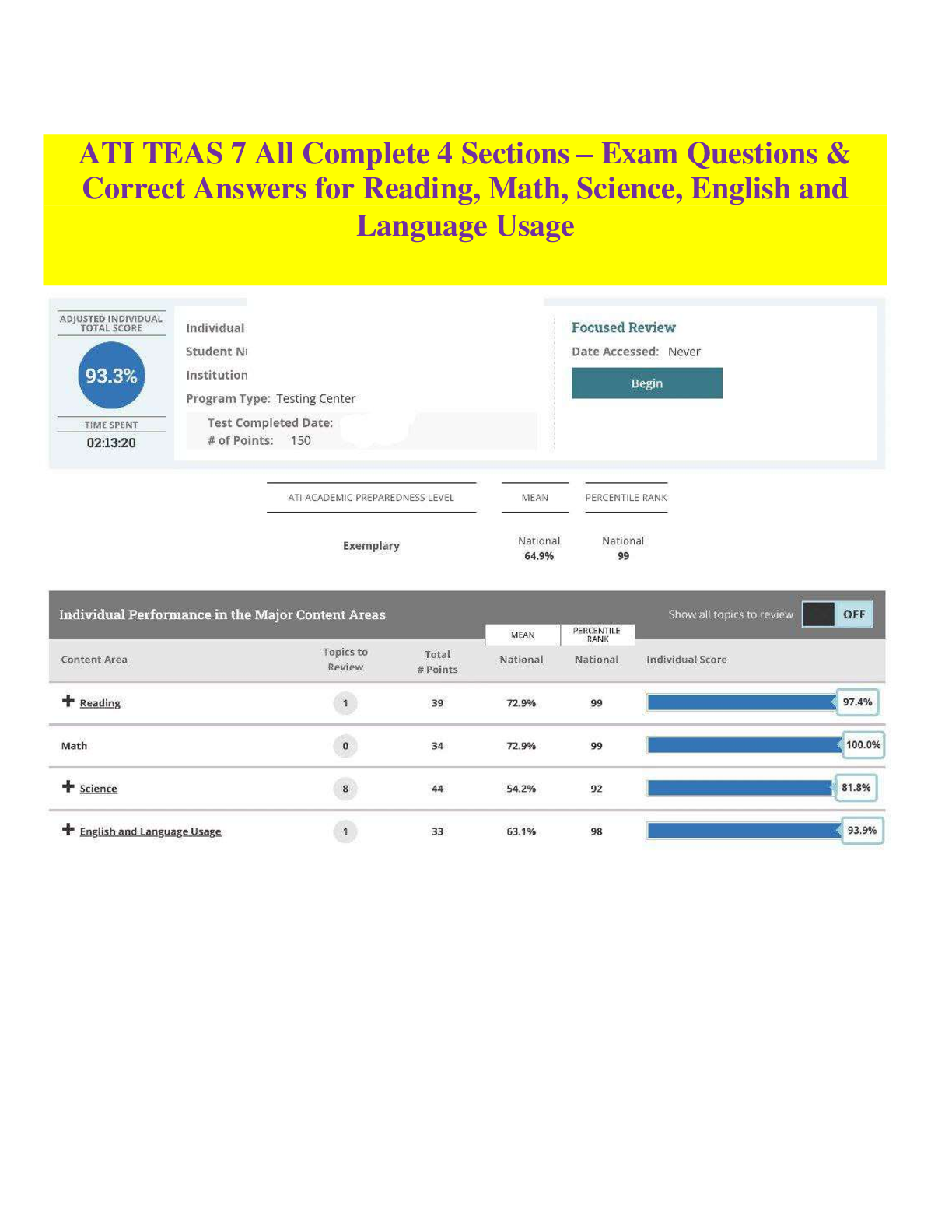
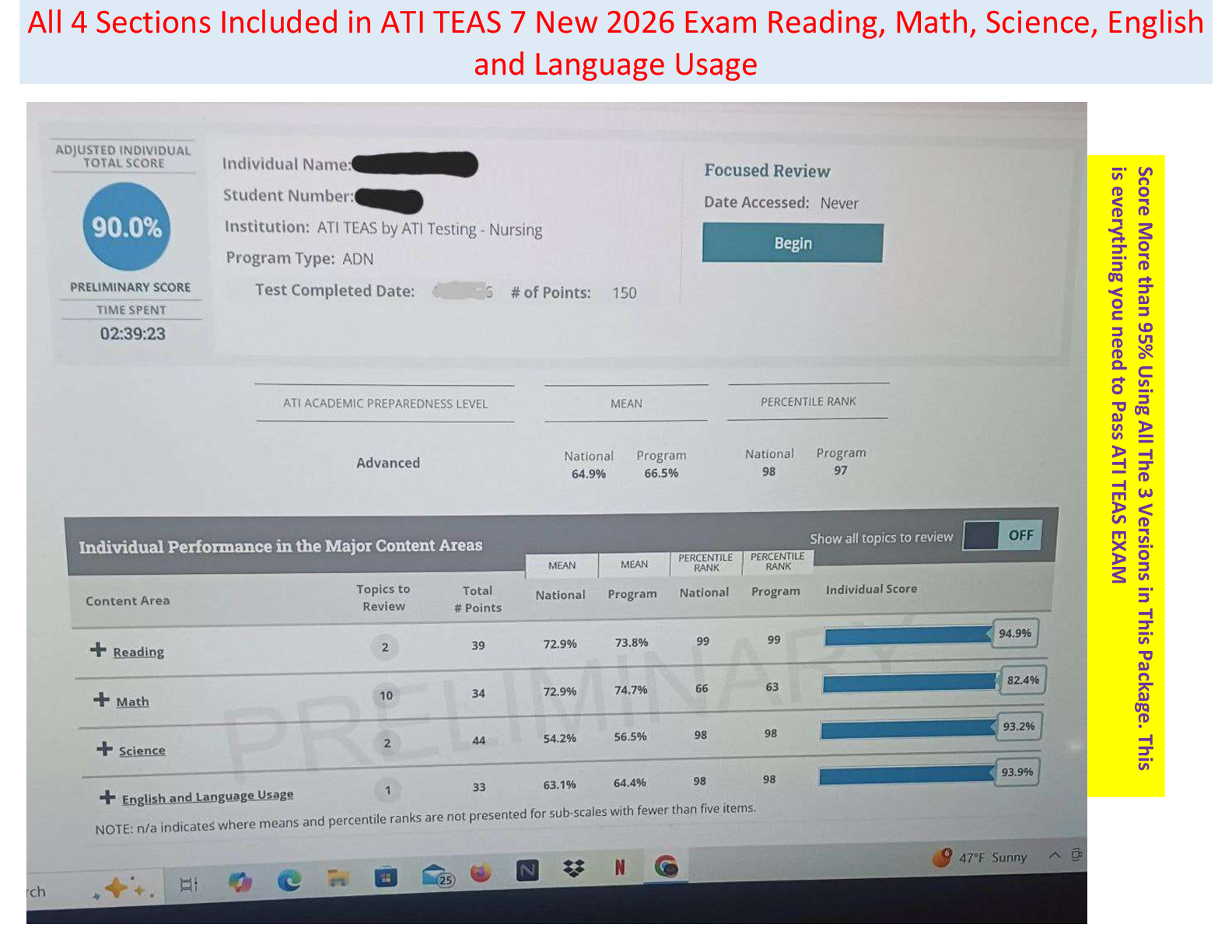
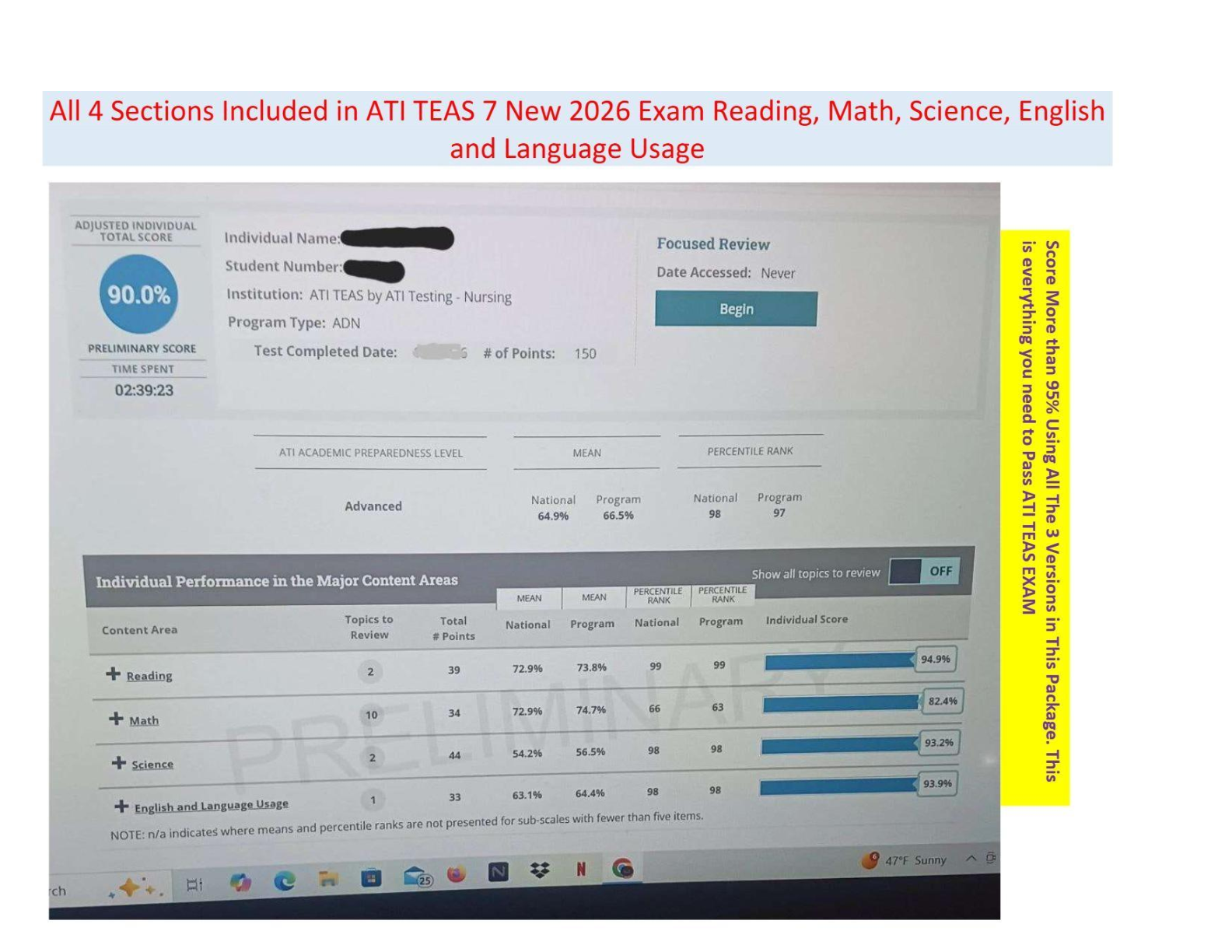
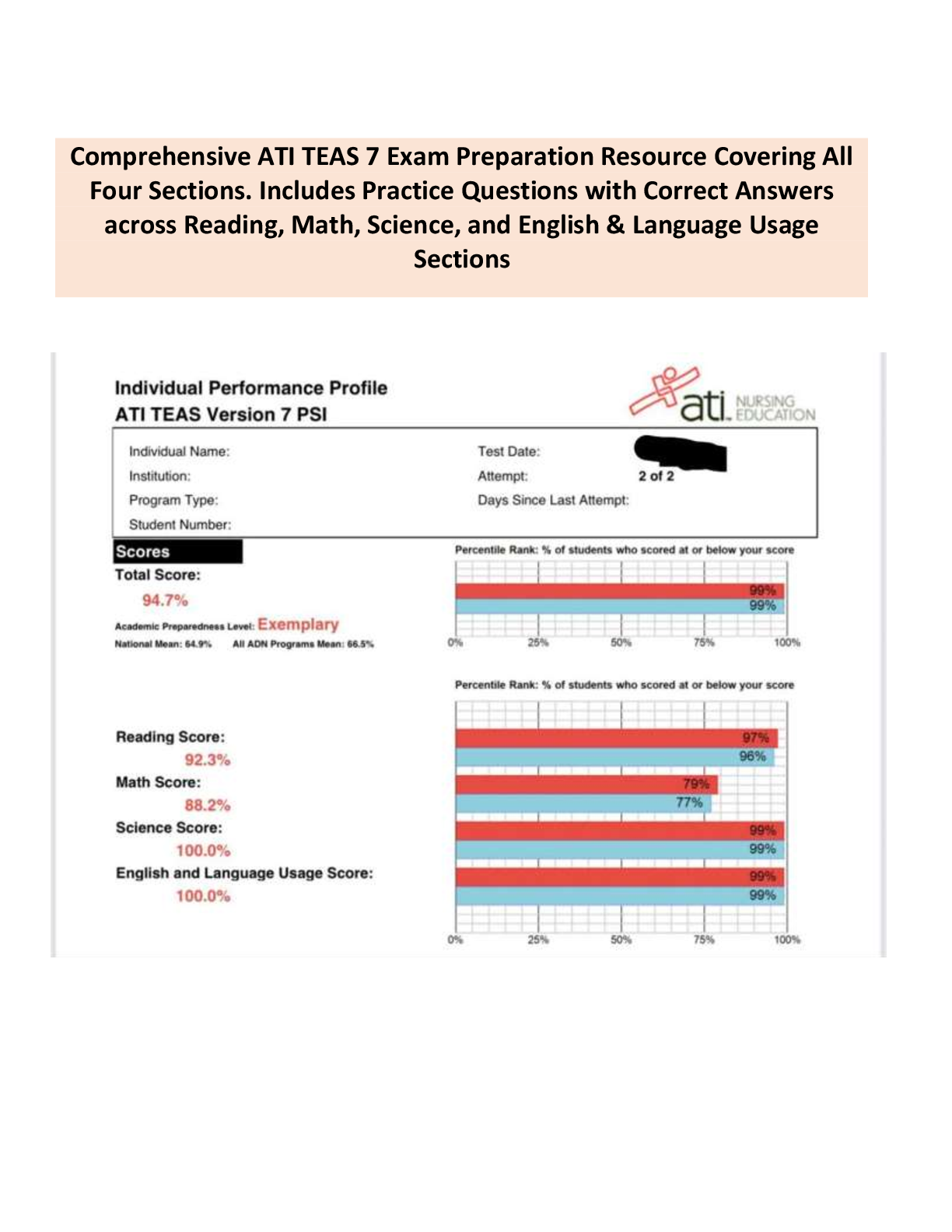
- ANSWER stages of a forensics examination:
Evaluation: Includes receiving instructions, clarifying the instructions, completing risk analysis, and allocating resources
3DES - ANSWER a symmetrical cipher. Three encry
...
- ANSWER stages of a forensics examination:
Evaluation: Includes receiving instructions, clarifying the instructions, completing risk analysis, and allocating resources
3DES - ANSWER a symmetrical cipher. Three encryption keys of various lengths are used. The first key is used to encrypt a block of data, a second key is then used to decrypt the block, and a third key is used to encrypt it again
