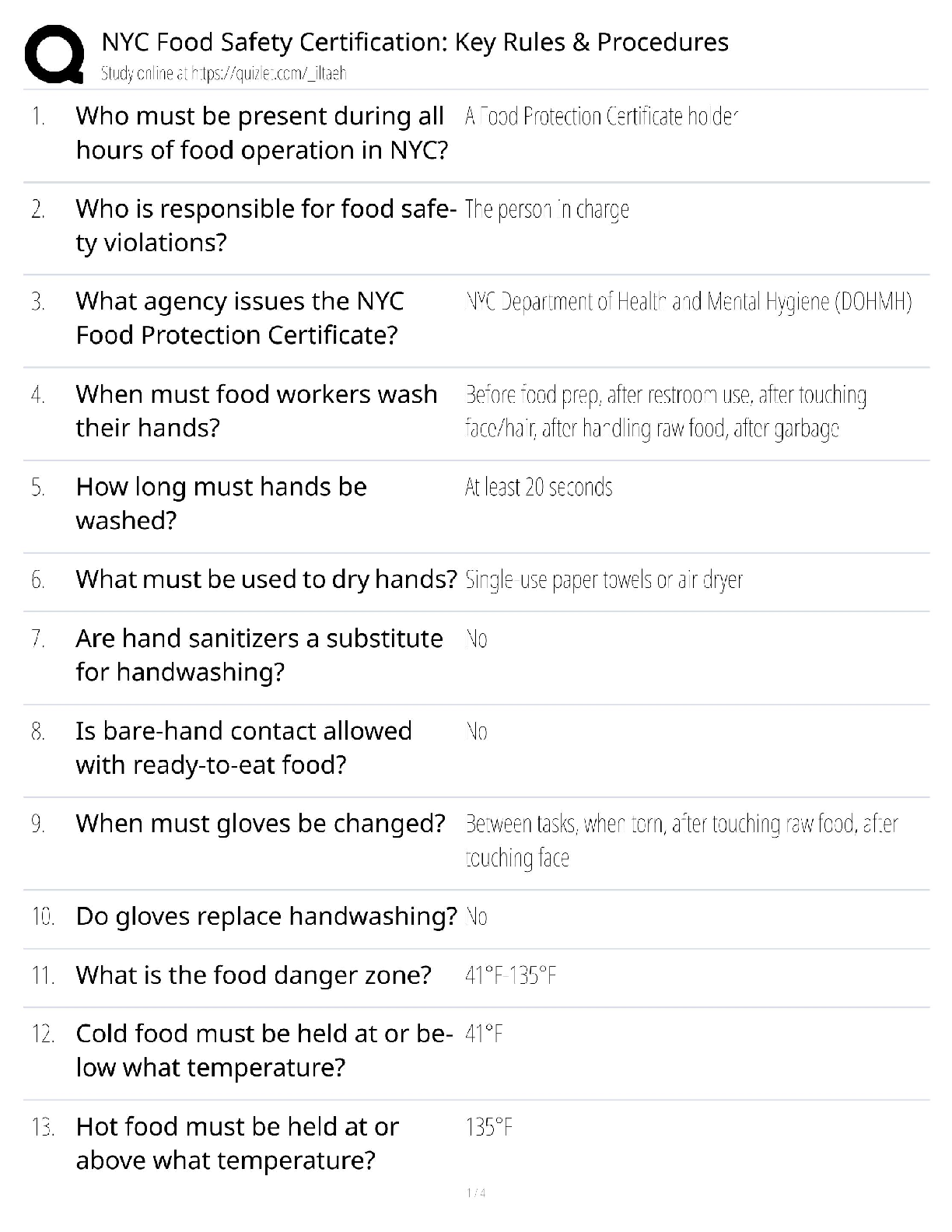
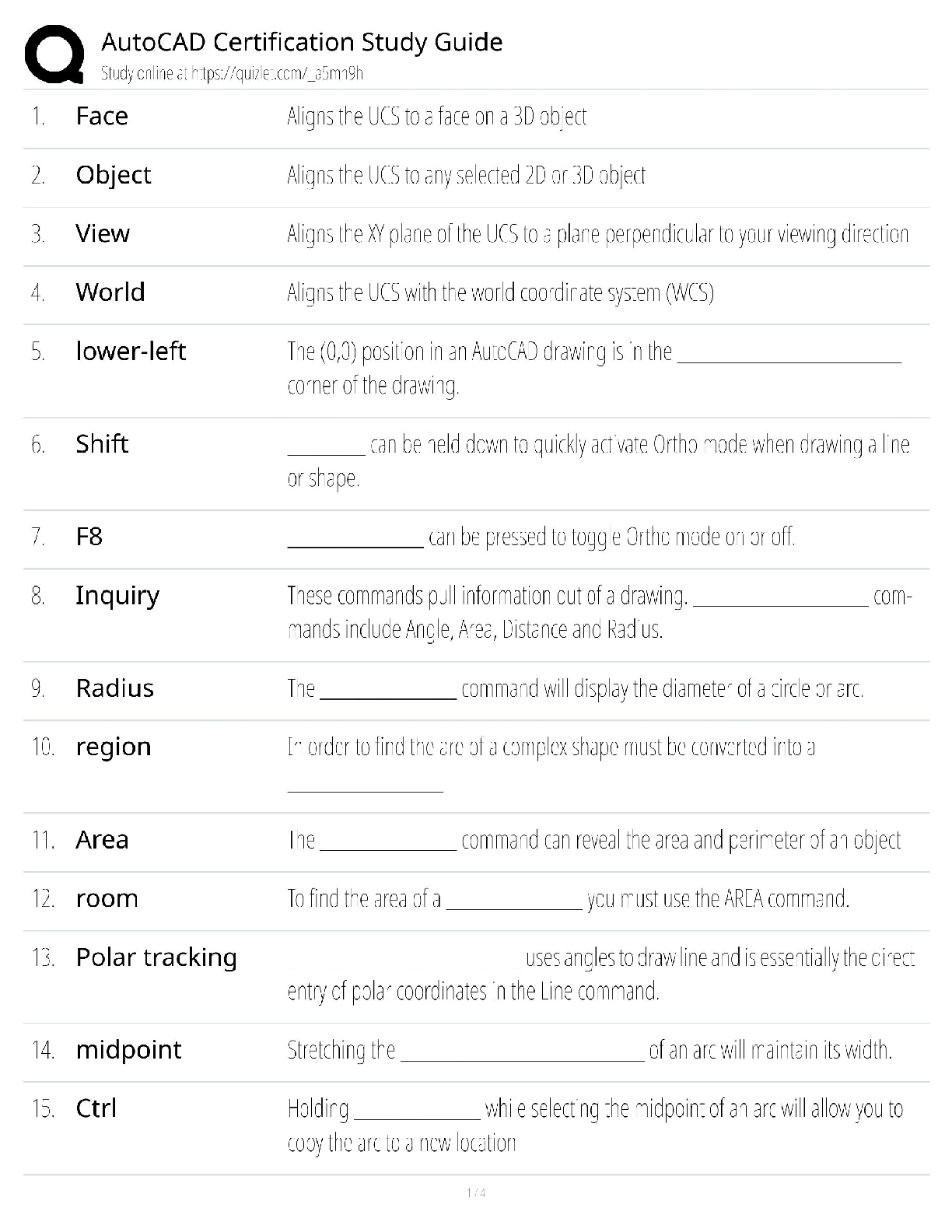
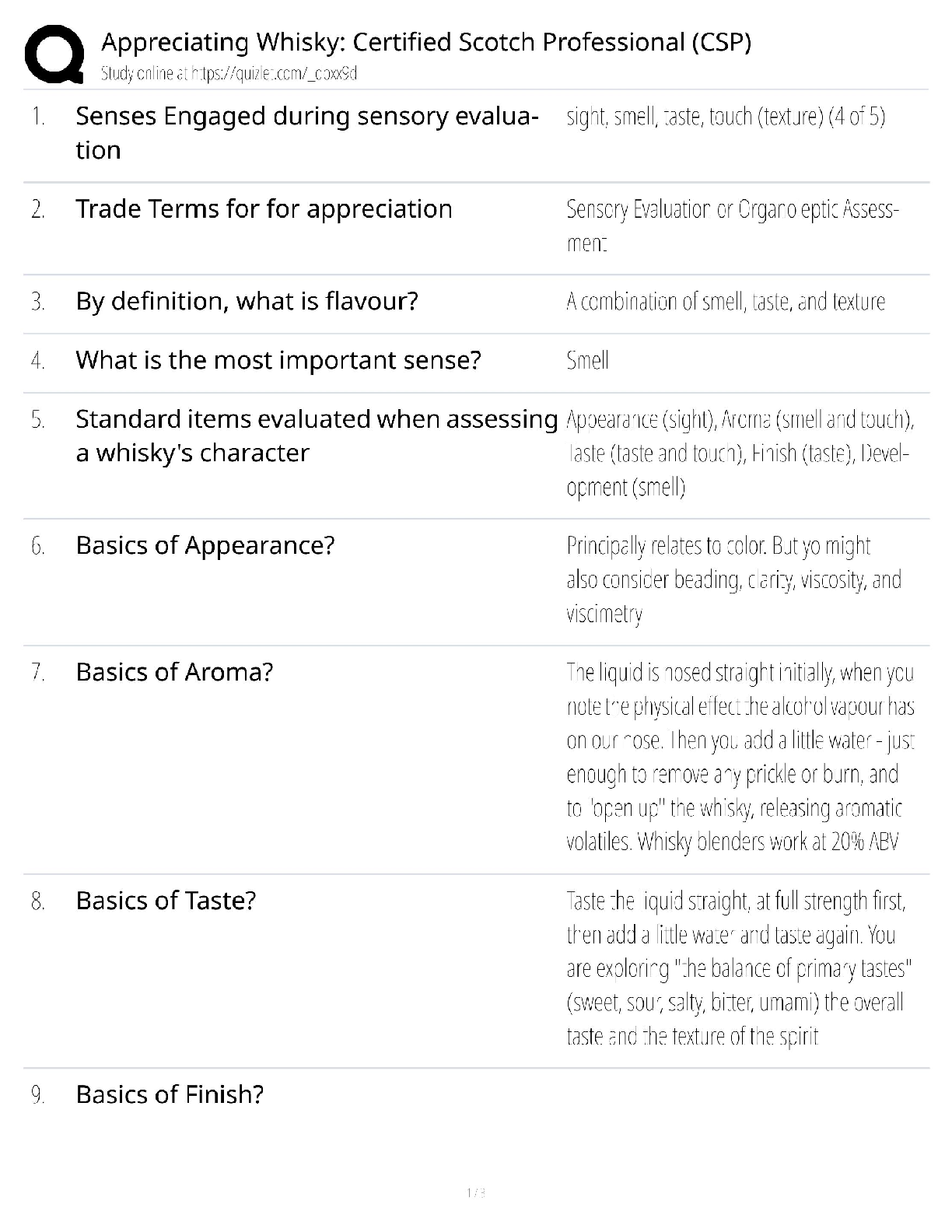
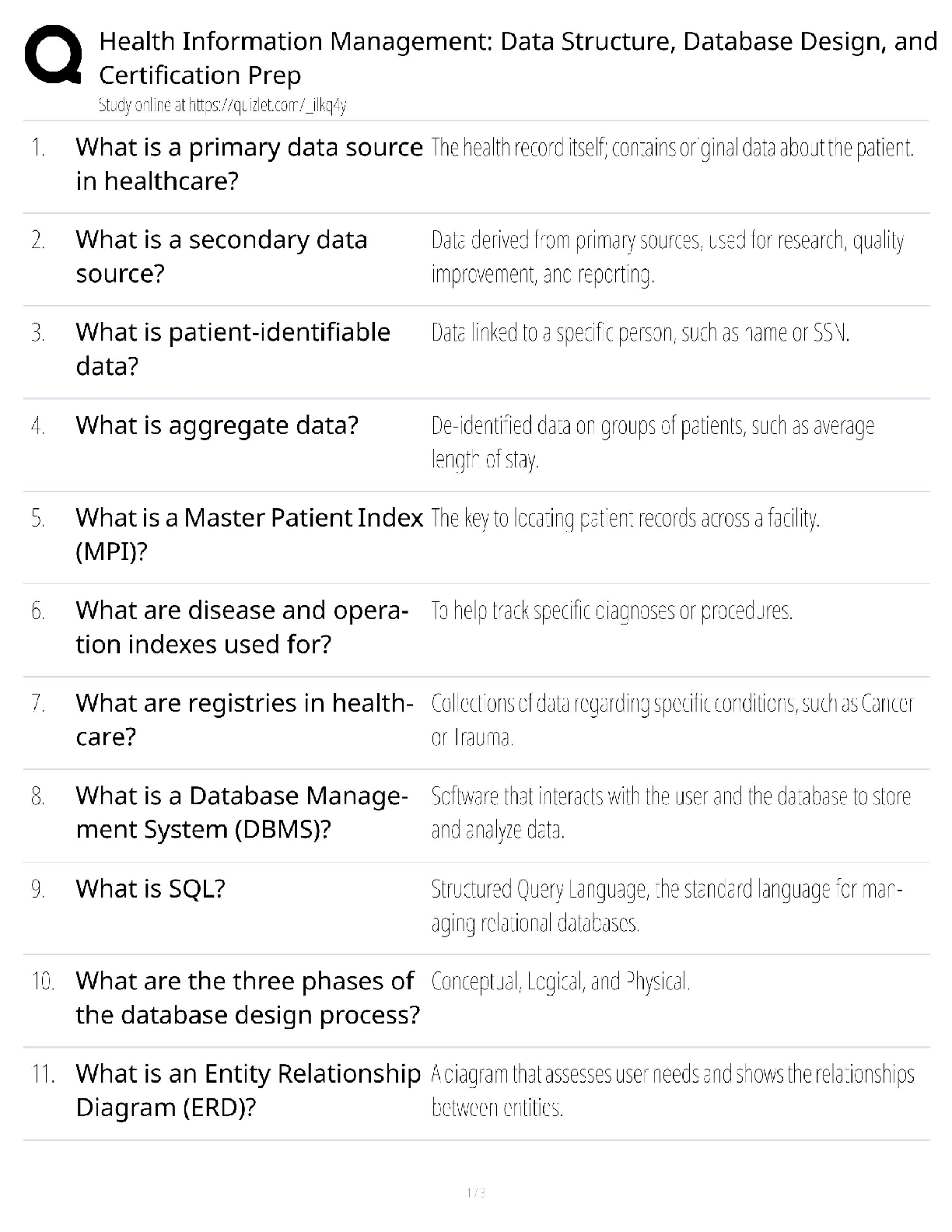
C724 (Information Systems Management) - WGU Complete Solution Guide.
$ 18
.png)
Abnormal Psychology Integrative Approach Study Guide
$ 7

