Ciampa CompTIA CySA Plus Guide to
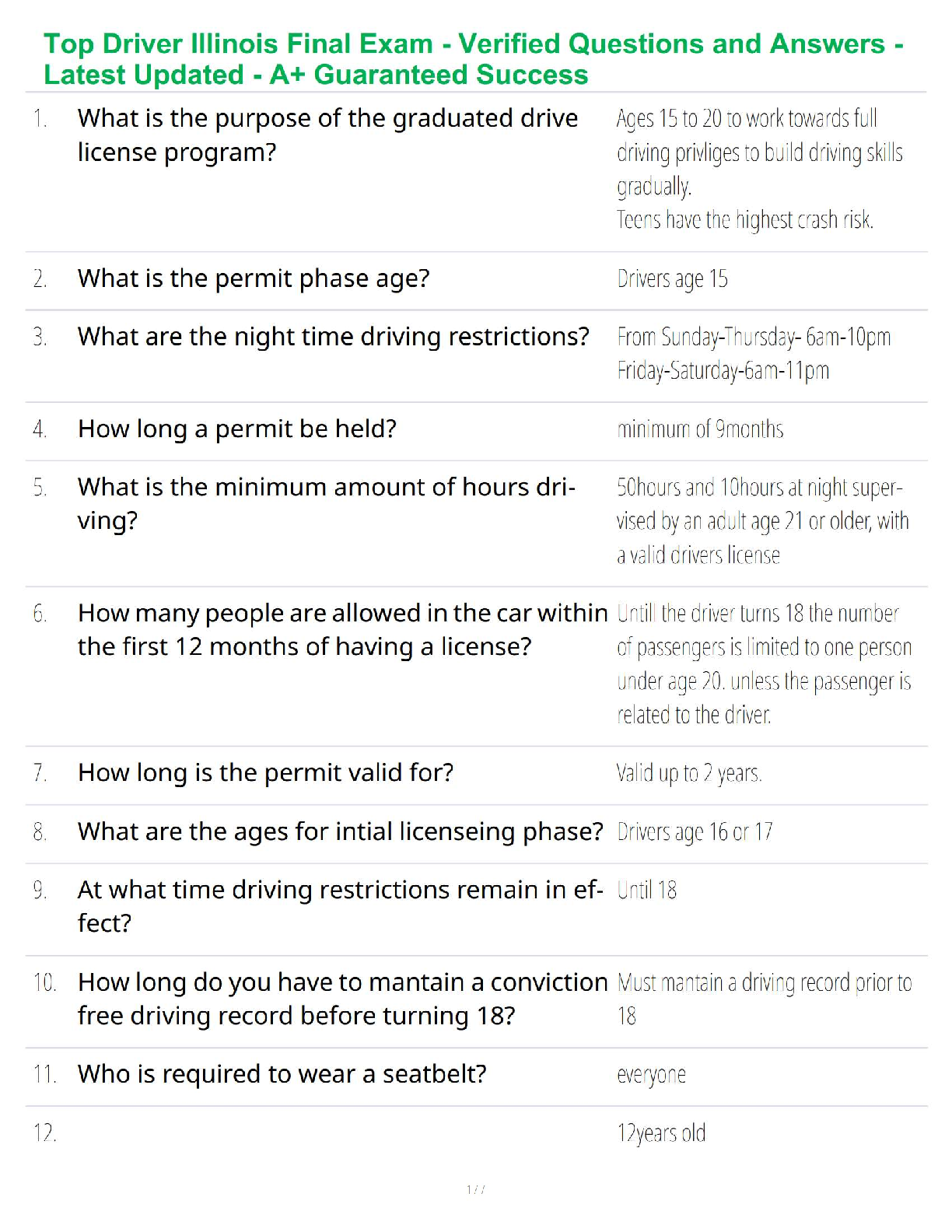
Cybersecurity Analyst 1e Mindtap
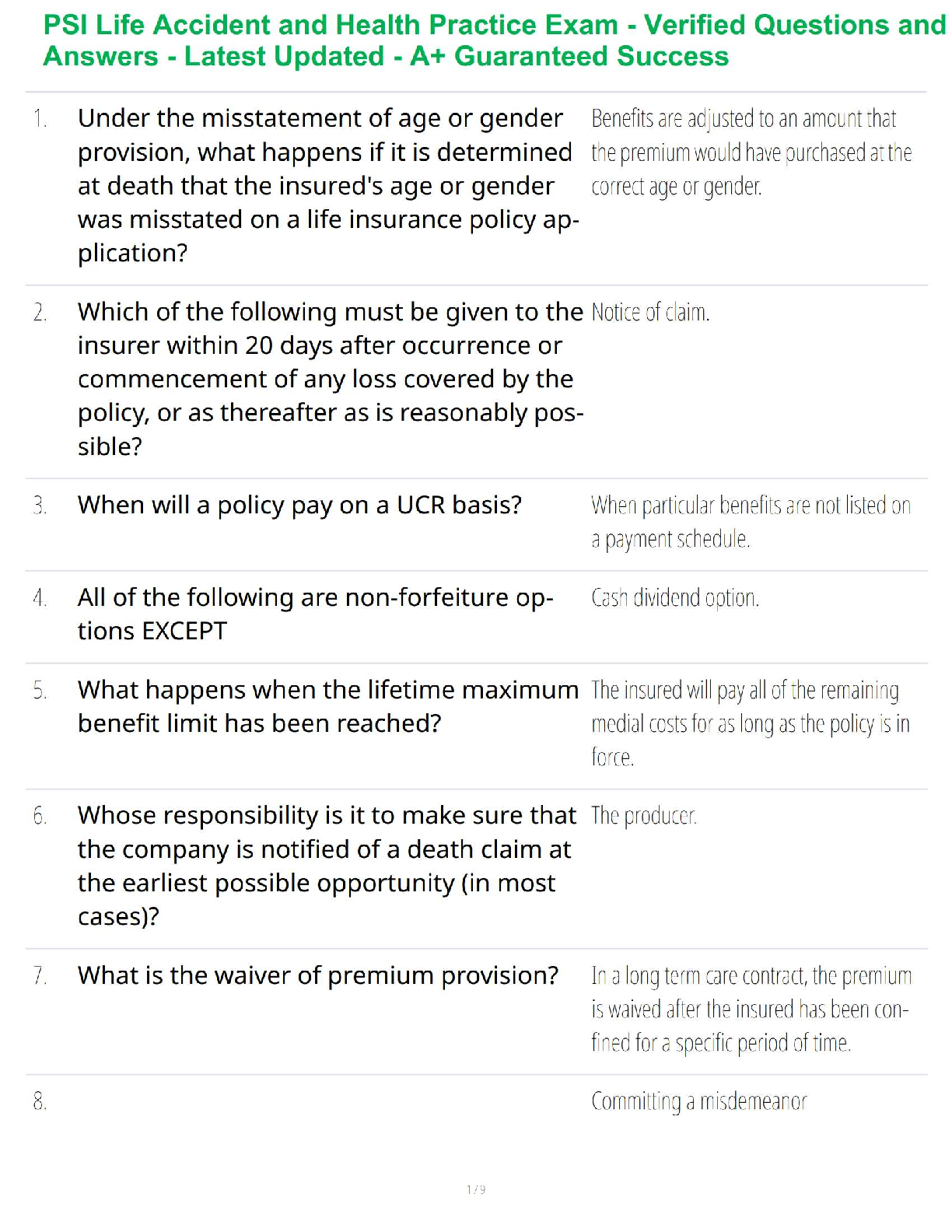
Which of the following is not a position for which the CompTIA CySA+ certification is designed?
a. Firewall analyst
b. Vulnerability analyst
c. Thre
...
