Information Technology > QUESTIONS & ANSWERS > CySA+ Questions and Answers Already Passed (All)
CySA+ Questions and Answers Already Passed
Document Content and Description Below
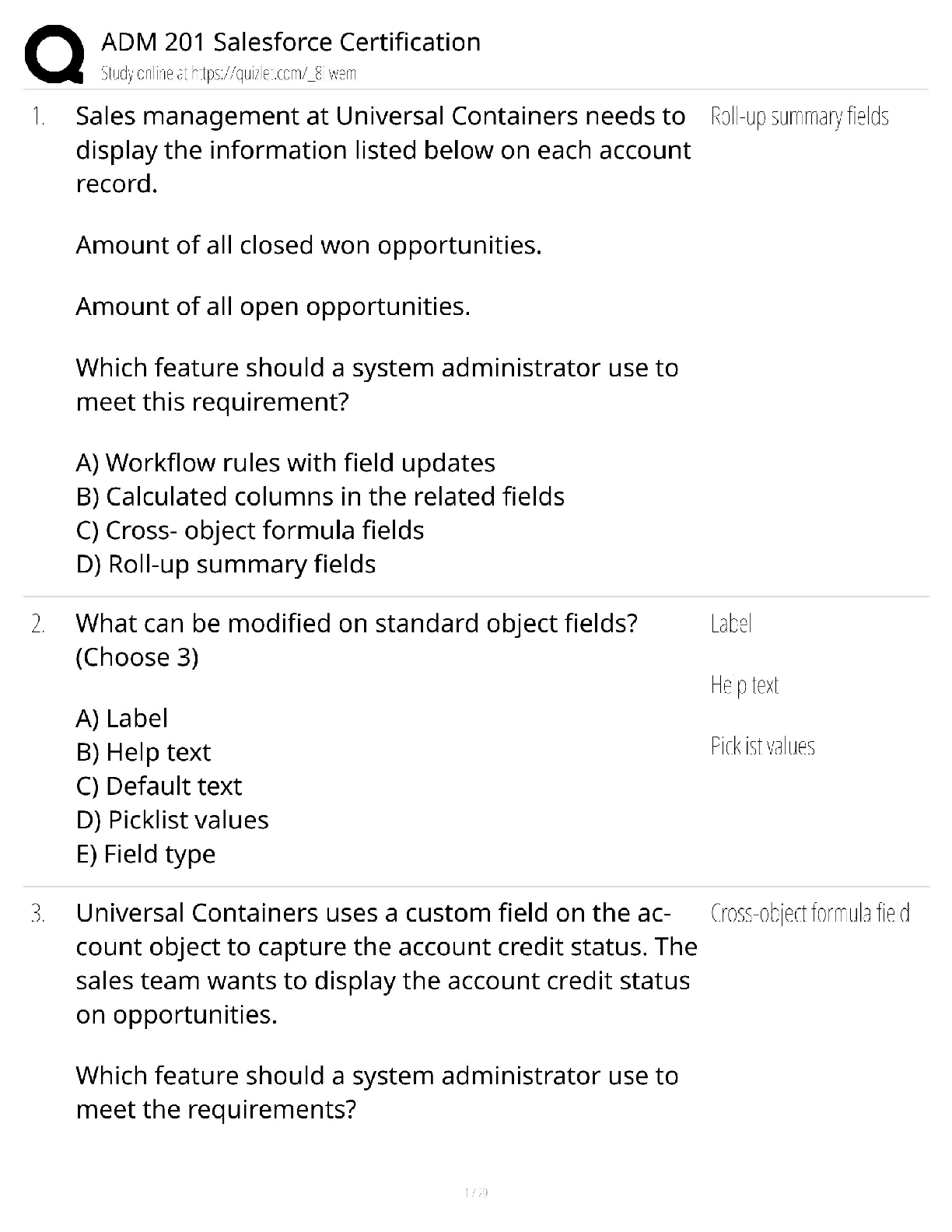
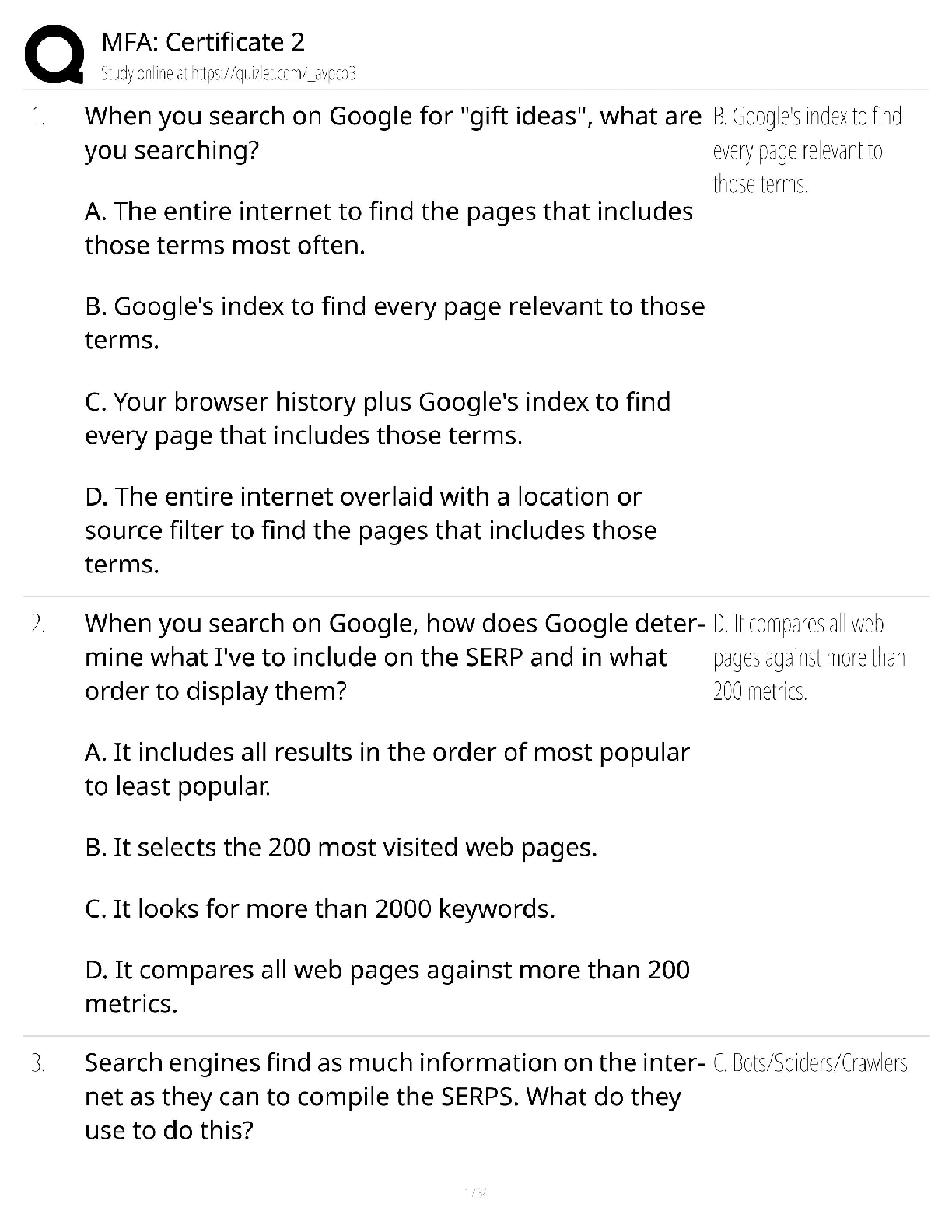
CySA+ Questions and Answers Already Passed Confidentiality, integrity, and availability ✔✔What are the three key objectives of information security? Threats and vulnerabilities. ✔✔Risk exi ... sts at the intersection of _______ and _________. Network access control ✔✔What type of system controls access to a network based on criteria such as time of day, location, device type, and system health? The Internet, an internal network, and a DMZ ✔✔What are the three networks typically connected to a triple-homed firewall? Packet filters Stateful inspection firewalls Next-generation firewalls Web application firewalls. ✔✔What are the four types of firewalls? Group Policy Objects (GPOs) ✔✔______ may be used to apply settings to many different Windows systems at the same time. Planning, Discovery, Attack, and Reporting ✔✔Four phases of penetration testing Port scanner ✔✔What type of software can you use to enumerate the services that are accepting network connections on a remote system without probing that system for vulnerabilities? nmap ✔✔What is the most commonly used port scanner? Traceroute or tracert, depending on the operating system ✔✔What tool can be used to determine the path between two systems over the Internet? Anomaly