MENU PLANNING AND CATERING SERVICES
$ 5
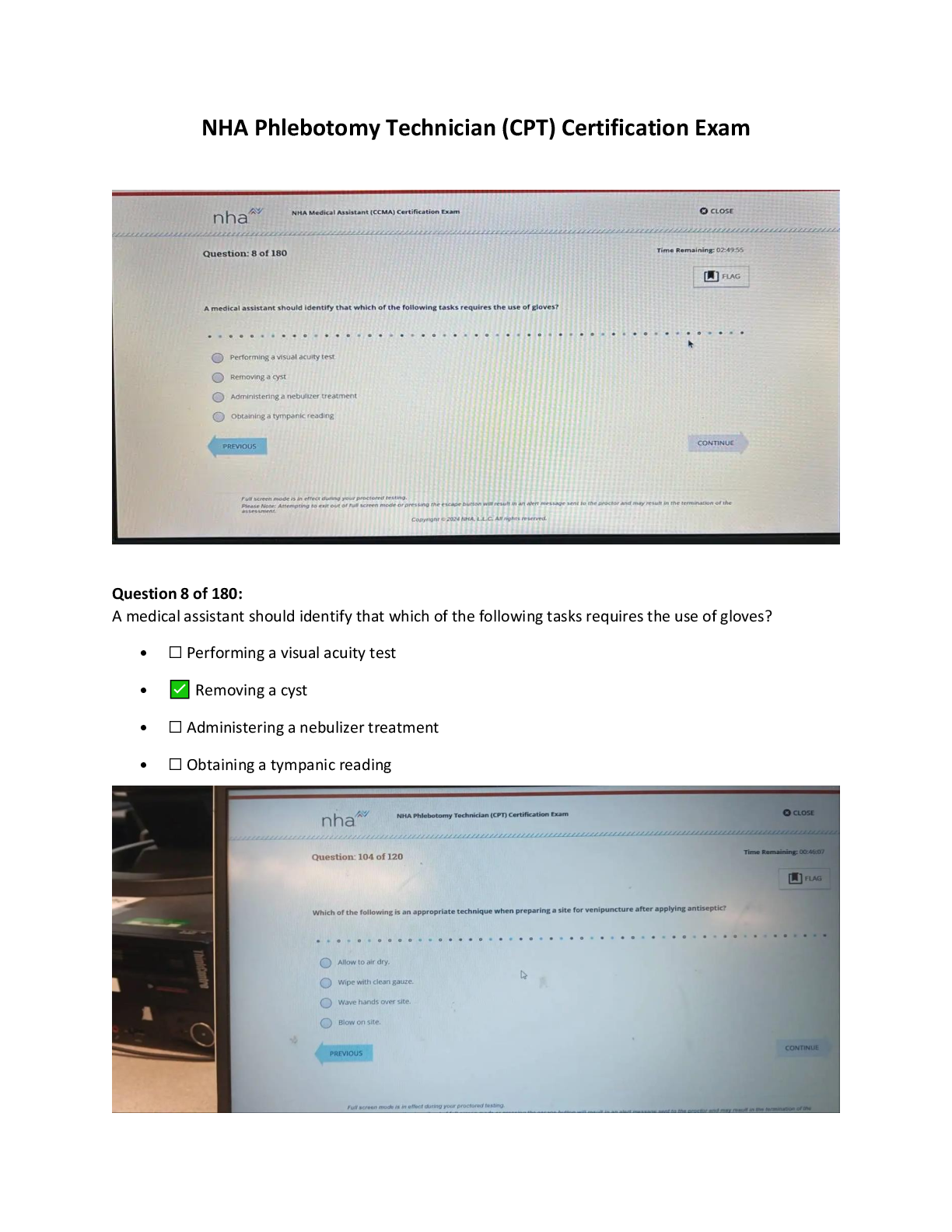
NHA Phlebotomy Technician CPT Certification Exam
$ 30
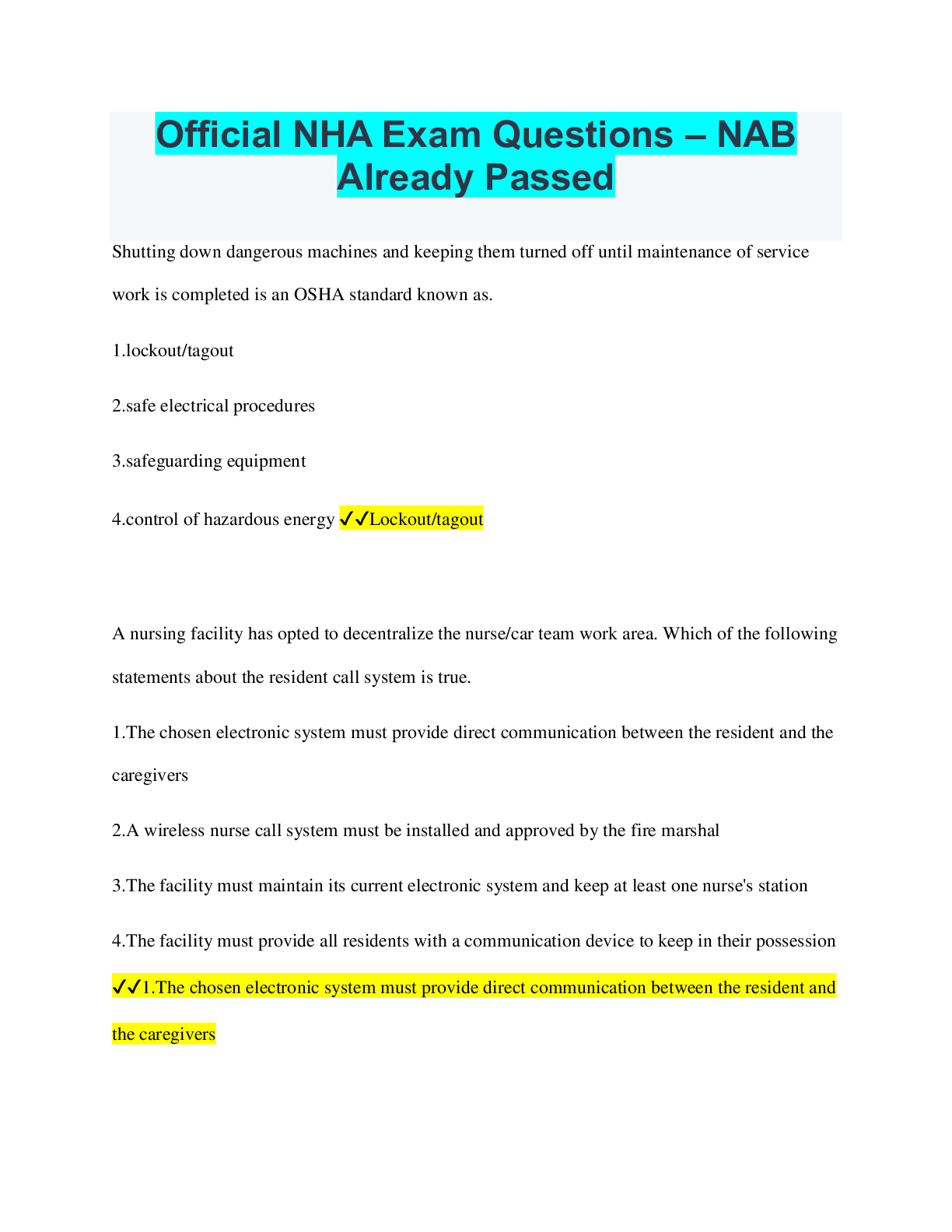
Official NHA Exam Questions – NAB With Complete Solution
$ 11.5

