Information Technology > QUESTIONS & ANSWERS > Certified Information Systems Auditor CISA Exam Questions (All)
Certified Information Systems Auditor CISA Exam Questions
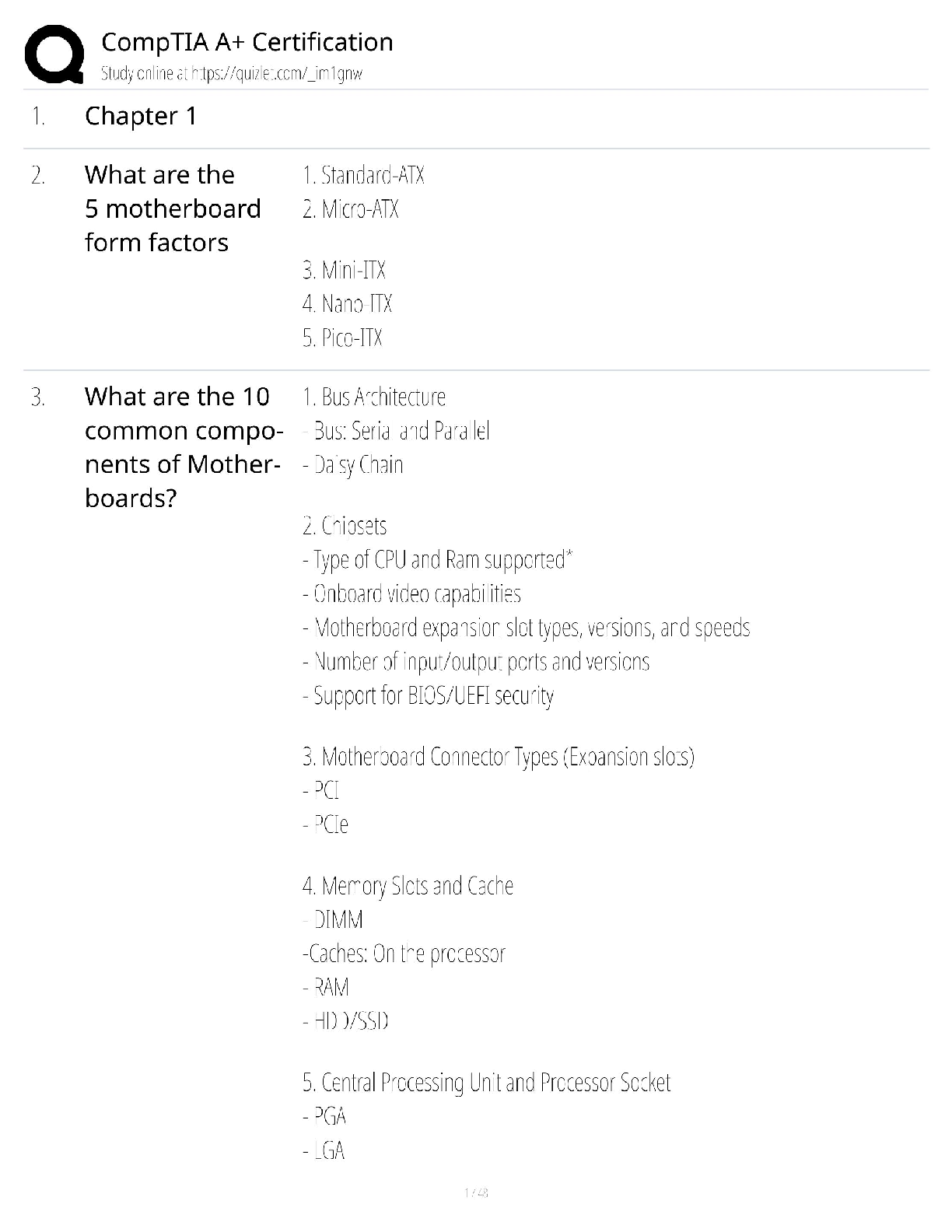
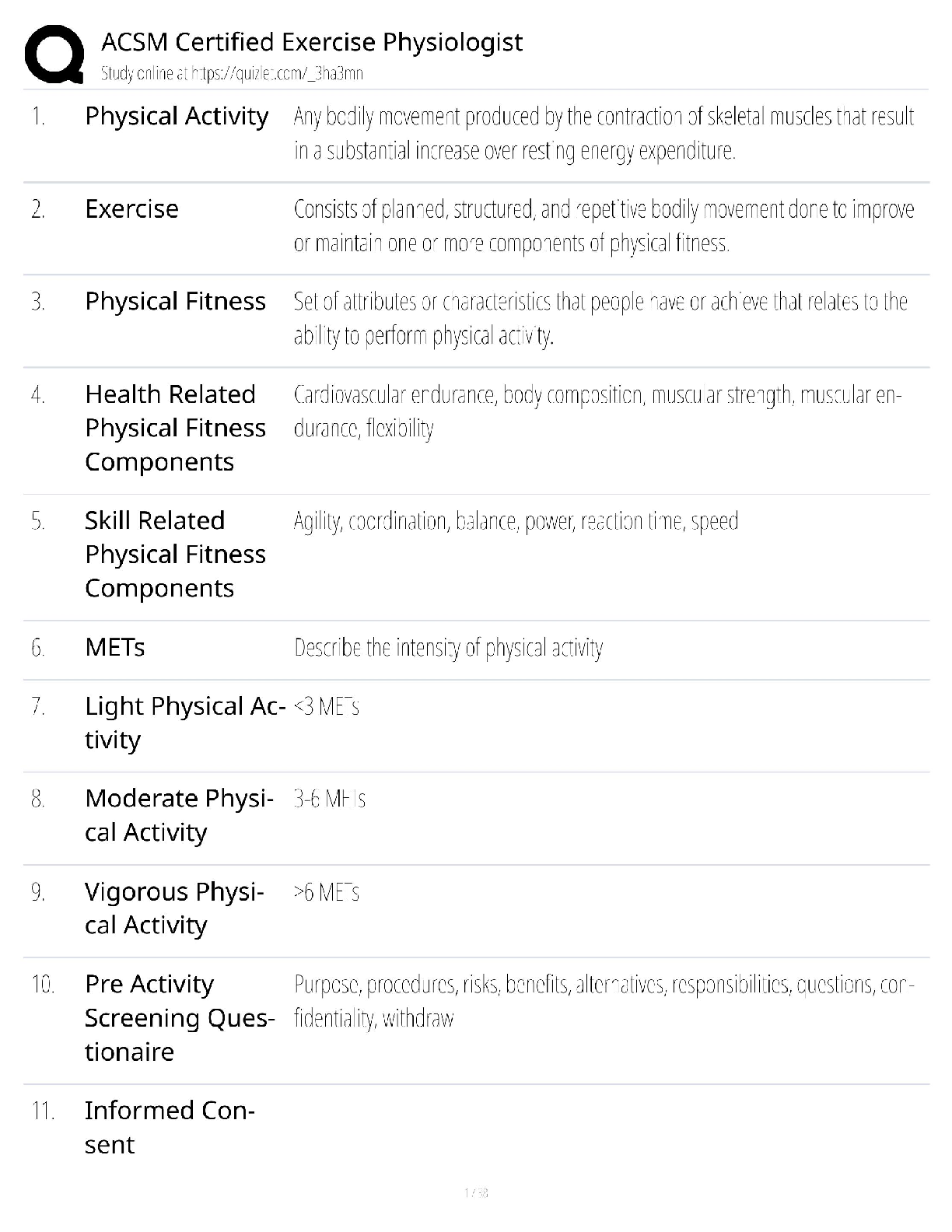
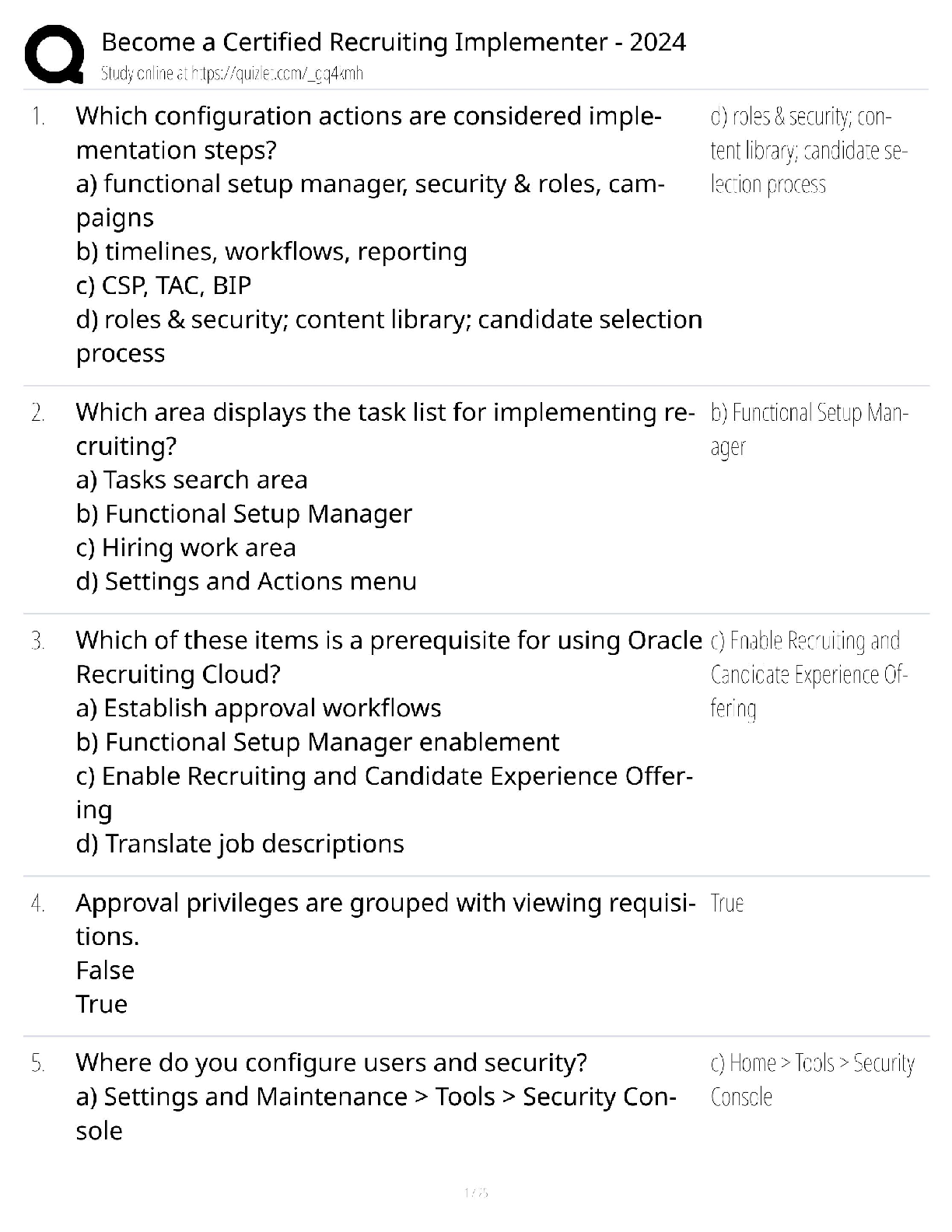
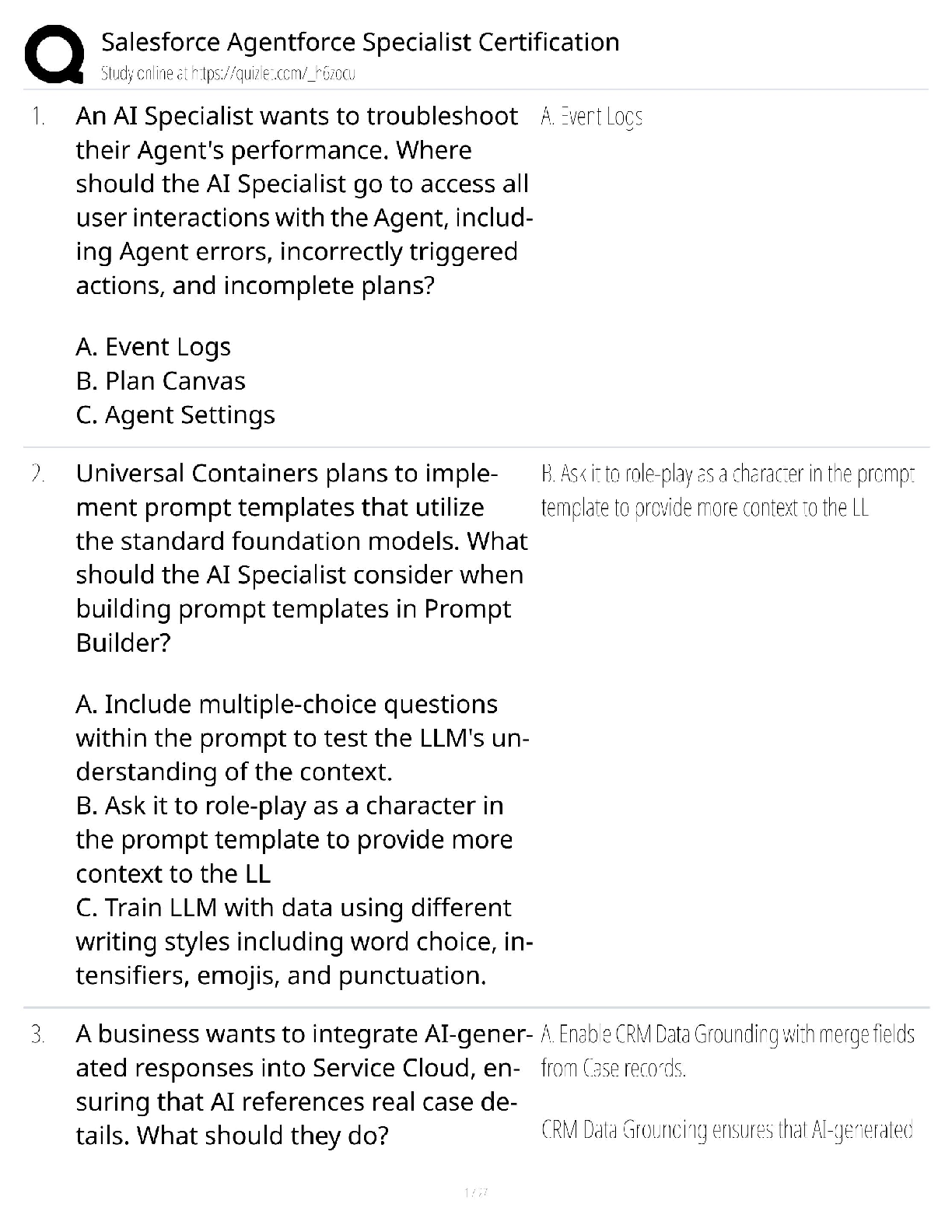
Document Content and Description Below
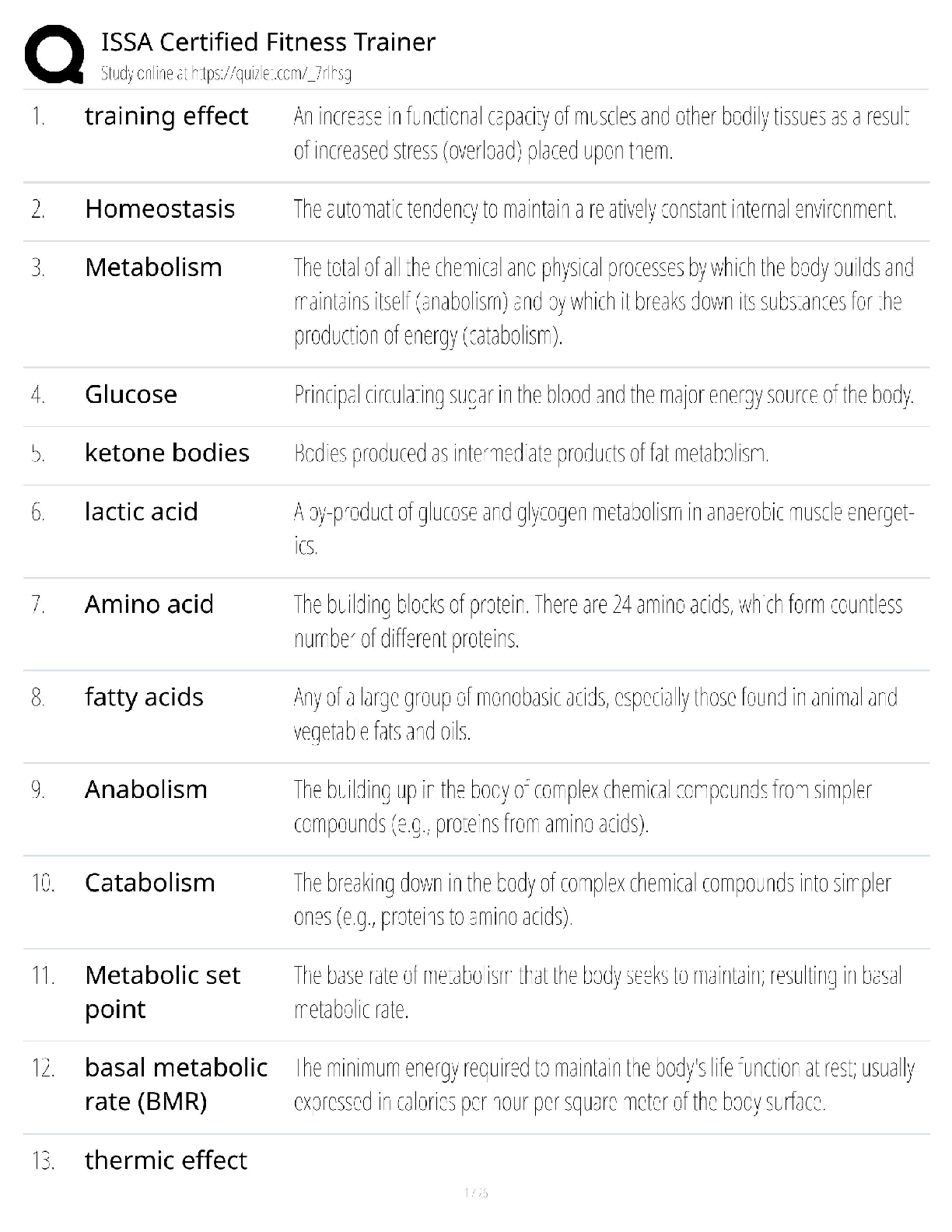
Certified Information Systems Auditor CISA Exam Questions Information system auditors have identified separation of duties in enterprise resource planning (ERP) systems. Which of the following is ... the best way to prevent repetitive configuration from occurring? A. Use a role-based model to grant user access B. Regularly monitor access rights C. Correcting separation of duties D. Reference standard user access matrix - ANS - A. Use a role-based model to grant user access Which of the following should be the most important factor driving a single application availability requirement when developing a disaster recovery plan? A. Confidentiality of