*NURSING > QUESTIONS & ANSWERS > Fortinet NSE 4 - FortiOS 6.0 - EXAM and solution (All)
Fortinet NSE 4 - FortiOS 6.0 - EXAM and solution
Document Content and Description Below
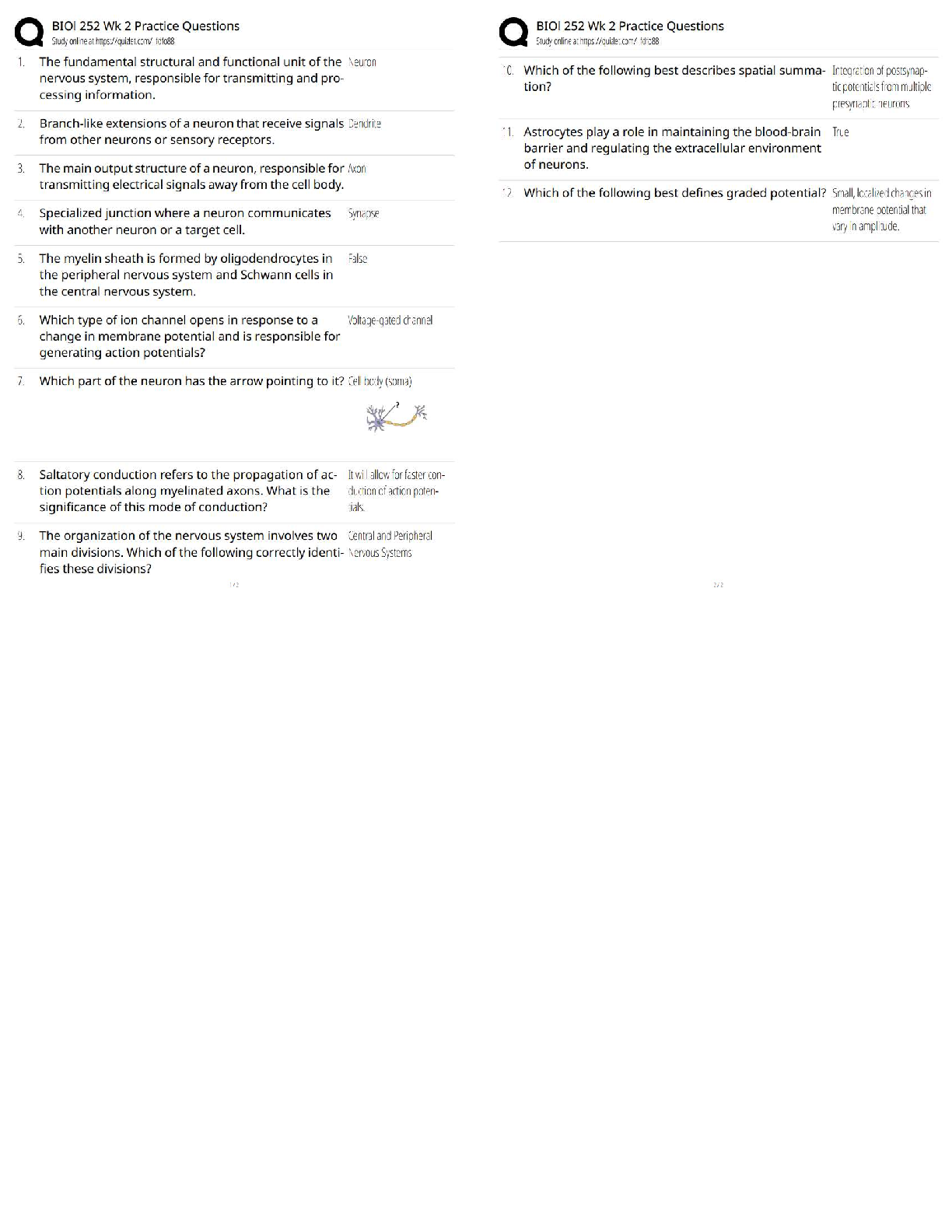
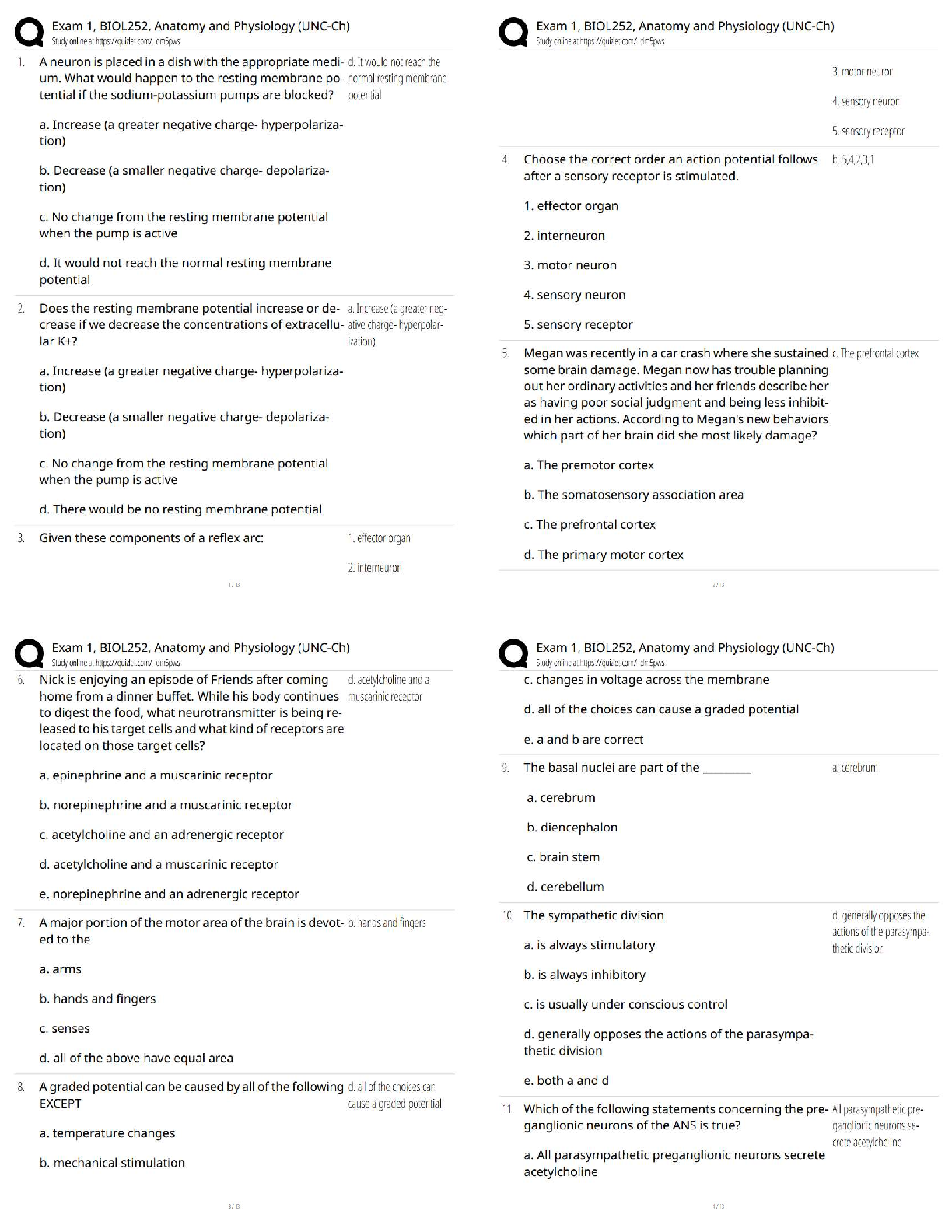
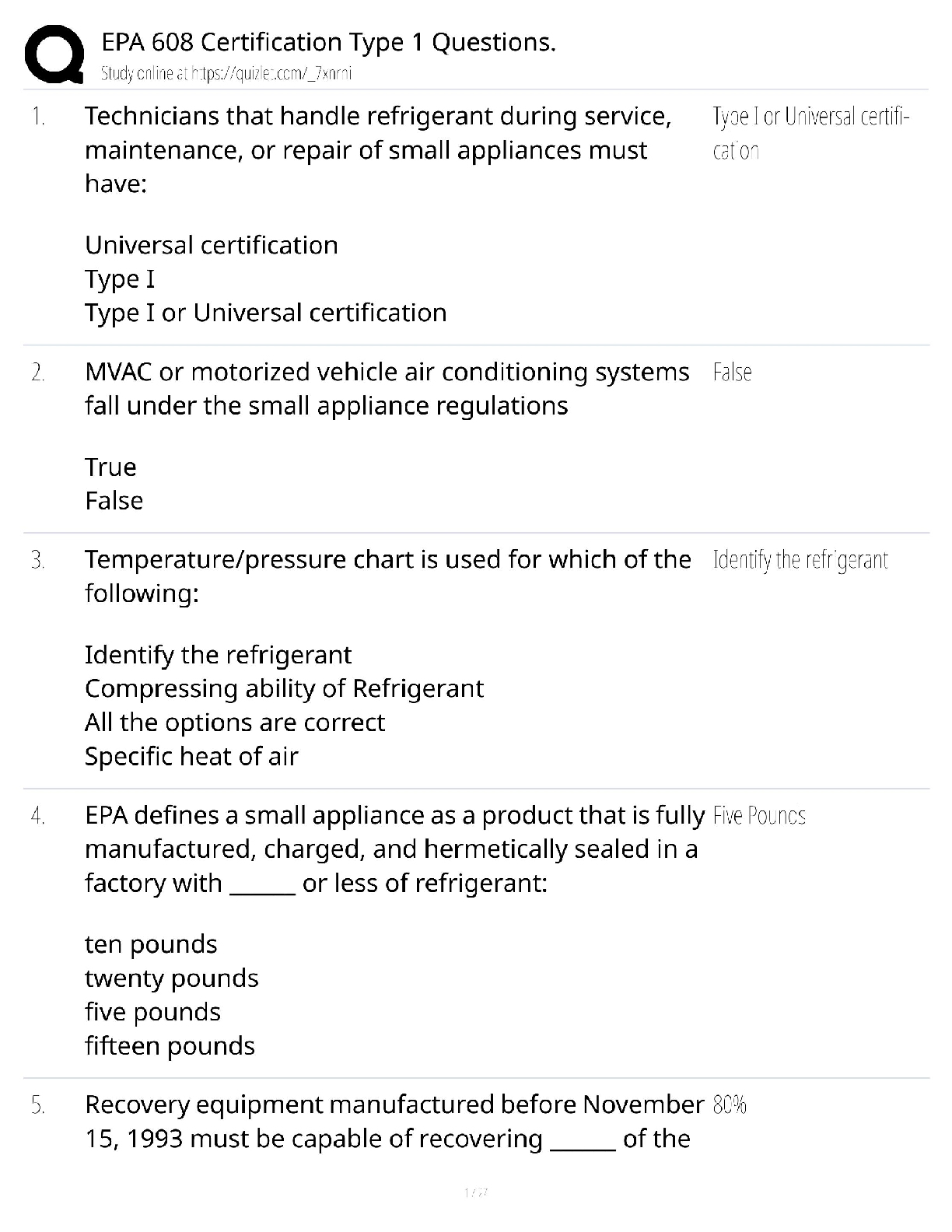
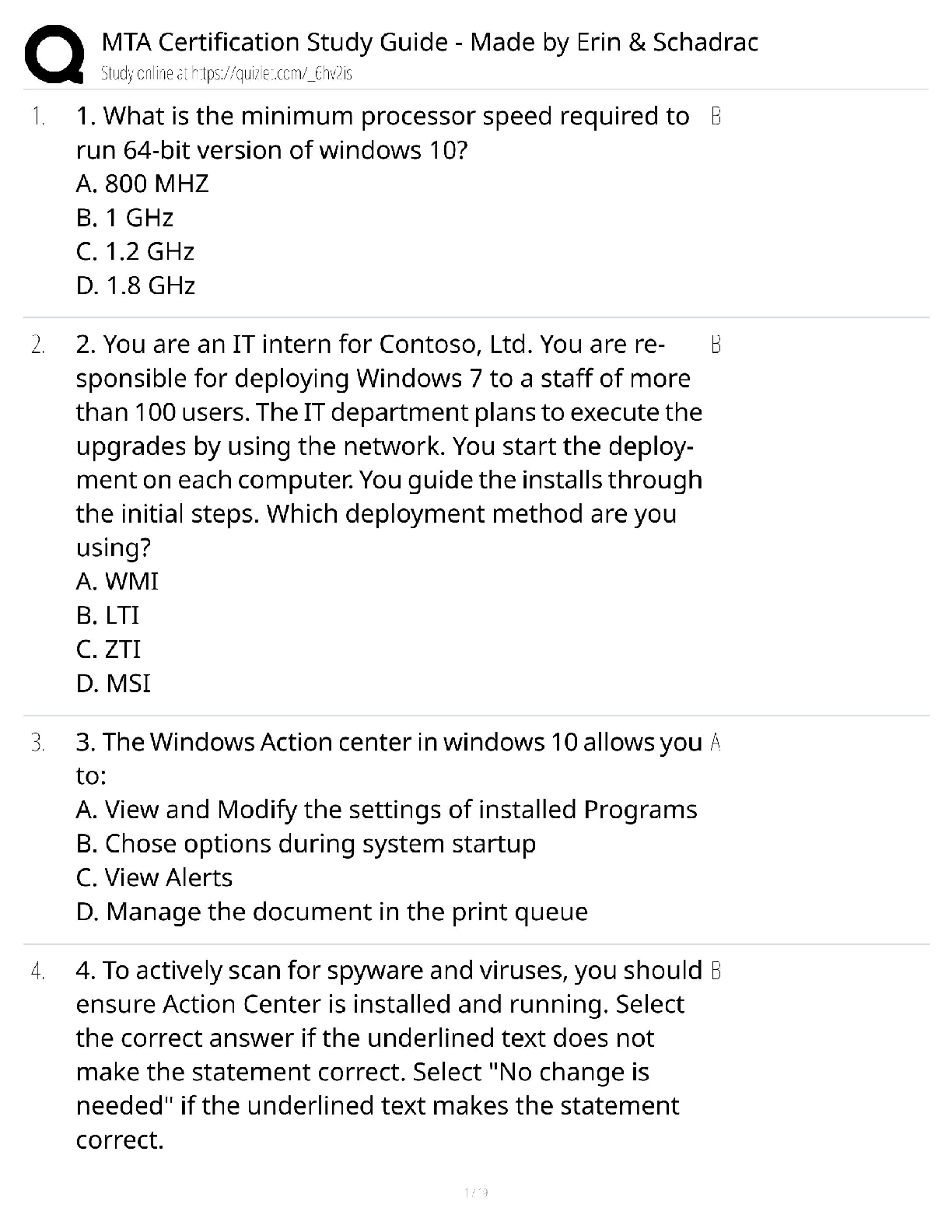
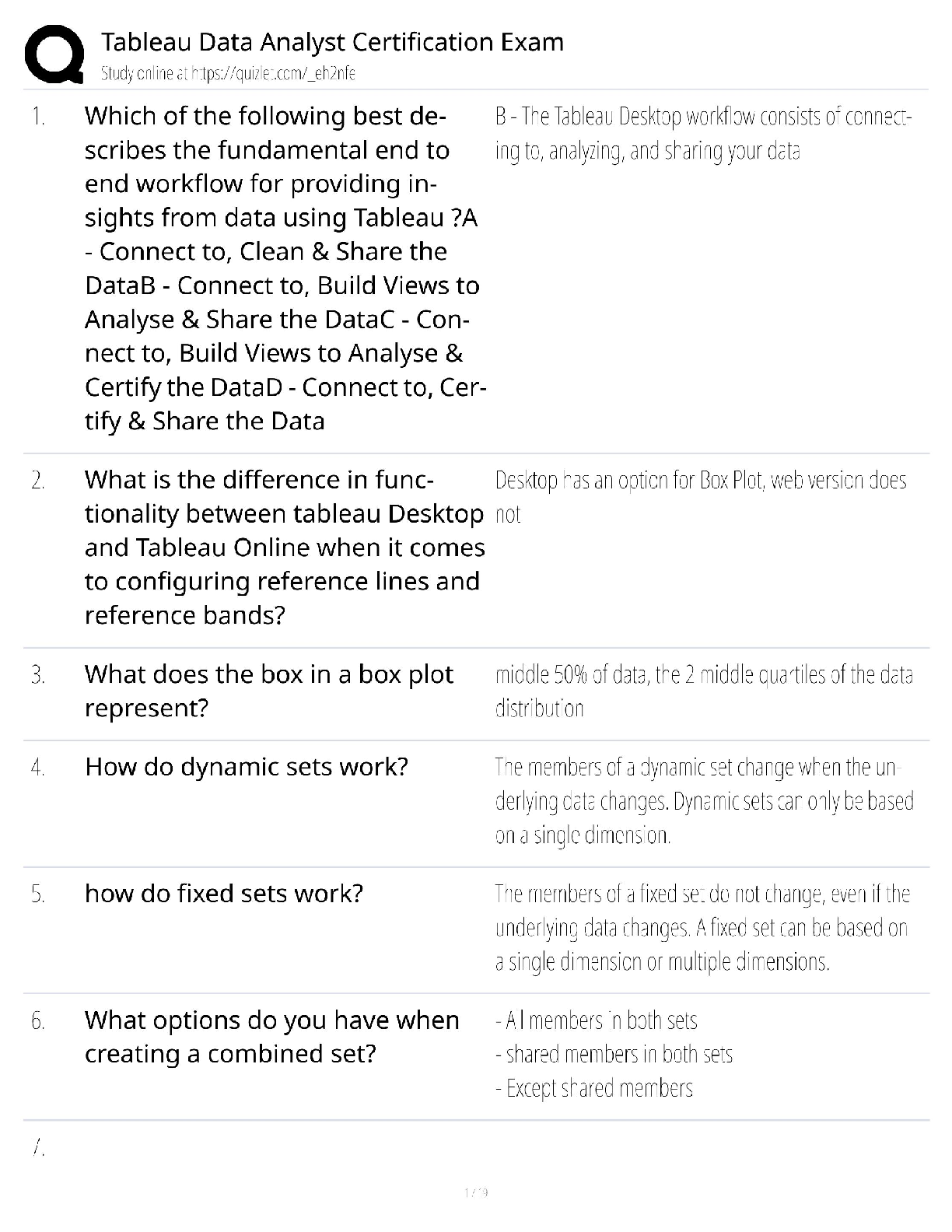
NO.1 Which statement about the IP authentication header (AH) used by IPsec is true? A. AH does not provide any data integrity or encryption. B. AH does not support perfect forward secrecy. C. AH pr ... ovides data integrity but no encryption. D. AH provides strong data integrity but weak encryption. NO.2 An administrator needs to create an SSL-VPN connection