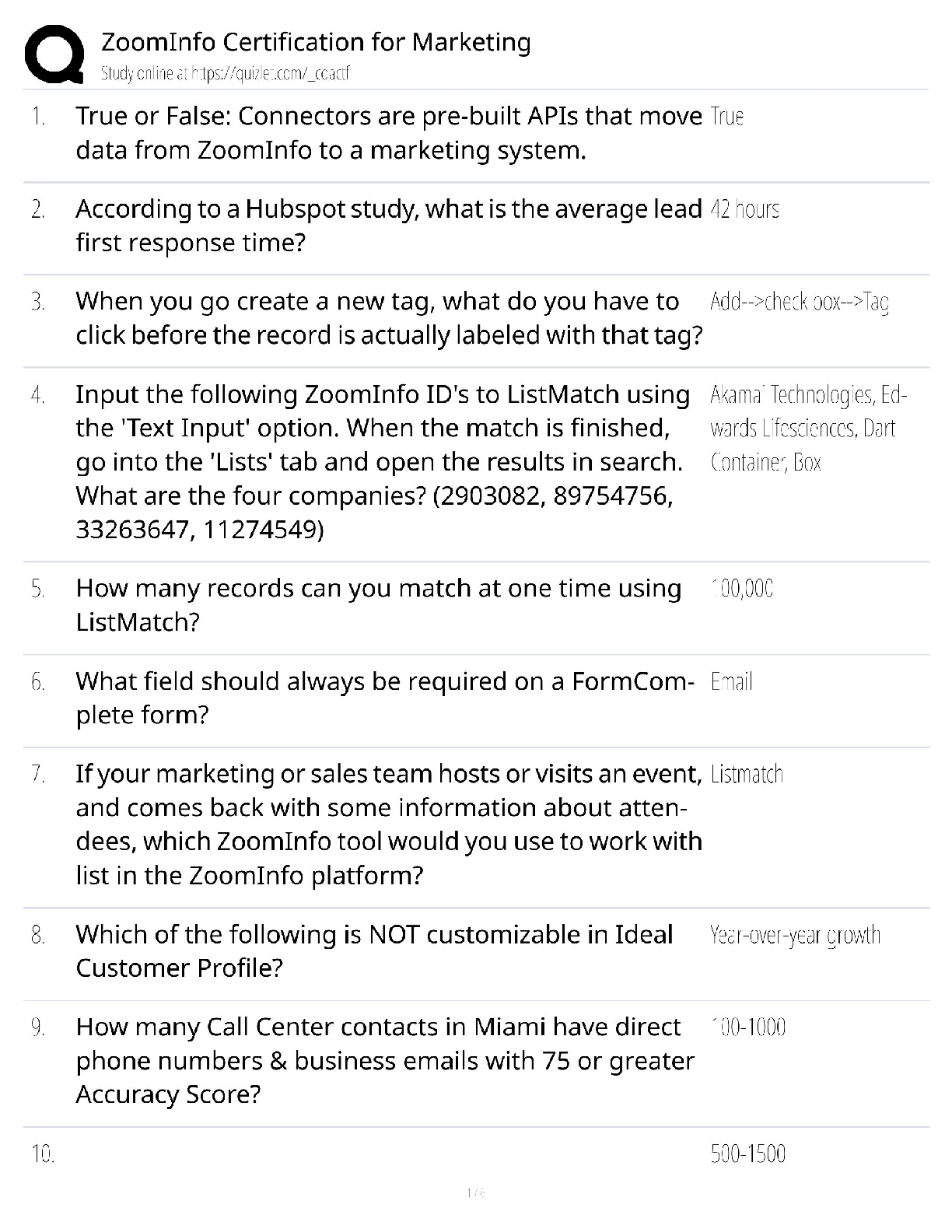
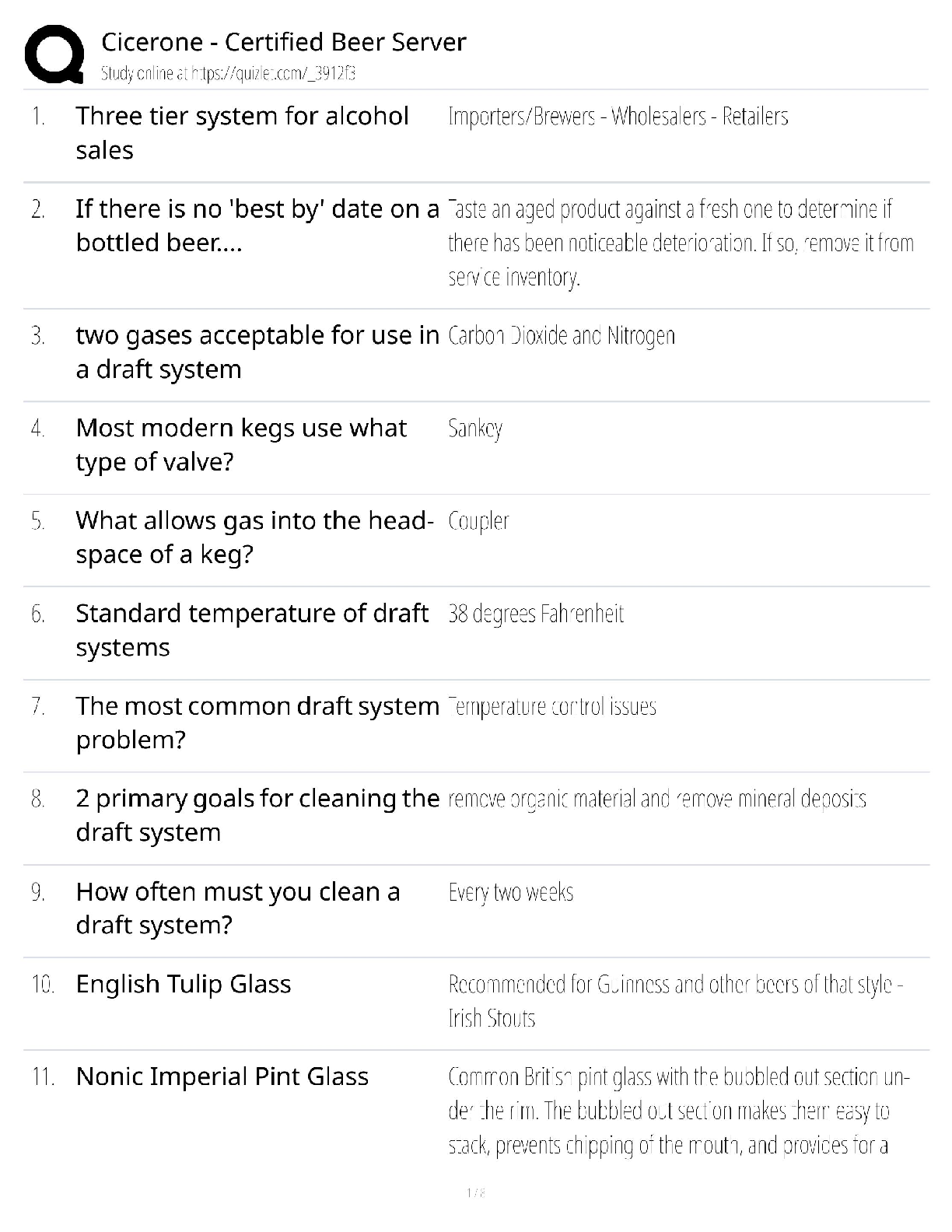
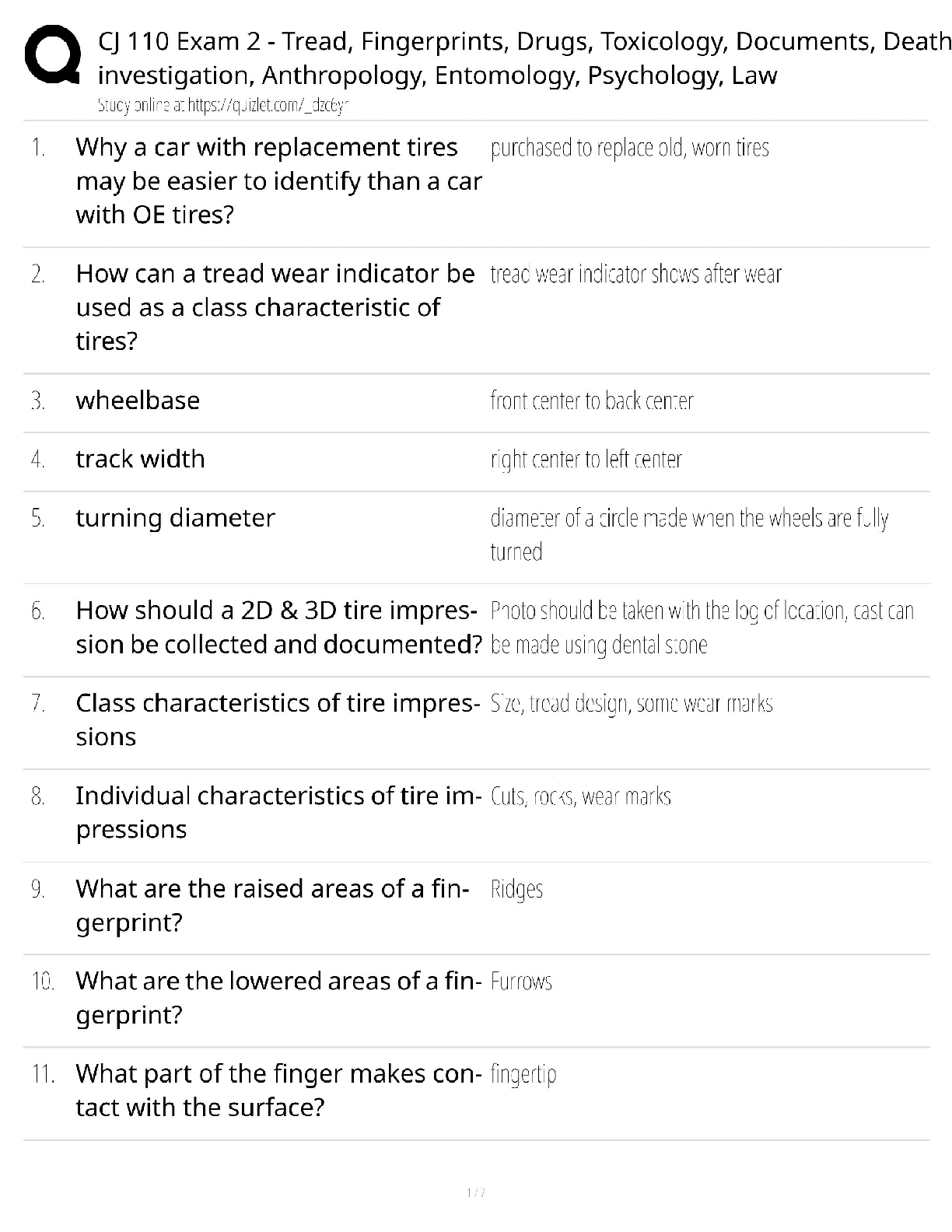
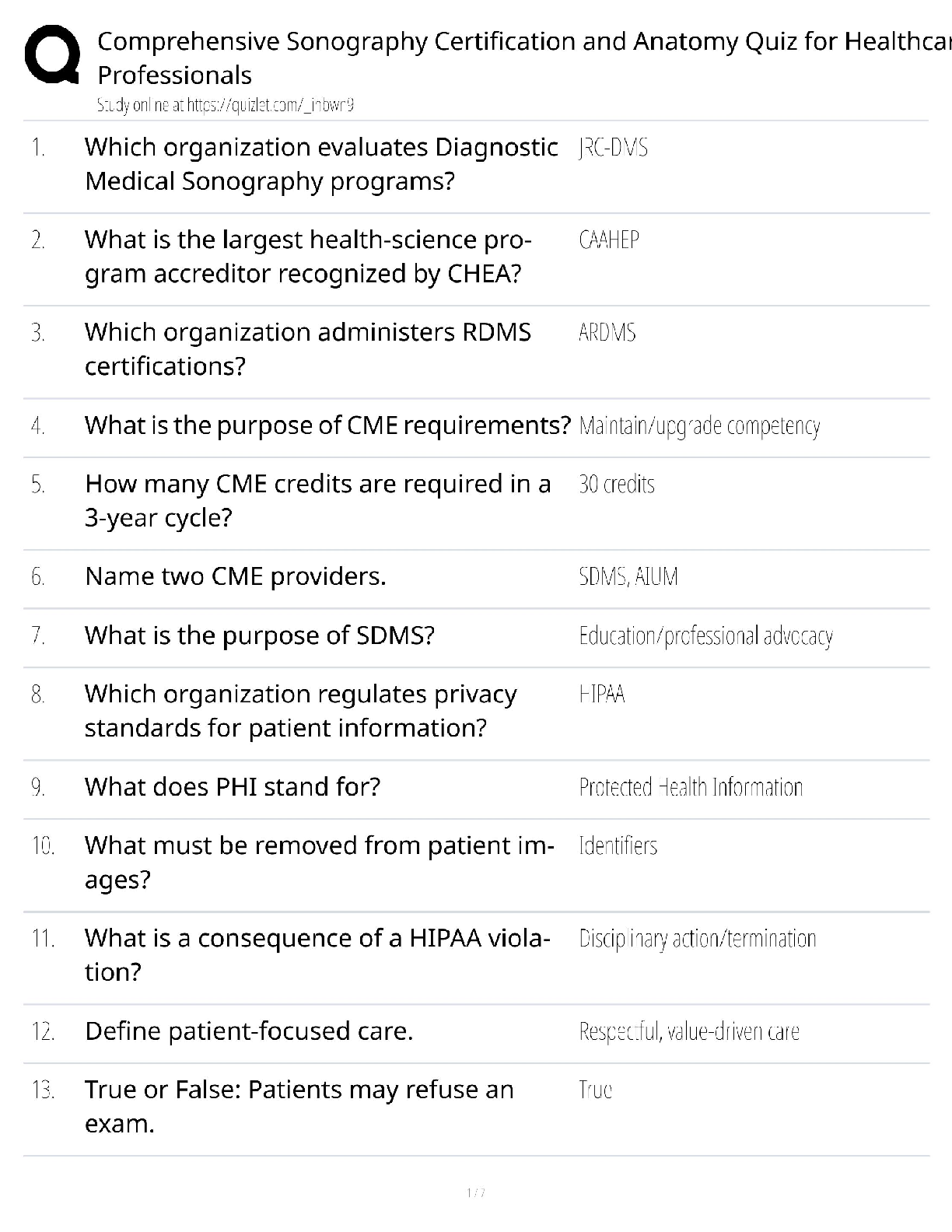
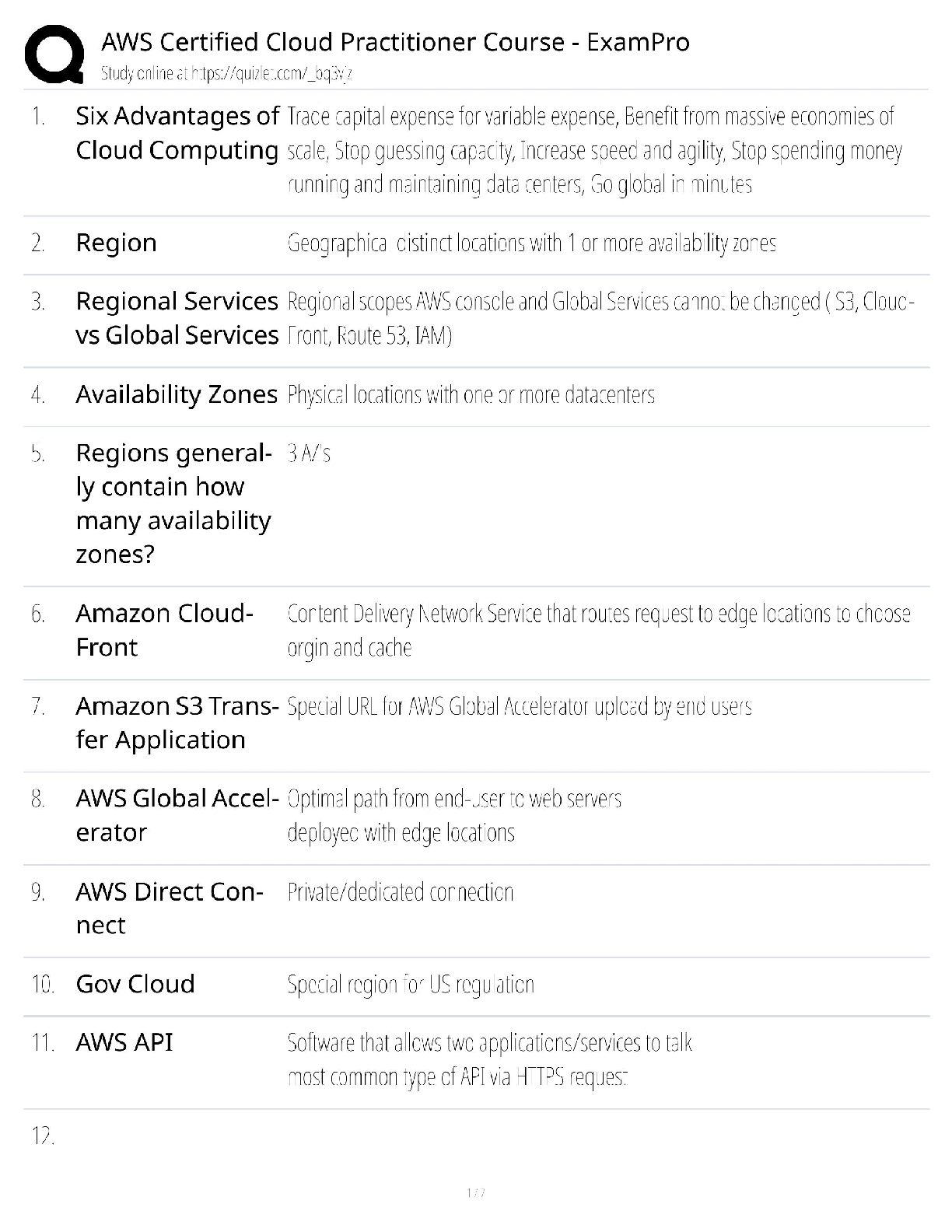
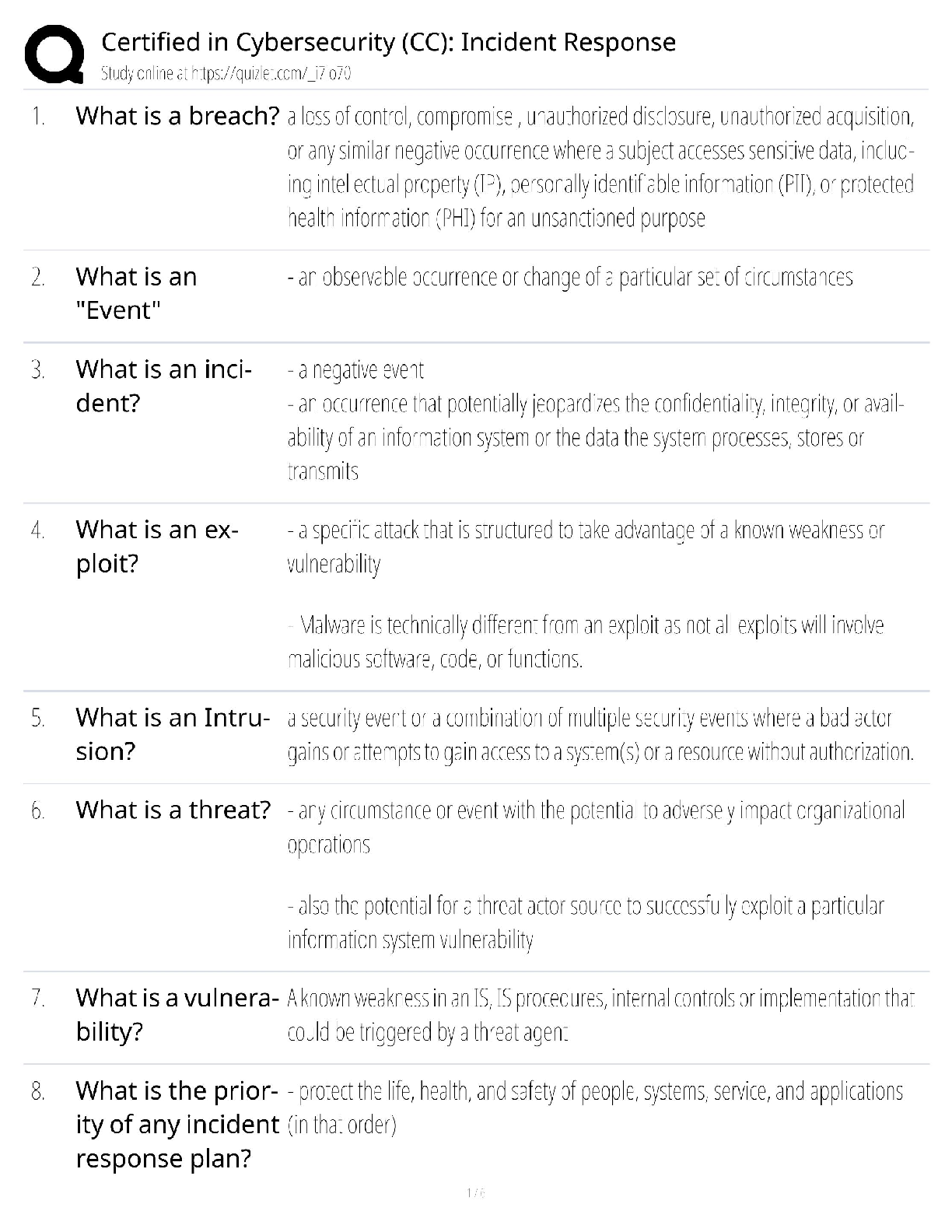
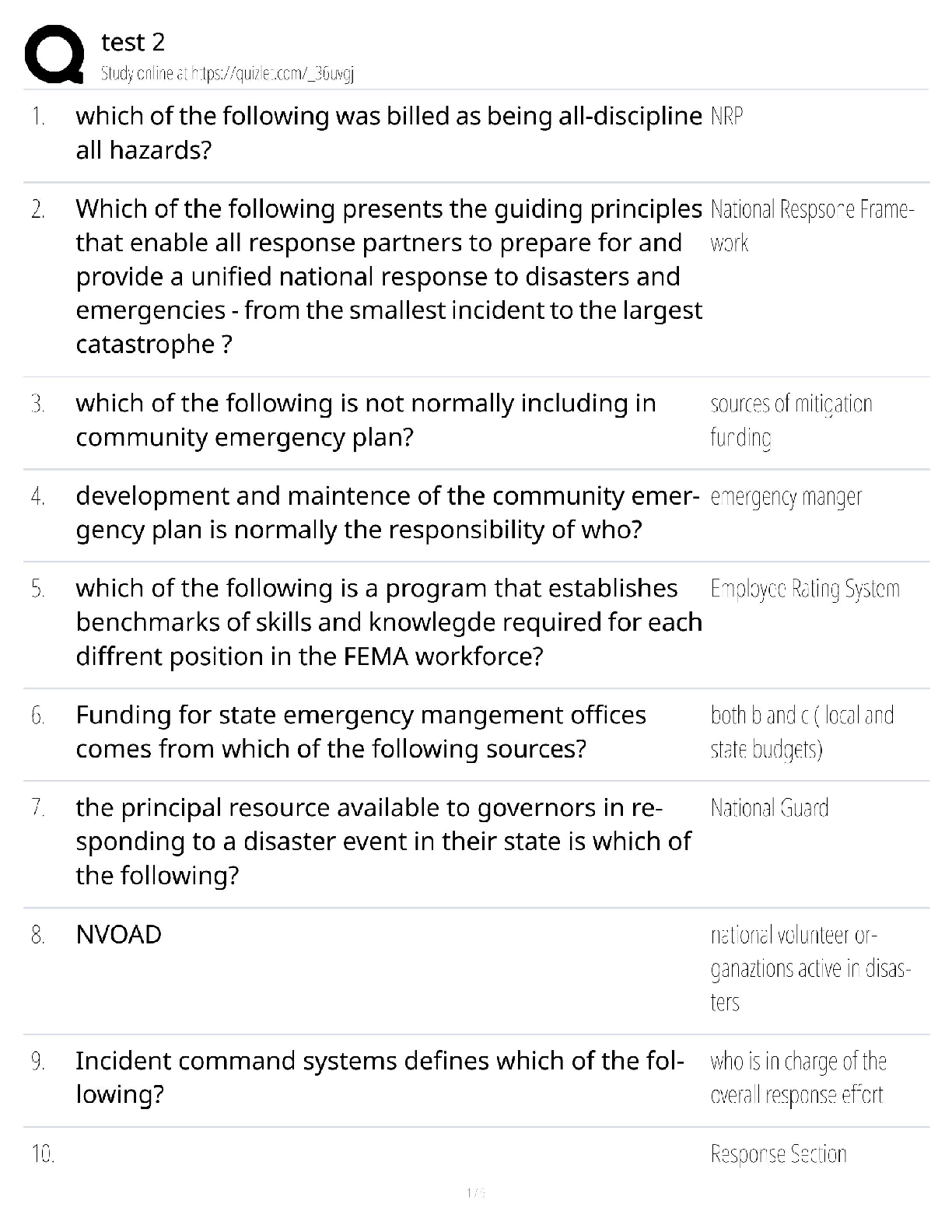
Information Technology > QUESTIONS & ANSWERS > CompTIA CySA+ CS0-002 Practice Questions and Answers with Complete Solutions (All)
CompTIA CySA+ CS0-002 Practice Questions and Answers with Complete Solutions
