OPSEC Fundamentals Final Exam
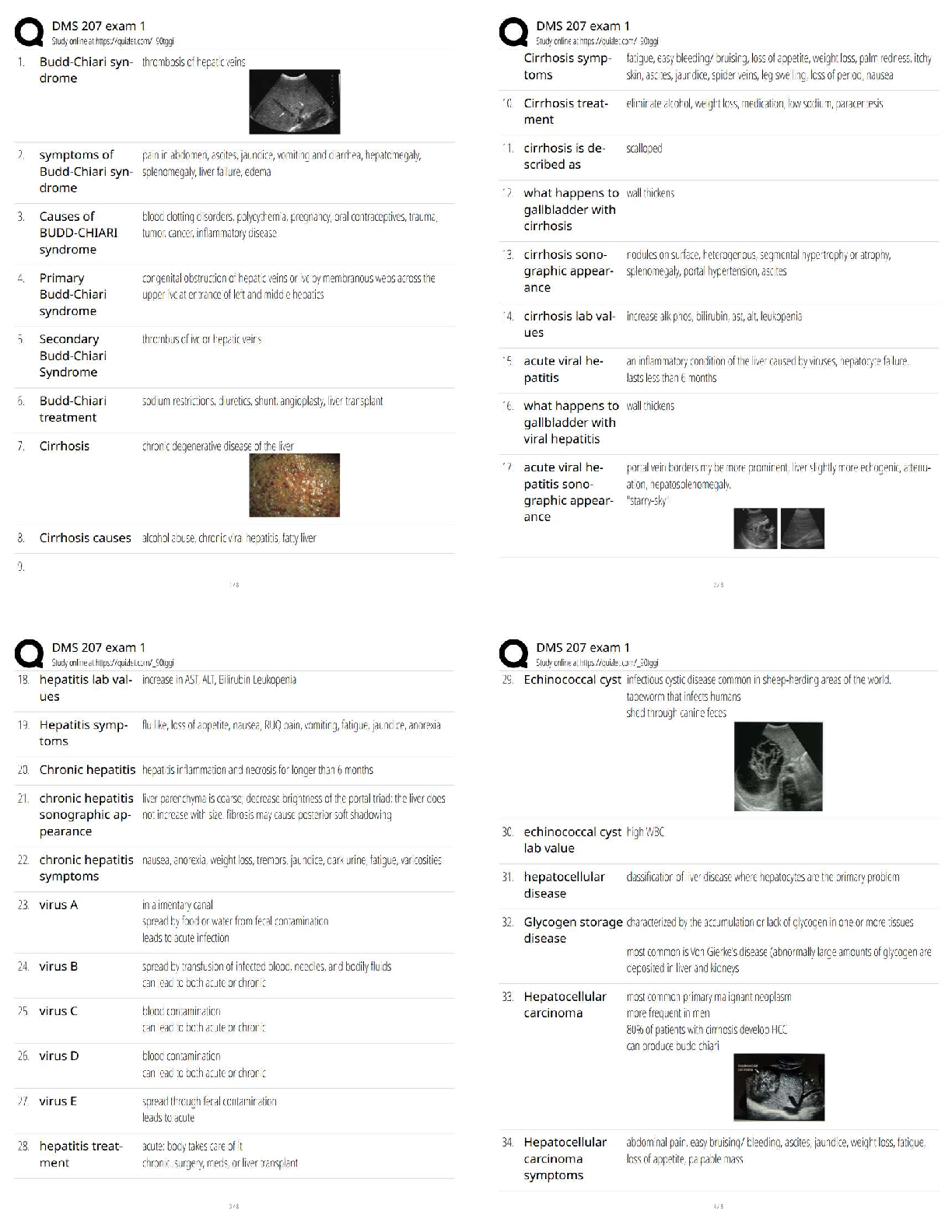
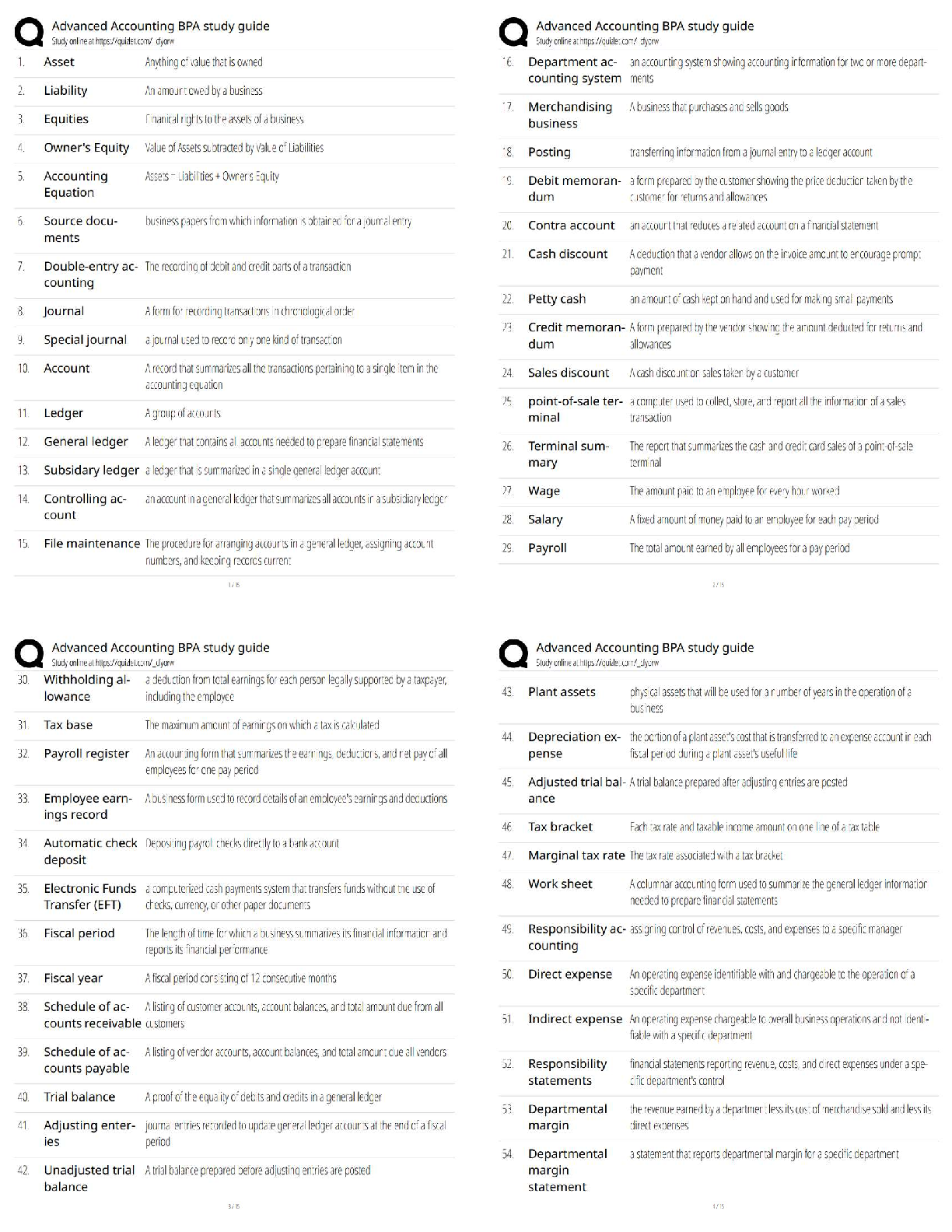