for accessing an internal server using the bookmark Port Forward. What step is required for this configuration? A. Configure an SSL VPN realm for clients to use the port forward bookmark. B. Configure the client application to forward IP traffic through FortiClient. C. Configure the virtual IP address to be assigned t the SSL VPN users. D. Configure the client application to forward IP traffic to a Java applet proxy. NO.3 When override is enabled, which of the following shows the process and selection criteria that are used to elect the primary FortiGate in an HA cluster? A. Connected monitored ports > HA uptime > priority > serial number B. Priority > Connected monitored ports > HA uptime > serial number C. Connected monitored ports > priority > HA uptime > serial number D. HA uptime > priority > Connected monitored ports > serial number NO.4 Which statements about HA for FortiGate devices are true? (Choose two.) A. Sessions handled by proxy-based security profiles cannot be synchronized. B. Virtual clustering can be configured between two FortiGate devices that have multiple VDOMs. C. HA management interface settings are synchronized between cluster members. D. Heartbeat interfaces are not required on the primary device. NO.5 What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.) A. Traffic to botnet servers B. Traffic to inappropriate web sites C. Server information disclosure attacks D. Credit card data leaks E. SQL injection attacks NO.6 Examine the exhibit, which contains a virtual IP and firewall policy configuration. IT Certification Guaranteed, The Easy Way! 2 The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address 10.0.1.254/24. The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address. Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IT Certification Guaranteed, The Easy Way! 3 IP address 10.0.1.10/24? A. 10.200.1.10 B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24 C. 10.200.1.1 D. 10.0.1.254 NO.7 Which of the following statements about virtual domains (VDOMs) are true? (Choose two.) A. The root VDOM is the management VDOM by default. B. A FortiGate device has 64 VDOMs, created by default. C. Each VDOM maintains its own system time. D. Each VDOM maintains its own routing table. NO.8 A team manager has decided that while some members of the team need access to particular website, the majority of the team does not. Which configuration option is the most effective option to support this request? A. Implement a web filter category override for the specified website. B. Implement web filter authentication for the specified website C. Implement web filter quotas for the specified website. D. Implement DNS filter for the specified website. [Show More]
Last updated: 3 years ago
Preview 1 out of 45 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 23, 2022
Number of pages
45
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 23, 2022
Downloads
0
Views
163