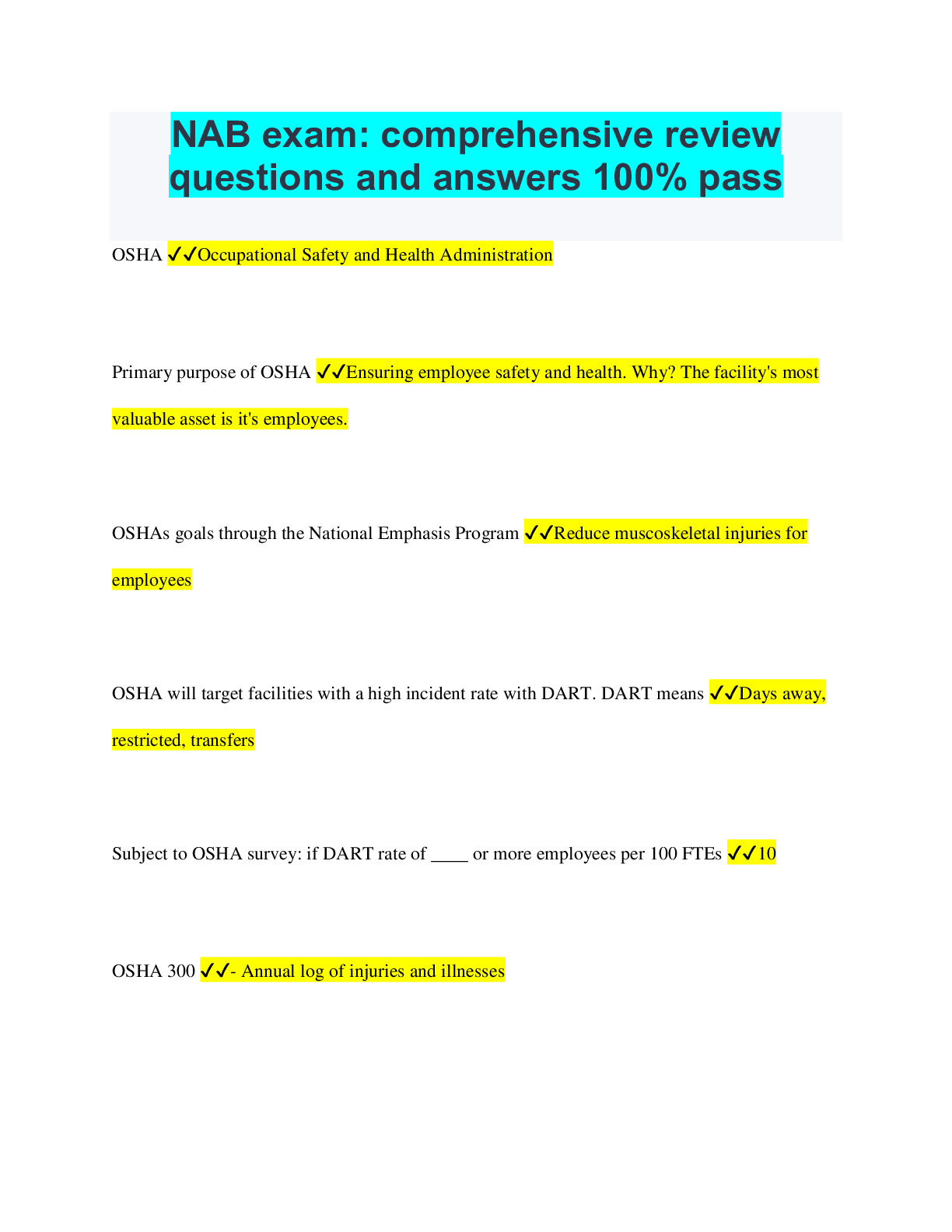
NAB exam: comprehensive review questions and answers 100% pass
$ 7
[eBook] [PDF] Science Fiction and Utopia in the Space of Possible Worlds Vol 28 By Alexander Popov, Zone Theory
