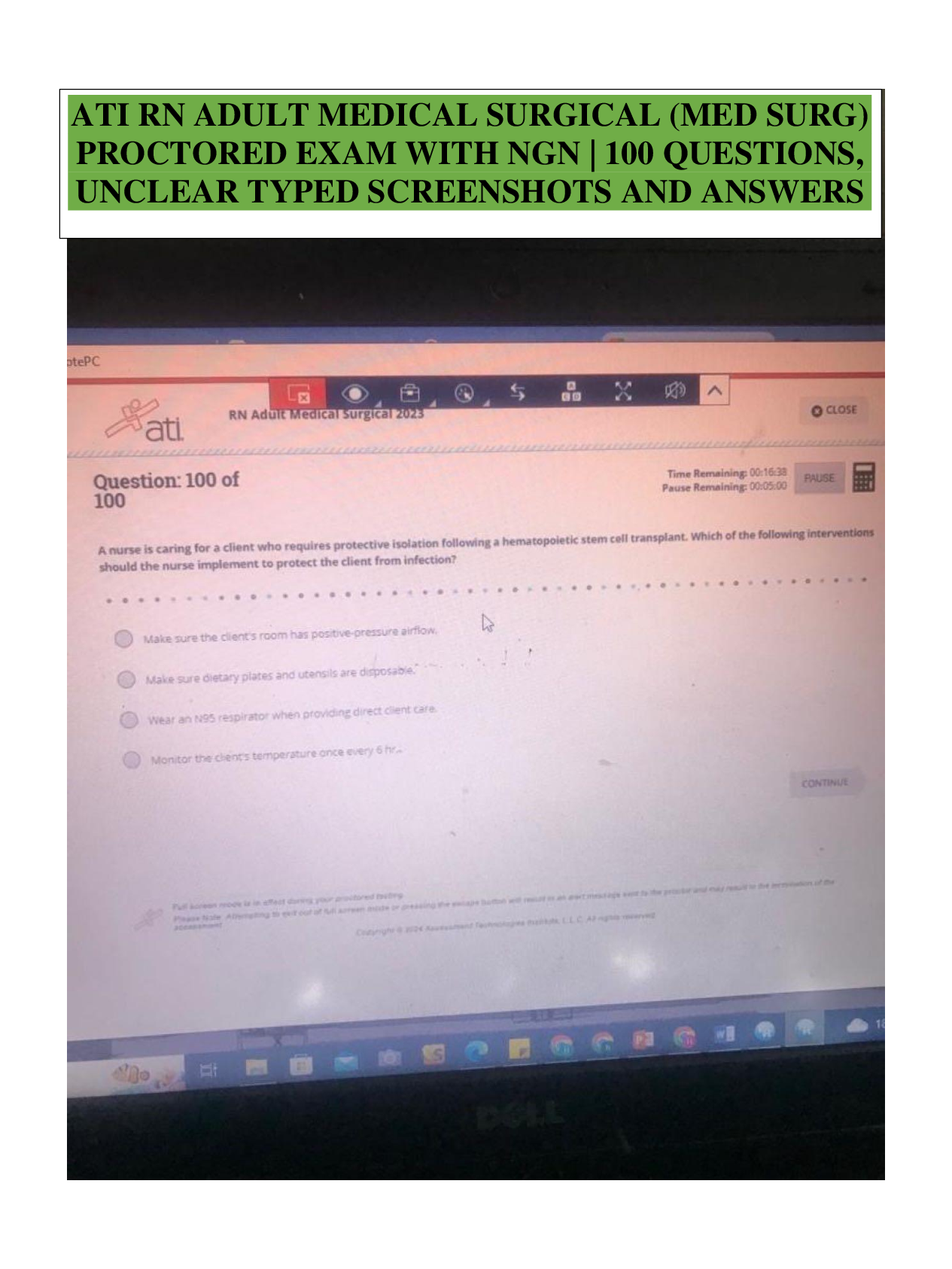
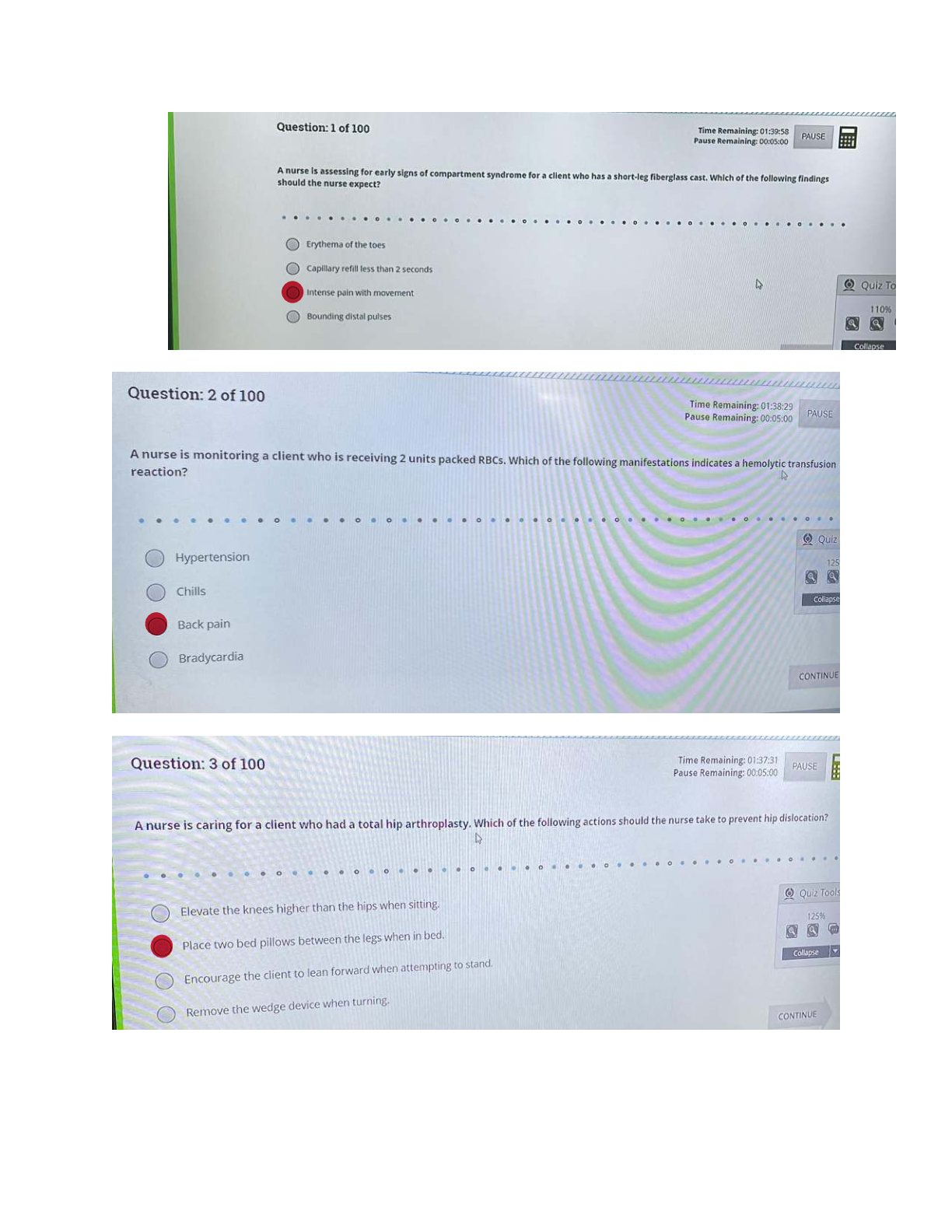
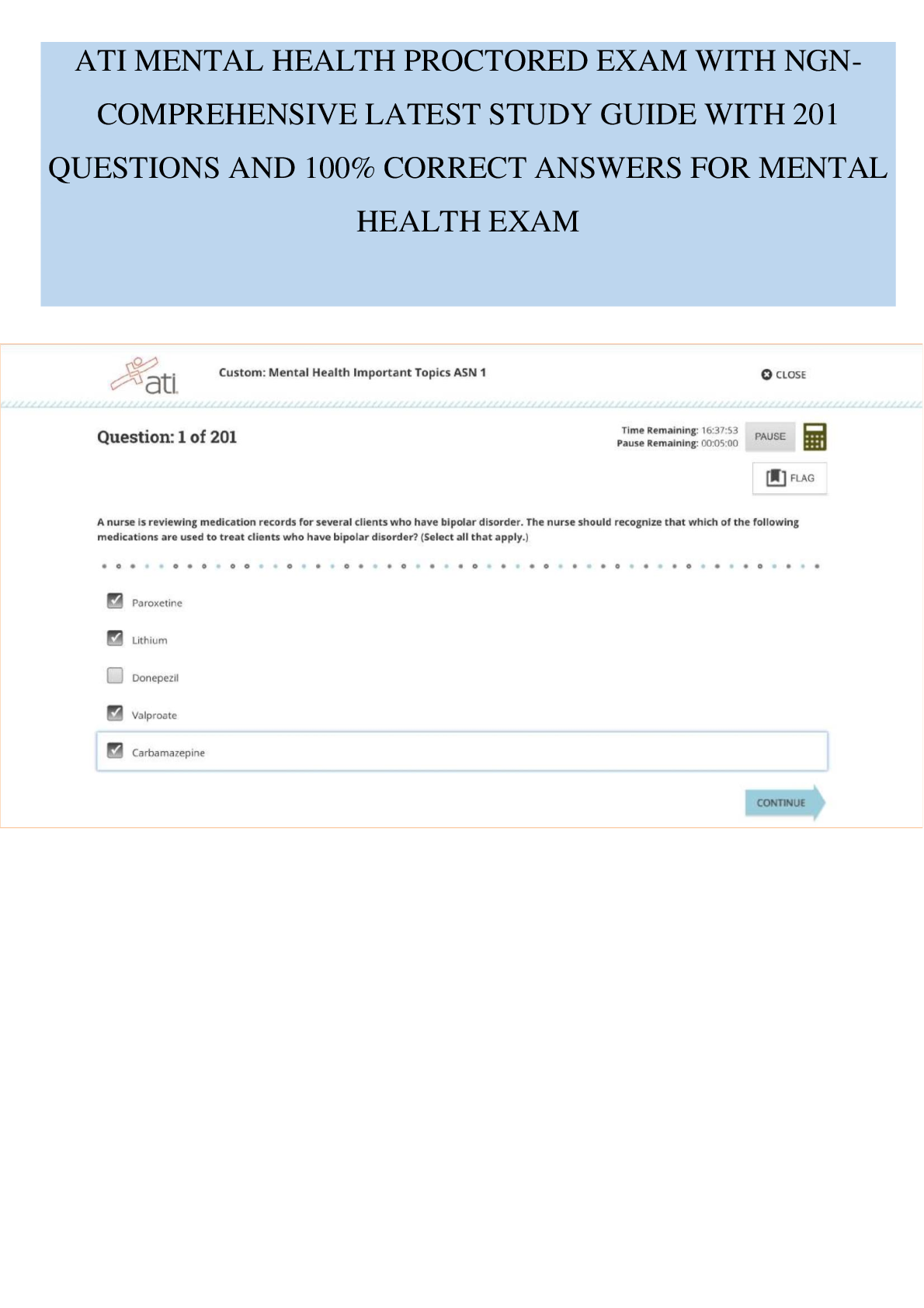
WGU Master's Course C701 - Ethical Hacking Already passed EXAM information on the internet are authentication, authorization, and non-repudiation; those related to the persons accessing information are confidentiality, i
...
WGU Master's Course C701 - Ethical Hacking Already passed EXAM information on the internet are authentication, authorization, and non-repudiation; those related to the persons accessing information are confidentiality, integrity, and availability.
A False
B True - ANSWER A
________ is the greatest asset to an organization.
A Policy
B Personnel
C Technology
D Information - ANSWER D
IA refers to the assurance of the integrity, availability, confidentiality, and authenticity of information and information systems during usage, processing, storage, and transmission of information assurance with the help of physical, technical, and administrative controls.
