C725 Exam Practice
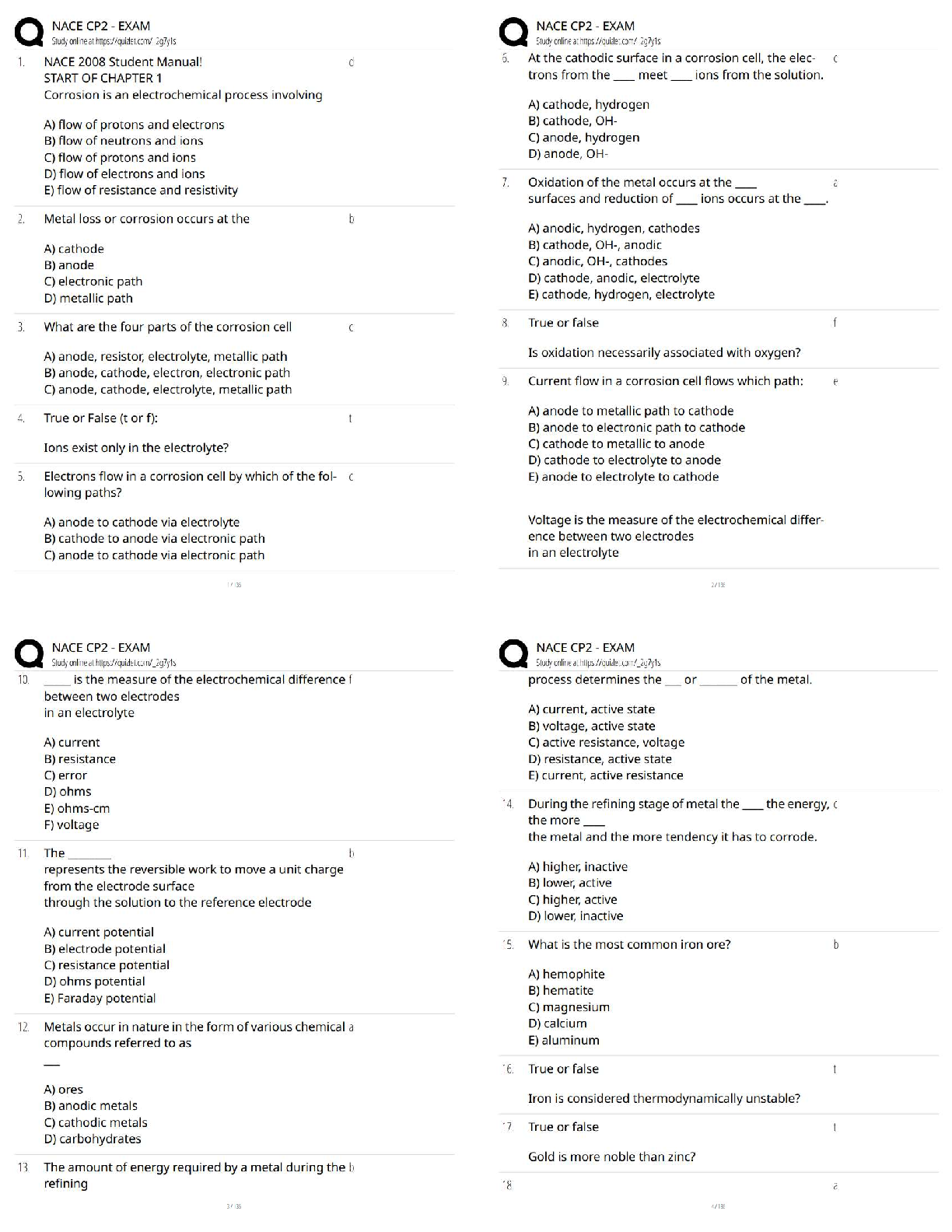
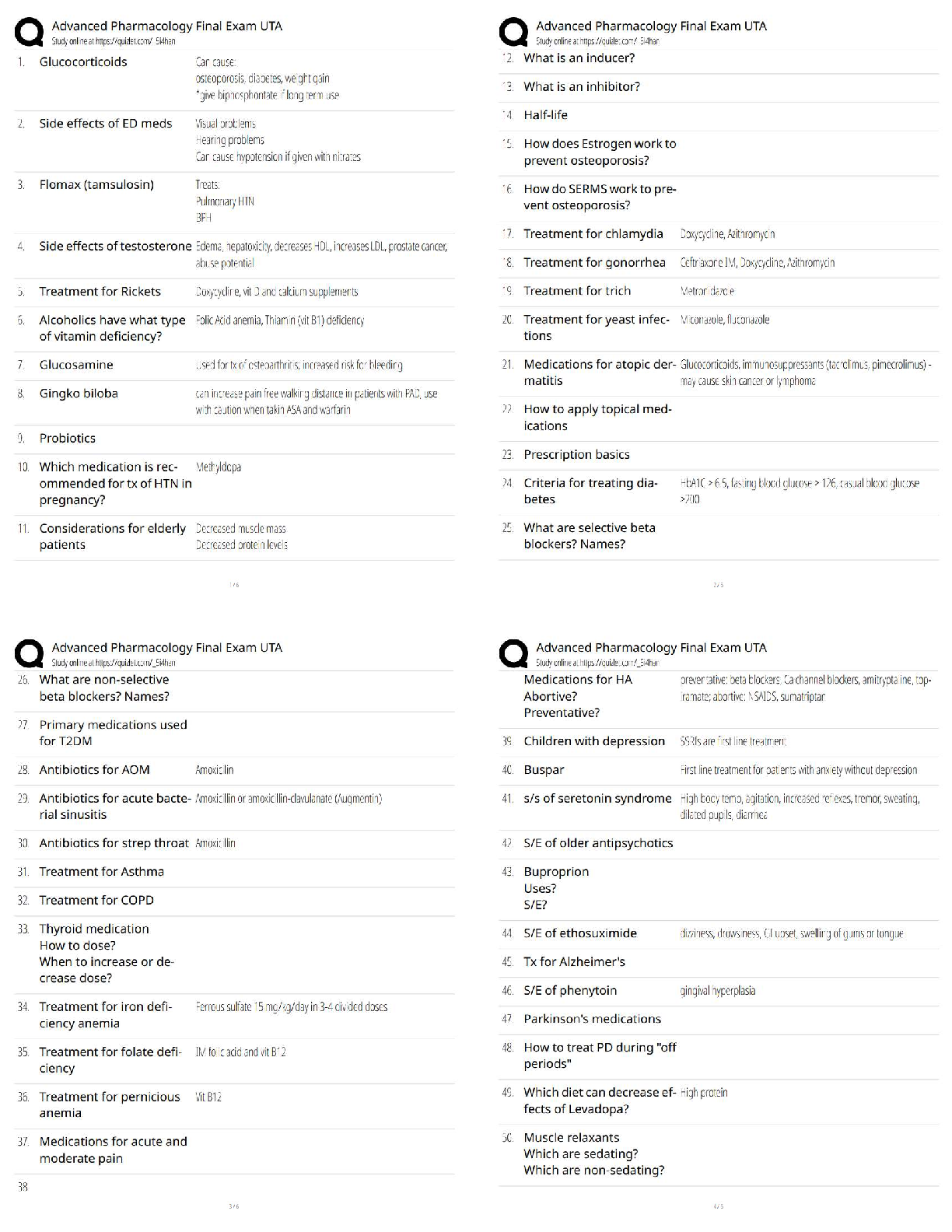
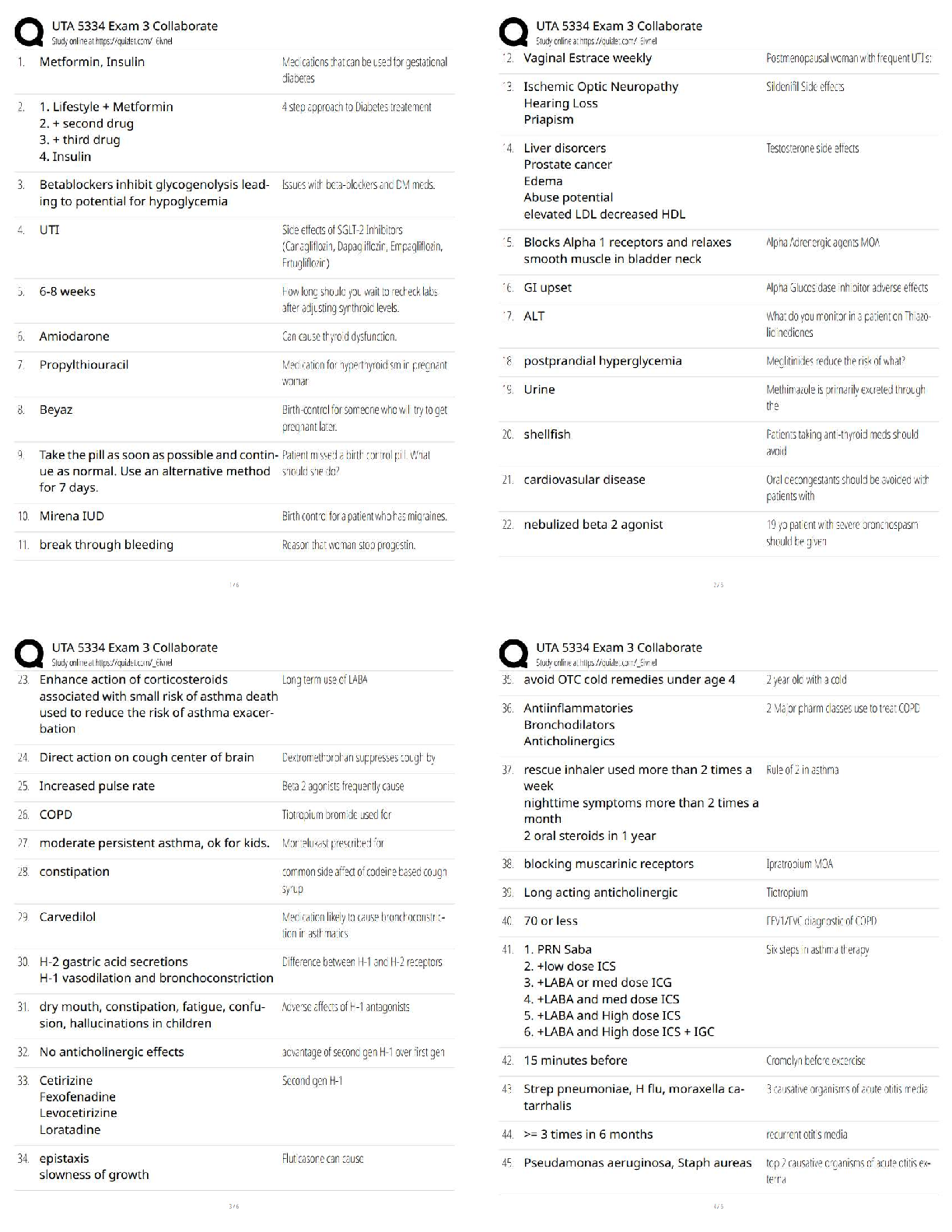
