems. Members and leaders of the group insist that not only does the Chinese government have no involvement in their activities, but that they are breaking C [Show More]
Last updated: 2 years ago
Preview 1 out of 22 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
WGU Course C840 - Digital Forensics in Cyber security Bundled Questions and Answers All Graded A+
WGU Course C840 - Digital Forensics in Cyber security Bundled Questions and Answers All Graded A+
By Nutmegs 3 years ago
$20
8
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
22
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
1
Views
423








.png)