Document Content and Description Below
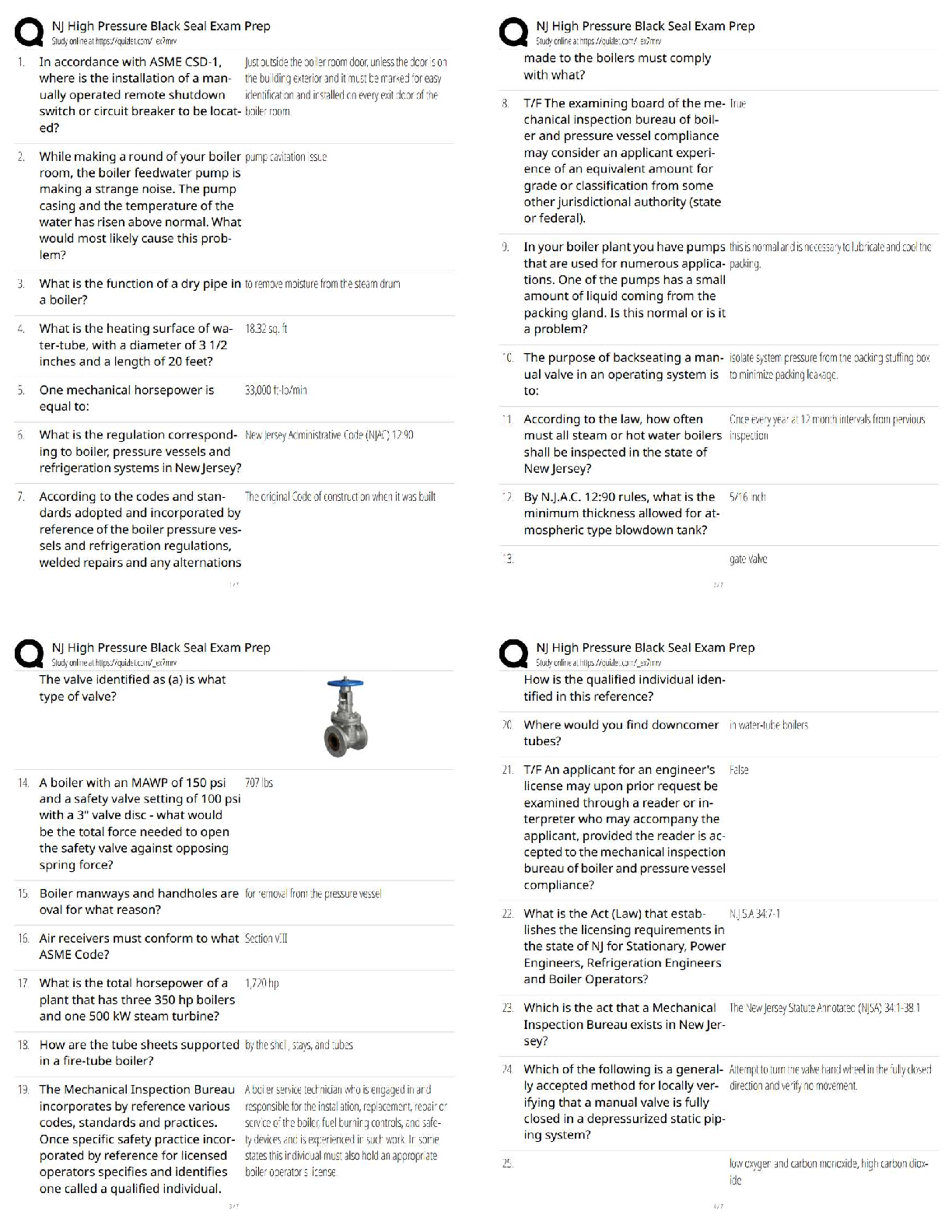
CompTIA CySA+ CS0-002 Practice Questions and Answers with Complete Solutions A cybersecurity analyst receives a phone call from an unknown person with the number blocked on the caller ID. After st ... arting conversation, the caller begins to request sensitive information. Which of the following techniques is being applied? A. Social engineering B. Phishing C. Impersonation D. War dialing ✔✔A Which of the following is the main benefit of