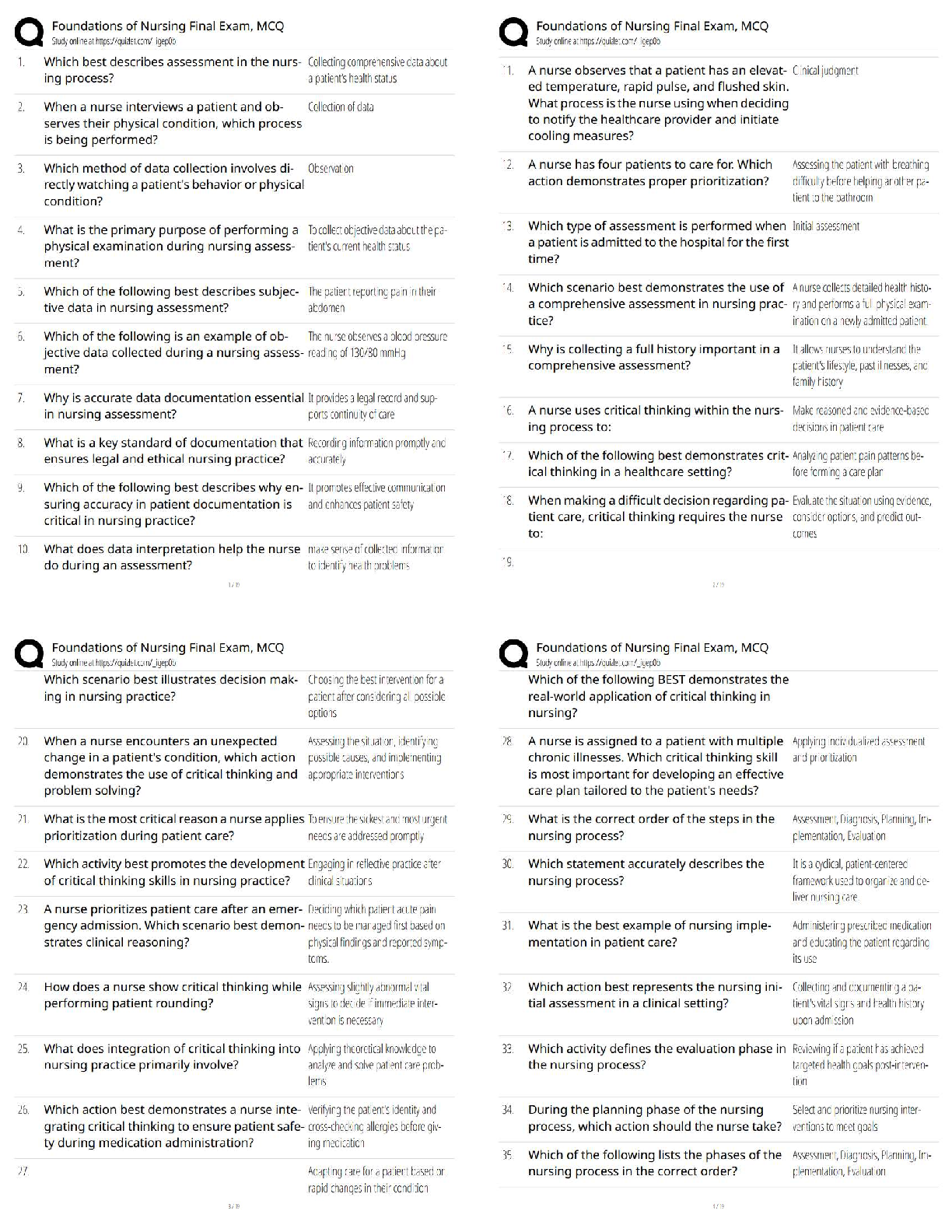
Information security is primarily a discipline to manage the behavior of - ✔✔People
Careers in information security are booming because of which of the following factors? -
✔✔threat of cyber terrori
...
