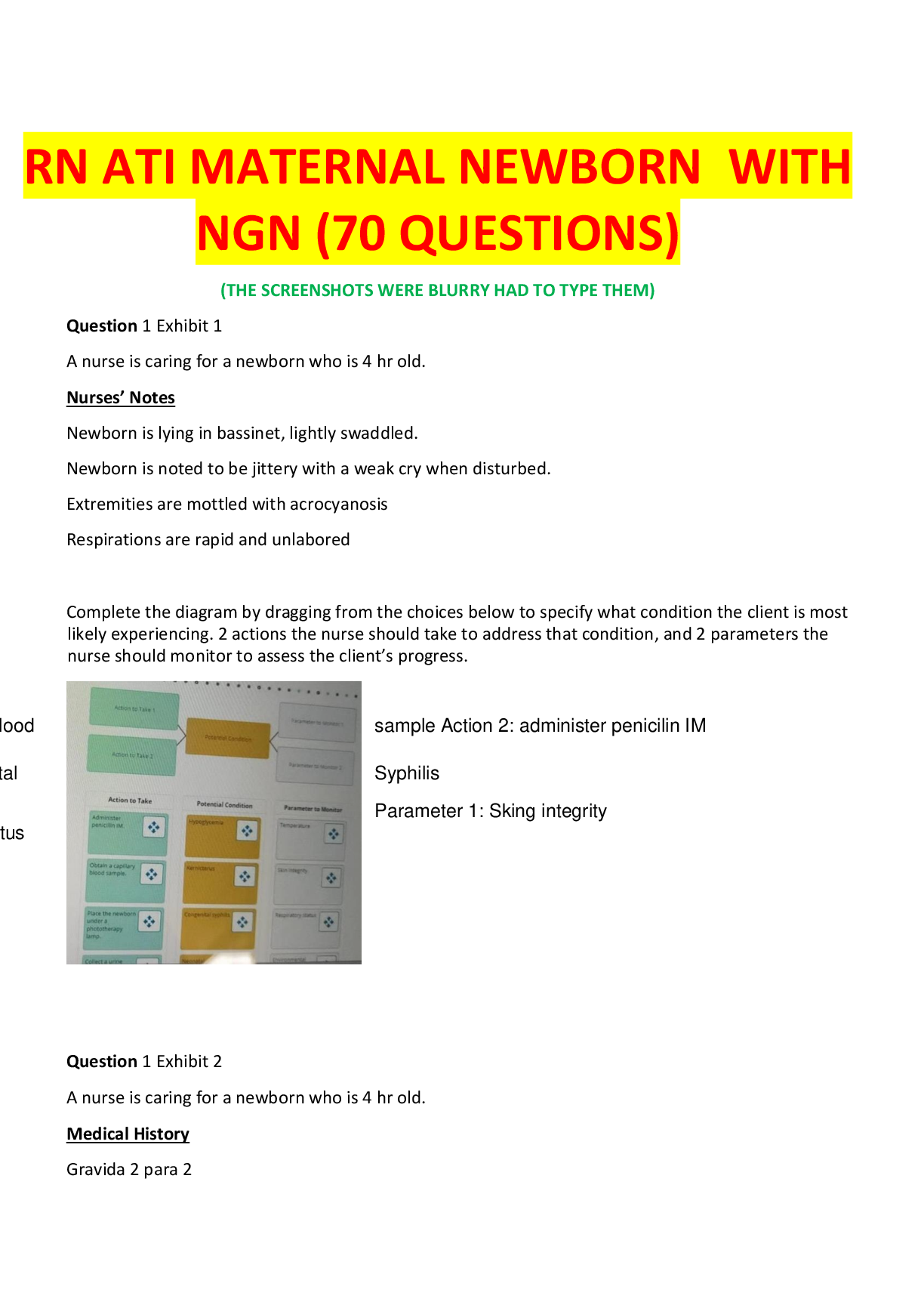
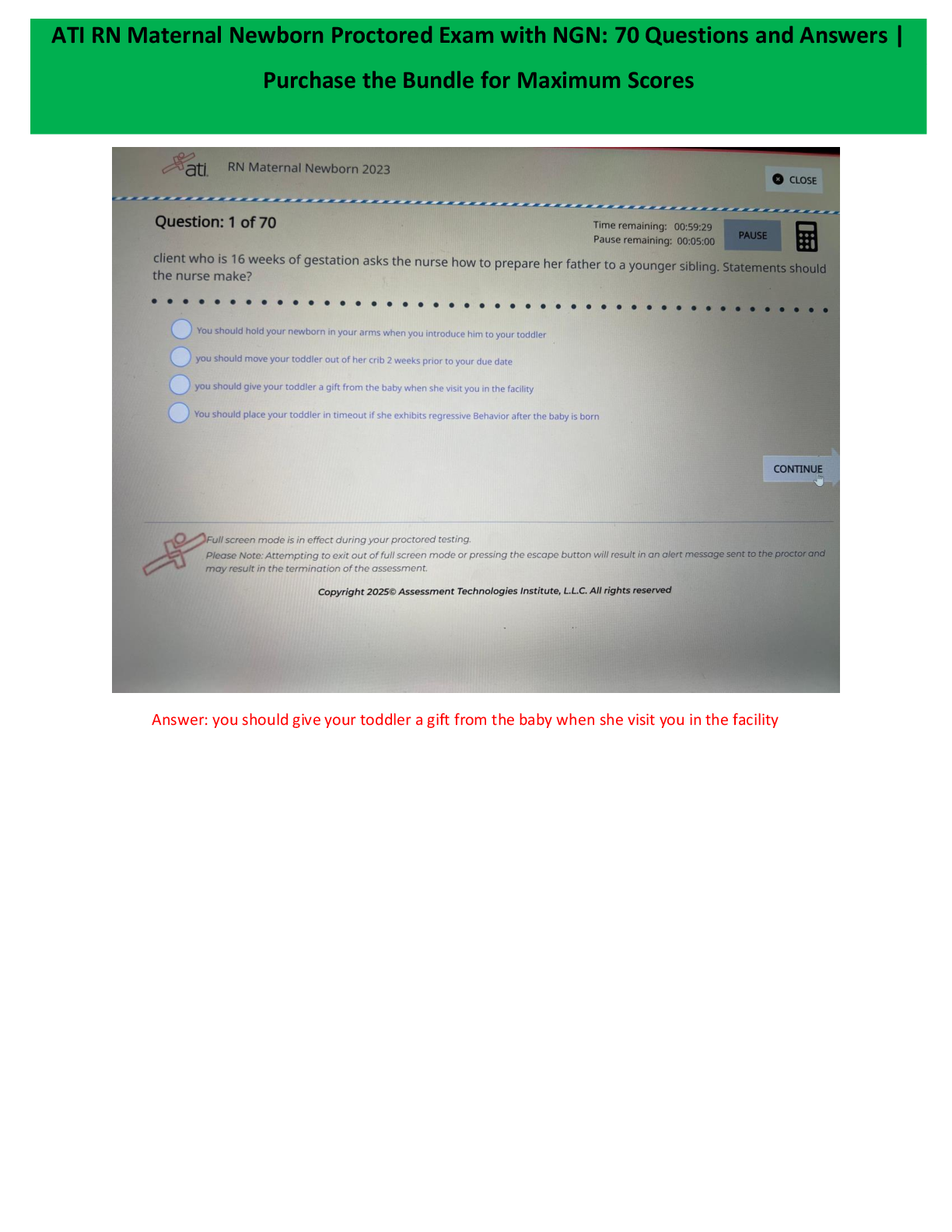
What is a business case? - ANSWER Defines a business need and describes a way to meet that goal
What is a biased sample? - ANSWER A measurement excluding relevant elements of data or "cherry picking" to get desired re
...
What is a business case? - ANSWER Defines a business need and describes a way to meet that goal
What is a biased sample? - ANSWER A measurement excluding relevant elements of data or "cherry picking" to get desired result.
What is intentional deceit? - ANSWER Purposely excluding and manipulating numbers to mislead
What are requirements of PCI-DSS? - ANSWER PCI-DSS stands for Payment Card Industry Data Security Standard. Its requirements include:
Firewall:
-default settings not allowed
-protect cardholder data
-encrypt transmissions
-antivirus
-secure systems and apps
Access Control:
-unique ID's
-physical access restricted
-monitor and track access
-test security system(s)
-infosec policy
4 reasons an organization or privacy professional should use a Privacy Framework. - ANSWER 1. Reduce risk
2. Avoid data loss
3. Sustain organization's market value
4. Comply with laws, regulations & industry standards
What is a privacy workshop? - ANSWER A meeting where privacy program stakeholders are informed about legal and market expectations concerning privacy; Q&A; and setting a baseline for privacy knowledge.
What is APEC and how is it relevant to privacy? - ANSWER APEC stands for Asia Pacific Economic Cooperation.
It is a privacy framework to enable safe data transfers meant to benefit consumers, business and government.
What is the ISTPA? - ANSWER It stands for the International Security Trust & Privacy Alliance.
It is an industry organization focused on creating actionable frameworks for businesses implementing data protection policies.
What are the metric taxonomies? Where do these taxonomies originate? - ANSWER -Objective/Subjective
-Qualitative/Quantitative
-IT metrics/Quantitative measurement
-Static/Dynamic (static= doesn't change over time)
-Absolute/Relative (absolute= not dependent on other)
-Direct/Indirect
They originate from NIST IR 7564
What framework did the US publish in 2012? - ANSWER The Consumer Bill of Rights (Obama)
White House Publication
What is the AICPA/CICA framework? - ANSWER Privacy Maturity Model (PMM).
