Information Technology > QUESTIONS & ANSWERS > Cysa Review Activities Questions and Answers Already Passed (All)
Cysa Review Activities Questions and Answers Already Passed
Document Content and Description Below
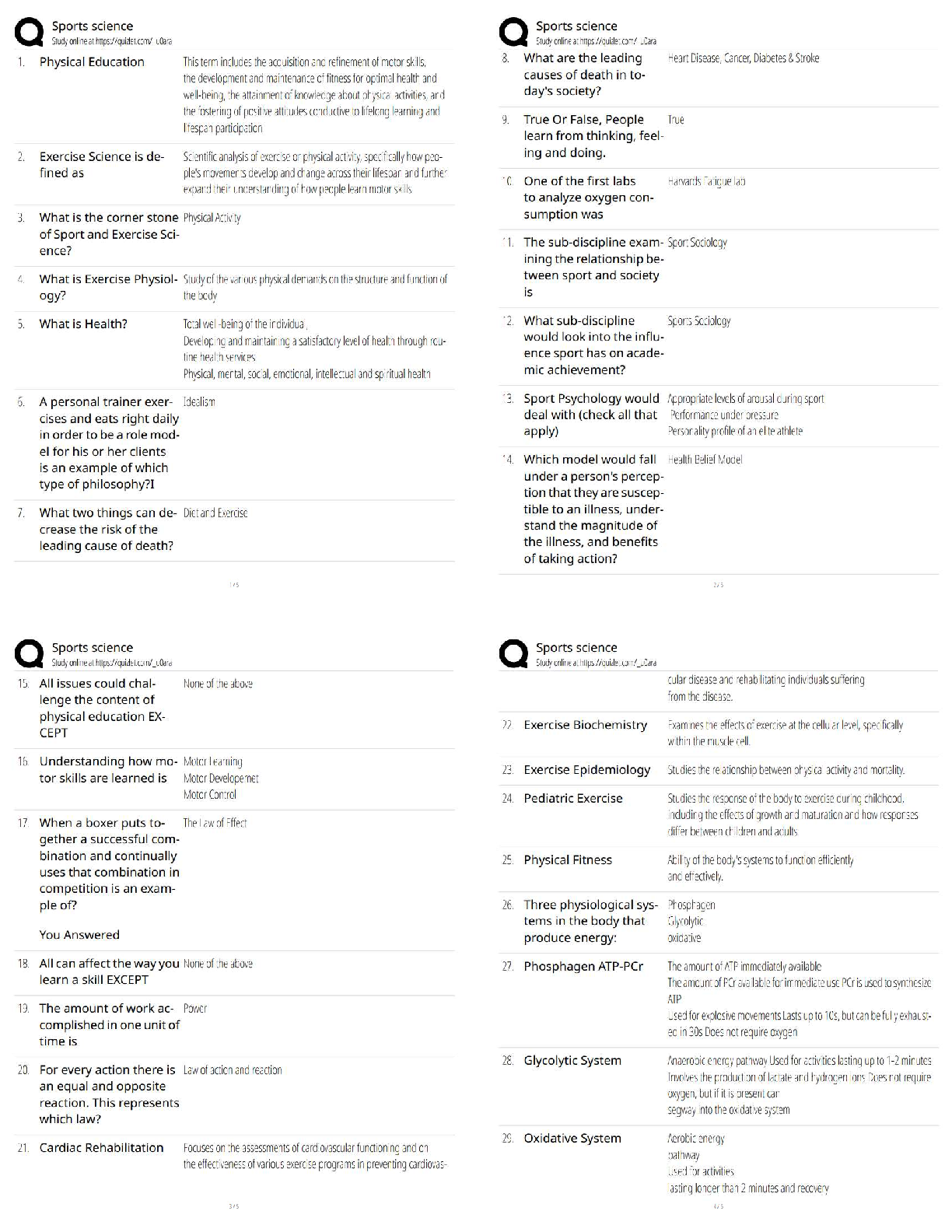
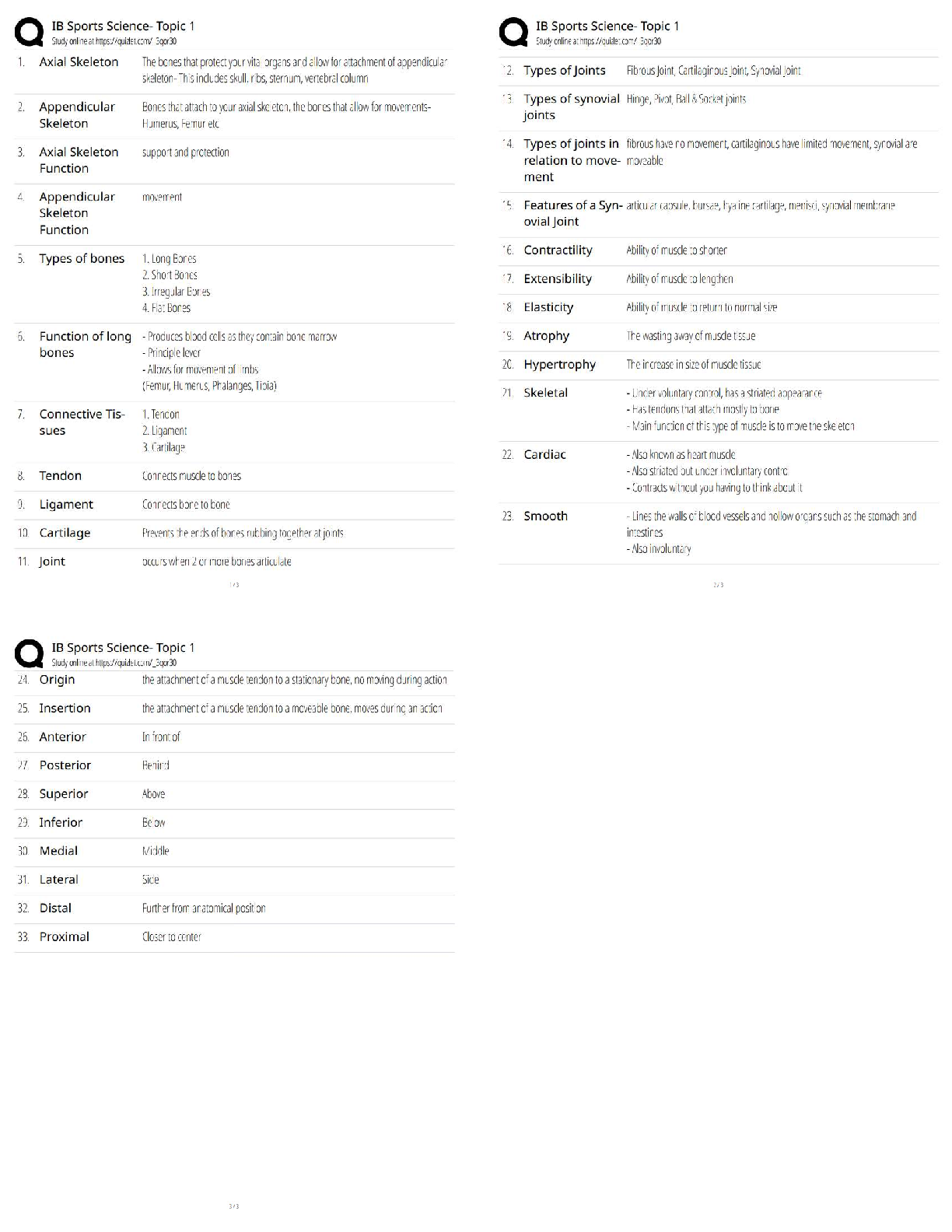
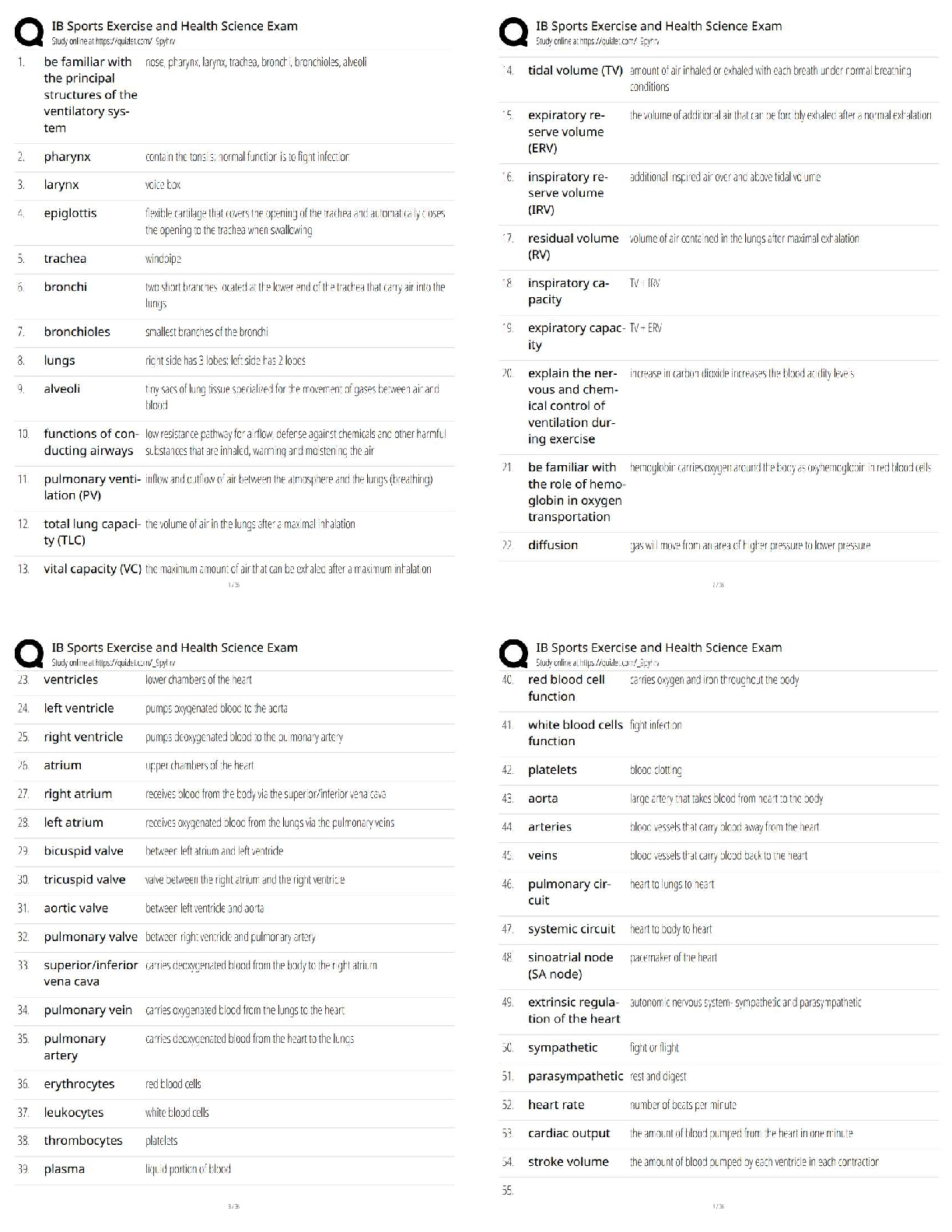
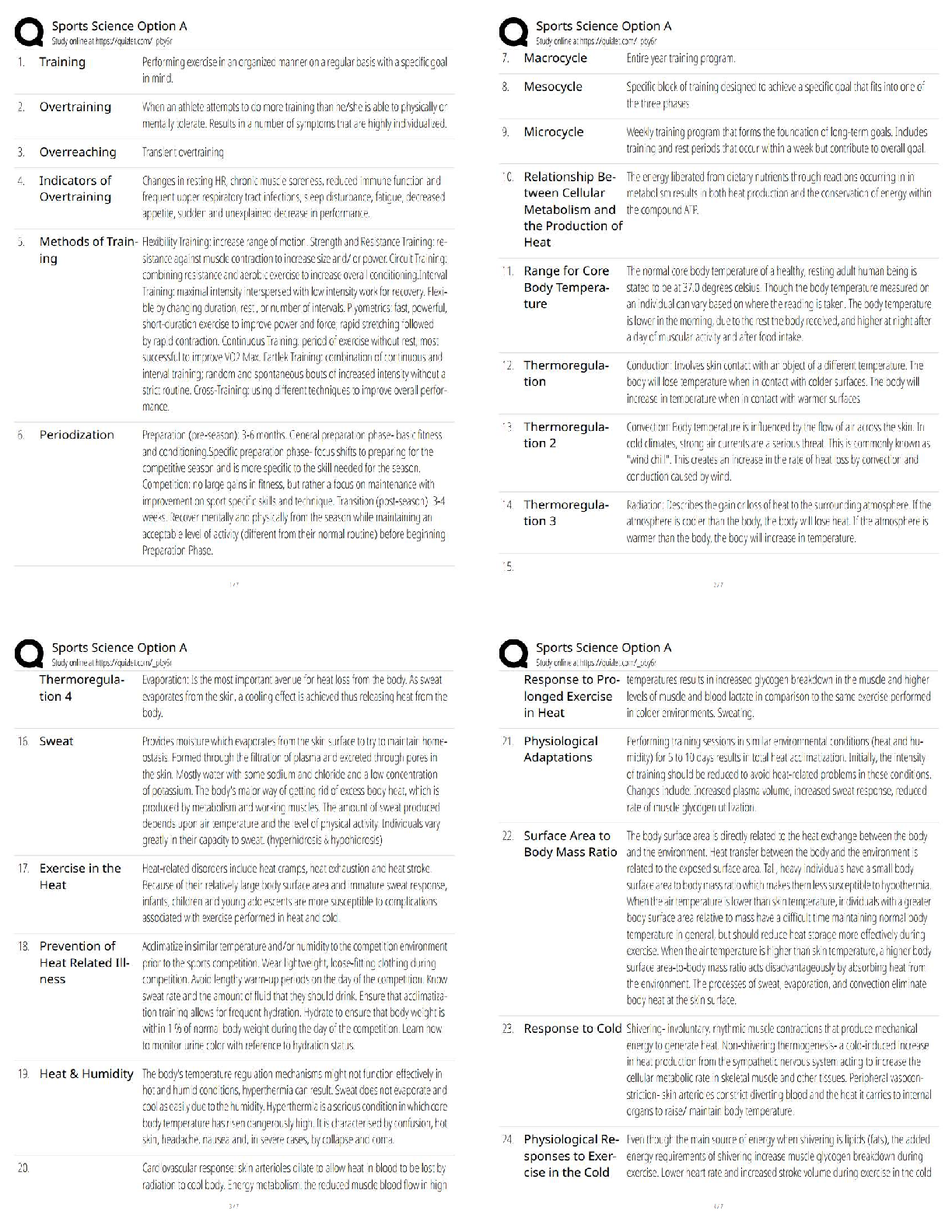
Cysa Review Activities Questions and Answers Already Passed Describe one advantage and one disadvantage of using the -T0 switch when performing an Nmap scan. ✔✔This sets an extremely high delay ... between probes, which may help to evade detection systems but will take a very long time to return results. What is the principal challenge in scanning UDP ports? ✔✔UDP does not send ACK messages so the scan must use timeouts to interpret the port state. This makes scanning a wide range of UDP ports a lengthy process. True or false? A port that is reported as "closed" by Nmap is likely to be one protected by a firewall. ✔✔False. A closed port responds to probes with an RST because there is no service available to process the request. This means that the port is accessible through the firewall. A port blocked by a firewall is in the "filtered" state. 