WGU Forensics and Network Intrusion - C702
Computer forensics -ANSWER refers to a set of methodological procedures and techniques to identify, gather, preserve, extract, interpret, document and present evide
...
WGU Forensics and Network Intrusion - C702
Computer forensics -ANSWER refers to a set of methodological procedures and techniques to identify, gather, preserve, extract, interpret, document and present evidence from computing equipment that is acceptable in a court of Law
Cybercrime is defined -ANSWER as any illegal act involving a computing device, network, its systems, or its applications. It is categorized into two types based on the line of attack: internal attacks and external attacks
Computer crimes -ANSWER pose new challenges for investigators due to their speed, anonymity, volatile nature of evidence, global origin of the crimes and difference in laws, and limited legal understanding
Approaches to manage cybercrime investigations include -ANSWER civil, criminal, and administrative approaches
Digital evidence is -ANSWER "any information of probative value that is either stored or transmitted in a digital form". It is of two types: volatile (Power off its lost) and non-volatile (now difference if off)
Forensic readiness refers to -ANSWER an organization's ability to optimally use digital evidence in a limited period of time and with minimal investigation costs. Helps maintain Business Continuity. Practice Drills.
'
Plan:
1. Identify potential evidence required.
2. Determine Source
3. Define Policy
4. establish Policy
5. Identify if Full/formal investigation is required.
6. create process for documenting procedure
7. Legal advisory board
8. Keep Incident response team ready.
includes technical and non-technical actions that maximize an organization's competence to use digital evidence.