Bus-470 Final Exam Review
$ 16

Solutions Manual and Test Bank for Advanced Financial Accounting 13th Edition By Theodore Christensen
$ 25
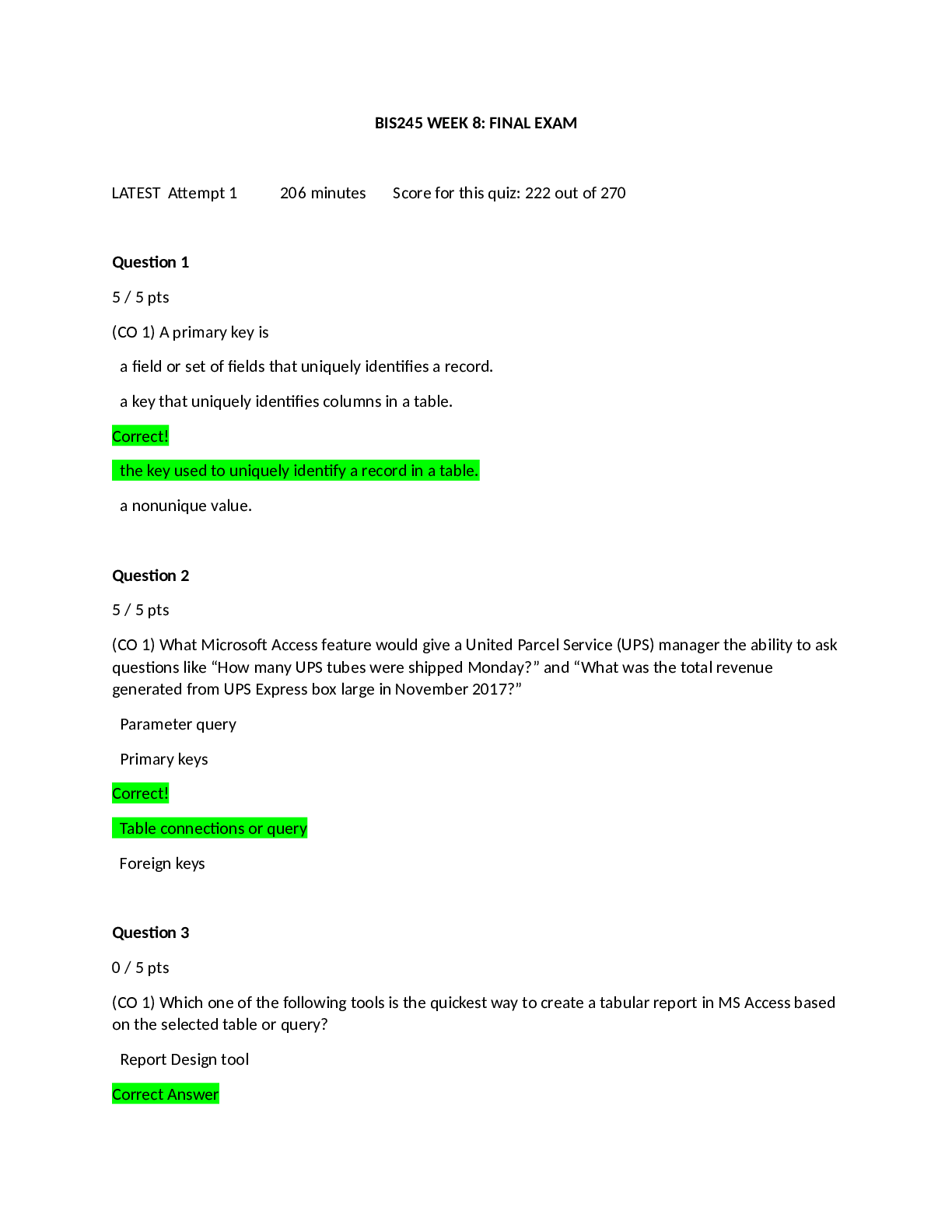
BIS245 WEEK 8: FINAL EXAM AND CORRECT ANSWERS HIGHLIGHTED 2021
$ 8