analysis ✔✔What type of data analysis looks for differences from expected behaviors? Trend analysis ✔✔What type of data analysis predicts threats based on existing data? Credentialed scan ✔✔What type of vulnerability scan leverages read-only access to the scan target? Risk appetite ✔✔What term is used to describe an organization's willingness to tolerate risk? Read-only account ✔✔What type of account should be used to perform credentialed vulnerability scans? Vulnerability scanning ✔✔What function is performed by QualysGuard, Nessus, Nexpose, and OpenVAS? Web application scanning ✔✔What is the purpose of Nikto and Acunetix? Criticality Difficulty Severity Exposure ✔✔Remediation Priority CVSS ✔✔What industry-standard system is used to assess the severity of security vulnerabilities? False positive ✔✔What is the term used to describe when a scanner reports a vulnerability that does not really exist? [Show More]
Last updated: 3 years ago
Preview 1 out of 11 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
CySA Bundled Exams with complete solution;everything you need is here
CySA+ (CS0-002) Exam 2022 Questions and Answers CySA+ 2022 Questions and Answers with complete solution CySA+ Exam guide 2022 with complete solution CYSA+ Practice Exam 2 Latest 2022 with complete sol...
By Nutmegs 3 years ago
$20
14
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 02, 2022
Number of pages
11
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 02, 2022
Downloads
0
Views
140








.png)