Organizations often include computer forensics as part of their -ANSWER incident response plan to track and prosecute the perpetrators of an incident
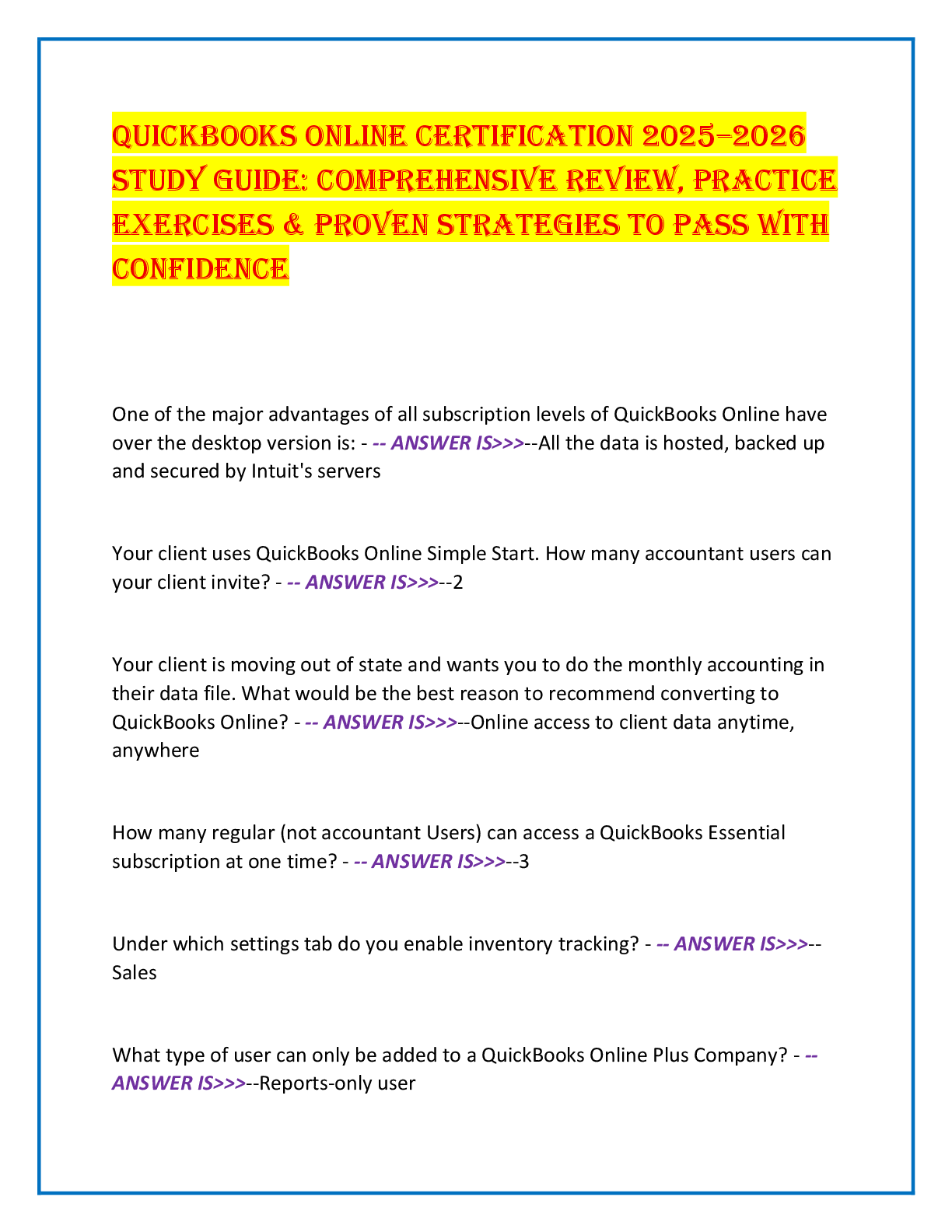
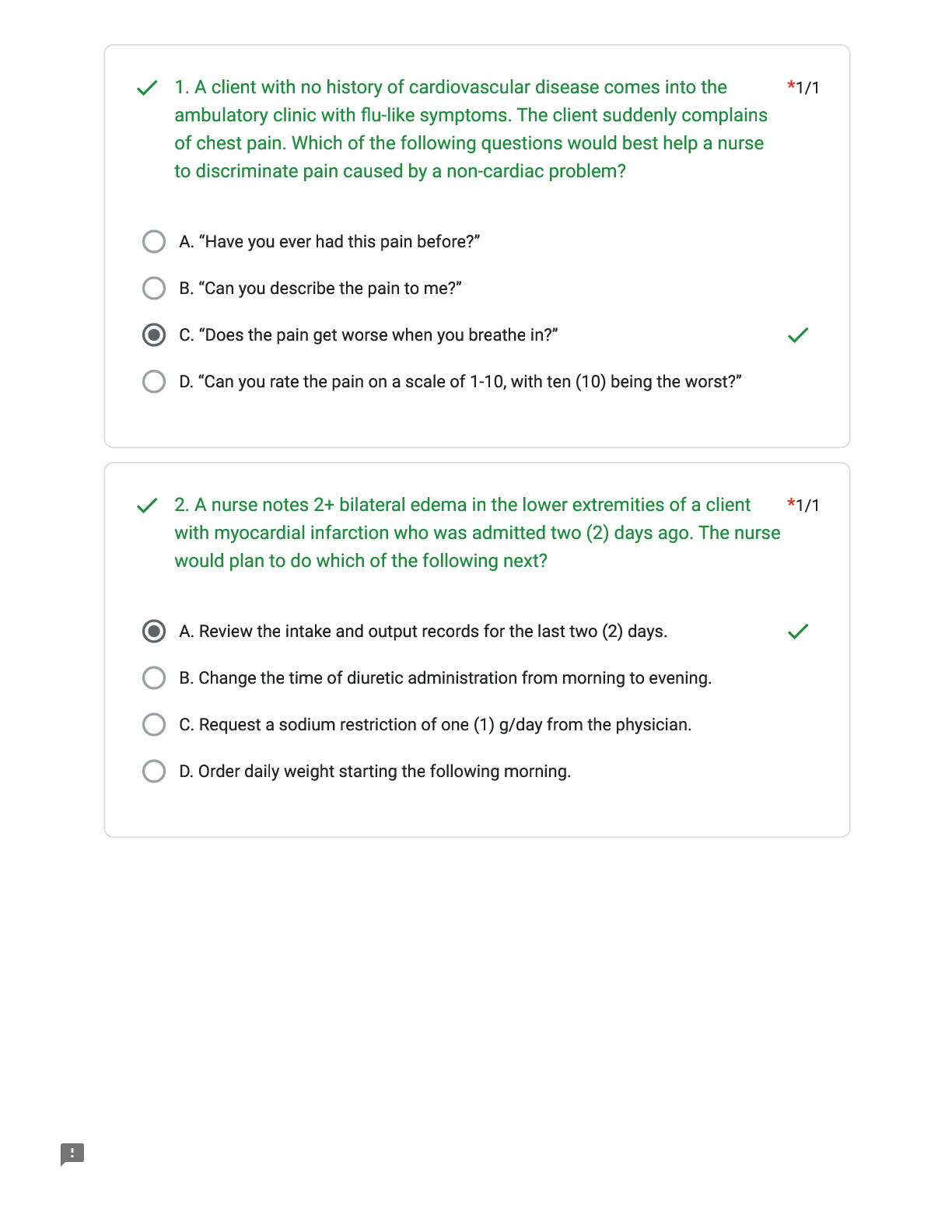
Which of the following is true regarding computer forensics? -ANSWER Computer forensics deals with the process of finding evidence related to a digital crime to find the culprits and initiate legal action against them.
Which of the following is not an objective of computer forensics? -ANSWER Document vulnerabilities allowing further loss of intellectual property, finances, and reputation during an attack.
What is not an impact of cybercrime? -ANSWER Huge financial gain
Which of the following is true of cybercrimes? -ANSWER Investigators, with a warrant, have the authority to forcibly seize the computing devices.
Which of the following is true of civil crimes? -ANSWER The initial reporting of the evidence is generally informal.
Which of the following is a user-created source of potential evidence? -ANSWER Address book
Which of the following is a computer-created source of potential evidence? -ANSWER Steganography
Under which of the following conditions will duplicate evidence not suffice? -ANSWER When original evidence is in possession of the originator
Rules -ANSWER Rule 101: Scope (in US)
Rule 102: Purpose (truth & Just)
Rule 103: Rulings on Evidence
Rule 104: Preliminary Questions
Rule 105: Limited Admissibility(proper scope)
Rule 502: Attorney-Client Privilege and Work Product; Limitations on Waiver
Rule 608: A Witness's Character for Truthfulness or Untruthfulness
Rule 609: Impeachment by Evidence of a Criminal Conviction
Rule 614: Court's Calling or Examining a Witness