data processed by the application B. The criticality of the business processes supported by the application C. Total cost of ownership (TCO) of the application D. Support the application's network bandwidth - ANS - B. The criticality of the business processes supported by the application In order to develop a robust data security program, the first step you should take is: A. Talk to the senior management level of IT. B. Implement monitoring controls. C. Implement data loss prevention measures D. Perform inventory of assets - ANS - D. Perform inventory of assets he advantage of object-oriented system development is that it: A. Suitable for data with complex relationships B. Partition the system as a client server architecture C. Easier to program than procedural languages D. Reduce system documentation requirements - ANS - A. Suitable for data with complex relationships Several portable computers containing customer-sensitive data were stolen from the staff's office because they were unattended. Which of the following is the best advice for an information systems auditor to protect data when it prevents similar incidents from happening again? A. Enhance physical security B. Encrypted disk drive C. Request for dual certification D. Requires the use of a cable lock - ANS - A. Enhance physical security During the physical security audit, the information system auditor received a contactless proximity card that allowed to access to three specific floors of the corporate office building. Which of the following questions should be the biggest concern? A. In the first two days of field work of audit, the proximity card did not work. B. No follow-up was made for unsuccessful attempts to access violations. C. The proximity card incorrectly grants access to the restricted zone D. No escort required during field work. - ANS - C. The proximity card incorrectly grants access to the restricted zone The company's operational procedures require urgent changes to be approved for business within 7 days of the occurrence. The Information Systems Auditor indicates that the manager verifies process compliance by performing a