An advantage of incorporating OPSEC principles into the planning stage of any operation is that
it: - ANS - Provides for early detection of OPSEC problems
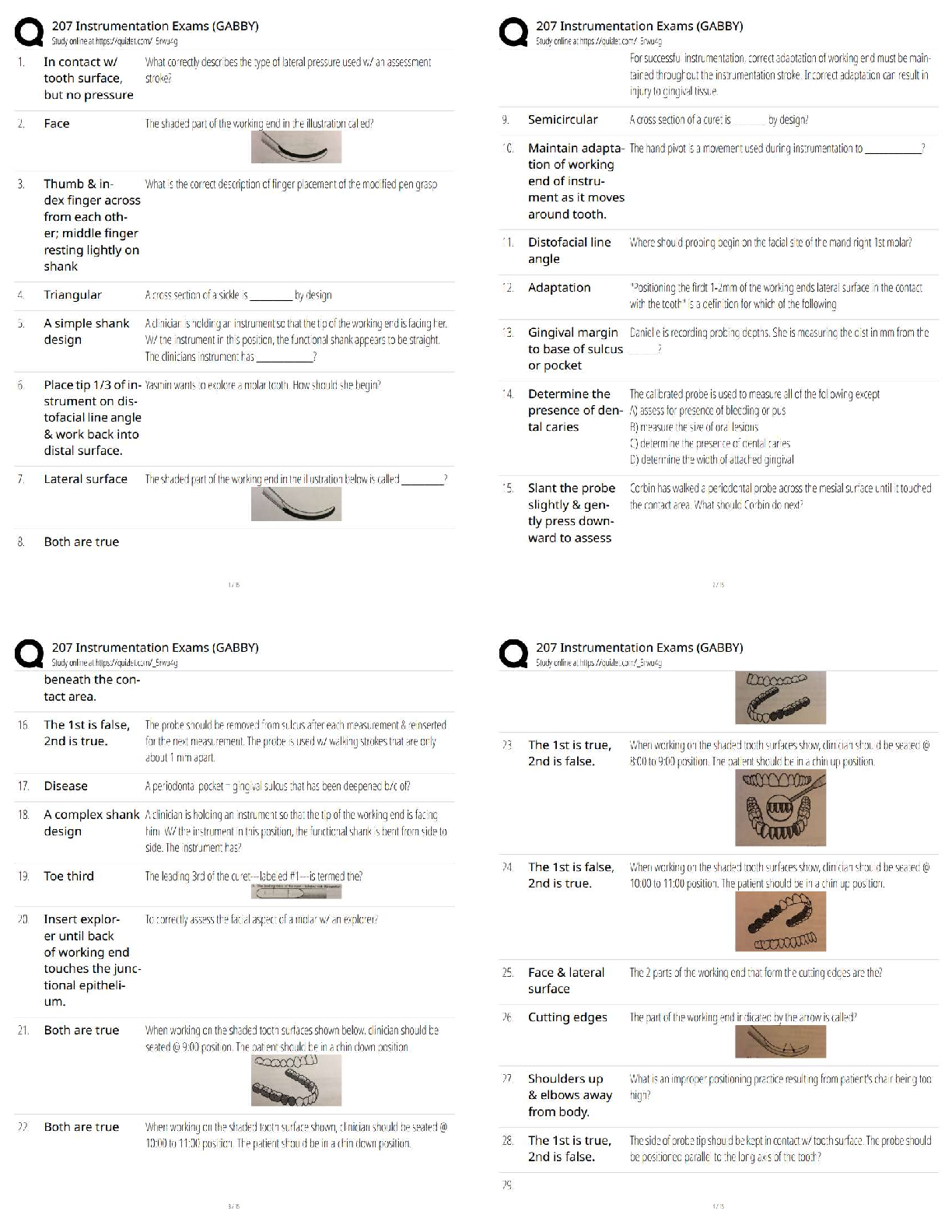
NSDD298, signed by President Ron
...
