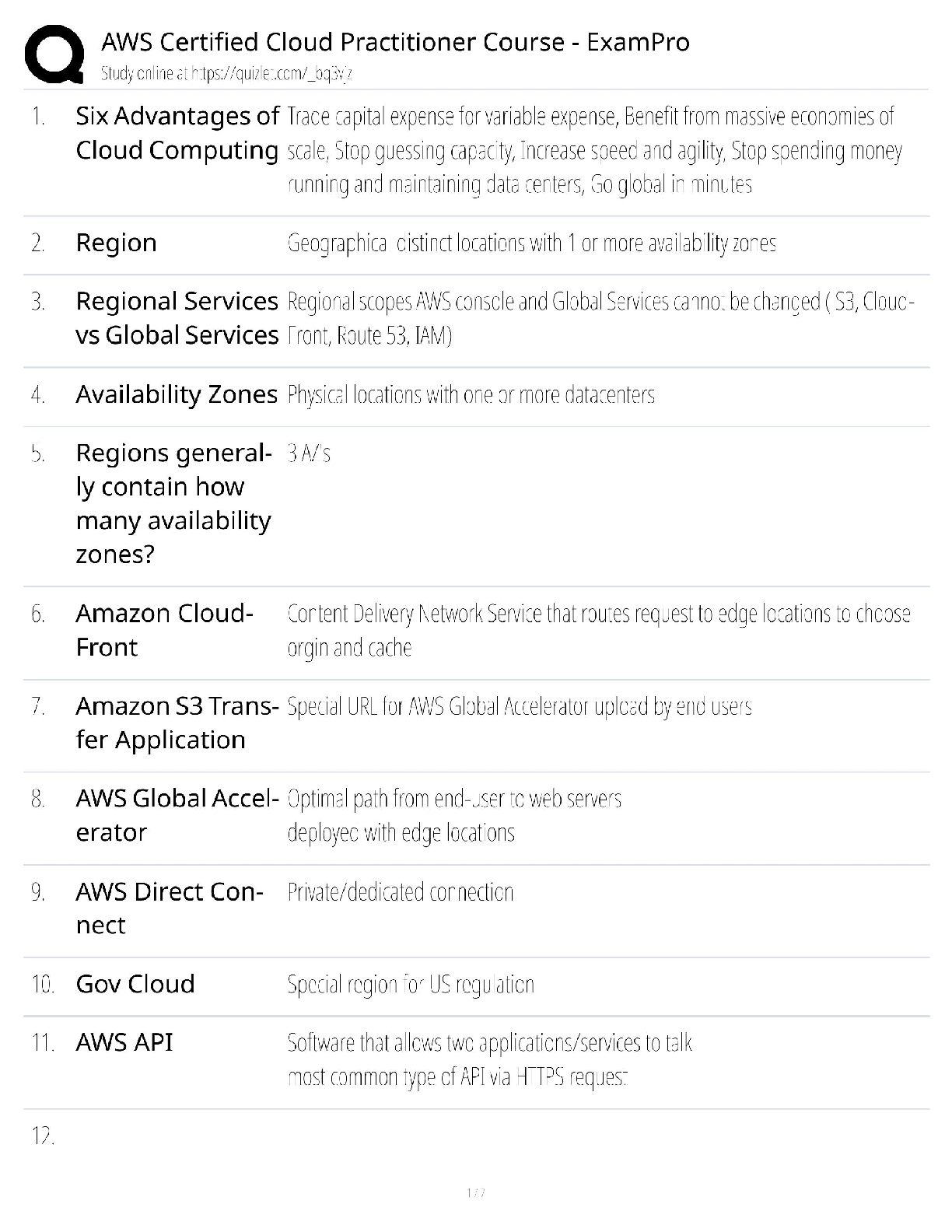
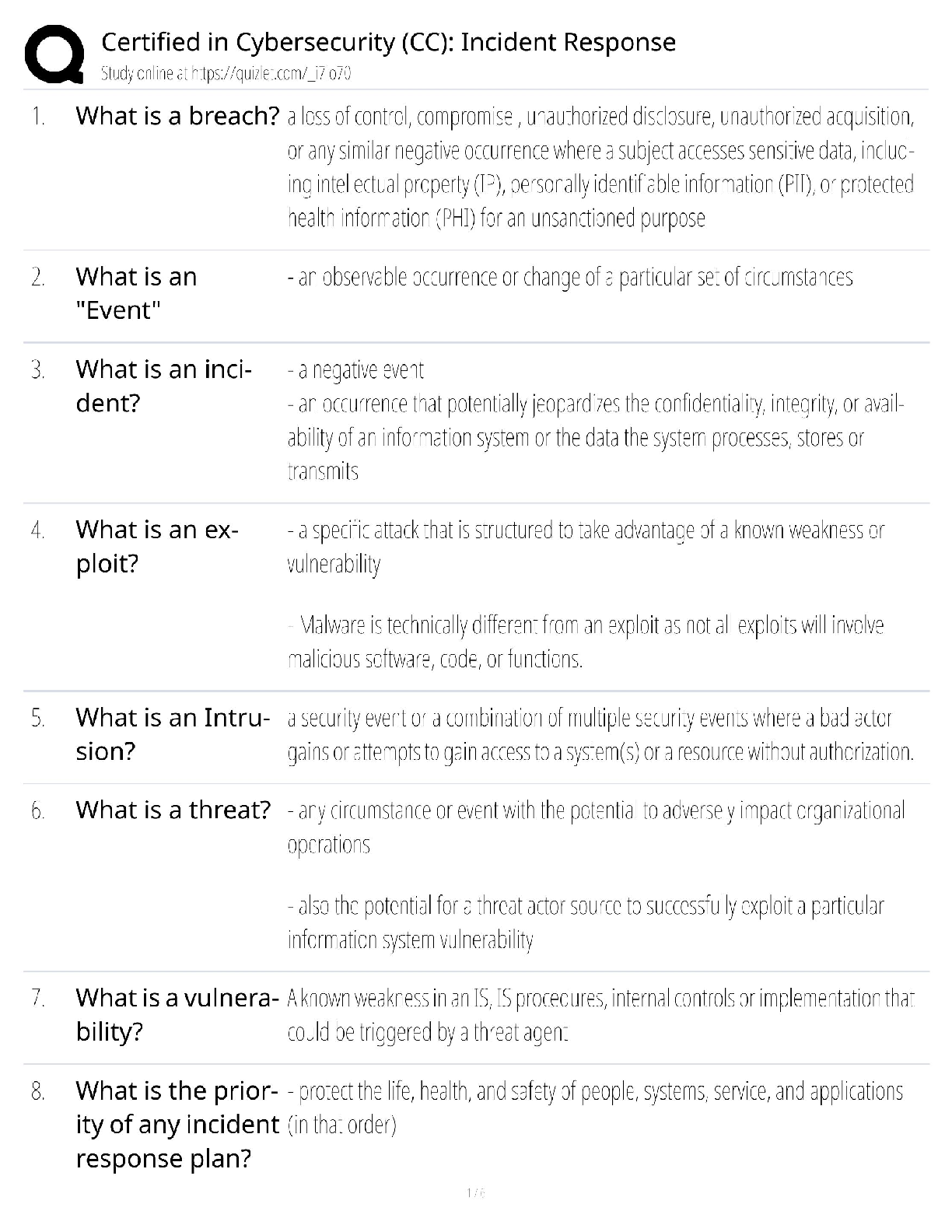
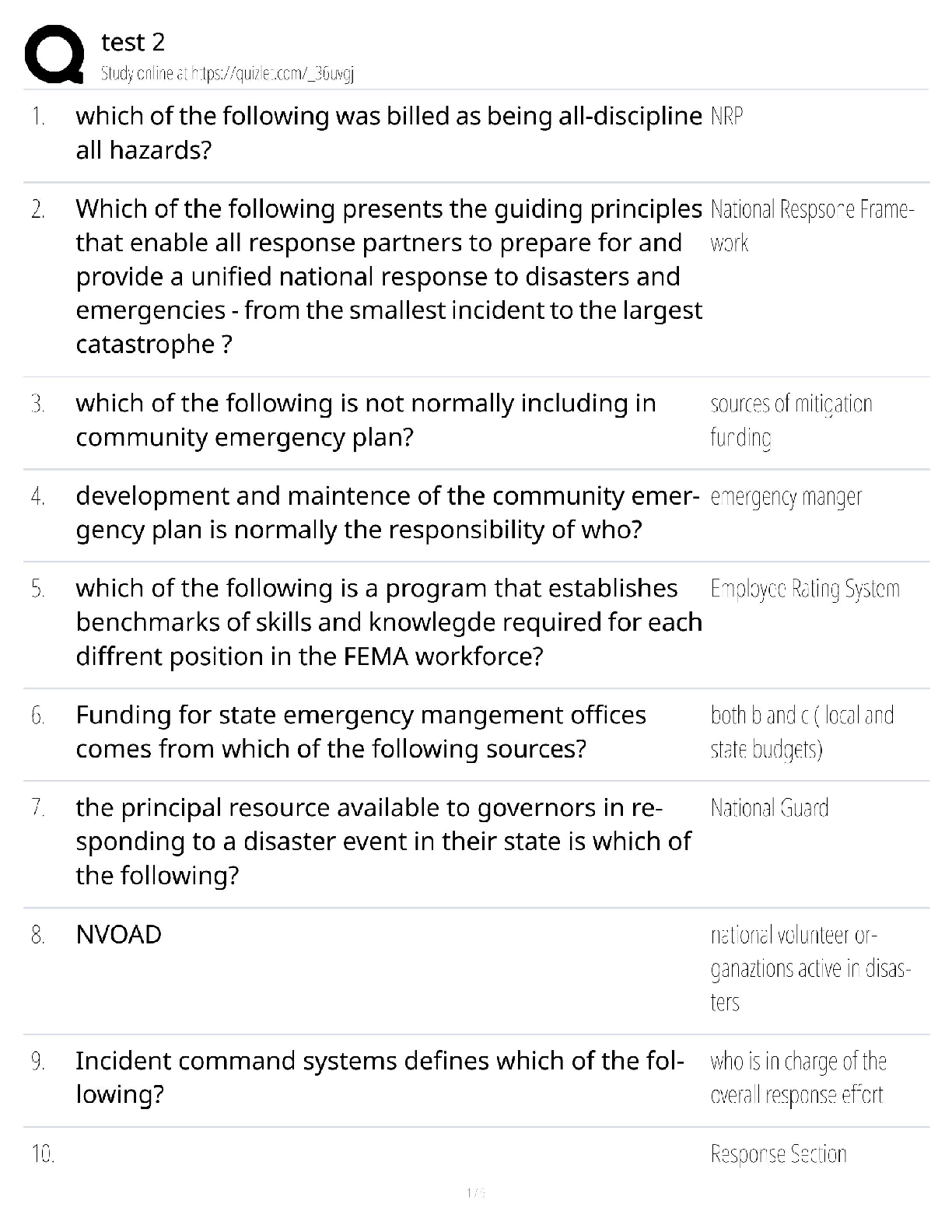
Information Technology > QUESTIONS & ANSWERS > CySA+ Exam guide Questions and Answers Rated A (All)
CySA+ Exam guide Questions and Answers Rated A
Document Content and Description Below
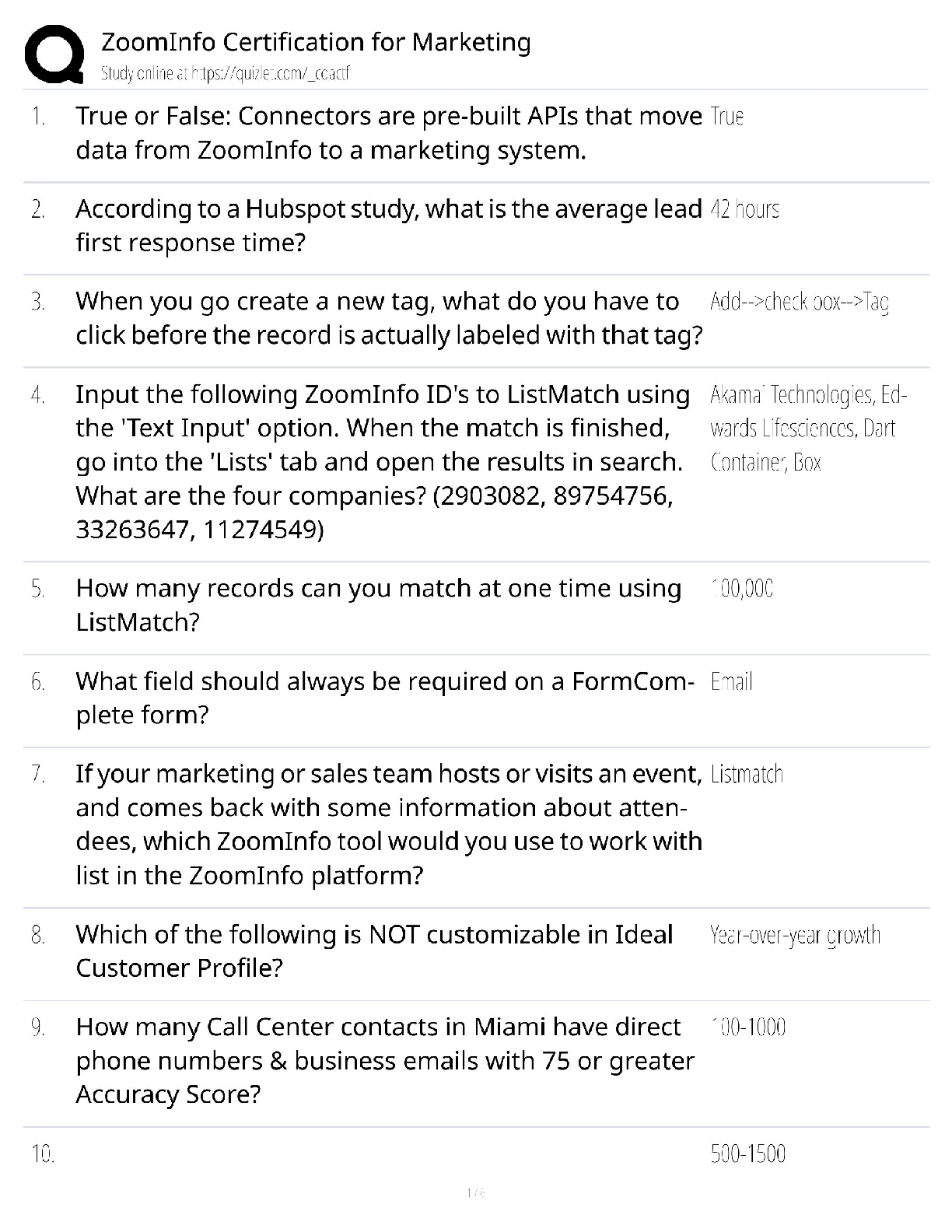
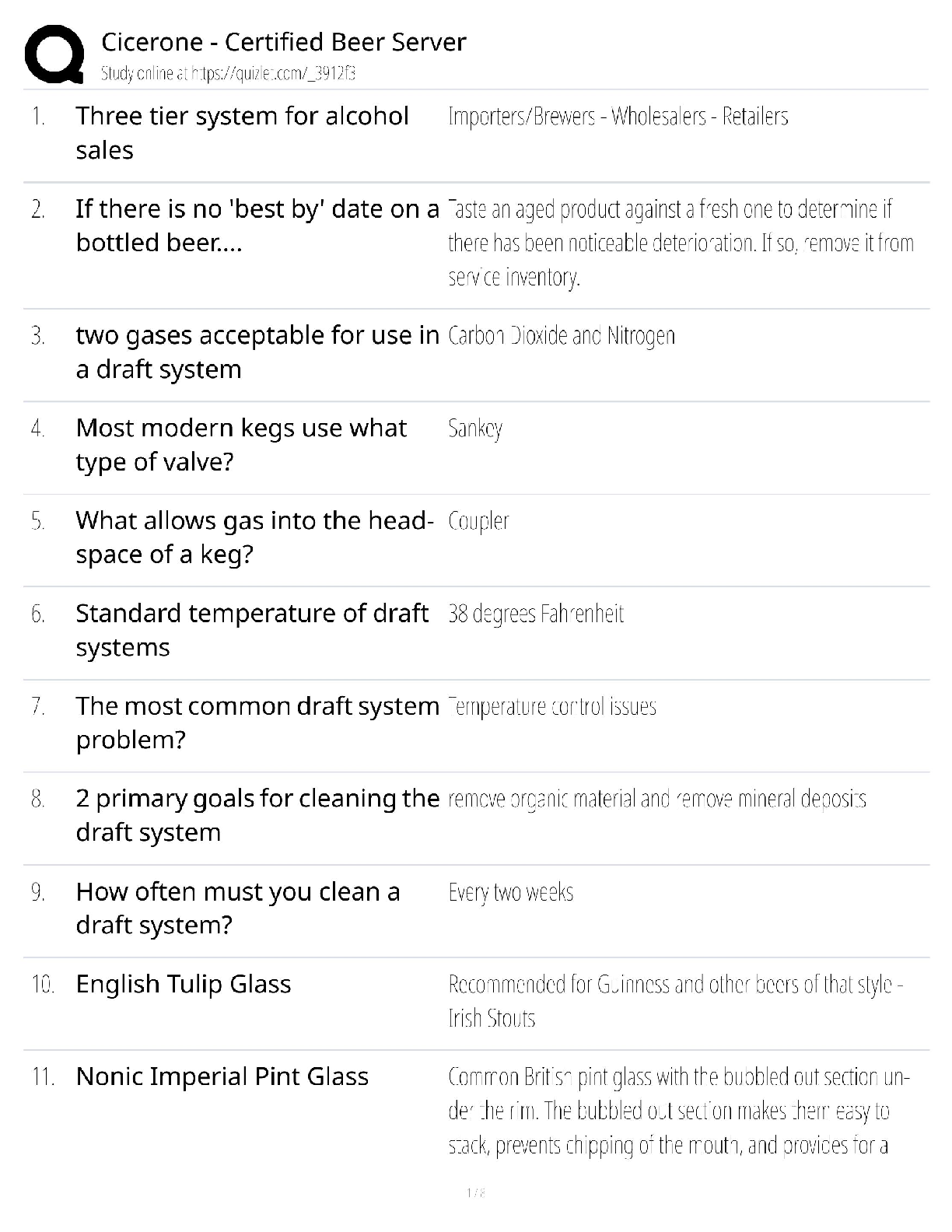
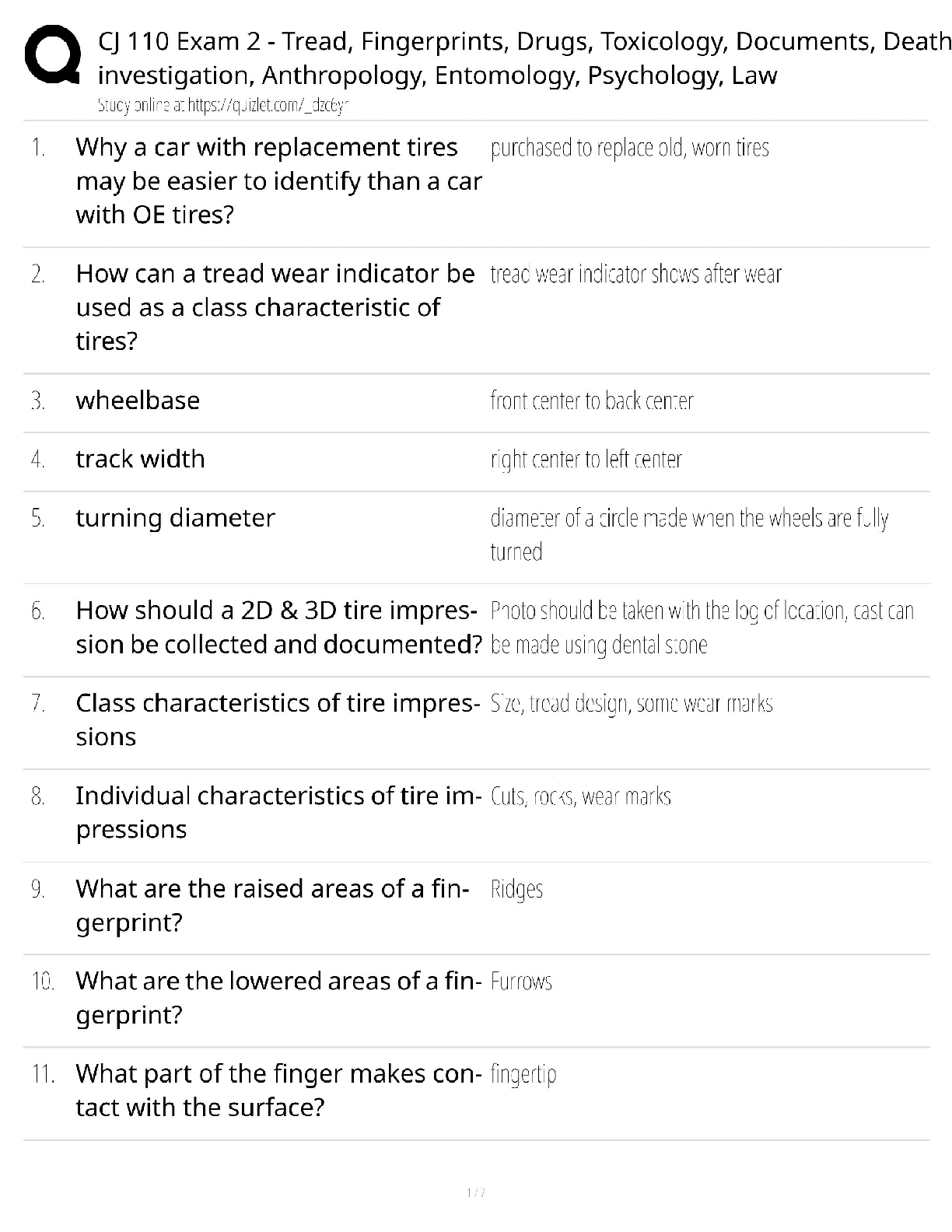
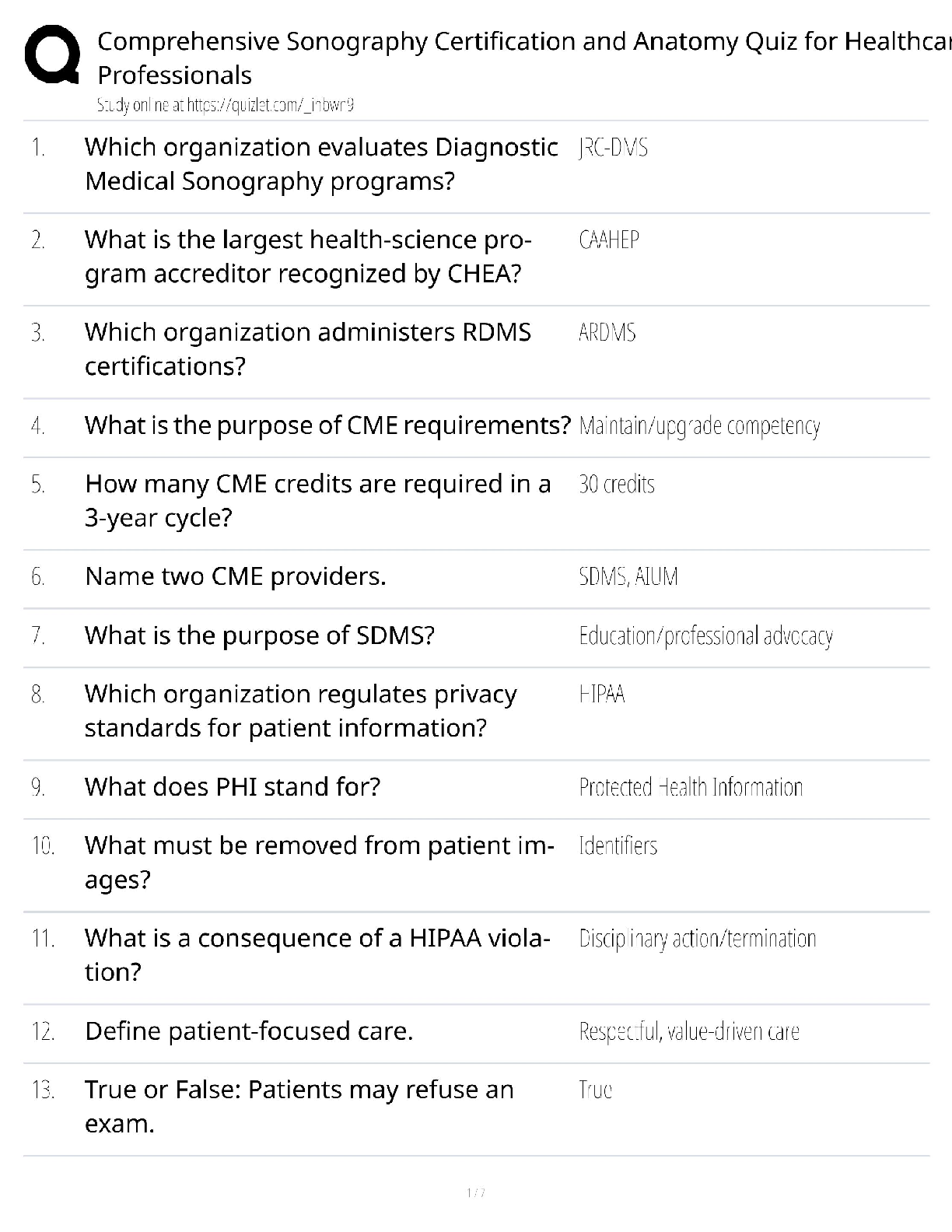