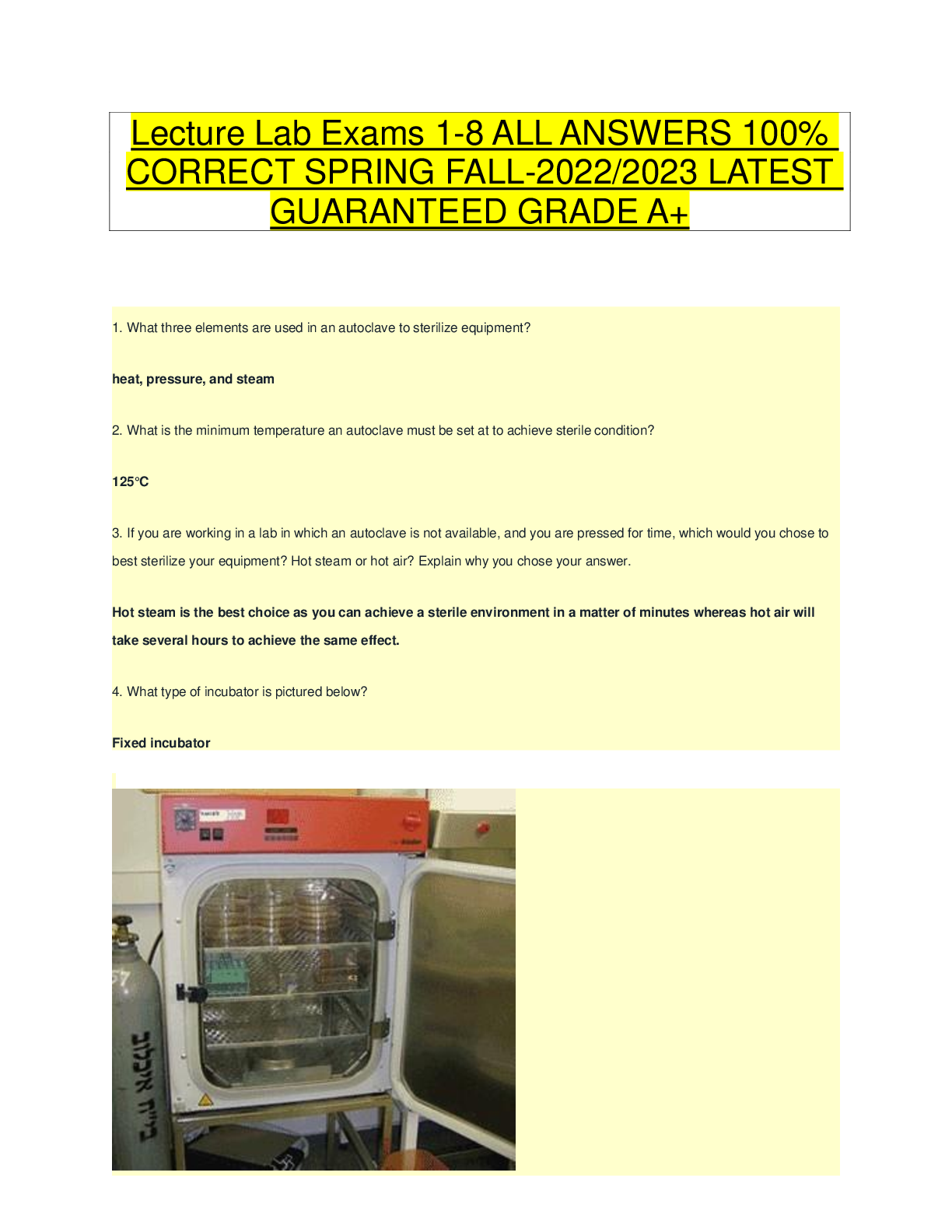
Lab Exams 1-8 Portage Learning 2021/22
$ 7.5
.png)
Study Guide Exam 1 Solution questions with answers 2022
$ 7
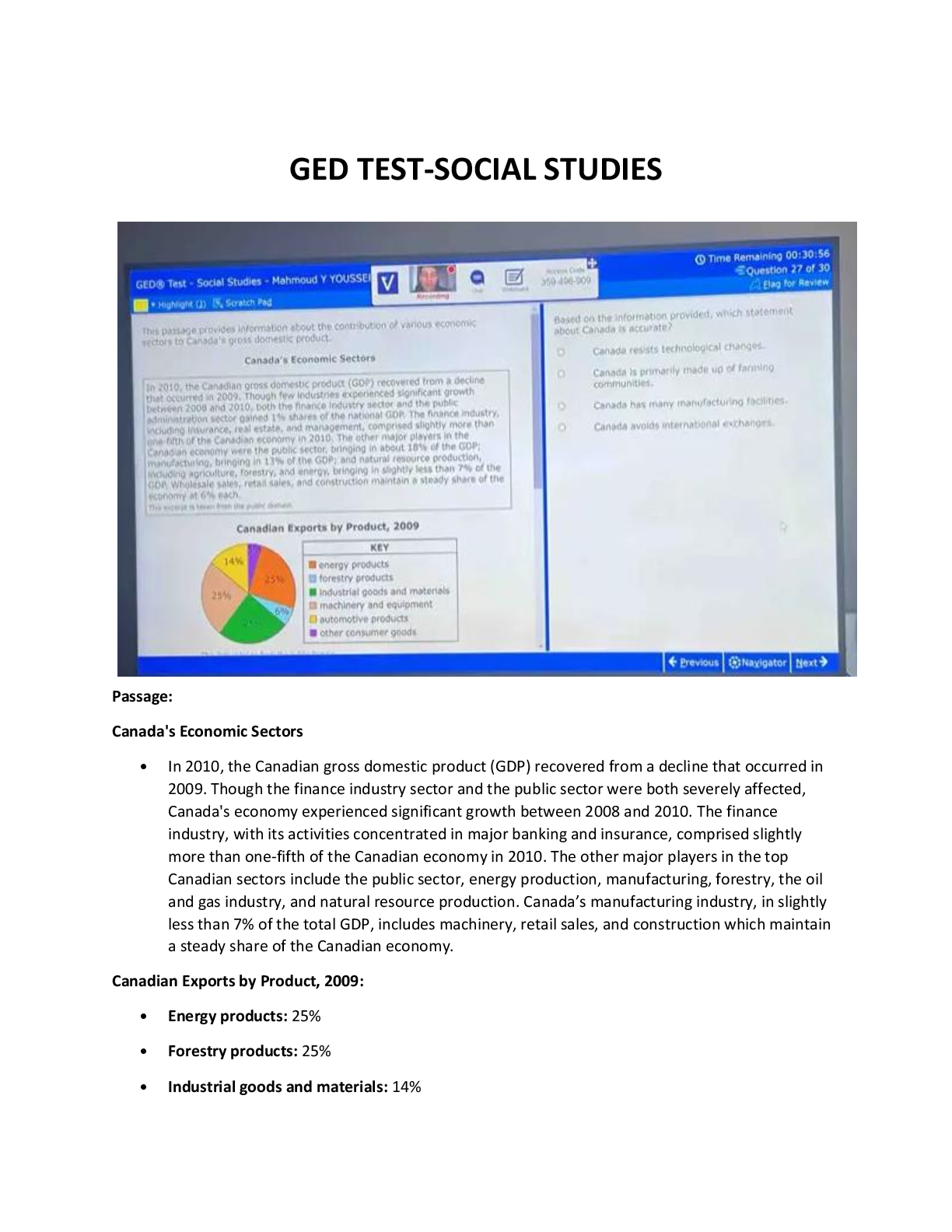
GED Test Social Studies Comprehensive Exam Study Guide
$ 20