C725 Exam Practice
Information security is primarily a discipline to manage the behavior of - ✔✔People
Careers in information security are booming because of which of the following factors? -
✔✔threat of cyber terrorism, gov regs, growth of the internet
Which of the following best represents the three objectives of information security? -
✔✔CIA
A program for information security should include which of the following elements? -
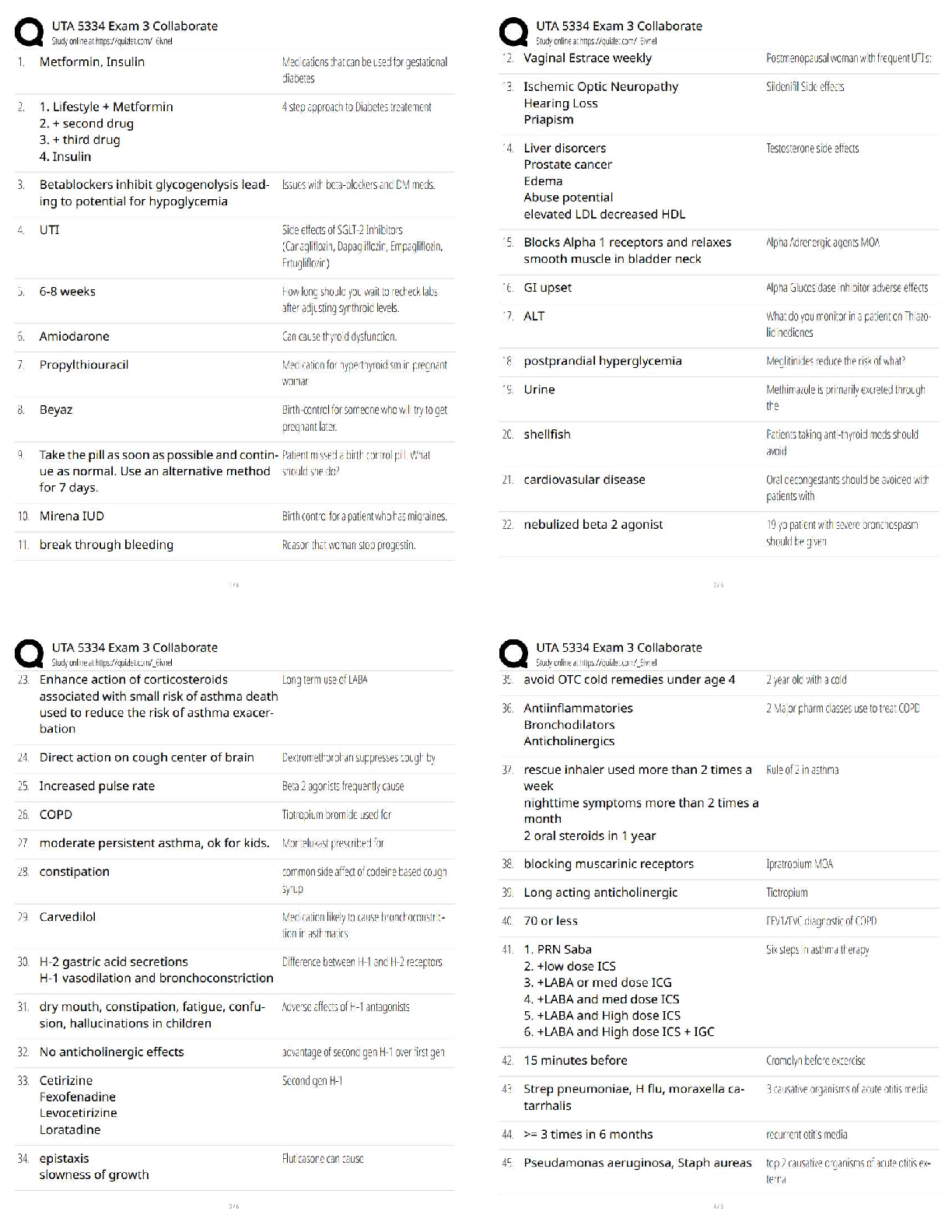
✔✔Security policies and procedures
Which of the following topics are part of an information security practice? - ✔✔Laws and
ethical practices, access controls, security architecture
Which college curriculum is more appropriate for a career in information security -
✔✔business admin and comp info sciences
The formal study of information security has accelerated primarily for what reason? -
✔✔(increasingly interconnected global networks)
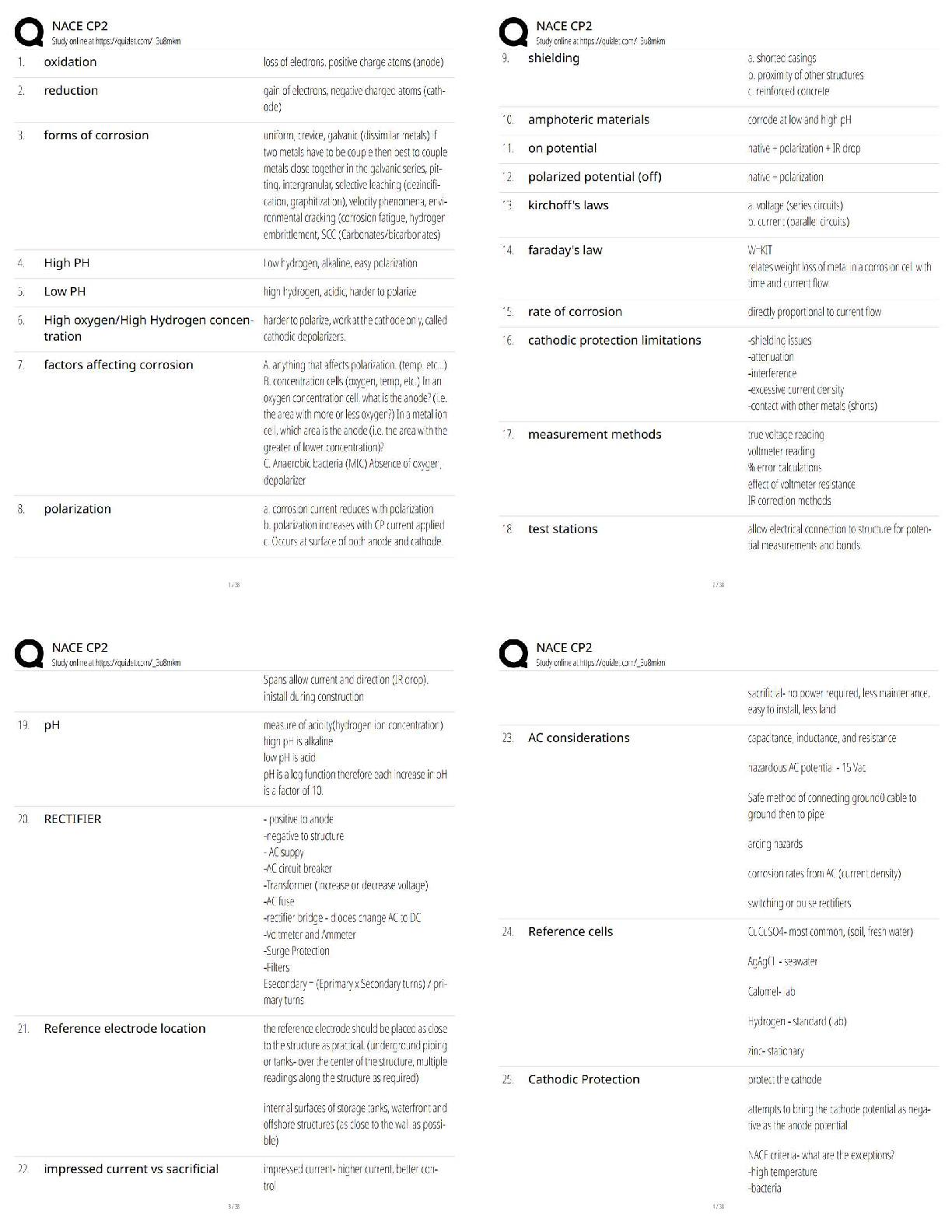
Cybersecurity is like an umbrella. Under the umbrella are the following: -
✔✔Compliance, policies, standards, admin, auditing, software dev security, permission
controls, incident response, physical security, intrusion detection and prevention, ops
controls, antivirus, security testing, training and awareness, key management, public
key infrastructure, disaster recovery, access controls
The growing demand for InfoSec specialists is occurring predominantly in which of the
following types of organizations - ✔✔Gov, corporations, not for profit foundations
What is meant by the phrase "the umbrella of information security"? - ✔✔IS
incorporates many different pursuits and disciplines
Which of the following roles helps development teams meet security requirements? -
✔✔Security consultants
Secuyrity consultants do this: - ✔✔perform risk analysis of new systems by balancing
the needs of business with the threats that stem from opening up access to data or
managing new information that could compromise the business if it fell into the wrong
hands.