monthly review via uncompleted urgent change. In this case, which one is the biggest risk? A. Audit risk B. Detection risk C. Inherent risk D. Control risk - ANS - C. Inherent risk An information system auditor who is conducting an application development review is attending a meeting of the development team. Which of the following actions the auditor may impair his independence? A. Assist in the development of integrated test equipment on the system. B. Re-execute the test program used by the development team C. Design and implement the user's acceptance test plan. D. Review the results of the system tests performed by the development team. - ANS - C. Design and implement the user's acceptance test plan. The information system auditor found that the accounts payable clerk had direct access to the file after the payment file was generated. The most significant risk to the business is that the money may be: A. Changed. B. Rejected. C. Very late to the customer. D. Copied. - ANS - A. Changed. Which of the following attacks is best suited for intrusion detection systems (IDS) checking? A. Spoofing B. System scanning C. Logic bomb D. Spamming - ANS - B. System scanning A company plans to have automated data feeds from third-party service providers into enterprise data warehousing. Which of the following is the best way to prevent receiving bad data? A. Implement business rules to reject invalid data B. Purchase data cleanup tools from reputable suppliers C. Appointment of data quality representatives within the company D. Get the error code for the data feed indicating the failure - ANS - A. Implement business rules to reject invalid data Which of the following is most helpful for information systems auditors when evaluating control effectiveness? A. Have interview communication with the management level B. Results of control test C. Control self-assessment D. Control matrix - ANS - B. Results of control test Due to cost constraints, the company postponed the replacement date for supporting core application hardware. Which of the following is the biggest risk? A. The final replacement cost may be higher B. System availability may be affected C. Maintenance costs may increase D. May not be upgraded in the future - ANS - B. System availability may be affected The information systems auditor is reviewing the maintenance contract for a core banking application. Which of the following can minimize the impact of bankruptcy of application vendors? A. Service Level Agreement (SLA) B. Liability Agreement C. Third Party Hosting Agreement D. Force Majeure Agreement - ANS - C. Third Party Hosting Agreement Which of the following is the most appropriate indicator of the effectiveness of change management? A. The interval between the change and the document material update B. Number of accidents caused by the change C. Number of system software changes D. The interval between configuration changes and record updates - ANS - B. Number of accidents caused by the change [Show More]
Last updated: 3 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 11, 2022
Number of pages
5
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 11, 2022
Downloads
0
Views
84










.png)