Ciampa CompTIA CySA Plus Guide to
Cybersecurity Analyst 1e Mindtap
Which of the following is not a position for which the CompTIA CySA+ certification is designed?
a. Firewall analyst
b. Vulnerability analyst
c. Threat intelligence analyst
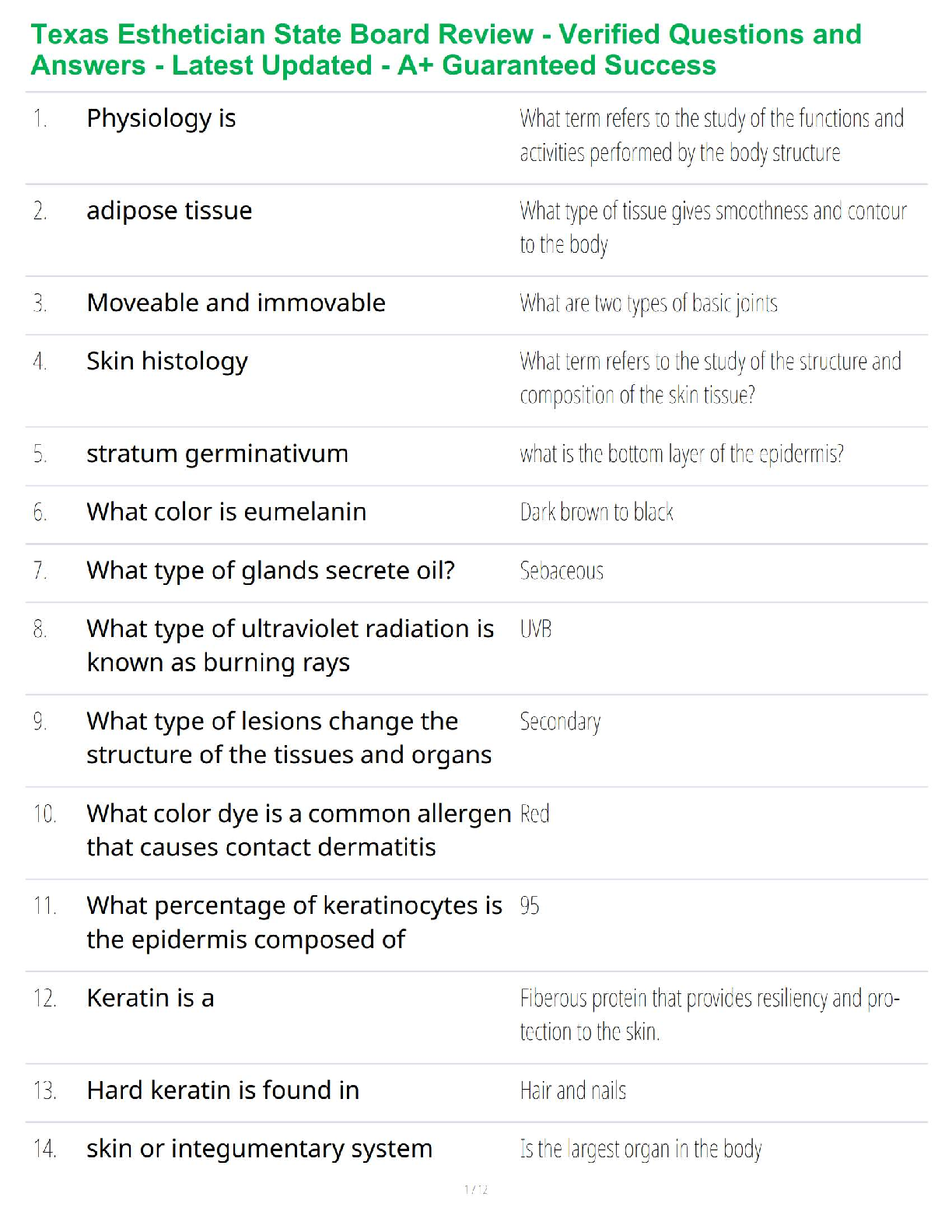
d. Security analyst ✔✔Firewall analyst
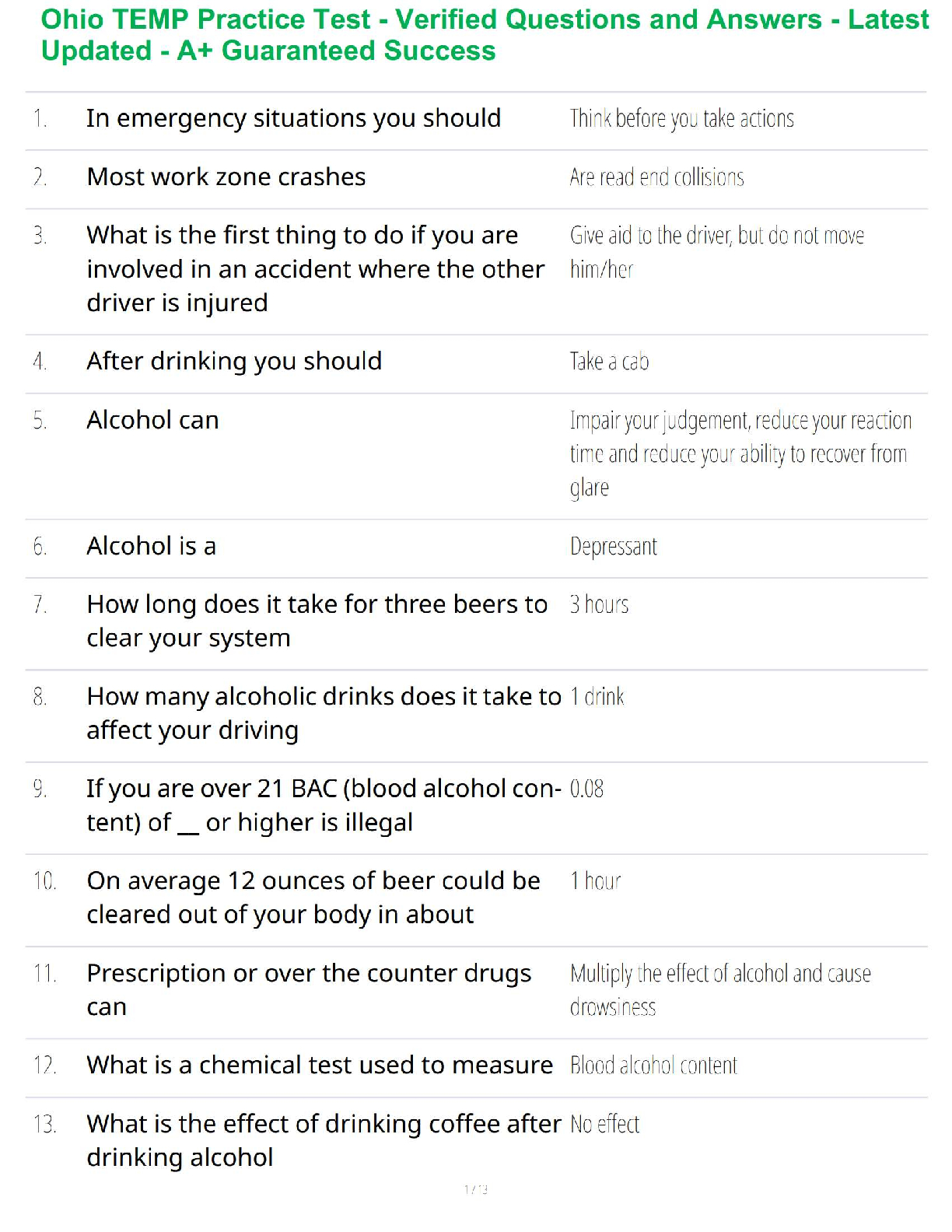
Alyona has been asked by her supervisor to be part of an internal group that will perform an
environmental reconnaissance. Which of the following activities would Alyona not be performing?
a. Probe a competitor's site for weaknesses.
b. Gather information through active and passive techniques.
c. Uncover weaknesses in the organization's cyber defense.
d. Attempt to determine what information a threat actor can gather. ✔✔Probe a competitor's site
for weaknesses.
Tatyana is compiling a list of company employees who may be targeted for user reconnaissance.