Created by the American Institute of CPAs and the Canadian Institute of Accountants with help from ISACA, this guide is based on Generally Accepted Privacy Principles (GAPP) and aims to assist organizations in strengthening their privacy policies, procedures and practices.
What are the elements of the Metric Lifecycle? - ANSWER 1. IDENTIFY intended audience
2. DEFINE data sources, data owners, data access
3. SELECT the actual metrics (based on audience and resources)
4. COLLECT the data; who, what when, where how, why
5. ANALYZE metrics/data; ROI
What are the following regulatory standards:
1. PCI-DSS
2. NAI
3. DMA
4. CARU - ANSWER 1. Payment Card Industry Data Security Standard (cc payments)
2. Network Advertising Initiative (online ads)
3. Digital Marketing Association (interactive mktg)
4. Children's Advertising Review Unit (ads to kids under 12)
What is Australia's information privacy law and what office enforces it? - ANSWER APP- Australian Privacy Principles (replaced Information Privacy Principles 2014)
Enforced by the Office of the Australian Information Commissioner
Who are the privacy regulatory authorities in:
1. Japan
2. USA - ANSWER 1. Public Management Ministry
2. FTC (3 bureaus):
-Bureau of Consumer Protection...protects against unfair and deceptive trade practices
-Bureau of Competition...investigates and enforces against anti-trust, price fixing, etc
-Bureau of Economics...studies economic effects of regulation/FTC rule making
What is a metric target? - ANSWER The threshold for a satisfactory rating of measurement (which may change over time)
Example: Target = 50% implementation by week 2
Target = 100% implementation by week 4
What are the areas in an organization which need effective controls to enforce policies? - ANSWER -IS/IT
-Training & Communications
-Internal Audit Group
-Procurement
What is XACML? - ANSWER It is a PET and stands for Extensible Access Control Marketing Language.
Request and response style language for determining access privileges (and routine for discovering policy).
What are the 4 Privacy Regulatory Models? - ANSWER 1. Comprehensive- official oversight and enforcement with PD procedures
2. Sectoral- PD procedures governed by sector (Health, Education, PCI)
3. Co-Regulatory- industry develops enforcement standards that a privacy agency oversees
4. Self Regulatory- organizations abide by a code of practice developed by industry standards bodies
What are PET's? - ANSWER Performance Enhancing Technologies.
Technology standards developed specifically for privacy:
1. choice control
2. quality of information
3. accessing and processing of PI
Examples of PET's:
-Platform for Privacy Preferences (P3P)
-Enterprise Privacy Authority Language (EPAL)
-Extensible Access Control Makeup Language (XACML)
-Security Assertion Makeup Language (SAML)
What are the governance models for privacy team structure? - ANSWER 1. Centralized- single source of authority for & directions (CPO), streamlined, efficient
2. Local- bottom to top info flow, lower tiers make decisions that are well informed, some duplication of effort
3. Hybrid- main individual or office issues directives; local entities fulfill & support policies & directives; local entities report to regional privacy manager who reports to CPO or main office. Better for large organizations
What are the elements of Data Inventory? - ANSWER -Types of info
-Volume of repository
-Countries where data is stored
-Owner of repository
-Use of information
-Nature of repository
-Countries where data is accessed
-International transfers
-Location of repository
What is the SMART Methodology? - ANSWER It is a method to select metrics and stipulates metrics be:
Specific- targeted area for improvement; clear definition
Manageable- quantifiable; allows for measurable progress
Actionable- reveals problems which can be fixed
Relevant- pertains to the context of organization business
Timely- trending allows for comparison over time
What should you do with training programs to increase effectiveness and keep trainees engaged? - ANSWER Change up the training methods and tools
What is overgeneralization? - ANSWER Inferences that are made from limited data set applied to make overly broad generalizations
Disadvantages of the 3 regulatory models? - ANSWER 1. Comprehensive-varying degree of DPA power & resource allocation; may lead to inadequate funding & protection
2. Sectoral- oversight through new legislation; difficult to ID all regulations; technology relevancy
3. Self Regulatory- inadequate enforcement
What is the privacy ROI calculation? - ANSWER Return On Investment
ROI = Benefits - Cost / Cost
Regarding improper use of metrics, what are:
1. Faulty assumptions
2. Selective use - ANSWER 1. Conclusion based on occurrence of events without substantiated evidence to correlate the evidence.