4.What is the function of the -A switch in Nmap? ✔✔Performs service detection (verify that the packets delivered over a port correspond to the "well known" protocol associated with that port) and version detection (using the scripts marked "default"). How do you run a specific Nmap script or category of scripts? ✔✔Use the --script argument with the script name or path or category name. What is the advantage of the Nmap "grepable" output format? ✔✔grep is a Linux command for running a regular expression to search for a particular string. Nmap's grepable output is easier for this tool to parse. Despite operating a patch management program, your company has been exposed to several attacks over the last few months. You have drafted a policy to require a lessons- learned incident report be created to review the historical attacks and to make this analysis a requirement following future attacks. How can this type of control be classified? ✔✔It is implemented as an administrative control as it is procedural rather than technical in nature. Additionally, it is a managerial control rather than an operational control as it seeks oversight of day-to-day processes with a view to improving them. In terms of function, you can classify it as corrective, as it occurs after an attack has taken place. 2A bespoke application used by your company has been the target of malware. The developers have created signatures for the application's binaries, and these have been added to endpoint detection and response (EDR) scanning software running on each workstation. If a scan shows that a binary image no longer matches its signature, an administrative alert is generated. What type of security control is this? ✔✔This is a technical control as it is implemented in software. In functional terms, it acts as a detective control because it does not stop malware from replacing the original file image (preventative control) or restore the original file automatically (corrective control). Your company is interested in implementing routine backups of all customer databases. This will help uphold availability because you will be able to quickly and easily restore the backed-up copy, and it will also help uphold integrity in case someone tampers with the database. What controls can you implement to round out your risk mitigation strategy