CySA+ Exam guide Questions and Answers Rated A DNS Sinkhole ✔✔Provide a response to a DNS query that does not resolve the IP address.. Instead targets the addresses for known malicious domains ... Role-Based access control (RBAC) ✔✔grants permissions based on a user's role or group. Reverse Engineering ✔✔the process of decontructing something in order to discover its features and constituents Banner grabbing ✔✔used to gain information about a computer system on a network and the services running on its open ports. Administrators can use this to take inventory of the systems and services on their network. Cross-site scripting XSS ✔✔a vulnerability in a web application that allows malicious users to execute arbitrary client side scripts. Forensic Acquisition ✔✔The process of extracting the digital contents from seized evidence so that they may be analyzed Fuzzing ✔✔techniqued used to discover flaws and vulnerabilities in software by sending large amounts of malformed, unexpected, or random data to the target programs in order to trigger failures Netstat ✔✔command-line interface tool that provides information on the status of network connections and listening sockets Input validation ✔✔an approach to protecting systems from abnormal user input by testing the data provided against appropriate values. (cha p 14) Interception Proxy ✔✔is a software tool that is inserted between two endpoints usually on the same network. to monitor traffic and help with security testing. SQL injection ✔✔A code injection technique that exploits security vulnerabilities in the DB layer of an application. Application Programing Interface ✔✔a set of subroutine definitions, protocols, and tools for building software. In general terms, it is a set of clearly defined methods of communication between various components. types of NAC policy? ✔✔1. location based 2 time based 3 Role Based 4 rule based a padded cell ✔✔performs intrusion isolation -after detection, intruder is automatically transferred here, which resembles a real environment but is fake and attacker cannot perform any dangerous activities -admin's can gather evidence here A system that waits for an IDS to detect an attacker and then transfers the attacker to a special host where he or she cannot do any damage to the production environment. firewalking ✔✔The concept of walking a firewall ACL or ruleset to determine what it filters and how. Armitage ✔✔gives you the users interface [Show More]
Last updated: 3 years ago
Preview 1 out of 14 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
CySA Bundled Exams with complete solution;everything you need is here
CySA+ (CS0-002) Exam 2022 Questions and Answers CySA+ 2022 Questions and Answers with complete solution CySA+ Exam guide 2022 with complete solution CYSA+ Practice Exam 2 Latest 2022 with complete sol...
By Nutmegs 3 years ago
$20
14
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 02, 2022
Number of pages
14
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 02, 2022
Downloads
0
Views
146








.png)