Computer Science > QUESTIONS & ANSWERS > WGU C839 Introduction to Cryptography - (EC-Council CES) Latest 2022 (All)
WGU C839 Introduction to Cryptography - (EC-Council CES) Latest 2022
Document Content and Description Below
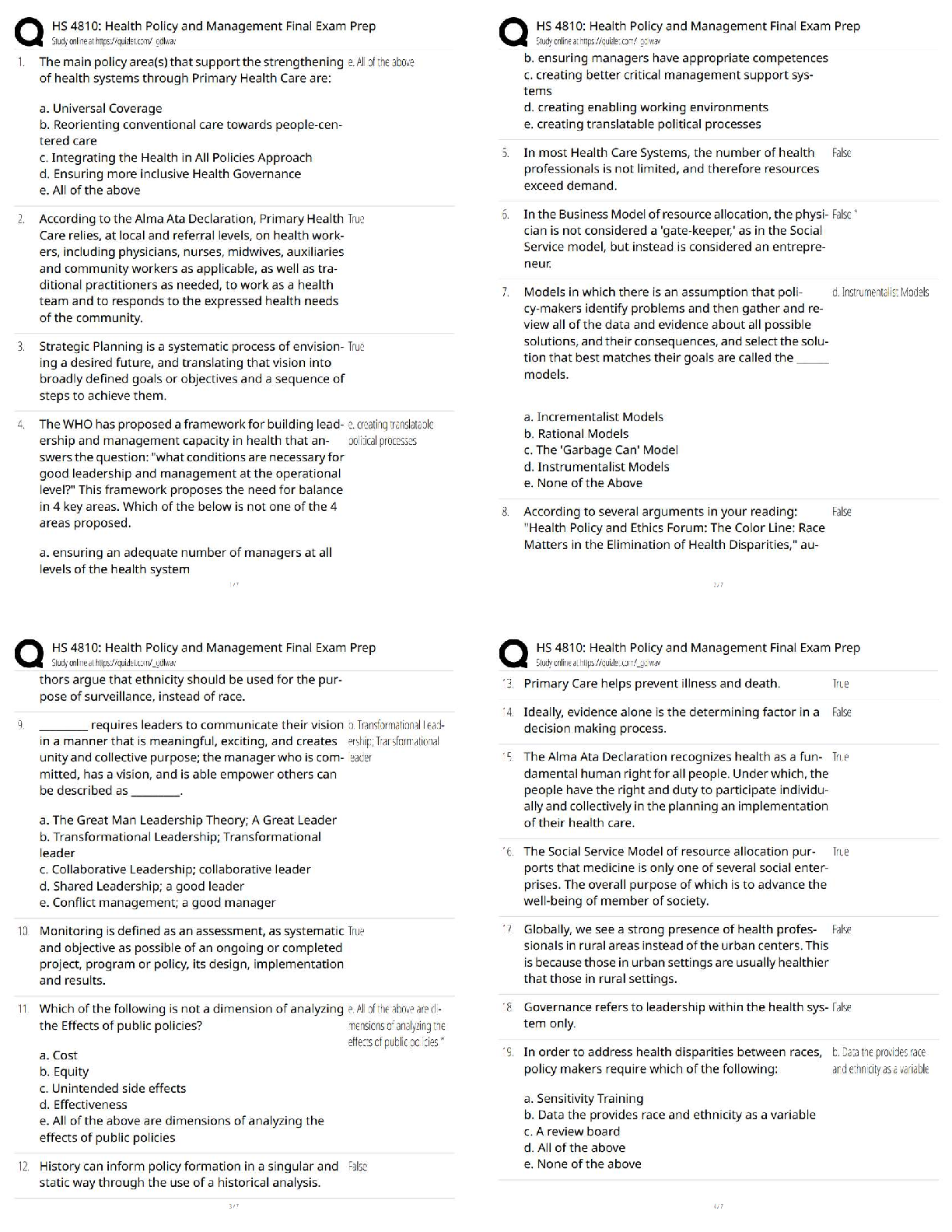
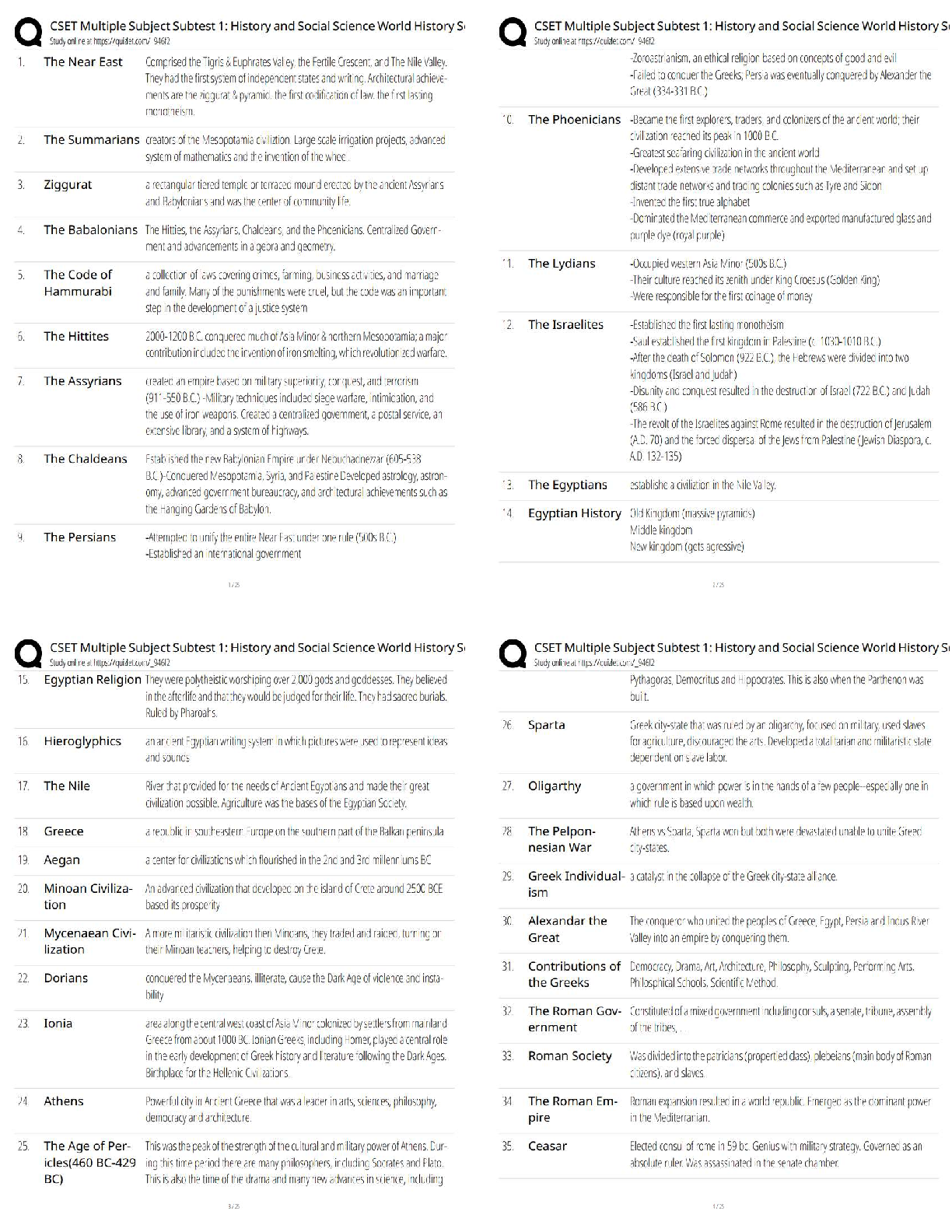
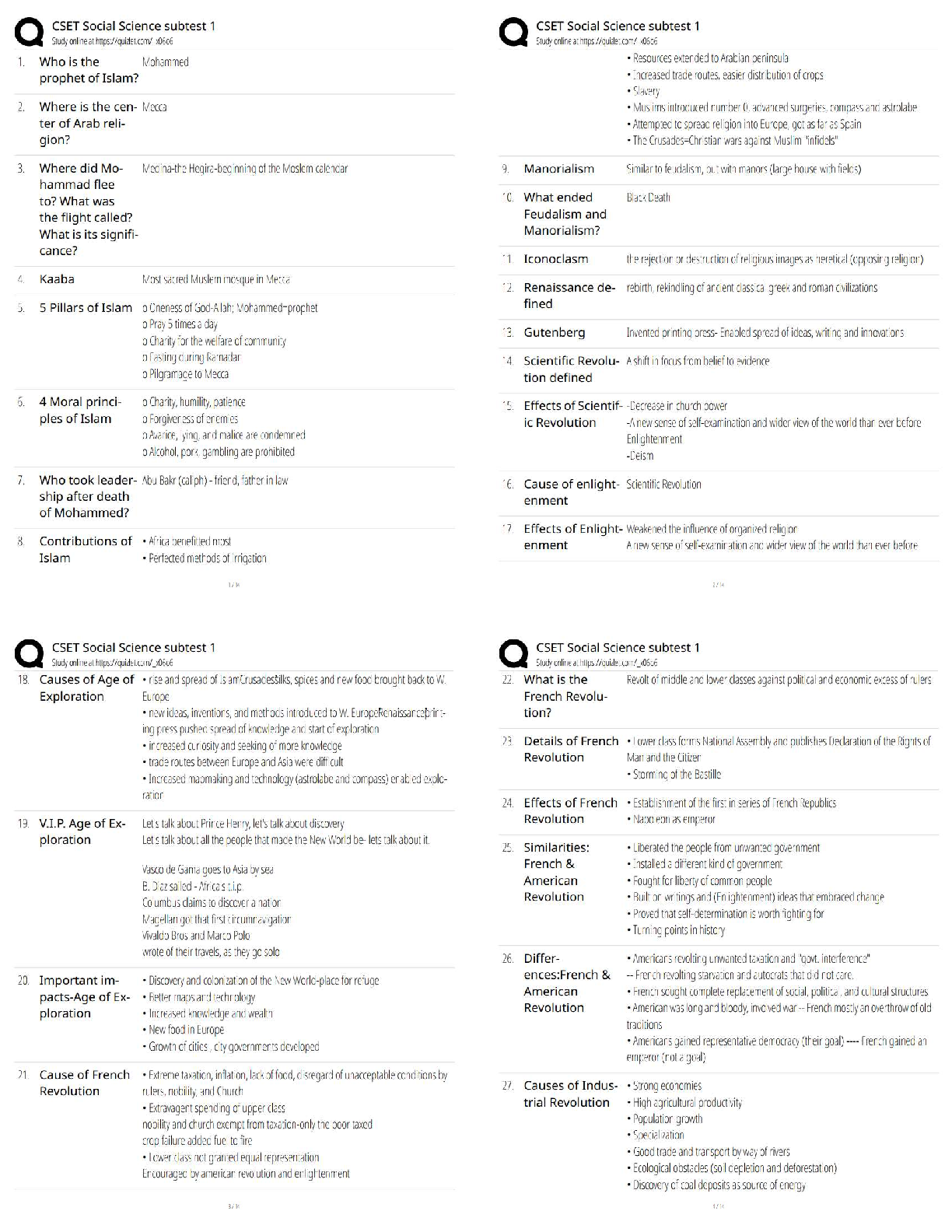
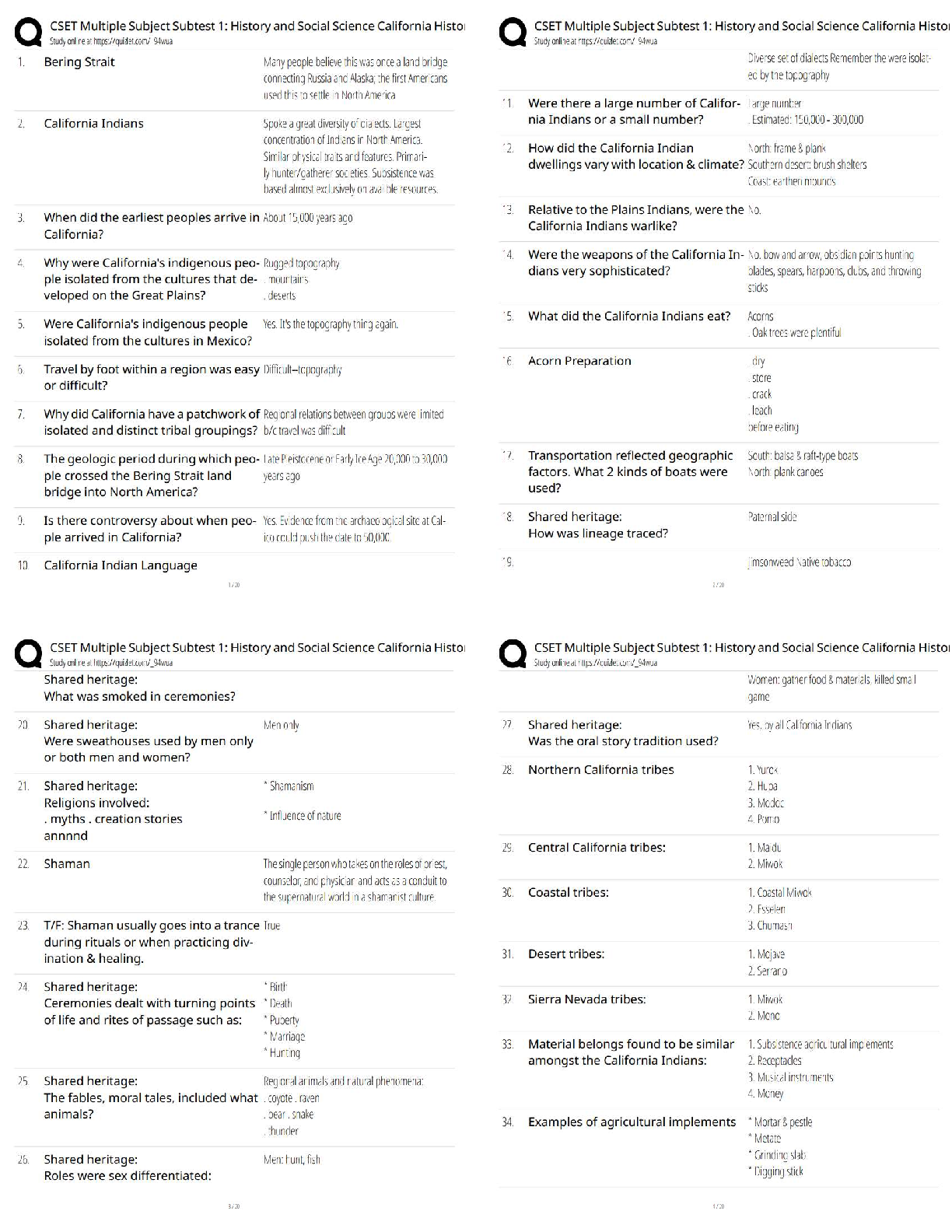
WGU C839 Introduction to Cryptography - (EC-Council CES) Latest 2022 CrypTool ✔✔Software which allows encryption of text using historic algorithms The Enigma Machine ✔✔In World War II the G ... ermans made use of an electro-mechanical rotor based cipher Known as The Enigma Machine. Allied cipher machines used in WWII included the British TypeX and the American SIGABA. The ADFGVX Cipher ✔✔invented by Colonel Fritz Nebel in 1918. The key for this algorithm is a six-by-six square of letters, used to encode a 36-letter alphabet. The Playfair Cipher ✔✔invented