and uphold the components of the CIA triad? ✔✔You should consider the confidentiality component. The backups contain the same privileged information as the live copy and so must be protected by confidentiality controls. Access controls can be used to ensure that only authorized backup operators have access to the data. Encryption can be used as an additional layer of protection. Your chief information security officer (CISO) wants to develop a new collection and analysis platform that will enable the security team to extract actionable data from its assets. The CISO would like your input as far as which data sources to draw from as part of the new collection platform, worrying that collecting from too many sources, or not enough, could impede the company's ability to analyze information. Is this a valid concern, and how can it be addressed within an intelligence life-cycle model? ✔✔Yes, it is a valid concern. The requirements (or planning and direction) phase of the intelligence cycle can be used to evaluate data sources and develop goals and objectives for producing actionable intelligence to support use cases demanded by intelligence consumers. You can also mention that the feedback phase of the cycle provides the opportunity to review sources and determine whether they are delivering valuable intelligence. What are the characteristics to use to evaluate threat data and intelligence sources? ✔✔Firstly, you can distinguish sources as either proprietary/closed-source, public/open-source, or communitybased, such as an ISAC. Within those categories, data feeds can be assessed for timeliness, relevancy, and accuracy. It is also important for analyst opinions and threat data points to be tagged with a confidence level. What are the phases of the intelligence c [Show More]
Last updated: 3 years ago
Preview 1 out of 16 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
CySA Bundled Exams with complete solution;everything you need is here
CySA+ (CS0-002) Exam 2022 Questions and Answers CySA+ 2022 Questions and Answers with complete solution CySA+ Exam guide 2022 with complete solution CYSA+ Practice Exam 2 Latest 2022 with complete sol...
By Nutmegs 3 years ago
$20
14
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 02, 2022
Number of pages
16
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 02, 2022
Downloads
0
Views
123








.png)