$ 30

LDR 531 Final Exam Guide 2019/LDR 531 Final Exam Guide 2019
$ 15
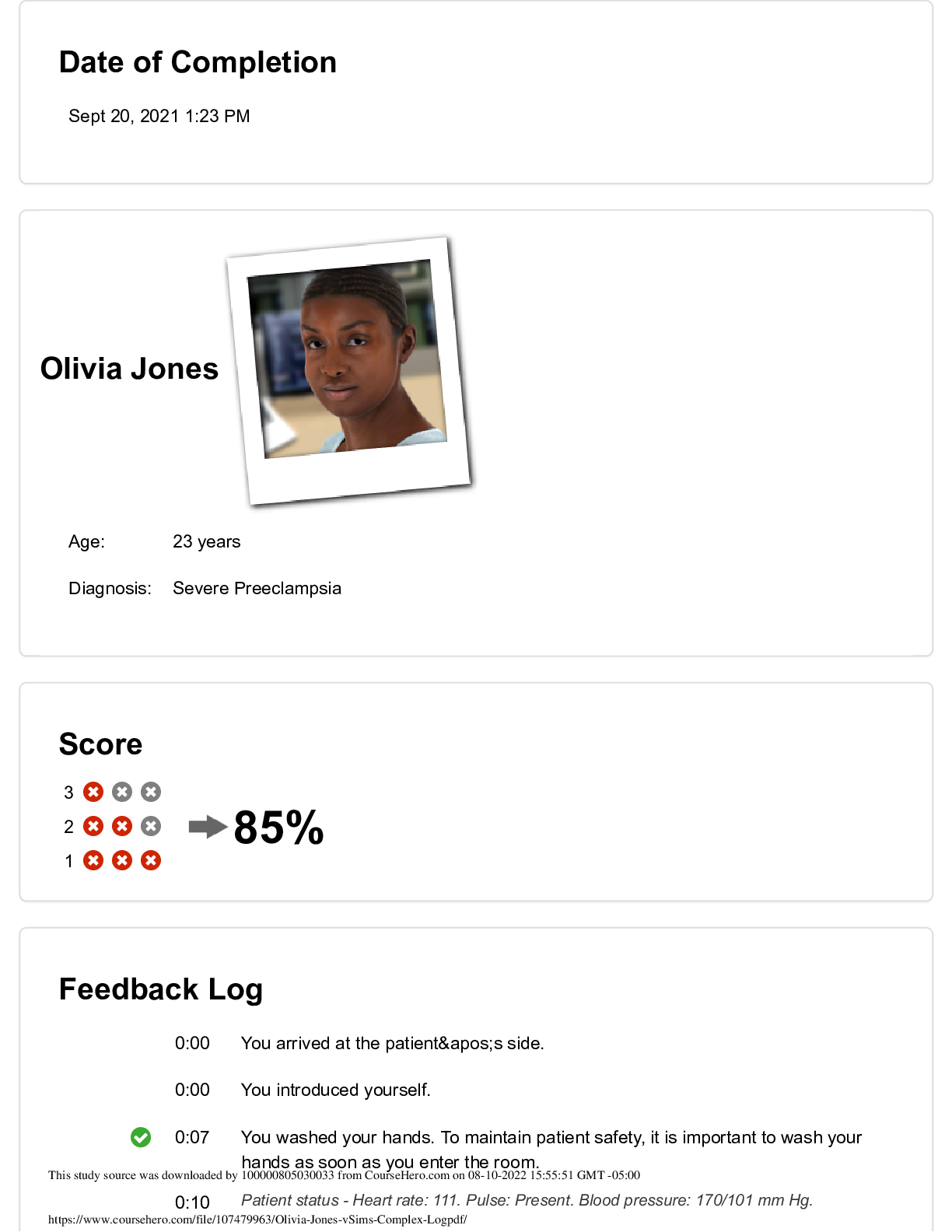
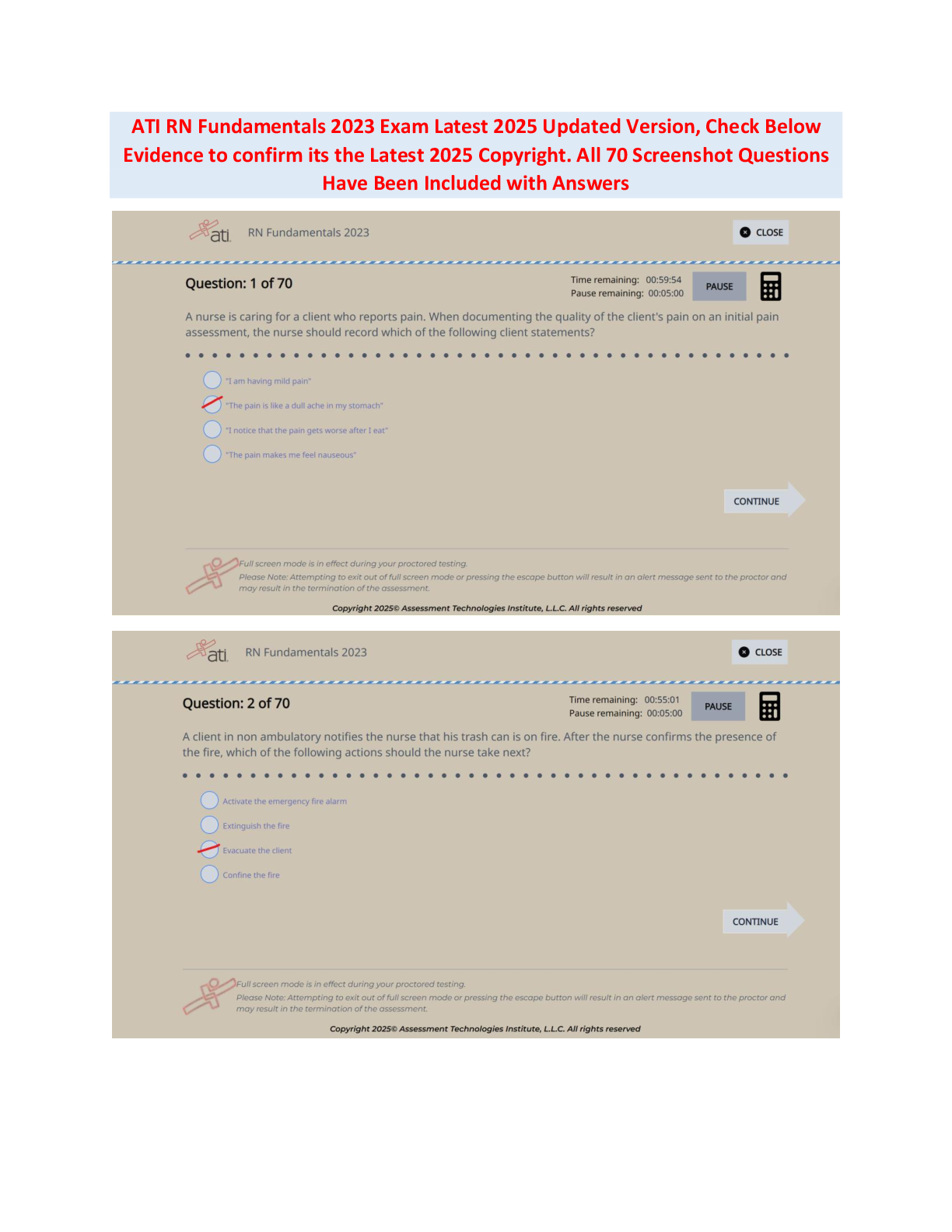
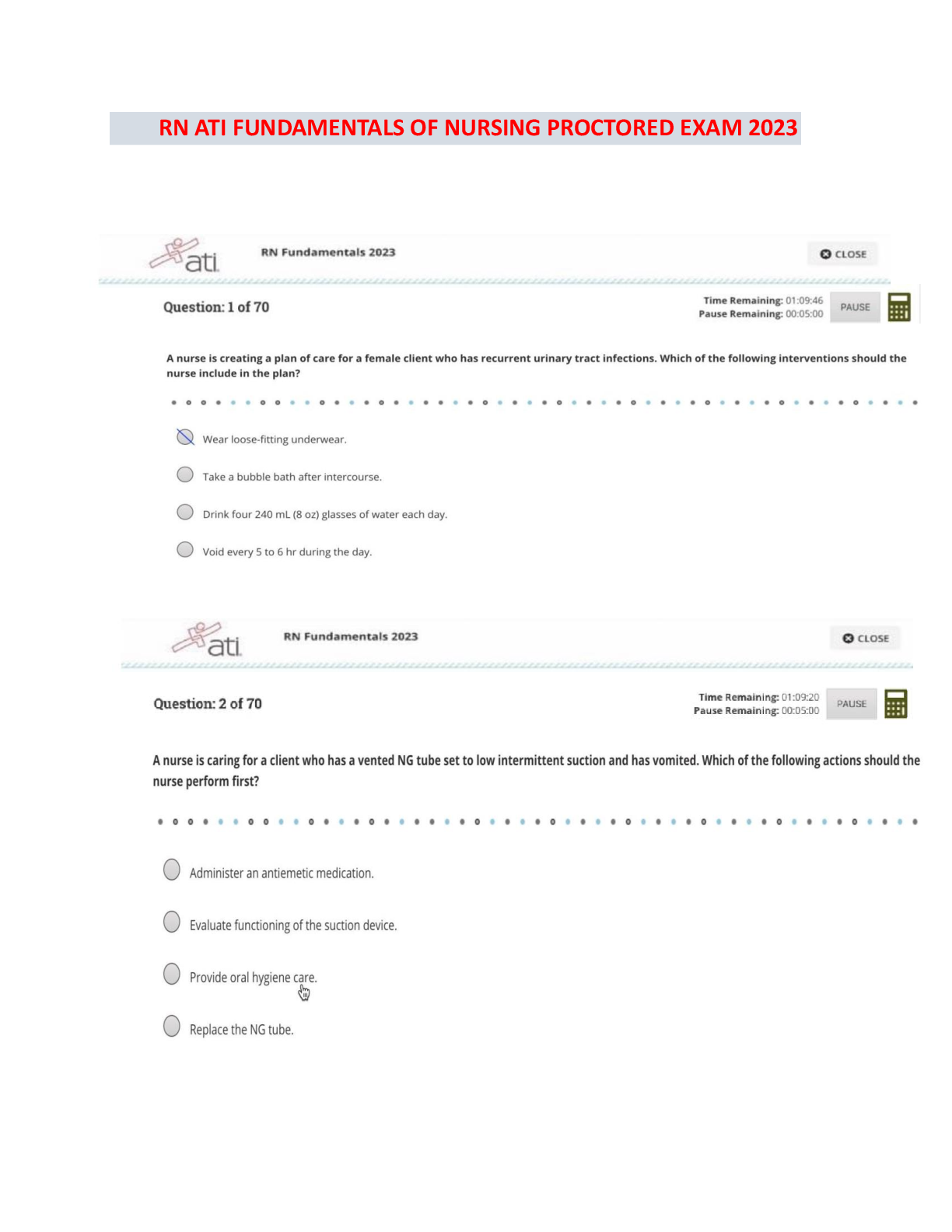