Who is responsible for ensuring that systems are auditable and protected from
excessive privileges? - ✔✔Security admins
Security admins do this - ✔✔help to establish new user accounts, ensure that auditing
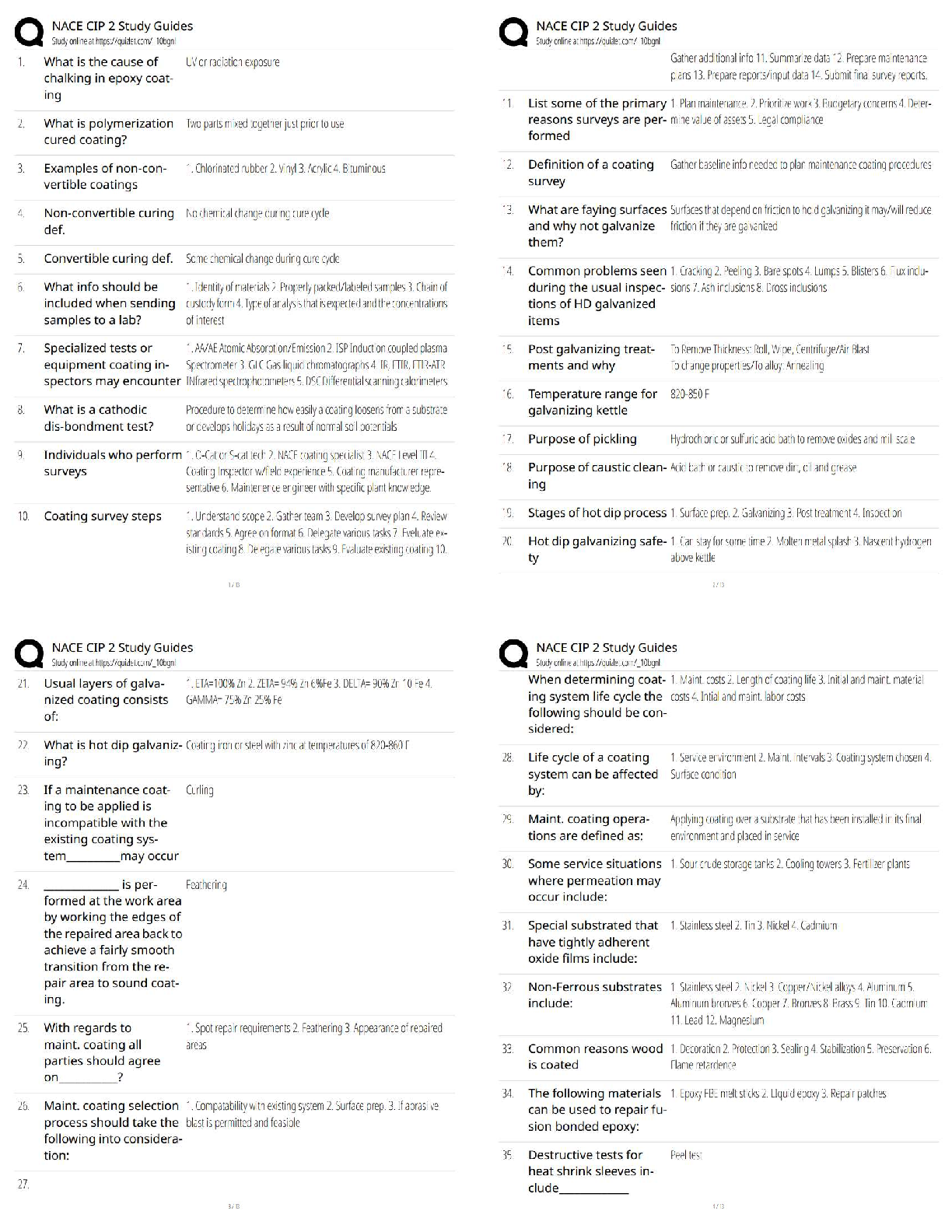
mechanisms are present and operating as needed, ensure that communications
between systems are securely implemented, and assist in troubleshooting problems
and responding to incidents that could compromise confidentiality, integrity, or
availability of the systems.
Which of the following roles is responsible for ensuring that third-party suppliers and
outsourced functions remain in security compliance? - ✔✔Vendor managers
Vendor managers are needed to - ✔✔ensrue that outsourced functions are operating
within security policies and standards
Confidentiality is sometimes referred to as - ✔✔the principle of least privilege, meaning
that users should be given only enough privilege to perform their duties, and no more.
Some other synonyms for confidentiality you might encounter include privacy, secrecy,
and discretion.