sharing incident details with partner organizations or external trusted parties during the incident response process? A. It facilitates releasing incident results, findings and resolution to the media and all appropriate government agencies B. It shortens the incident life cycle by allowing others to document incident details and prepare reports. C. It enhances the response process, as others may be able to recognize the observed behavior and provide valuable insight. D. It allows the security analyst to defer incident-handling activities until all parties agree on how to proceed with analysis. ✔✔C The security analyst determined that an email containing a malicious attachment was sent to several employees within the company, and it was not stopped by any of the email filtering devices. An incident was declared. During the investigation, it was determined that most users deleted the email, but one specific user executed the attachment. Based on the details gathered, which of the following actions should the security analyst perform NEXT? A. Obtain a copy of the email with the malicious attachment. Execute the file on another user's machine and observe the behavior. Document all findings. B. Acquire a full backup of the affected machine. Reimage the machine and then restore from the full backup. C. Take the affected machine off the network. Review local event logs looking for activity and processes related to unknown or unauthorized software. D. Take possession of the machine. Apply the latest OS updates and firmware. Discuss the problem with the user and return the machine. ✔✔C Which of the following tools should a cybersecurity analyst use to verify the integrity of a forensic image before and after an investigation? A. strings B. sha1sum C. file D. dd E. gzip ✔✔B Given the following logs: Aug 18 11:00:57 comptia sshd[5657]: Failed password for root from 10.10.10.192 port 38980 ssh2 Aug 18 23:08:26 comptia sshd[5768]: Failed password for root from 18.70.0.160 port 38156 ssh2 Aug 18 23:08:30 comptia sshd[5770]: Failed password for admin from 18.70.0.160 port 38556 ssh2 Aug 18 23:08:34 comptia sshd[5772]: Failed password for invalid user asterisk from 18.70.0.160 port 38864 ssh2 Aug 18 23:08:38 comptia sshd[5774]: Failed password for invalid user sjobeck from 10.10.1.16 port 39157 ssh2 Aug 18 23:08:42 comptia sshd[5776]: Failed password for root from 18.70.0.160 port 39467 ssh2 Which of the following can be suspected? [Show More]
Last updated: 3 years ago
Preview 1 out of 25 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
CySA Bundled Exams with complete solution;everything you need is here
CySA+ (CS0-002) Exam 2022 Questions and Answers CySA+ 2022 Questions and Answers with complete solution CySA+ Exam guide 2022 with complete solution CYSA+ Practice Exam 2 Latest 2022 with complete sol...
By Nutmegs 3 years ago
$20
14
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 02, 2022
Number of pages
25
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 02, 2022
Downloads
0
Views
150








.png)