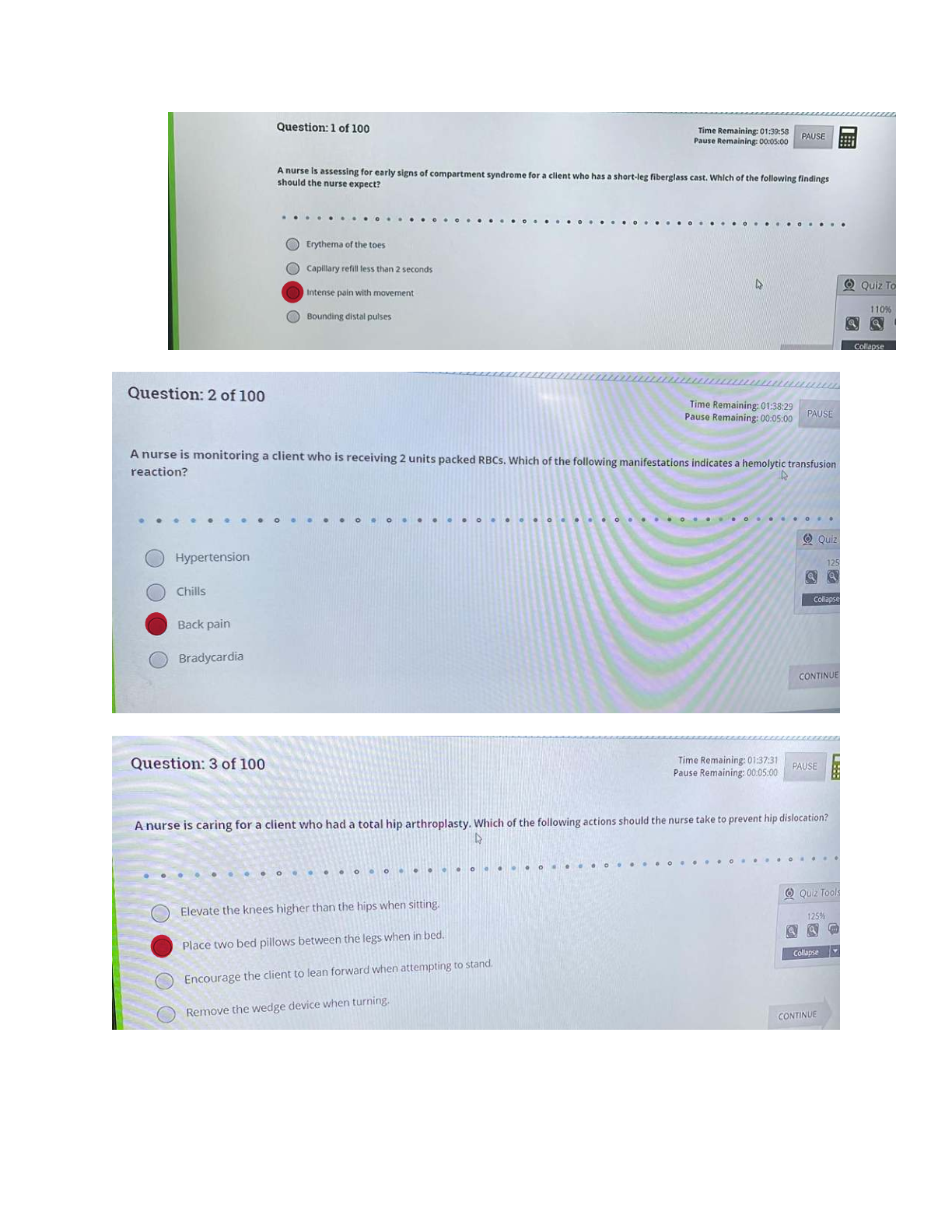
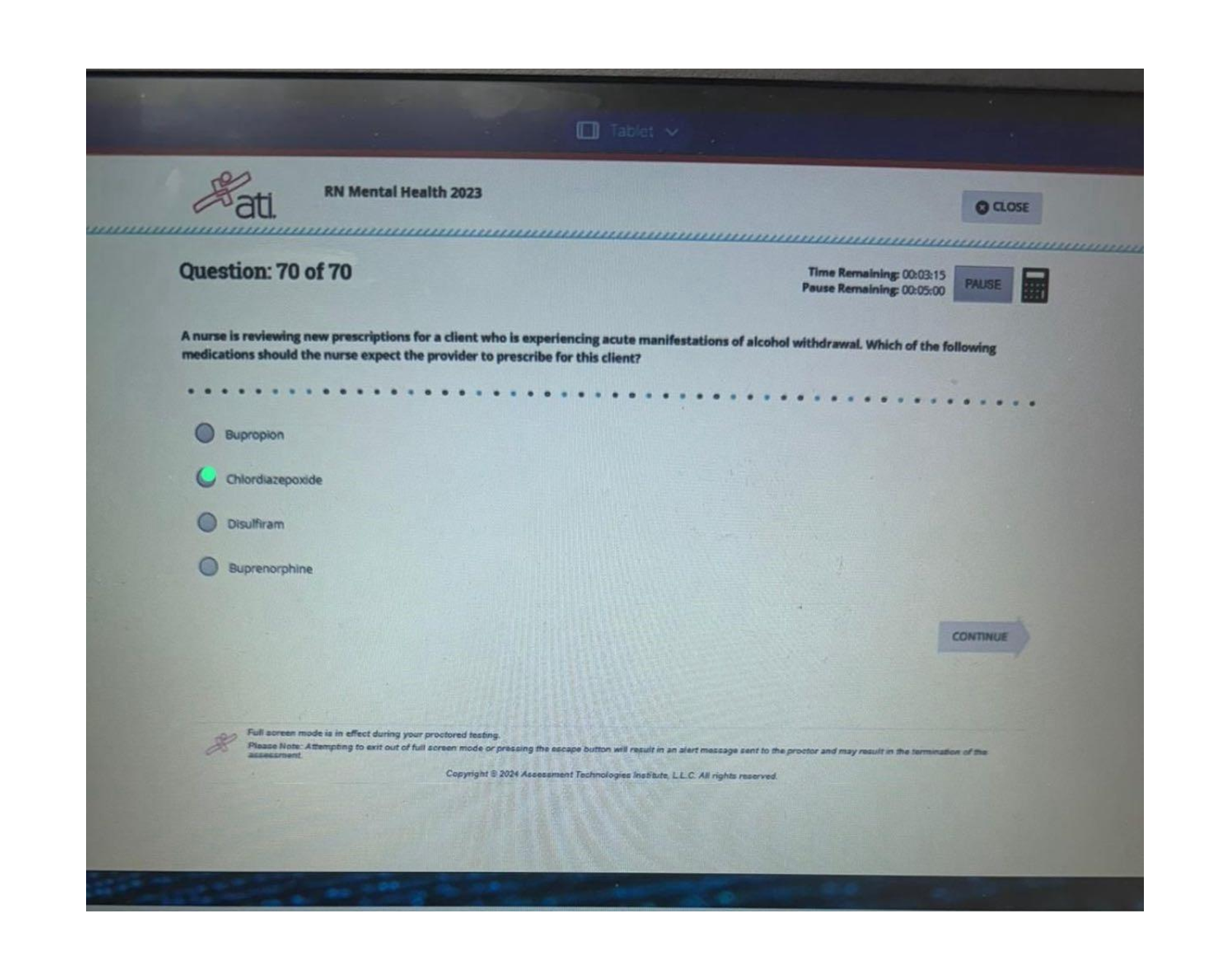
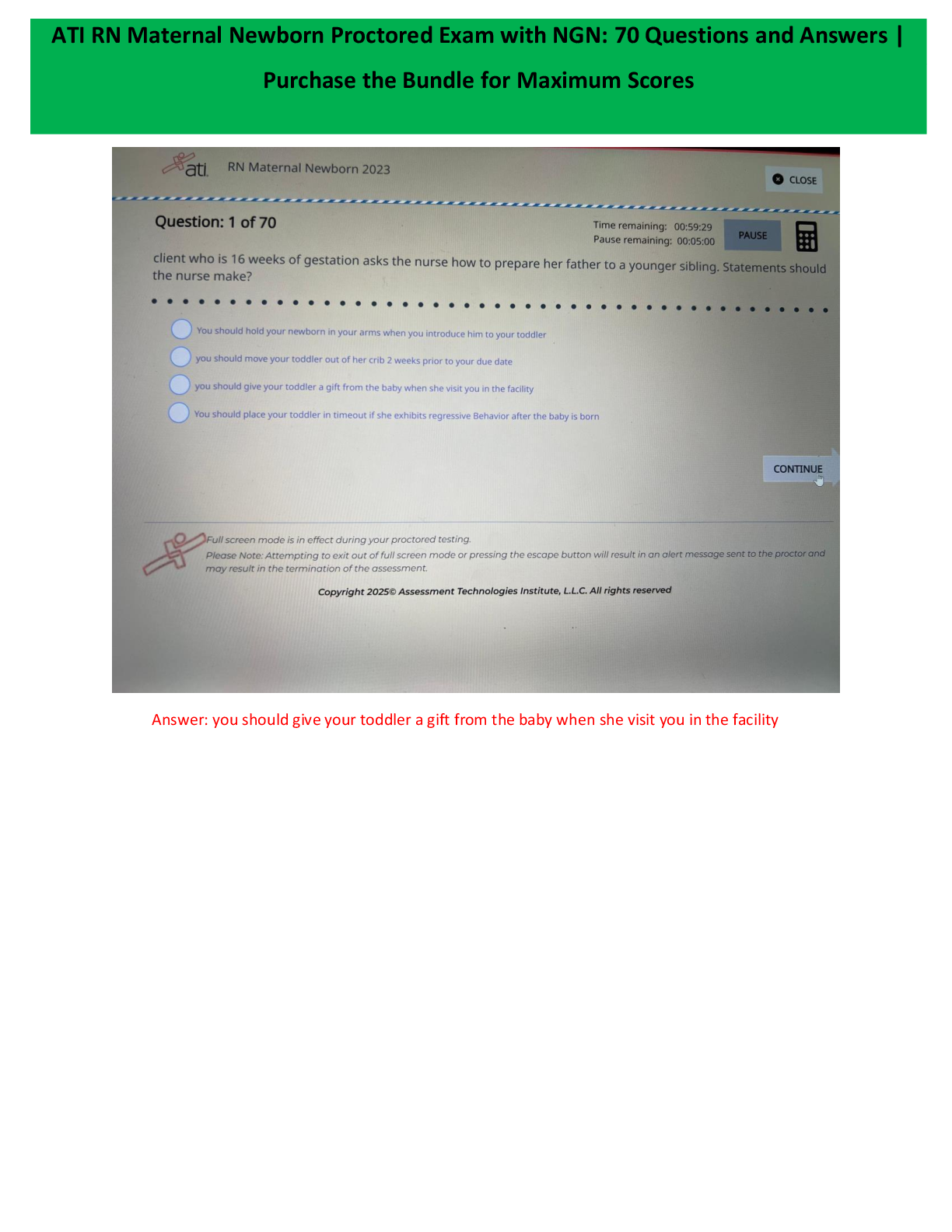
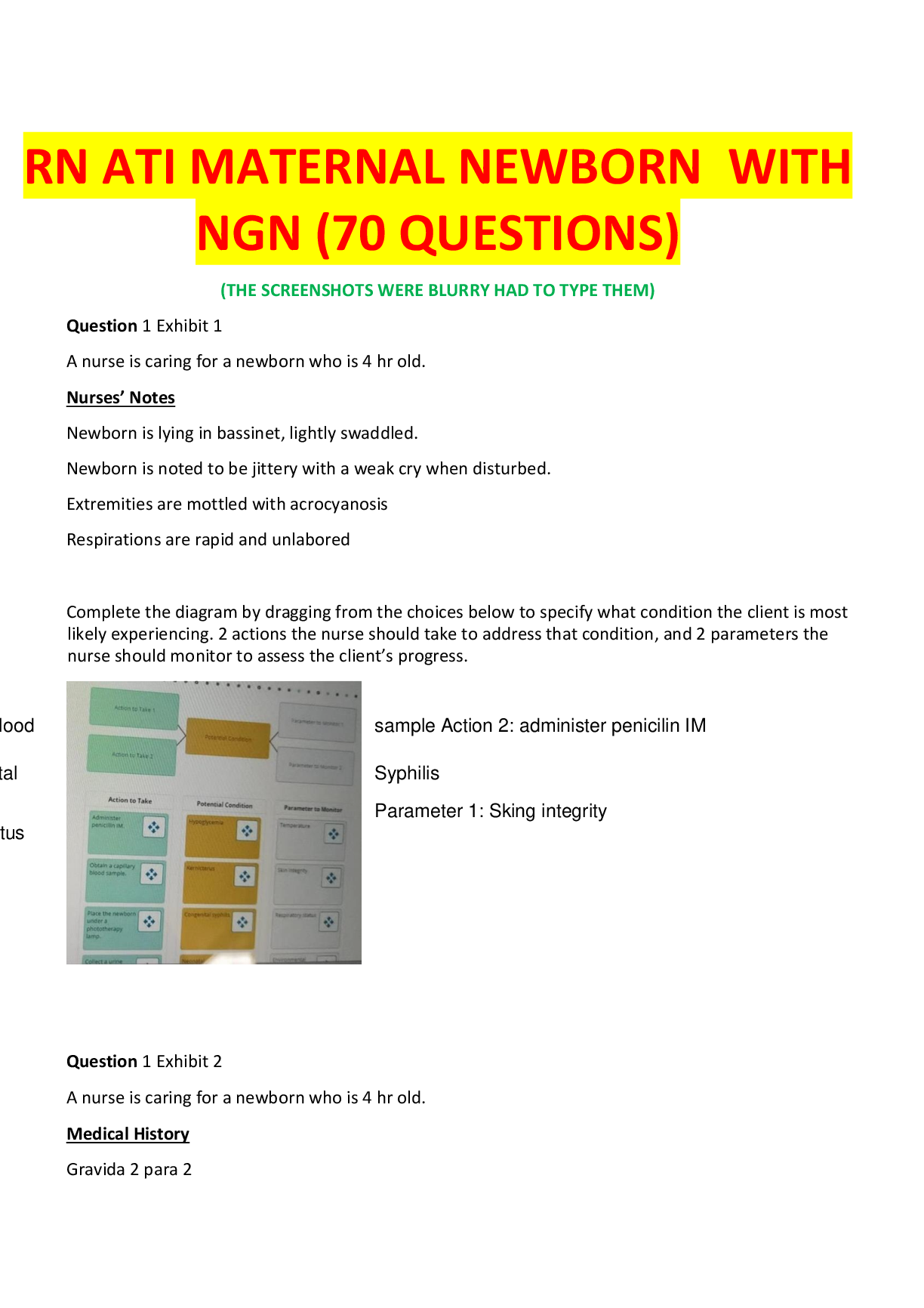
ATI RN COMPREHENSIVE EXAM 2024
$ 50
MT 140 TEST BANK 2023