in 1854 by Charles Wheatstone. The Playfair cipher uses a five-by-five table containing a keyword or key phrase. Breaking the Vigenère Cipher ✔✔In 1863, Friedrich Kasiski was the first person to publish a successful general attack on the Vigenère Cipher The Vigenère Cipher ✔✔This is perhaps the most widely known multi-alphabet substitution cipher. invented in 1553 by Giovan Battista Bellaso. Uses a series of different Caesar ciphers based on the letters of a keyword. The Cipher Disk ✔✔The cipher disk was invented by Leon Alberti in 1466. each time you turned the disk, you used a new cipher. It was literally a disk you turned to encrypt plaintext. Multi-Alphabet Substitution ✔✔Use of multiple substitution alphabets. Example:Cipher Disk, Vigenere Cipher, Enigma Machine Scytale ✔✔This was a cylinder tool used by the Greeks, and is often specifically attributed to the Spartans. Physical cylinder that was used to encrypt messages. ROT13 Cipher ✔✔It is essentially the Caesar cipher always using a rotation or shift of 13 characters. The ATBASH Cipher ✔✔Hebrew scribes copying religious texts used this cipher. substitutes the first letter of the alphabet for the last, and the second letter for the second-to-the-last, etc. The Caesar Cipher ✔✔You can choose to shift any number of letters, either left or right. If you choose to shift two to the right, that would be a +2; if you choose to shift four to the left, that would be a -4. Mono-Alphabet Substitution ✔✔These algorithms simply substitute one character of cipher text for each character of plain text. Examples: Atbash Cipher, Caesar Cipher, Rot13 Symmetric Cryptography ✔✔It is simply any algorithm where the key used to decrypt a message is the same key used to encrypt. Diffusion ✔✔Changes to one character in the plain text affect multiple characters in the cipher text. Confusion ✔✔Confusion attempts to make the relationship between the statistical frequencies of the cipher text and the actual key as complex as possible. This occurs by using a complex substitution algorithm. Avalanche ✔✔a small change yields large effects in the output, This is Fiestel's variation on Claude Shannon's concept of diffusion. Kerckhoffs's Principle ✔✔This principle states that a cryptosystem should be secure even if everything about the system, except the key, is publicly known. Substitution ✔✔Substitution is changing some [Show More]
Last updated: 3 years ago
Preview 1 out of 27 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
WGU C839 BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
WGU C839 BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
By Nutmegs 3 years ago
$15
10
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 27, 2022
Number of pages
27
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 27, 2022
Downloads
0
Views
158










.png)