A False
B True - ANSWER B
Information Assurance and Information Risk Management (IRM) ensure that only authorized personnel access and use information.
A False
B True - ANSWER B
Today's information security management programs are primarily concerned with firewalls and passwords.
A False
B True - ANSWER A
Effective management of information security is NOT an ongoing process; updates should be made periodically.
A False
B True - ANSWER A
The threat model consists of ________ major building block(s).
A three
B one
C two
D four - ANSWER A
EISA ensures that the security architecture and controls are in alignment with the organization's core goals and strategic direction.
A True
B False - ANSWER A
A security zone is an area within a network that consists of a group of systems and other components with the same characteristics, all of which serve to manage a secure network.
A False
B True - ANSWER B
Defense in Depth uses the military principle that it is more difficult for an enemy to defeat a complex and multi-layered defense system than to penetrate a single barrier.
A False
B True - ANSWER B
Defense in Depth is a security strategy in which security professionals use several protection layers throughout an information system.
A False
B True - ANSWER B
Defense in Depth helps to prevent ________ against an information system and its data because a break in one layer only leads the attacker to gain access to a single system.
A indirect attacks
B hacking attacks
C internal attacks
D direct attacks - ANSWER D
Incident management only involves responding to incidents.
A False
B True - ANSWER A
[Show More]