$ 6

Chapter 01: The Nursing Process and Drug Therapy MULTIPLE CHOICE
$ 12

Questions and Answers > INFO 367 Chapter 2 Problems
$ 5

Test Bank for Nutrition Concepts and Controversies, 16th Edition, Frances Sizer, Ellie Whitney, Leonard Piché
$ 14

eBook Feminist Reconfigurings of Alien Encounters Ethical Co-Existence in More-than-Human Worlds 1st Edition By Nina Lykke, Katja Aglert, Line Henriksen
$ 29

Comptia Network + Exam with Questions & Answers
$ 7

eBook Strategic Management of Technological Innovation 7th Edition By Melissa A. Schilling
$ 30

Reaction Energy GIZMO ( ALL ANSWERS ARE 100% CORRECT )
$ 11

Critical Care HESI Review
$ 20

LMSW EXAM Top Examinable Questions with accurate answers. QuizBank! Graded A Theories of Hu
$ 12
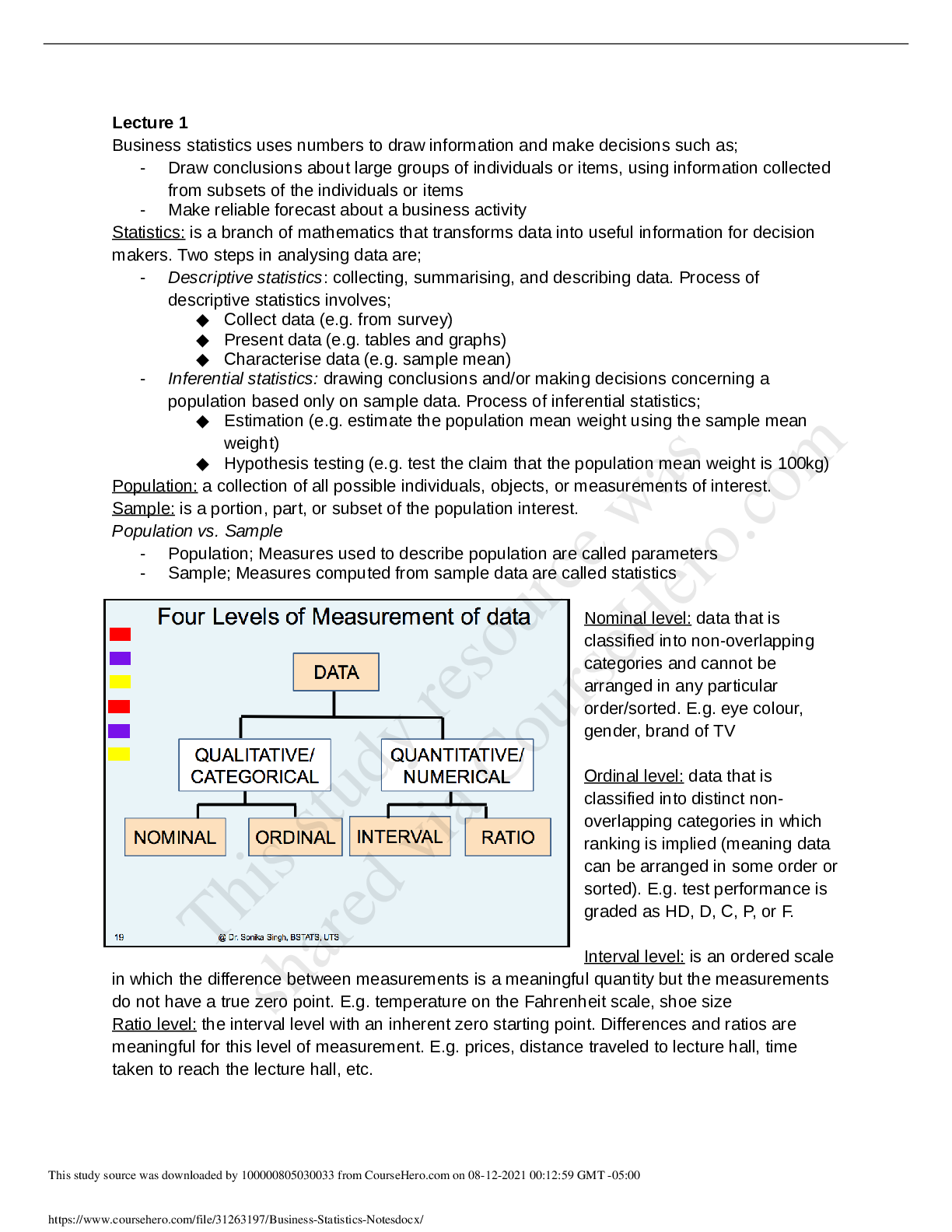
University of Technology Sydney BUSINESS Statistics Notes
$ 12

California Flagger Certification questions and answers complete solution 2024
$ 14.5

eBook PDF Heritage and War 1st Edition By William Bülow, Helen Frowe, Derek Matravers






.png)
.png)