Rule 701: Opinion Testimony by Lay Witnesses
Rule 705: Disclosing the Facts or Data Underlying an Expert's Opinion
Rule 801: Definitions That Apply to This Article; Exclusions from Hearsay
Rule 803: Exceptions to the Rule Against Hearsay-Regardless of Whether the Declarant is Available as a Witness
Rule 804: Exceptions to the Rule Against Hearsay-When the Declarant is Unavailable as a Witness
Rule 901: Authenticating or Identifying Evidence
Rule 1001: Definitions that apply to this article
Rule 1002: Requirement of the Original
Rule 1003. Admissibility of Duplicates
Rule 1004. Admissibility of Other Evidence of Content
Minimizing the tangible and intangible losses to the organization or an individual is considered an essential computer forensics use. -ANSWER True
Cybercrimes can be classified into the following two types of attacks, based on the line of attack. -ANSWER Internal and external
Espionage, theft of intellectual property, manipulation of records, and Trojan horse attacks are examples of what? -ANSWER Insider attacks or primary threats
External attacks originate from outside of an organization or can be remote in nature. Such attacks occur when -ANSWER there are inadequate information-security policies and procedures.
Which type of cases involve disputes between two parties? -ANSWER Civil cases involve disputes between two parties, which may include an individual versus a company, an individual versus another individual, or one company versus another.
________ is the standard investigative model used by the FBI when conducting investigations against major criminal organizations. -ANSWER Enterprise Theory of Investigation (ETI)
Gramm-Leach-Bliley Act (GLBA) -ANSWER requires companies that offer financial p
[Show More]









.png)
.png)