AES - ANSWER Advanced Encryption Standard. This is a symmetrical block cipher. AEShas been approved and adopted by many governments, including the United States and Canada, to encrypt sensitive data. AES has also been adopted as a standard by the National Institute of Standards and Technolo
cipher - ANSWER Any method of encrypting data by concealing its readability and meaning.
DIACAP - ANSWER compliance is required to be certified to meet the U.S. Department of Defense security requirements for contractors
discretionary access controls - ANSWER Give users the ability to grant or assign rights to objects and make access decisions.
DSA - ANSWER a asymmetrical encryption that uses a private key and a public key. PKI is the framework that uses protocols for encryption.
FedRAMP - ANSWER a U.S. federal government-wide program that outlines the standards for a security assessment, authorization, and continuous monitoring for cloud products and services.
FIPS 140-2 - ANSWER National Institute of Standards and Technology (NIST) publication that coordinates the requirements and standards for cryptography modules.
FISMA - ANSWER a U.S. federal law that outlines the framework to protect federal government information, operations, and facilities.
Generic Routing Encapsulation or GRE - ANSWER A standardized network tunneling protocol that is used to encapsulate any network layer protocol inside a virtual link between two locations. commonly used to create tunnels across a public network that carries private network traffic.
harden - ANSWER The process of disabling all unused services, ports, and applications on a server to make it as secure as possible.
HIPAA - ANSWER defines the standard for protecting medical patient data. Companies that work with protected health information must ensure that all the required physical, network, and process security measures are in place and followed to meet compliance requirements.
IP Security or IPsec - ANSWER A framework or architecture that uses many different protocols to provide integrity, confidentiality of data, and authentication of data on a TCP/IP network.
ISO 27001 - ANSWER standard for quality that ensures a cloud provider meets all regulatory and statutory requirements for its product and service offerings.
ITAR - ANSWER Restricts information from being disseminated to certain foreign entities. a list of data security requirements that cloud companies can certify as being compliant with to meet this U.S. requirement.
