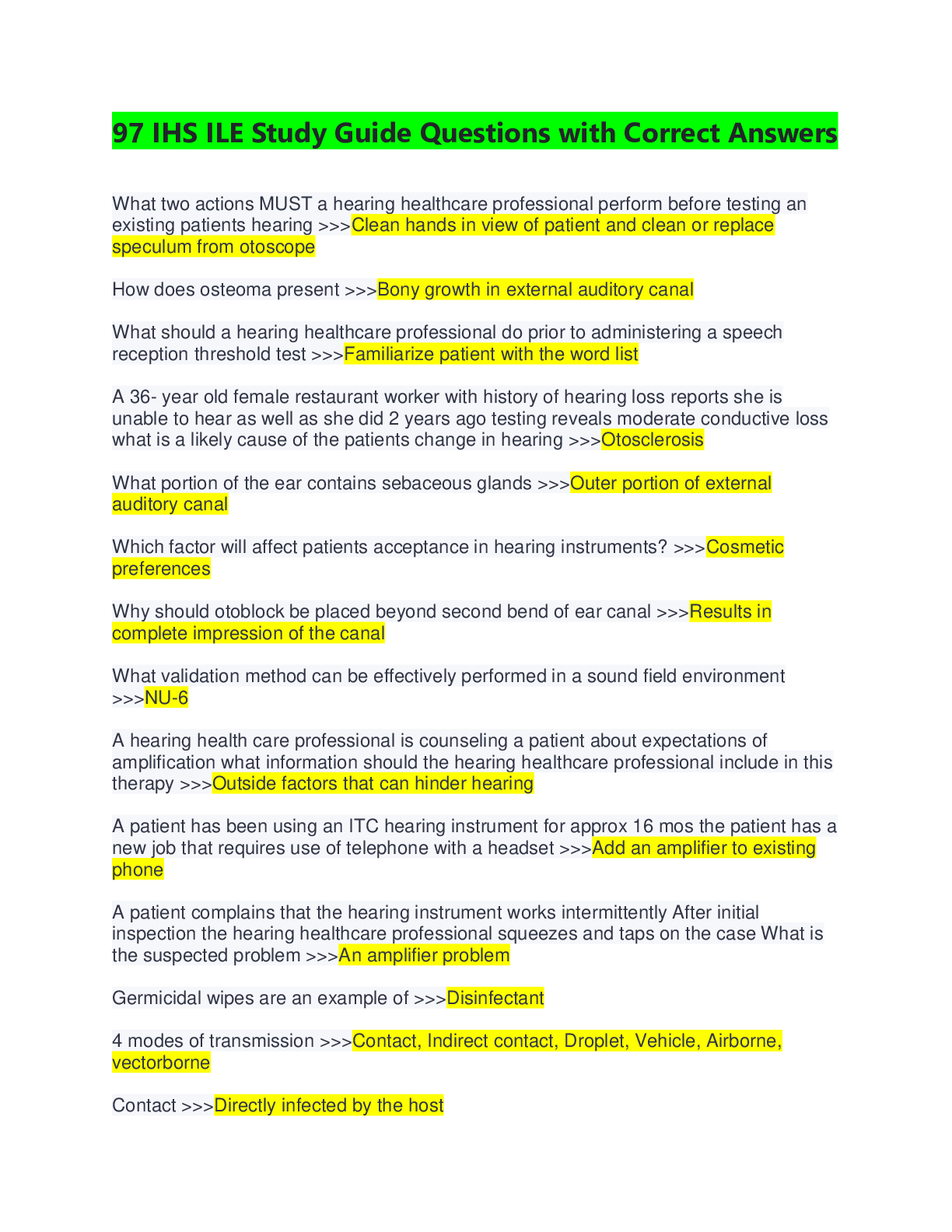
2022 COMPTIA SECURITY/SY0-601 BEST EXAM
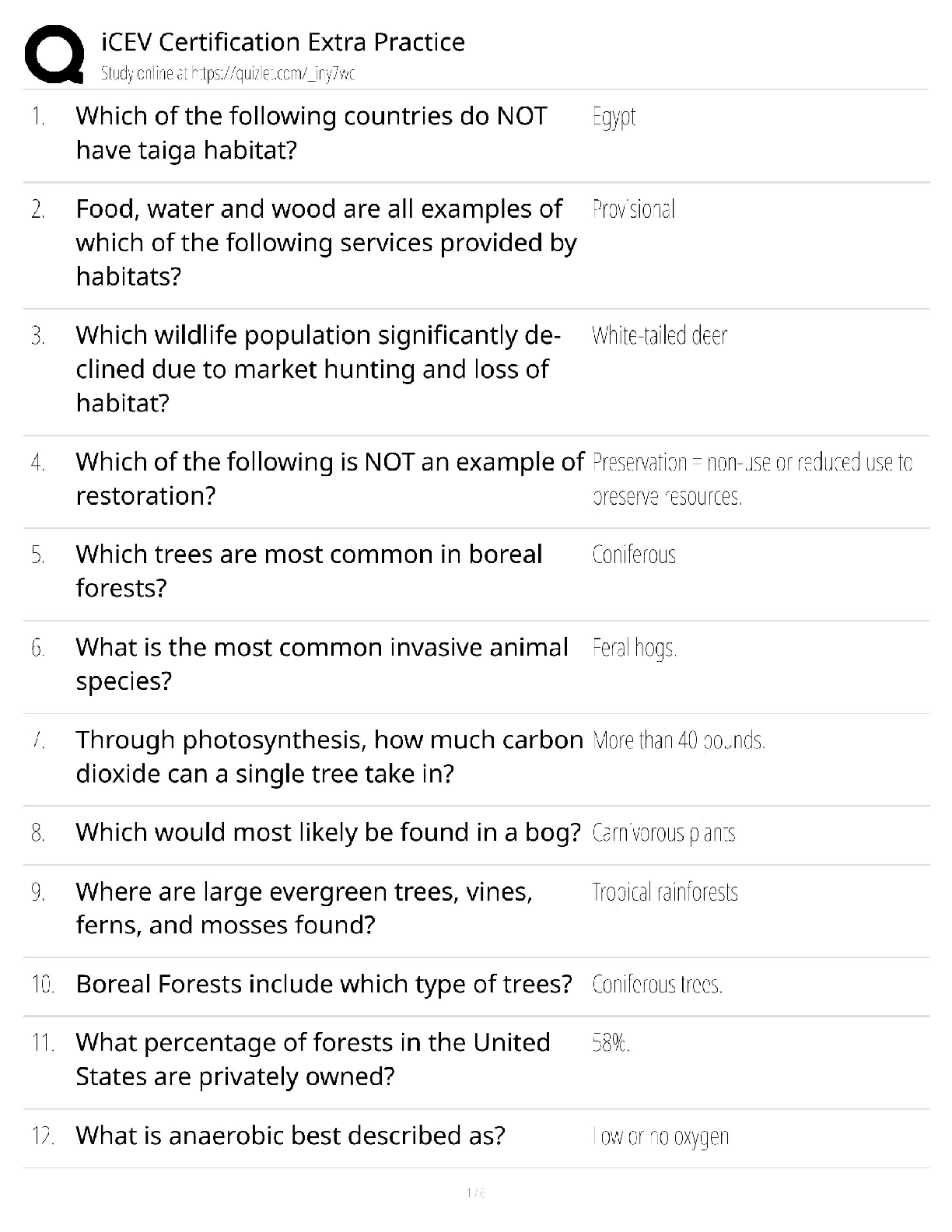
STUDY(100% Verified)
A >>>>A security administrator suspects an employee has been emailing proprietary
information to a competitor. Company policy requires the administrator t
...
2022 COMPTIA SECURITY/SY0-601 BEST EXAM
STUDY(100% Verified)
A >>>>A security administrator suspects an employee has been emailing proprietary
information to a competitor. Company policy requires the administrator to capture an
exact copy of the employee's hard disk.
Which of the following should the administrator use?
A. dd
B. chmod
C. dnsenum
D. logger
THIS IS THE ORDER AS FOLLOWS:
ssh-keygen -t rsa
ssh-copy-id -i ~/.ssh/id_rsa.pub user@server
chmod 644 ~/.ssh/id_rsa
ssh root@server >>>>DRAG AND DROP SIMULATION (SEE IMAGE)
Firewall 1:DNS Rule "" ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound "" 10.0.0.1/24 --> ANY --> HTTPS --> PERMIT
Management "" ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound "" ANY --> ANY --> HTTPS --> PERMIT
HTTP Inbound "" ANY --> ANY --> HTTP --> DENY
Firewall 2: No changes should be made to this firewall
Firewall 3:DNS Rule "" ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound "" 192.168.0.1/24 --> ANY --> HTTPS --> PERMIT
Management "" ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound "" ANY --> ANY --> HTTPS --> PERMIT
HTTP Inbound "" ANY --> ANY --> HTTP --> DENY >>>>DROP DOWN SIMULATION
(SEE IMAGE)
See IMAGE >>>>DRAG AND DROP SIMULATION (SEE ANSWERS IN IMAGE)
DF >>>>Which of the following will MOST likely adversely impact the operations of
unpatched traditional programmable-logic controllers, running a back-end LAMP server
and OT systems with human-management interfaces that are accessible over the
Internet via a web interface? (Choose two.)
A. Cross-site scripting
