Information Technology > QUESTIONS & ANSWERS > System Administration and IT Infrastructure Service Latest 2022 (All)
System Administration and IT Infrastructure Service Latest 2022
Document Content and Description Below
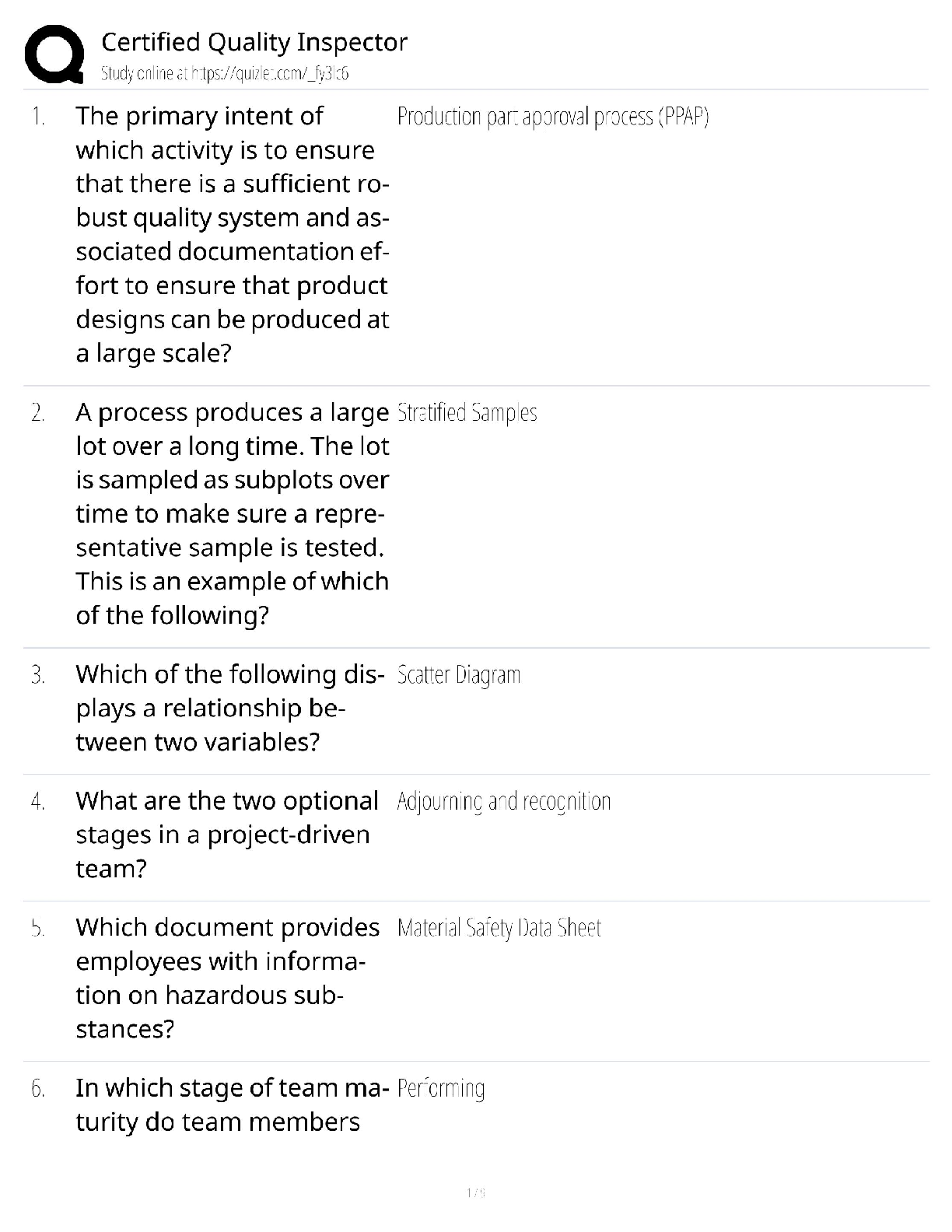
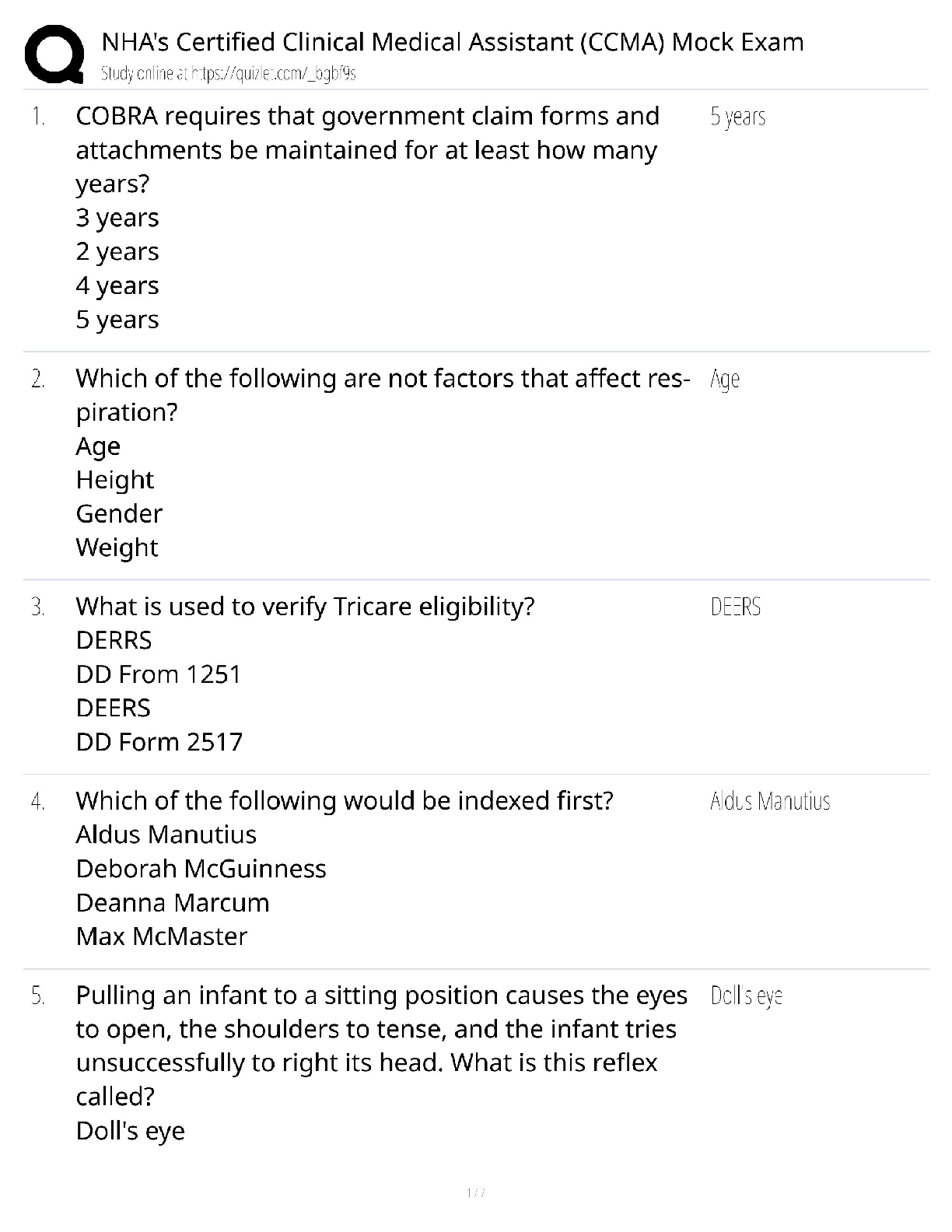
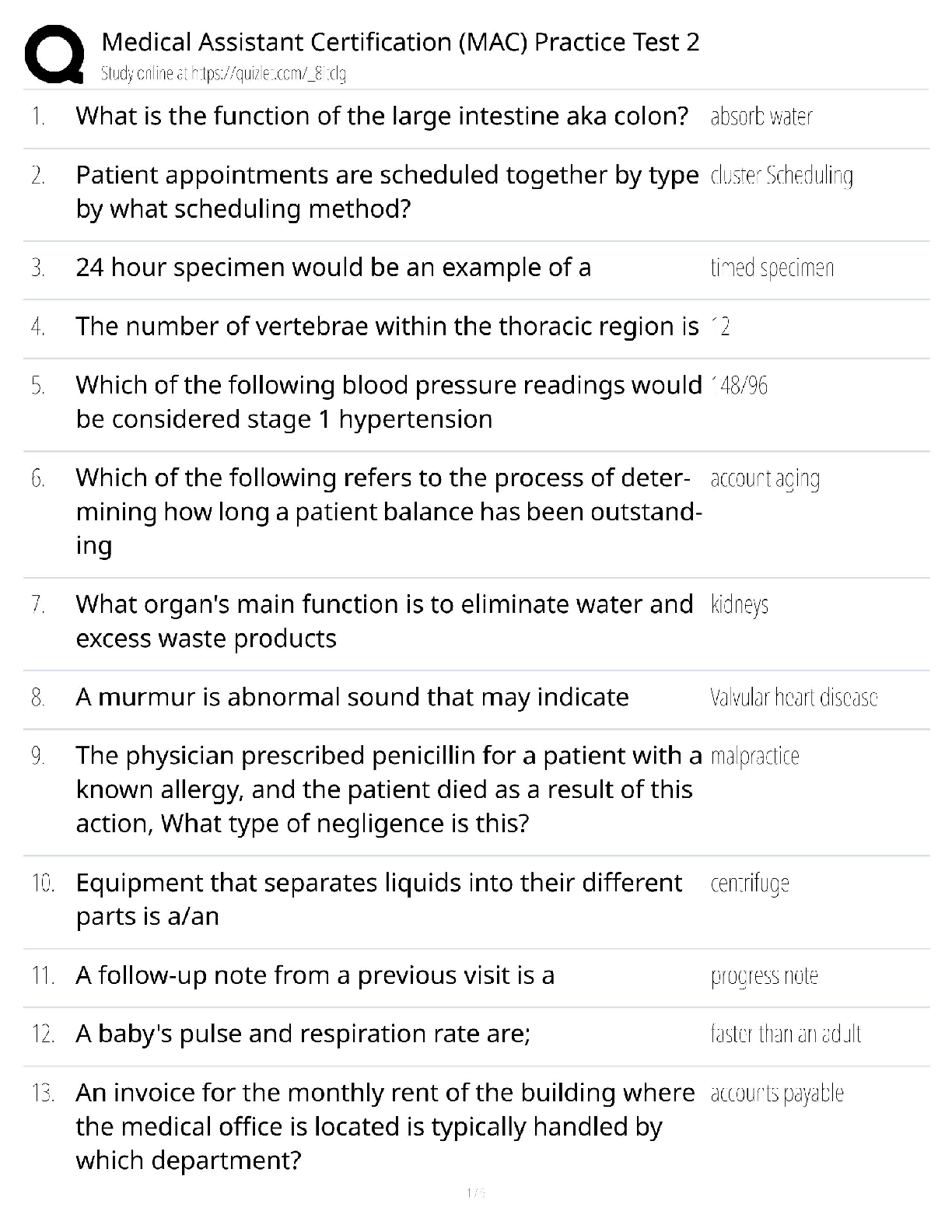
Contains a lookup service that provides mapping between network resources and their network addresses ✔✔Directory Server Active Directory stores a ____________________________ of the password. � ... ��✔One-way cryptographic hash This method of authentication can employ the help of security protocols like TLS. Requires the client and the directory server to authenticate using some method. One of the most common methods is using Kerberos. ✔✔SASL Authentication. Passwords can be easily turned into a ______________, but _____________ cant be easily turned back into passwords. ✔✔Hash/Hashes In most organizations, access to computer and network resources is based on ✔✔Your role in the organization If there's more then one person who can _______________ using the same username and password, then __________________ becomes difficult or even impossible ✔✔Authenticate Auditing A network authentication protocol that's used to authenticate user identity, secure the transfer of user credentials, and more. ✔✔Kerberos If someone forgets there password. Someone with Sysadmin responsibilities, may be authorized to _____________ their password for them. ✔✔Reset [Show More]
Last updated: 3 years ago
Preview 1 out of 7 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$5.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 12, 2022
Number of pages
7
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 12, 2022
Downloads
0
Views
115

.png)

.png)
.png)
.png)
.png)
.png)