L2TP or Layer 2 Tunneling Protocol - ANSWER .A remote access communications protocol that is a common method to connect to a remote device over the Internet.
logging - ANSWER The detailed transaction records generated by all elements in the cloud for the transactions and interactions of a device or system.
mandatory access control or MAC - ANSWER Highly controlled systems where the access is defined by strict levels of access that are common in secure environments such as defense or financial systems.
MPAA - ANSWER Motion Picture Society of America-published best practices for storing, processing, and delivering protected media and content securely over the Internet.
object - ANSWER An item that can be accessed and manipulated in the cloud. It is a cloud component where you can define the measurements that are sent to monitoring systems to collect operational data.
PCI DSS or Payment Card Industry Data Security Standard - ANSWER sets the requirements to guarantee that companies that process, store, or transmit credit card information offer secure processing and handling of credit card data.
Point-to-Point Tunneling Protocol or PPTP - ANSWER Allows a remote PC or network to access a remote network, such as a cloud, by encapsulating PPP packets inside of GRE tunnels.
public key infrastructure or PKI - ANSWER A standardized set of roles, policies, and procedures used to create, manage, distribute, use, store, and revoke digital certificates and manage public/ private key encryption.
RC4 - ANSWER This uses a shared key to encrypt and decrypt a stream of data. was commonly used to secure wireless connections and web transactions as an encryption protocol used in SSL.
RC5 - ANSWER This is the replacement for RC4. It is also a symmetrical block cipher algorithm that uses a variable-length key.
RSA - ANSWER An asymmetrical encryption that uses a private key and a public key. With PKI and RSA, the common implementation is an asymmetrical protocol using a public and private key pair
Secure Sockets Layer or SSL and Transport Layer Security or TLS - ANSWER Protocols that operate on top of TCP and provide an encrypted session between the client and the server.
security policy - ANSWER A document that defines your company's cloud controls, organizational policies, responsibilities, and underlying technologies to secure your cloud deployment.
SOC 1 - ANSWER Service Organization Controls report (also known as SSAE 16 and ISAE 3402). This is a report that outlines controls on a service organization and the internal controls of financial reporting operations.
SOC 2 - ANSWER Service Organization Controls report that concerns a business's nonfinancial reporting controls for availability, confidentiality, privacy, processing integrity, and security of a system.
SOC 3 - ANSWER Service Organization Controls report for public disclosure of financial controls and security reporting.
Application programming interface or API - ANSWER The means to programmatically access, control, and configure a device between different and discrete software and security components.
cloud segmentation - ANSWER The process of dividing the cloud deployment into small sections allow for granular security policies to be applied
command-line interface or CLI - ANSWER A text-based interface tool used to configure, manage and troubleshoot devices.
data classification - ANSWER Organizing data into different tiers or categories to make data available as required and to meet regulatory requirements, mitigate risk, manage risk, and secure data.
durable storage - ANSWER Storage volumes that retain data if the virtual machine is removed or deleted
ephemeral storage - ANSWER Storage volumes that do not retain data if the virtual machine is removed or deleted.
graphical user interface or GUI - ANSWER A graphical representation commonly used to create, configure, manage, and monitor cloud resources and services.
intrusion detection systems or IDSs - ANSWER Detects suspicious activity on the network in real time, by passively monitoring traffic looking for signatures of network activity that indicate an intrusion based on predefined rule sets, and generate alerts.
intrusion prevention systems or IPSs - ANSWER Detect suspicious activity on the network in real-time, by passively monitoring traffic looking for signatures of network activity that indicate an intrusion based on predefined rule sets, and actively shut down the intrusion.
JavaScript Object Notation or JSON - ANSWER A lightweight data-interchange format standard that is easily readable and for computing systems to parse and to generate.
Managed Security as a Service or MSaaS - ANSWER Companies that specialize in cloud-based managed security services.
nondurable storage - ANSWER Storage volumes that do not retain data if the virtual machine is removed or deleted.
Python - ANSWER A high-level programming language.
Representational State Transfer or REST - ANSWER A protocol that communicates between devices over HTTP/HTTPS. This is a method of providing device communications over IP networks.
scripting - ANSWER A method of running configuration commands in the cloud to automate cloud deployments and security services.
Extensible Markup Language or XML - ANSWER a flexible way to describe data, create information formats, and electronically share structured data between computing systems
Cloud segmentation is the process of dividing up your cloud deployment into sections for granular security. segments include compute, network, and storage. - ANSWER Robert has been tasked to create a security implementation that segments his employer's e-commerce design to allow for policy enforcement. What are the areas that he is investigating?
[Show More]