Which of the following employees would most likely not be a primary target?
a. Secretary of the president
b. Chief financial officer
c. System administrator
d. Network administrator ✔✔a. Secretary of the president
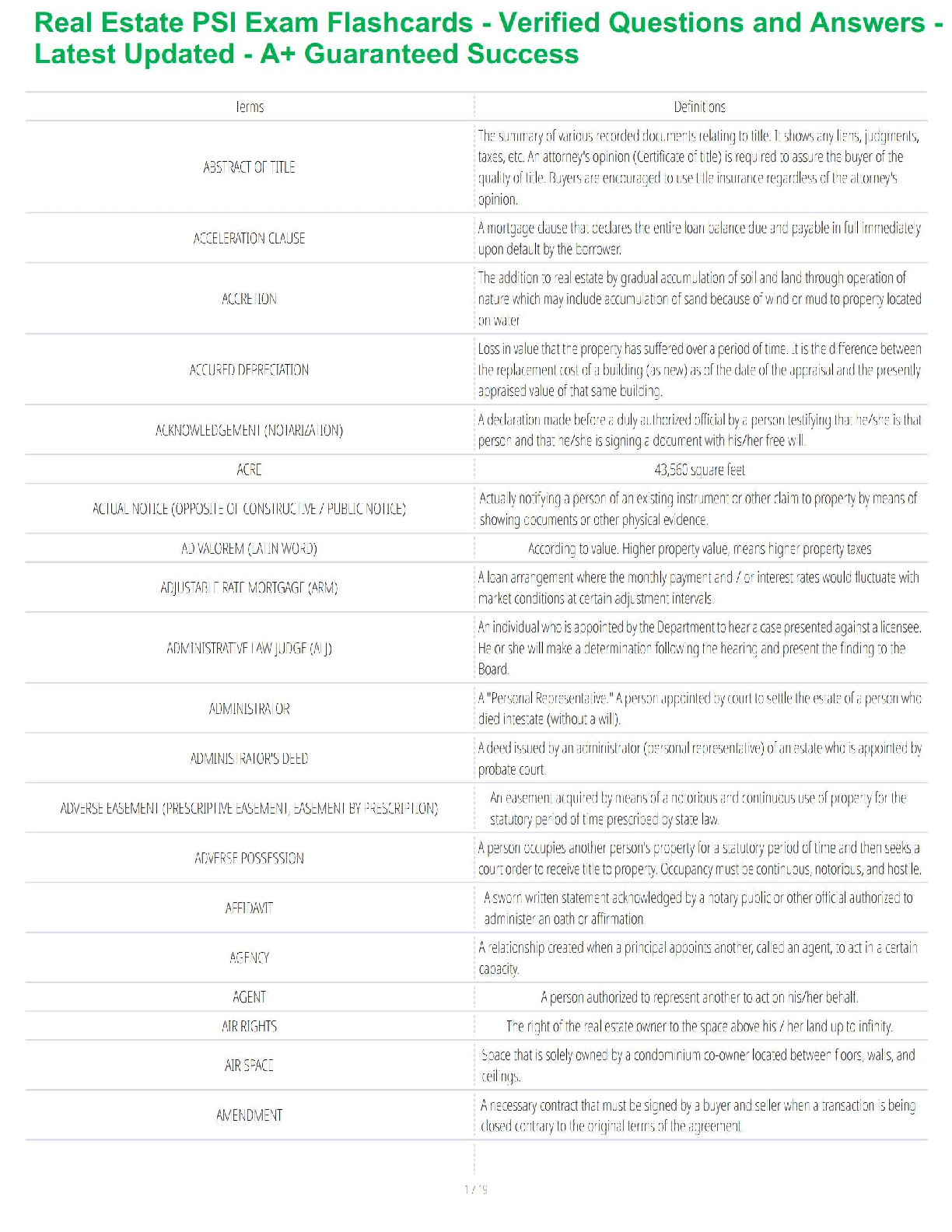
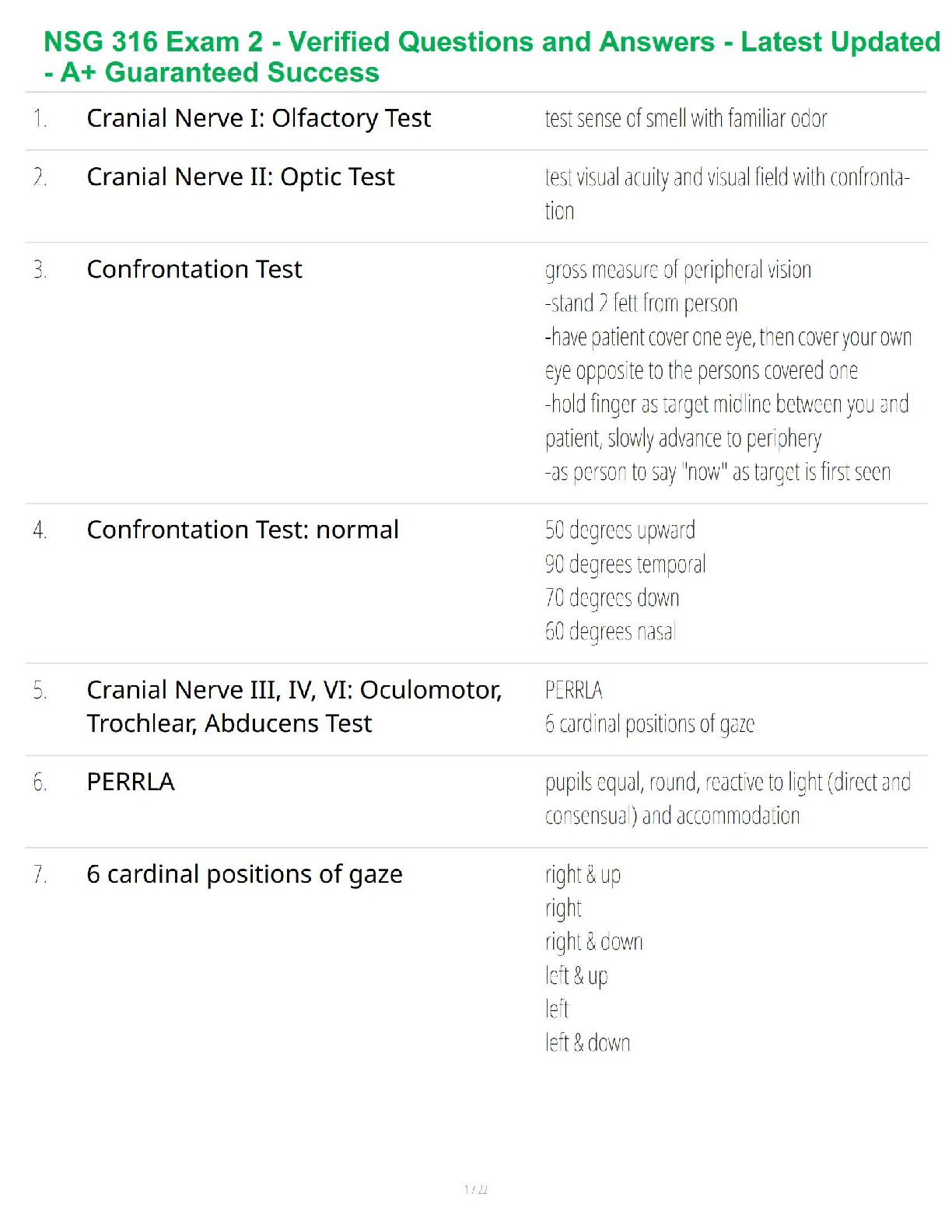
Which of the following statements about social media profiling is true?
a. Social media profiling is considered to be unethical.
b. People search engines can assist when conducting social media profiling.
c. A profile only includes employment information and does not include personal information such
as family connections, hobbies, and interests.
d. Social media profiling is rarely used due to the security protections built into modern social
media sites. ✔✔b. People search engines can assist when conducting social media profiling.