Confidentiality models are primarily intended to - ✔✔ensure that no unauthorized
access to information is permitted and that accidental disclosure of sensitive information
is not possible. Common confidentiality controls are user IDs and passwords
Related to information security, confidentiality is the opposite of which of the following? -
✔✔Disclosure
One way to think of the CIA triad... - ✔✔Protect the confidentiality of data
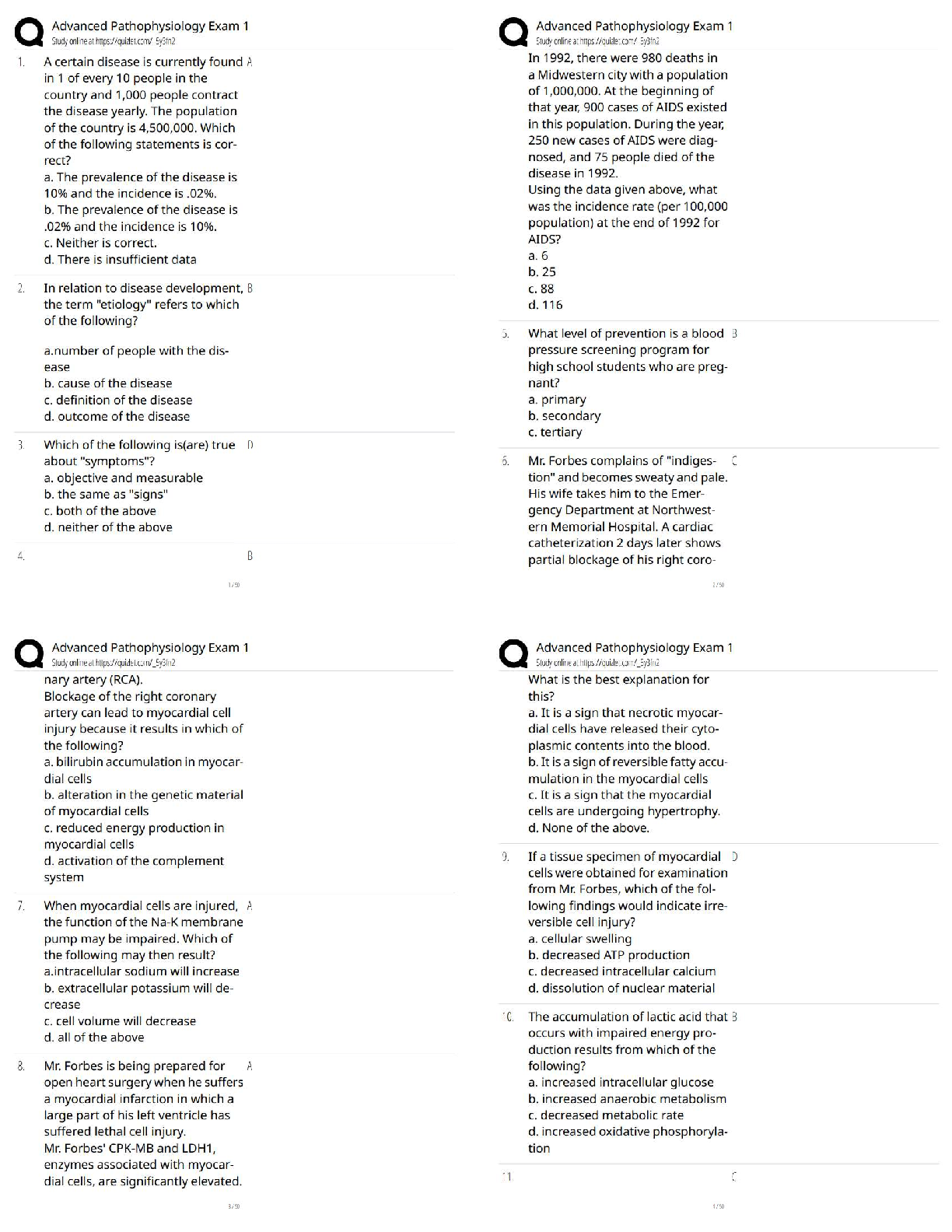
Preserve the integrity of data
Promote the availability of data for authorized use
Integrity models ... - ✔✔keep data pure and trustworthy by protecting system data from
intentional or accidental changes.
Integrity models have three goals: - ✔✔Prevent unauthorized users from making
modifications to data or programs
Prevent authorized users from making improper or unauthorized modifications
Maintain internal and external consistency of data and programs
An example of integrity checks is - ✔✔balancing a batch of transactions to make sure
that all the information is present and accurately accounted for.
Availability models ... - ✔✔keep data and resources available for authorized use,
especially during emergencies or disasters.
Information security professionals usually address three common challenges to
availability: - ✔✔Denial of service (DoS) due to intentional attacks or because of
undiscovered flaws in implementation (for example, a program written by a programmer
who is unaware of a flaw that could crash the program if a certain unexpected input is
encountered)
Loss of information system capabilities because of natural disasters (fires, floods,
storms, or earthquakes) or human actions (bombs or strikes)
Equipment failures during normal use
Some activities that preserve confidentiality, integrity, and/or availability are -
✔✔granting access only to authorized personnel, applying encryption to information that
will be sent over the Internet or stored on digital media, periodically testing computer
system security to uncover new vulnerabilities, building software defensively, and
developing a disaster recovery plan to ensure that the business can continue to exist in
the event of a disaster or loss of access by personnel.