2. Specific subset of information extrapolated from larger data set which leads to invalid/incorrect conclusions
Who are the audience member categories for metrics reporting and who are the comprised of? - ANSWER Primary: CPO/legal officer, CIO, CISO, program mgr, info system owner, InfoSec officer, users & mgrs
Secondary: CFO, HR, Inspector General, HIPPA security officials, training organizations
Tertiary: sponsors, stockholders, external watchdogs
What is the regulatory authority in:
1. Canada
2. Hong Kong - ANSWER 1. Office of Privacy Commissioner
2. Office of Privacy Commissioner for Personal Data
What should a privacy policy document? - ANSWER -Practices, principles, policies
-Breach and incident
-Roles and responsibilities
-Complaint process (internal & external) w/ dedicated email address
What is massaging the numbers? - ANSWER Manipulating measurements to create the appearance of success
What is the first step in creating a company privacy program? - ANSWER Identify stakeholders and internal partnerships; have informal one-on-one; obtain sponsorship; develop internal partnerships
Proposal Phase - ANSWER The phase of a project in which the associated metrics are introduced.
How do you communicate a privacy framework to internal and external stakeholders? - ANSWER -Meetings (in person and over phone)
-Formal training and awareness:
-Classroom
-Web
-CBT
-Newsletters and email
In analyzing metrics data what are:
1. Trending/ time series
2. Cyclical component - ANSWER 1. Pattern in information viewed over time
2. Occurrences in a regular time interval
What are ISO 27001 & 27002? - ANSWER Standards specification for:
27001- InfoSec management systems
27002- IT security technologies; code of practice for security controls
What is "rationalized" approach in Data Governance Strategy? - ANSWER A solution that addressed the requirements common to most laws and regulations
Example: almost all DP laws require notice, choice, consent, access, etc.
Does ISO 27001 require taking a layered approach to effective security? - ANSWER No
What is the Liberty Alliance SAML? - ANSWER It is a PET and stands for Security Assertion Makeup Language. It is an industry consortium specification for single sign on account linking and global logout in online e-business environments.
What is P3P? - ANSWER P3P or Platform for Privacy Preferences
PET and machine readable format, helping express a site's data management practices in an automated fashion.
What are the improper uses of metrics? - ANSWER -Intentional deceit
-Faulty assumption
-Average (not median or mode)
-Selective use
-Semi-attachment
-Massaging the numbers
-Overgeneralization
-Biased Sample
What is a GAP analysis? - ANSWER The review of current systems, infrastructures, services to see whether they are meeting an organizations privacy objectives and documenting gaps that are categorized in order of risk magnitude to the organization.
What is EPAL? - ANSWER Enterprise Privacy Authorization Language is a PET and language for writing enterprise privacy policies to govern data handling practices in IT systems according to fine grain positive and negative authorization rights.
What is the OECD? - ANSWER Organization for Economic Cooperation & Development
A voluntary framework (most widely used principles) and basis for EU GDPR. Also provides for data transfers.
What is the CSA privacy code? - ANSWER Became the national privacy standard in 1996 in Canada and formed the basis for PIPEDA. Based on OECD guidelines to which Canada was signatory.
How are stakeholders involved in a privacy mission statement? - ANSWER First, the privacy mission statement must have consensus approval from stakeholders. Second, it communicates the privacy stance to all stakeholders.
What assets do you apply ROI to? - ANSWER -Physical
-Personnel
-IT
-Operational Management
Why are ROI's useful? What are some hidden economic considerations? - ANSWER Useful for:
-obtaining funding and justification within the organization
-measuring how worthwhile privacy initiatives have been
Hidden economic consideration include:
-cost of producing and collecting PD
-advantage to competitor(s) if PD destroyed or used
-loss of public confidence
-cost of info released or destroyed
-Value of PD on open market
How might an organization obtain professional competency? - ANSWER Endorse efforts to keep privacy professionals current and up to date through:
-certifications
-training
-seminars and conferences
Where is PD likely to be found in an organization? - ANSWER HR, IT, Marketing, Finance, CRM
What is a privacy framework? - ANSWER An implementation roadmap that provides the structure (or checklists) to guide a privacy professional through privacy management and determines privacy relevant decisions for an organization
What is ISO 17799/BS 7799 - ANSWER Standard for information security practices containing controls for assuring data quality and security for PI.
In regards to improper use of metrics, what are:
1. Well chosen average
2. Semi-attachment - ANSWER 1. where mean is selected instead of more accurate median or mode
2. Results when an individual is unable to prove their point; semi attachment may result with the exclusion of elements of a measurement when conveying results
What is a privacy mission statement? - ANSWER A concise statement that provides what the organization does and stands for in regards to privacy.
What is business resilience and how is it measured? - ANSWER The ability to adopt to disruptions and maintain continuous business operations.
It is measured through business resiliency metrics:
-system outages
-database uptime
-general availability measurements
What are the regulatory authorities in the EU called? - ANSWER Data Protection Authority (DPA)
[Show More]