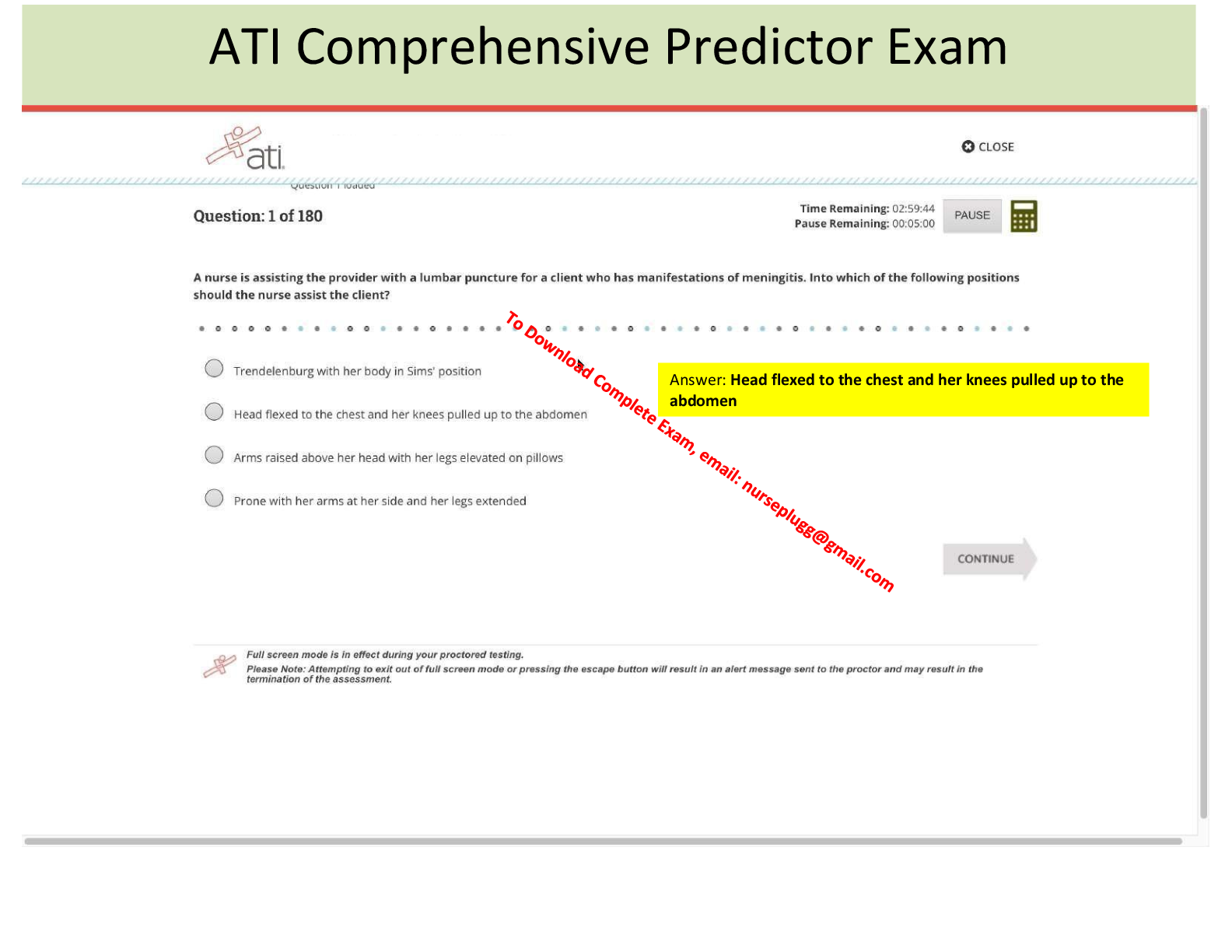
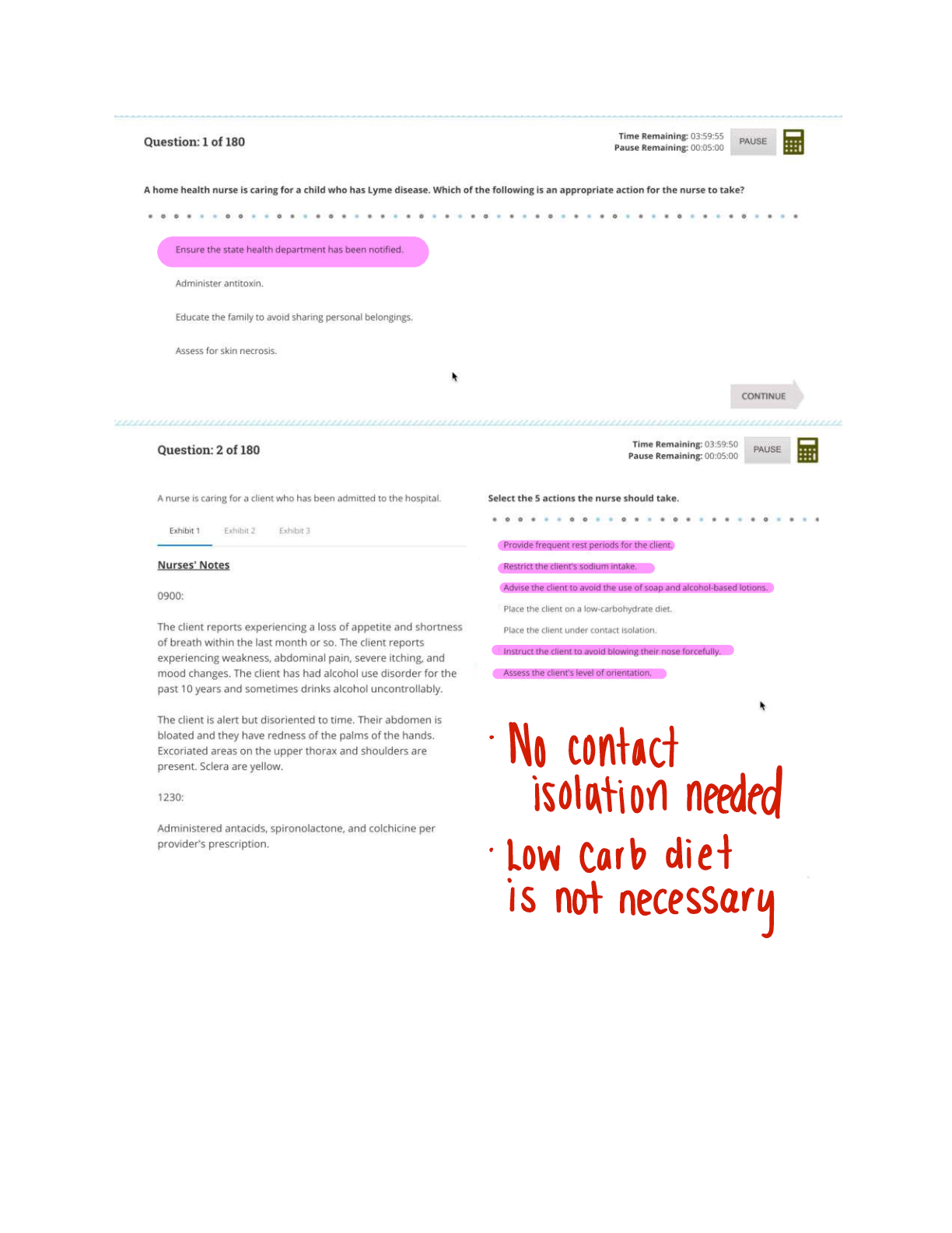
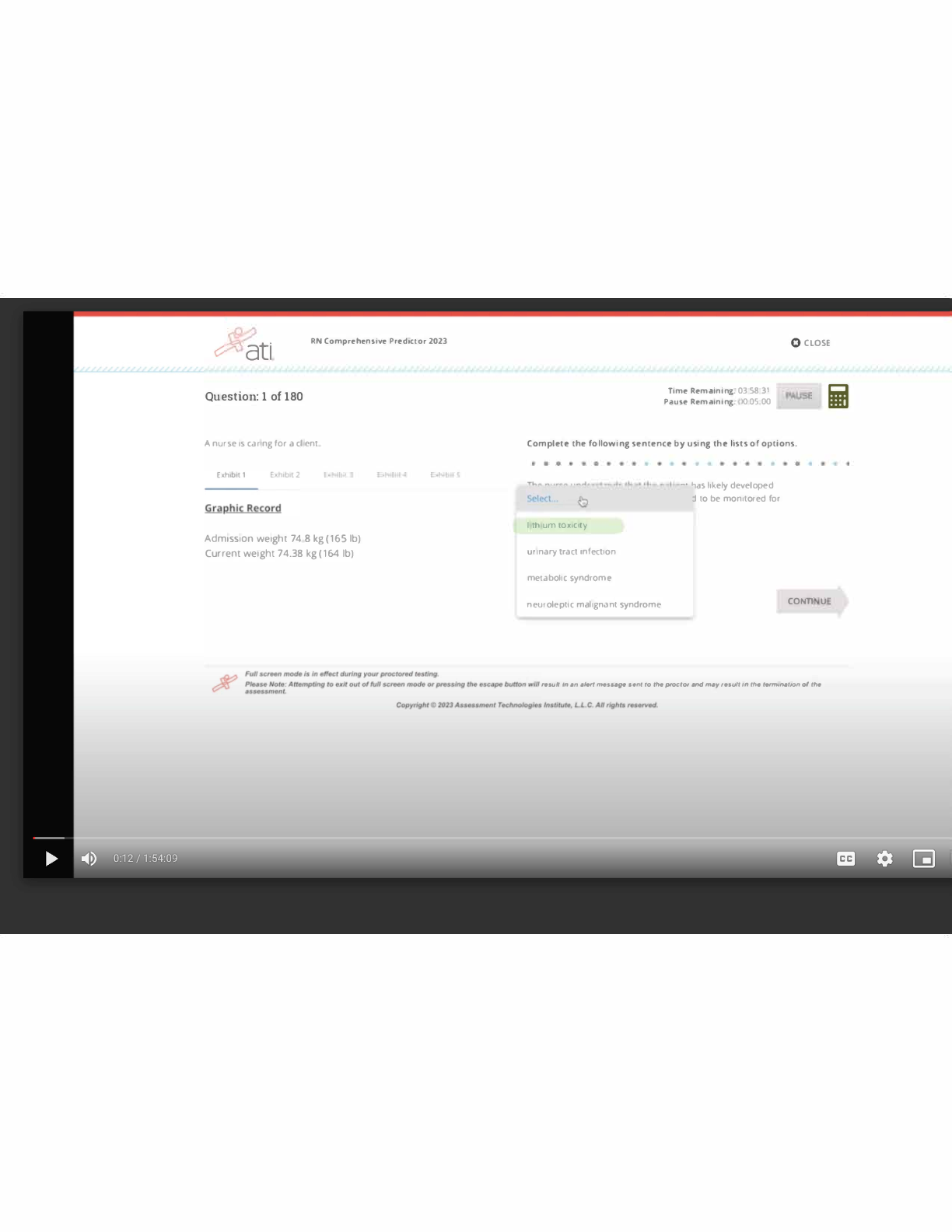
First users were the engineers who built and programmed computers, then employees who had received specialized training were users, and now today, anyone and everyone can be a user. - Evolution of Users
Sends files ov
...
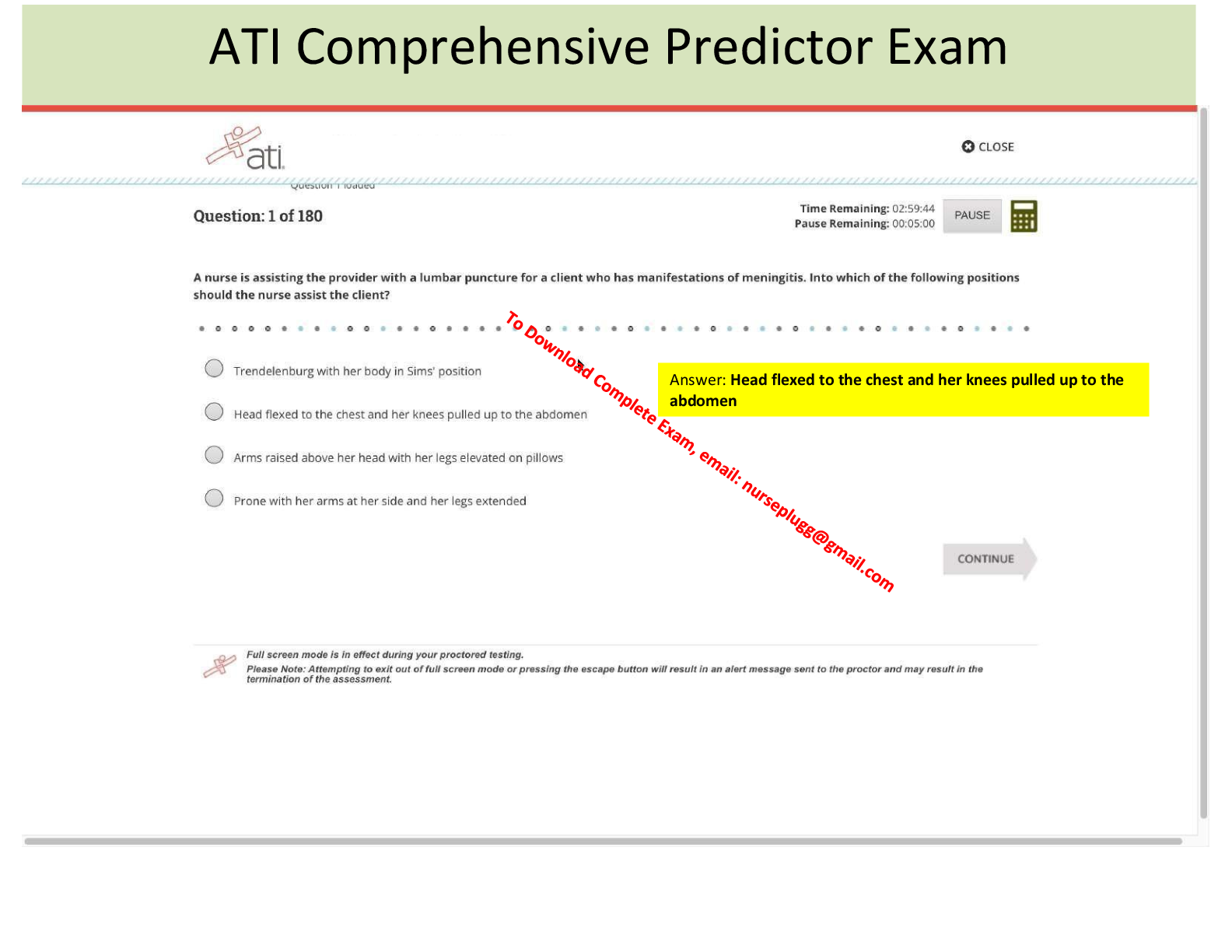
First users were the engineers who built and programmed computers, then employees who had received specialized training were users, and now today, anyone and everyone can be a user. - Evolution of Users
Sends files over the network at the request of clients. Responds over LAN, within one location/site. Support both application software and data files. - FILE SERVER
Turns a user-friendly domain name, like Google.com, into an Internet Protocol (IP) address like ((( 70.42.251.42 ))) that computers use to identify each other on the network. - Domain Name Server (DNS)