C493: Leadership and Professional Image TASK 2
$ 15
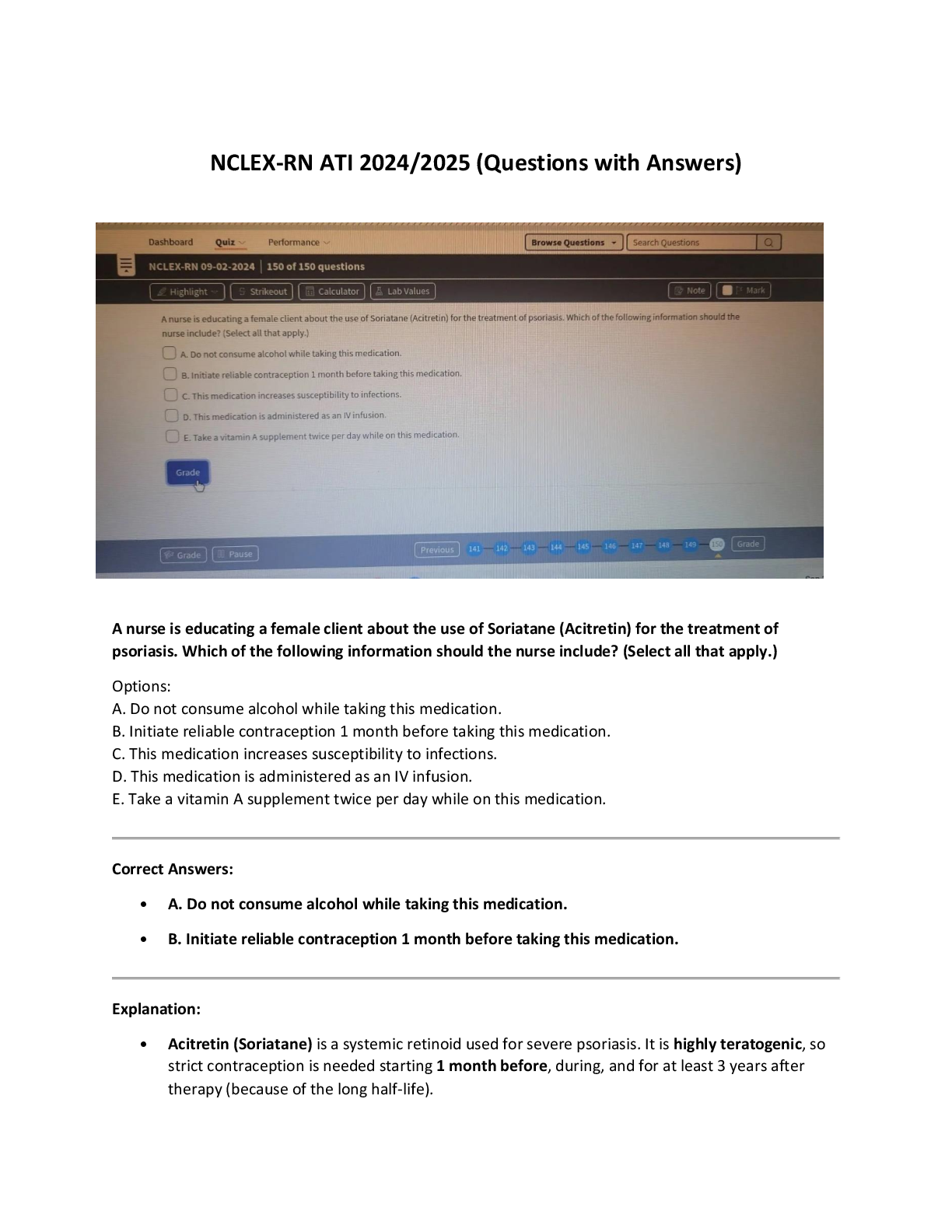
RN NCLEX V2 Comprehensie Exam Guide
$ 20

BUSN 250 Final Exam 2024
$ 16

FISDAP TRAUMA LATEST EXAM.pdf
$ 19

Test Bank for Groups Process and Practice 9th Edition by Corey.
$ 6
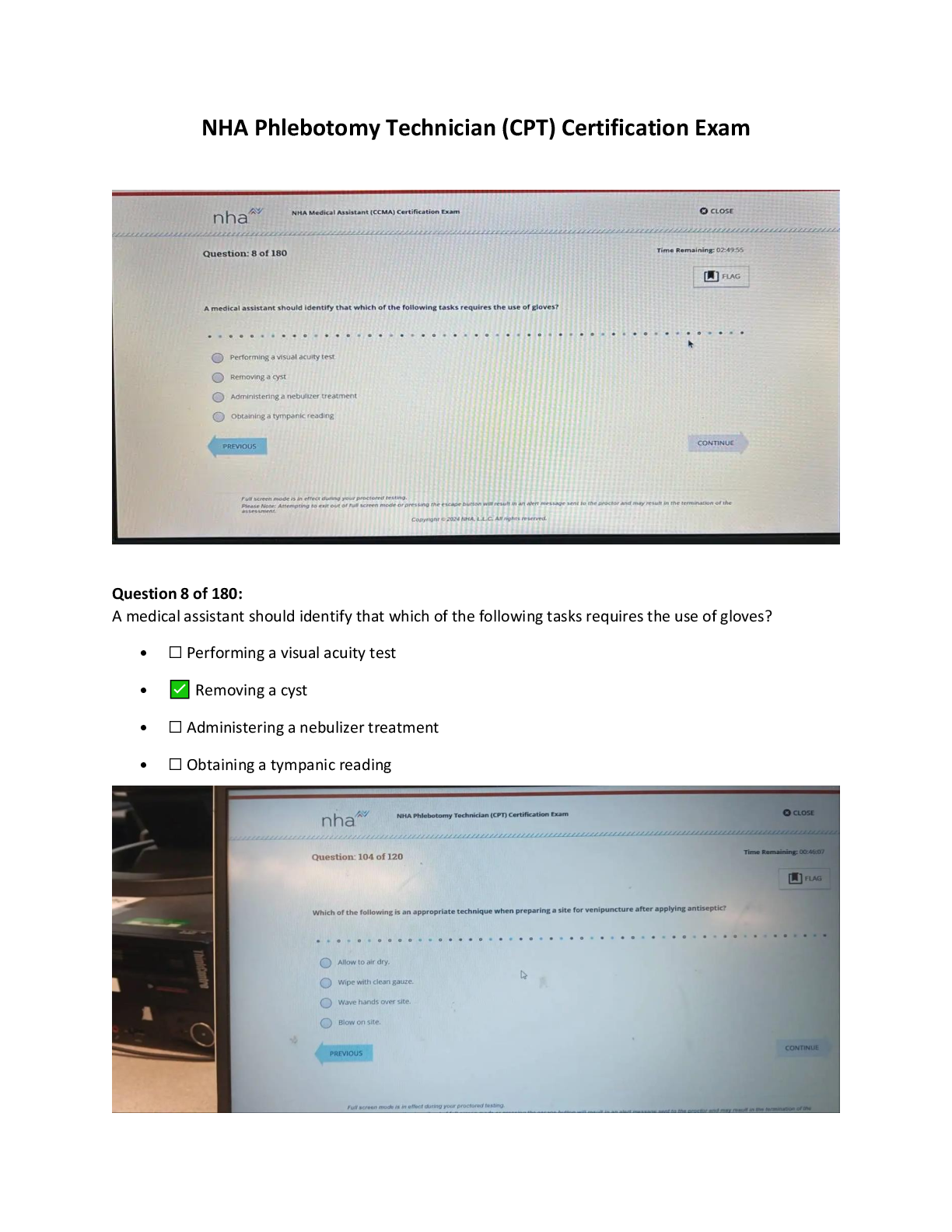
NHA Phlebotomy Technician CPT Certification Exam
$ 20