OPSEC Fundamentals Final Exam
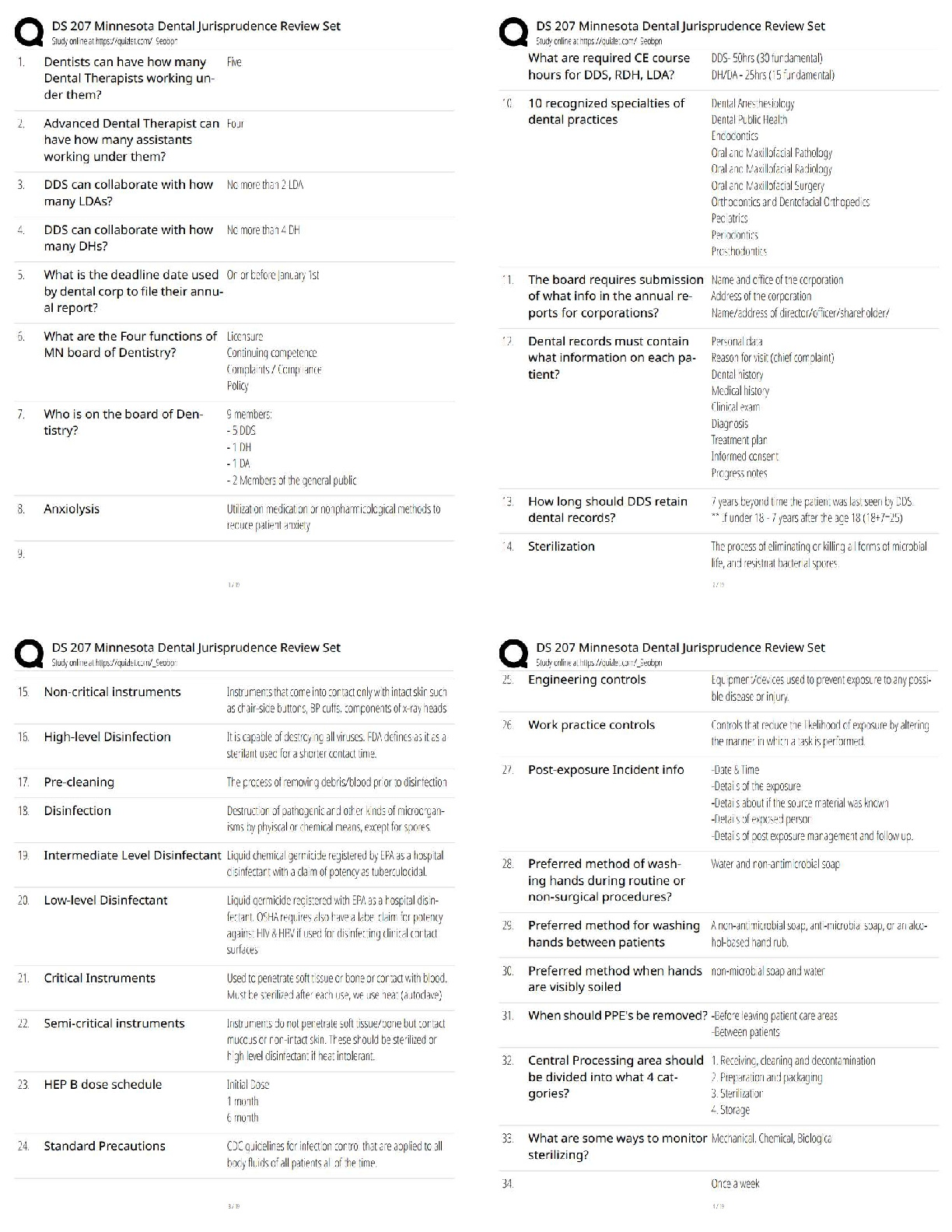
An advantage of incorporating OPSEC principles into the planning stage of any operation is that
it: - ANS - Provides for early detection of OPSEC problems
NSDD298, signed by President Ronald Reagan in 1988, directed which organizations to
establish OPSEC programs? - ANS - All executive departments and agencies with national
security missions
An adversary is anyone with whom you do not wish to share your critical information. - ANS -
True
Which step in the OPSEC process requires you to look at your operation through the eyes of the
adversary? - ANS - Analyze vulnerabilities
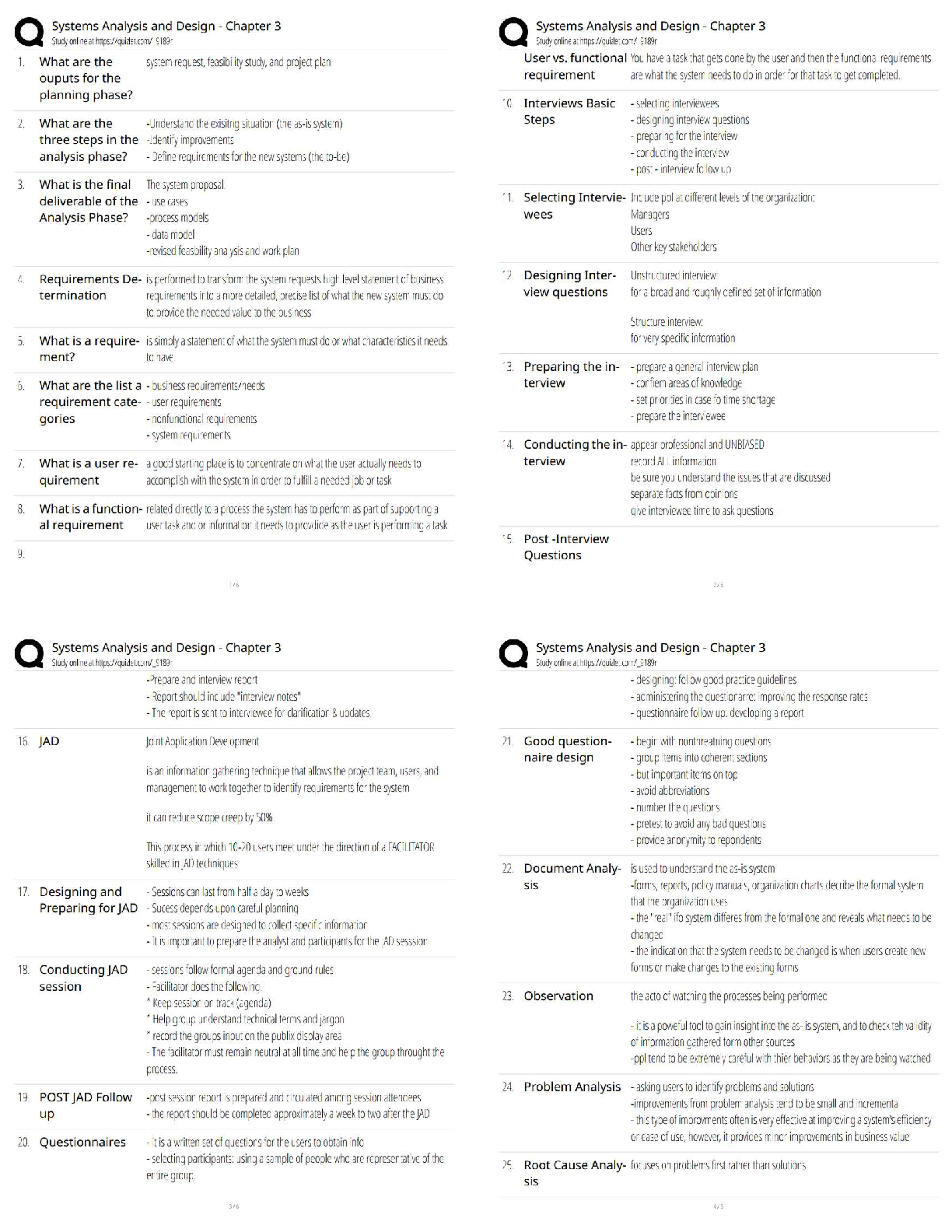
Which of the following should be taken into consideration when determining which critical
information should be protected? (more than one may apply) - ANS -
An adversary that is capable of collecting and exploiting information and has expressed the