B. Data exfiltration
C. Poor system logging
D. Weak encryption
E. SQL injection
F. Server-side request forgery
A >>>>A company recently transitioned to a strictly BYOD culture due to the cost of
replacing lost or damaged corporate-owned mobile devices.
Which of the following technologies would be BEST to balance the BYOD culture while
also protecting the company's data?
A. Containerization
B. Geofencing
C. Full-disk encryption
D. Remote wipe
D >>>>A Chief Security Office's (CSO's) key priorities are to improve preparation,
response, and recovery practices to minimize system downtime and enhance
organizational resilience to ransomware attacks.
Which of the following would BEST meet the CSO's objectives?
A. Use email-filtering software and centralized account management, patch high-risk
systems, and restrict administration privileges on fileshares.
B. Purchase cyber insurance from a reputable provider to reduce expenses during an
incident.
C. Invest in end-user awareness training to change the long-term culture and behavior
of staff and executives, reducing the organization's susceptibility to phishing attacks.
D. Implement application whitelisting and centralized event-log management, and
perform regular testing and validation of full backups.
AC >>>>A network engineer has been asked to investigate why several wireless
barcode scanners and wireless computers in a warehouse have intermittent connectivity
to the shipping server. The barcode scanners and computers are all on forklift trucks
and move around the warehouse during their regular use.
Which of the following should the engineer do to determine the issue? (Choose two.)
A. Perform a site survey
B. Deploy an FTK Imager
C. Create a heat map
D. Scan for rogue access points
E. Upgrade the security protocols
F. Install a captive portal
[Show More]






 v.png)