CASE STUDY #1-ACS-MI Unfolding Reasoning
$ 15

MSN 571 Pharm midterm questions
$ 32

eBook Investigating Human Interaction through Mathematical Analysis The Queue Transform 1st Edition By Kurt T. Brintzenhofe
$ 29
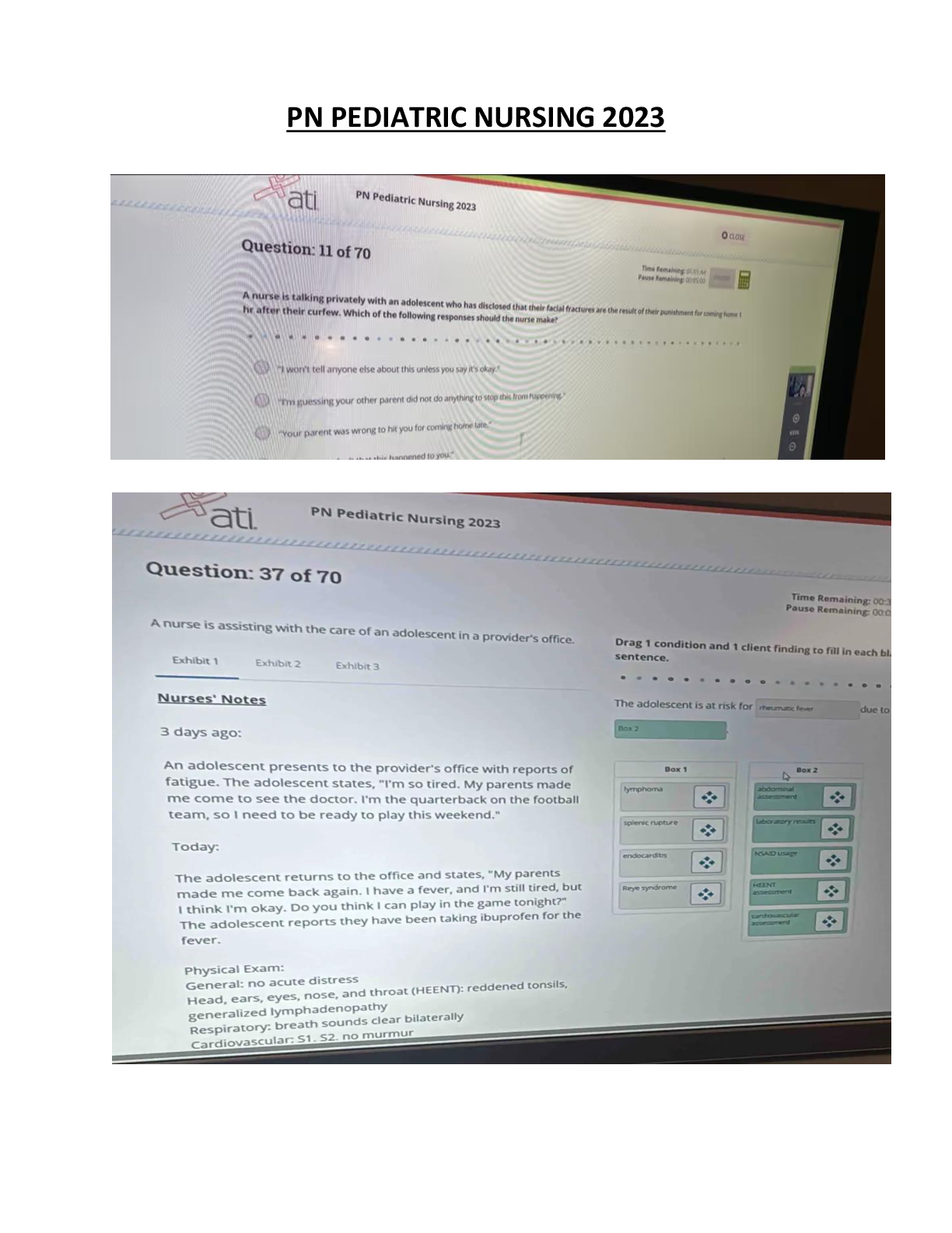
PN Pediatric Nursing Comprehensive Exam Guide
$ 30

ENGLISH 11- FULL PRACTICE QUESTIONS FOR EXAMS
$ 4.5

COMPSCI 70 Discrete Mathematics for Computer Science Homework 3 Table Manipulation and Visualization
$ 11

AQA A - LEVEL PHILOSOPHY PAPER 2023
$ 17

JB Learning Final Exam Quizs With Verified Answers
$ 7.5
.png)
PTCB Practice Exam 2021 Already Passed
$ 10