intent to do so is considered a: - ANS - Threat
The value of OPSEC lies in its ability to: - ANS - Complement traditional security by
augmenting security practices already in place
Detectable activities or clues that can be pieced together by an adversary to compromise your
operations are called: - ANS - Indicators
A countermeasure is anything that effectively reduces an adversary's ability to exploit our
vulnerabilities. - ANS - True
The development of a countermeasure focuses directly on the: - ANS - Vulnerability it is
designed to protect
_____ is the "so what" factor of risk assessment. - ANS -
Which of the following countermeasures would likely be considered the most effective across all
organizations? - ANS - Awareness training
Lack of proper awareness training is an example of which of the following: - ANS -
Vulnerability
Risk is a function of the: - ANS - Threat, vulnerability, and impact
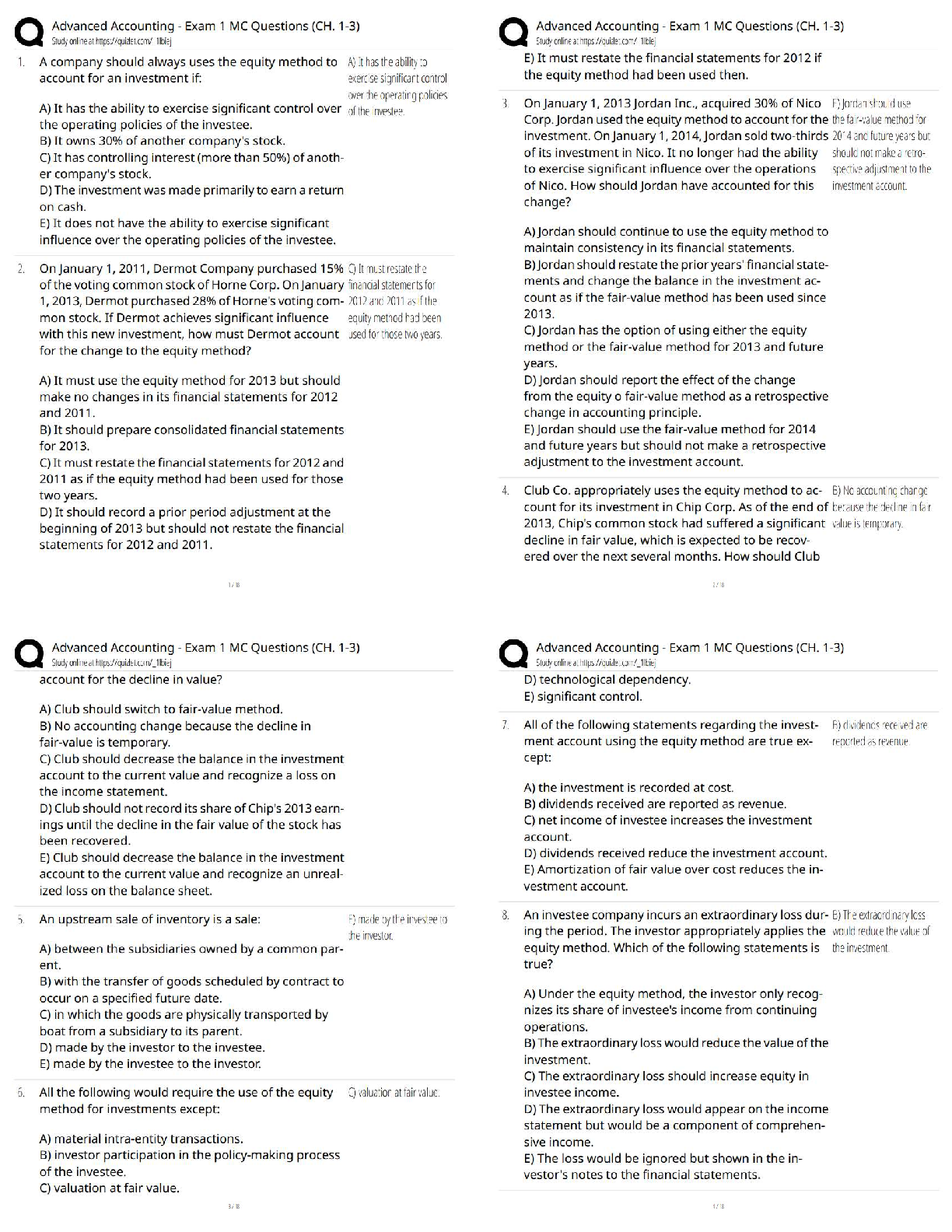
An advantage of integrating OPSEC principles in your day-to-day operations is that it: - ANS -
Makes OPSEC principles second nature to your employees
Which of the following common vulnerabilities associated with family members usually involve
the sharing of too many details? (more than one may apply) - ANS - Social media, trash and
public conversations
Stereotypes, patterns, and predictable actions are all types of: - ANS - Indicators
Which of the following is defined as a weakness in your operation? - ANS - Vulnerability
The probability that an adversary will exploit a weakness in your operation, tempered by the
impact to your mission, is defined as the: - ANS - Risk
Which step in the OPSEC process is a decision-making step because it helps the decision maker
prioritize and decide whether or not to assign a countermeasure? - ANS - Assess risk
[Show More]
.png)













.png)