Uses TWO KEYS a public and private key for performing encryption and decryption - Public Key Encryption
PROVING you are who you say you are which can be done by: what you know, what you have! - Authentication
TIER WHERE THE USER interface for the system is developed; SHIELDS THE USER from the underlying logic of the systems as well as the underlying data structures - Presentation Tier
SYSTEMS DEPLOYMENT Steps 1. System Conversion 2. Final Documentation 3. End User Training - System Deployment
CONNECTS MULTIPLES networks together; can be used to directly connect computers to a network; will relay messages to computers with APPROPRIATE IP ADDRESS - ROUTER
Requires that data is KEPT secure so that they are not accidentally provided or obtained by unauthorized users - Confidentiality
Protecting EVERY LAYER that SURROUNDS ((( DATA ))) - Defense in Depth
Can take on DIFFERENT FORMS depending on the complexity of the application; in certain instances, it is AN ACTUAL OBJECT that is an ACTUAL IMPLEMENTATION of the application - THE MODEL
Creates a subset of the data by reducing the data from multiple dimensions to one dimension - Slicing Data
The technology used in creating, maintaining, and making information accessible. - Information Technology
In charge of all aspects of the COMPUTER NETWORKS - Network Administrator
Focuses on the design, development, and support of DATABASE MANAGEMENT systems (DBMSs). - Database Administrator
Installs, configures, maintains, secures, and troubleshoots web severs - Web Administrator
Processed data. - Information
INFORMATION THAT HAS BEEN PUT TO USE information placed into a context. Refined information such that the user of the knowledge is able to call forth only relevant portions of information when needed. - Knowledge in DIKW
Provides a social setting to knowledge; AN UNDERSTANDING OF THE ((( WHY ))) Can only come by having BOTH KNOWLEDGE and EXPERIENCE - WISDOM
The INPUT Processing, OUTPUT, STORAGE Cycle - I.P.O.S.
Raw data is organized or structured for usefulness. - PROCESSED DATA
Information is output so user can see results. - OUTPUT DATA
Processed information is stored for permanent record. - STORAGE
A collection of components that work together to meet the needs of the user; typically : CATEGORIZED AS EITHER HARDWARE, SOFTWARE, NETWORKS AND USERS - COMPUTER SYSTEM
Physical components of a computer system which include the system unit and its components and peripheral devices; TANGIBLE ASPECTS OF THE COMPUTER - HARDWARE
A collection of computers and resources CONNECTED by various media so that they can COMMUNICATE WITH EACH OTHER. - NETWORK
Systems Software and Applications Software - SOFTWARE CATEGORIES
RULES provided by WHICH NETWORKS communicate with each other - IP PROTOCOL
STORES the programs BEING EXECUTED and the data they are using. - COMPUTER MEMORY
[Show More]