BURNS NCLEX QUESTIONS LATEST 2024
$ 15

NR 509 Midweek Comprehension Quiz
$ 10.5

ATI Comprehensive proctored exam 2021
$ 15

HESI A2 2020 EXAM.
$ 12

BIOD 171 Portage Learning Exam 3
$ 16

Devoted Health Agent Certification Test 2022 NEW EXAM UPDATE SOLUTION
$ 9

BCIS 3610 Basic Information Systems > BCIS 3610 EXAM 1 (all questions and answers,all correct)
$ 22
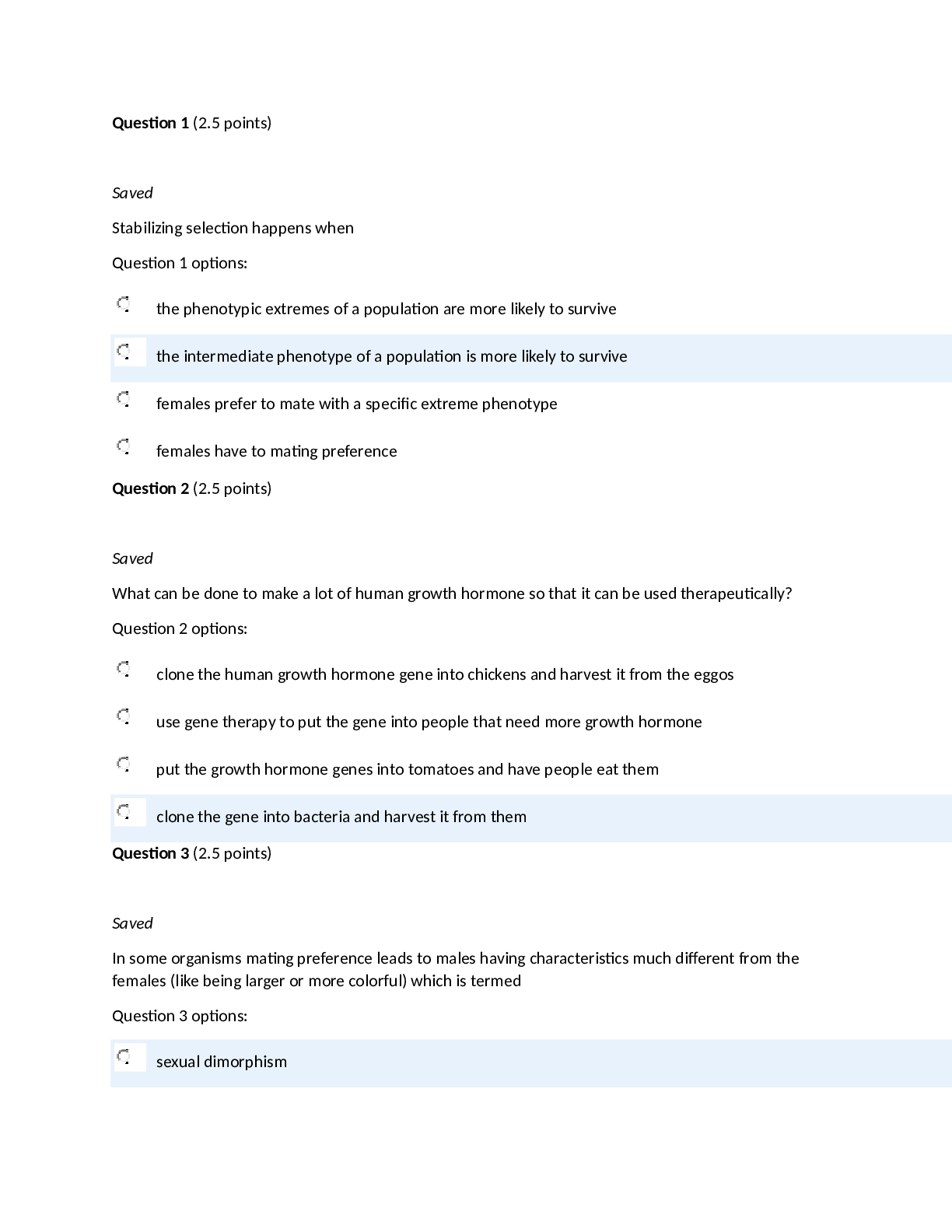
BIOL133_Exam_4_Full_Score_Too_Easy.
$ 12

Using MIS, 12e David Kroenke, Randall Boyle (Test Bank)
$ 25

AWMA Complete Study Questions And Answers
$ 7
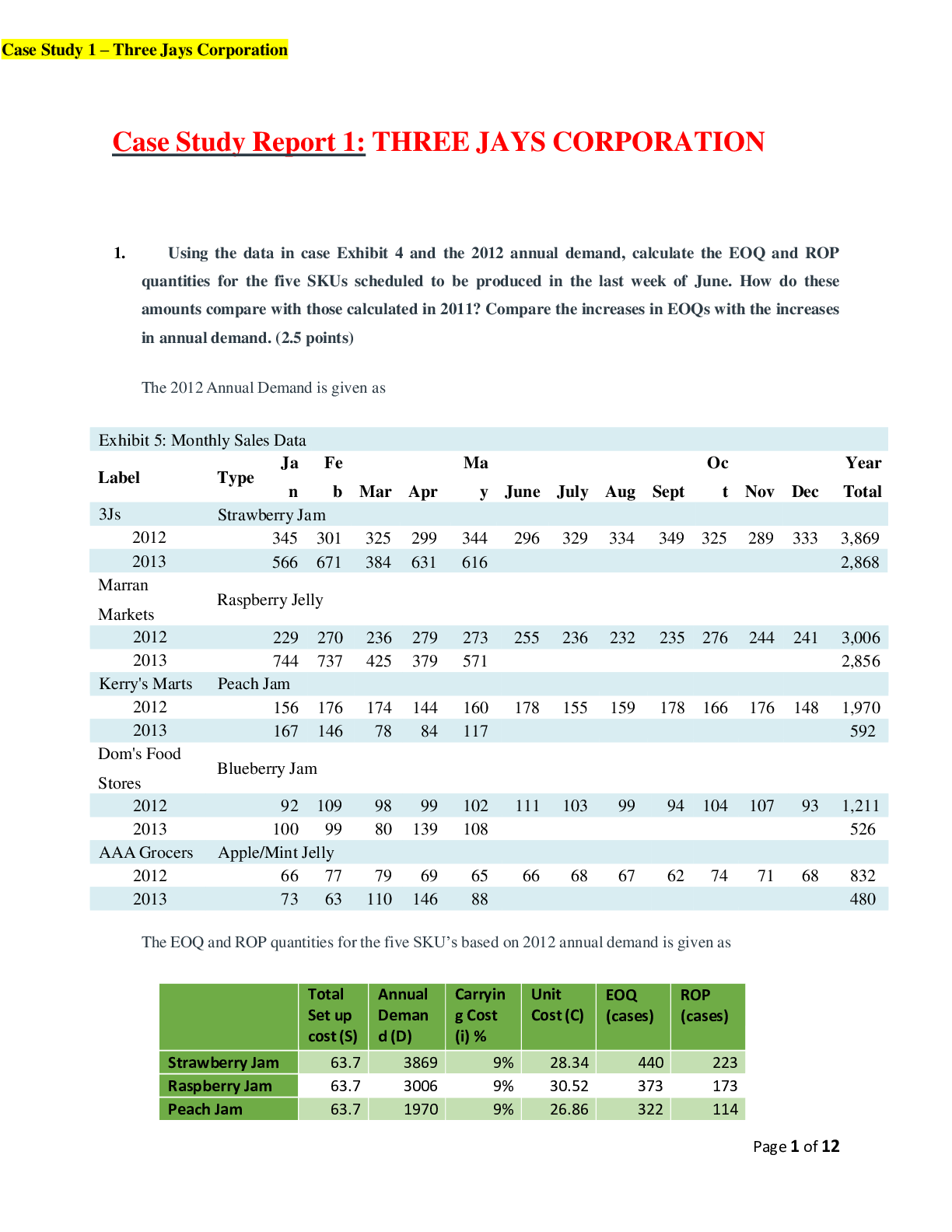
Case Study Report 1: THREE JAYS CORPORATION
$ 11

ATI_ADN_Proctored_Exam_Schedule_
$ 18

NURS 6501N MIDTERM EXAM.
$ 13.5

The Immune System, 5th Edition by Peter Parham – Complete eBook PDF
$ 25

2022 HESI EXIT V1
$ 15

NAB Practice Questions And Answers With Complete Solution