Which of the following is not a goal of network reconnaissance?
a. Topology discovery
b. Threat actor identification
c. Service discovery
d. Operating system fingerprinting ✔✔b. Threat actor identification
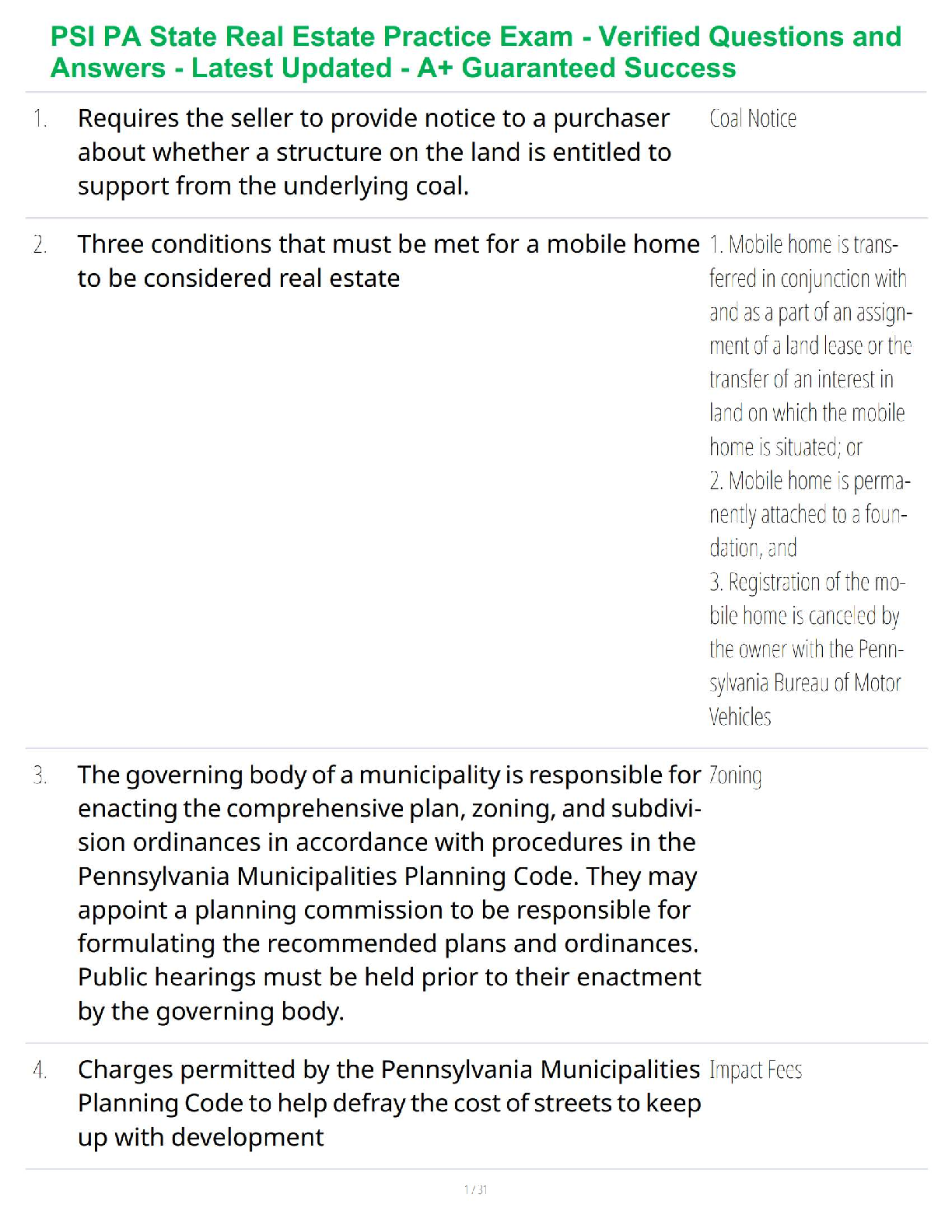
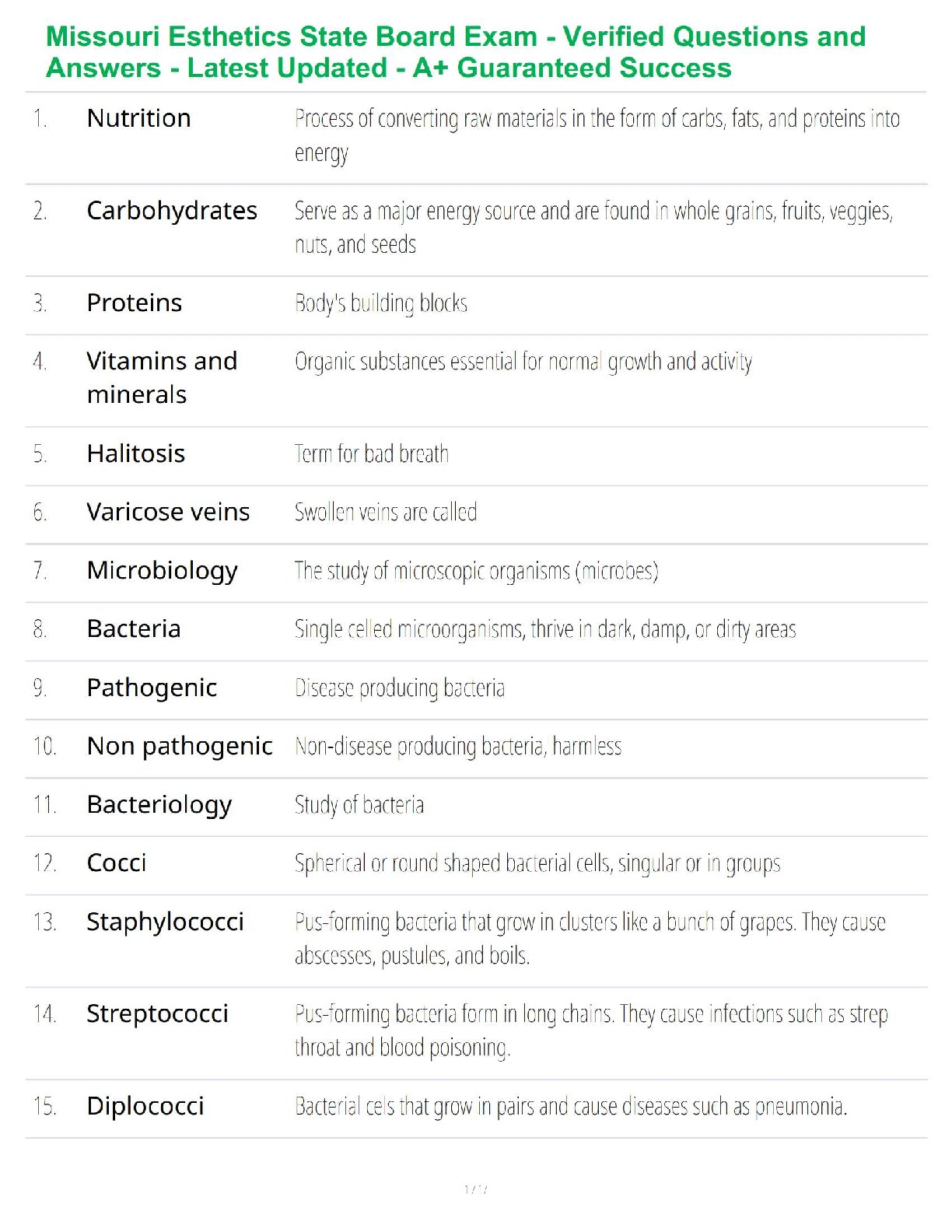
A threat actor who is attempting to uncover the layout of an internal network is performing which
of the following?
a. Site identification
b. Topology discovery
c. Network investigation
d. Packet analysis ✔✔b. Topology discovery
Which of the following is not a reason that a threat actor might have difficulty capturing packets?
a. She would need access to the network, which requires access within a protected building.
b. Packets behave differently once they have left the network.
c. Bypassing network authentication and access control can be difficult.
d. Once the threat actor connects to a network, the connection may become immediately apparent.
✔✔b. Packets behave differently once they have left the netwo
[Show More]
.png)

.png)












.png)