Which of the following represents the three goals of information security? Spell it out -
✔✔Confidentiality, Integrity, and availability
Layered security, as in the previous example, is known as defense in depth... So -
✔✔This security is implemented in overlapping layers that provide the three elements
needed to secure assets: prevention, detection, and response. Defense in depth also
seeks to offset the weaknesses of one security layer by the strengths of two or more
layers.
Defense in depth is needed to ensure that which three mandatory activities are present
in a security system? - ✔✔(prevention, detection, and response
. Verification is the process of - ✔✔confirming that one or more predetermined
requirements or specifications are met.
Validation then determines the - ✔✔correctness or quality of the mechanisms used to
meet the needs. In other words, you can develop software that addresses a need, but it
might contain flaws that could compromise data when placed in the hands of a
malicious user
Verification testing for seat belt functions might include - ✔✔conducting stress tests on
the fabric, testing the locking mechanisms, and making certain the belt will fit the
intended application, thus completing the functional tests.
Validation, or assurance testing, might then include - ✔✔crashing the car with crash-test
dummies inside to "prove" that the seat belt is indeed safe when used under normal
conditions and that it can survive under harsh conditions.
Which of the following best represents the two types of IT security requirements? -
✔✔Functional and assurance
Functional requirements describe - ✔✔what a system should do.
Assurance requirements describe - ✔✔how functional requirements should be
implemented and tested.
When risks are well understood, three outcomes are possible: - ✔✔The risks are
mitigated (countered).
Insurance is acquired against the losses that would occur if a system were
compromised.
The risks are accepted and the consequences are managed.
The simplest form of determining the degree of a risk involves looking at two factors: -
✔✔What is the consequence of a loss?
What is the likelihood that this loss will occur?
Vulnerability refers to a - ✔✔known problem within a system or program.
In applying these concepts to risk analysis, the IS practitioner must anticipate... -
✔✔who might want to attack the system, how capable the attacker might be, how
available the exploits to a vulnerability are, and which systems have the vulnerability
present.
An attacker, then, is the link between a ___and an ____The attacker has two
characteristics: __ and ___ - ✔✔vulnerability, exploit.
skill, will
An exploit is - ✔✔a program or "cookbook" on how to take advantage of a specific
vulnerability. I
Which of the following terms best describes the probability that a threat to an
information system will materialize? - ✔✔Risk
Risk involves ... - ✔✔looking at what is the consequence of a loss and the likelihood
that this loss will occur.
Question :Which of the following terms best describes the absence or weakness in a
system that may possibly be exploited? - ✔✔Vulnerability
Question :Which of the following terms best describes a cookbook on how to take
advantage of a vulnerability? - ✔✔Exploit
The Three Types of Security Controls Are - ✔✔Preventative, Detective, and Responsive
Controls (such as documented processes) and countermeasures (such as firewalls) ... -
✔✔must be implemented as one or more of these previous types, or the controls are
not there for the purposes of security
Access controls is equated to - ✔✔prevention
In example
In the room where the safe resides, closed-circuit televisions, motion sensors, and
alarm systems quickly detect any unusual activity - ✔✔(detection)
In example
The sound of an alarm could trigger the doors to automatically lock, the police to be
notified, or the room to fill with tear gas - ✔✔(response).
Controls are implemented to - ✔✔mitigate risk and reduce the potential for loss.
Process controls are implemented to - ✔✔ensure that different people can perform the
same operations exactly in the same way each time. Processes are documented as
procedures on how to carry out an activity related to security.
People, process, and technology controls are - ✔✔essential elements of several areas
of practice in information technology (IT) security, including operations security,
applications development security, physical security, and cryptography. These three
pillars of security are often depicted as a three-legged stool
Security functional requirements describe which of the following? - ✔✔What a security
system should do by design
Security controls are the basic toolkit for the security practitioner who mixes and
matches them to carry out the objectives of confidentiality, integrity, and/or availability
by using - ✔✔people, processes, and technology to bring them to life.
Process controls for IT security include assignment of roles for - ✔✔least privilege,
separation of duties, and include documented procedures
Question :ISC2 was formed for which of the following purposes? - ✔✔Maintaining a
common body of lknoweldge for IS, certifying industy professionals and practioners in
ana international IS standard, ensuring that creds are maintained
Which of the following statements best describes the information security Common
Body of Knowledge? - ✔✔The information security Common Body of Knowledge is a
compilation and distillation of all security information collected internationally of
relevance to information security professionals.
How many domains are contained within the CBK? - ✔✔8
The Information Security Governance and Risk Management domain includes which of
the following? - ✔✔Documented policies, standards, procedures, and guidelines
Management of risk to corporate assets
The Security Architecture and Design domain includes which of the following? -
✔✔Concepts and principles for secure designs of computing resources
[Show More]


















.png)