Computer Networking > EXAMs > Certified Ethical Hacker 312-50 (1-25) (All)
Certified Ethical Hacker 312-50 (1-25)
Document Content and Description Below
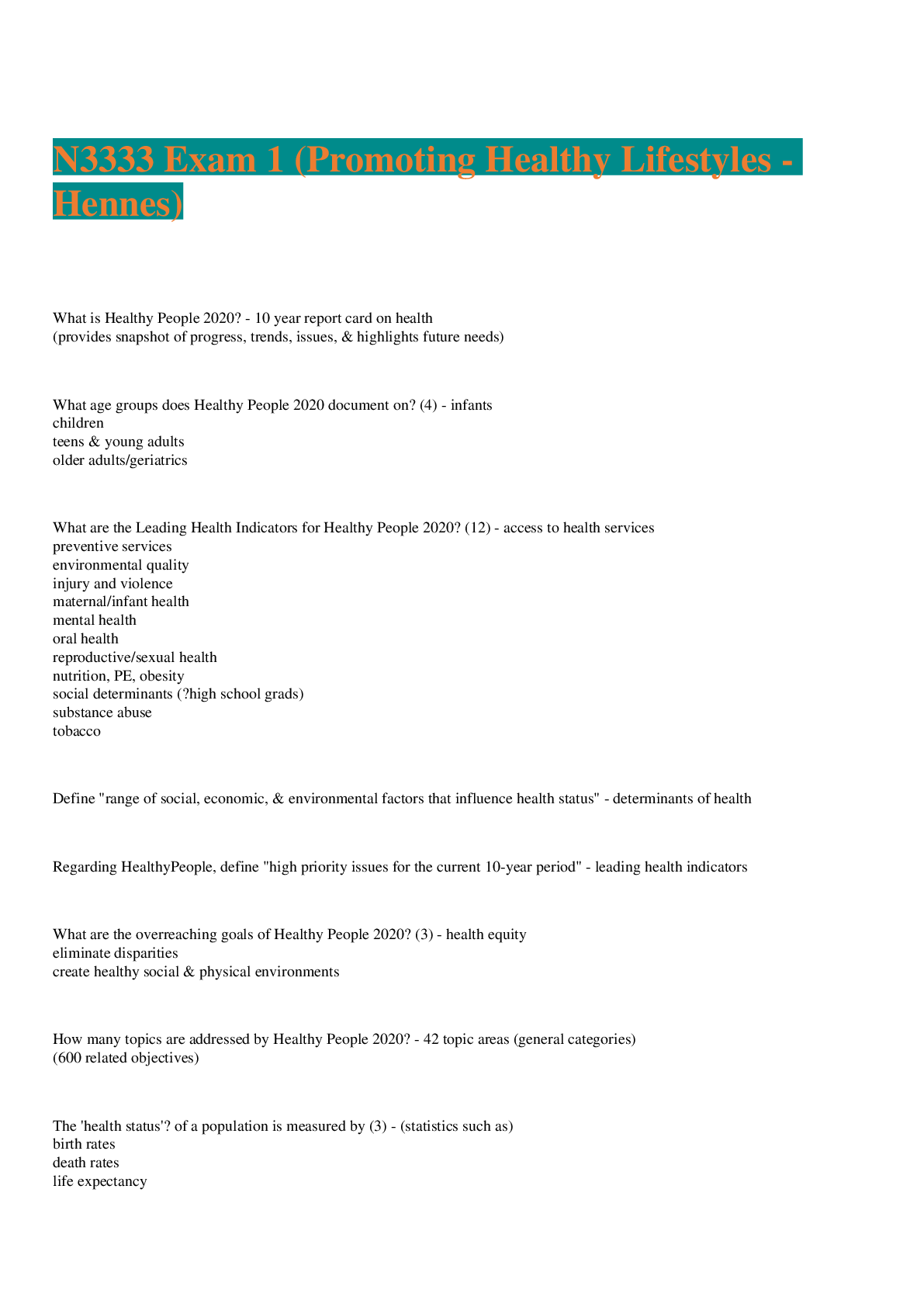
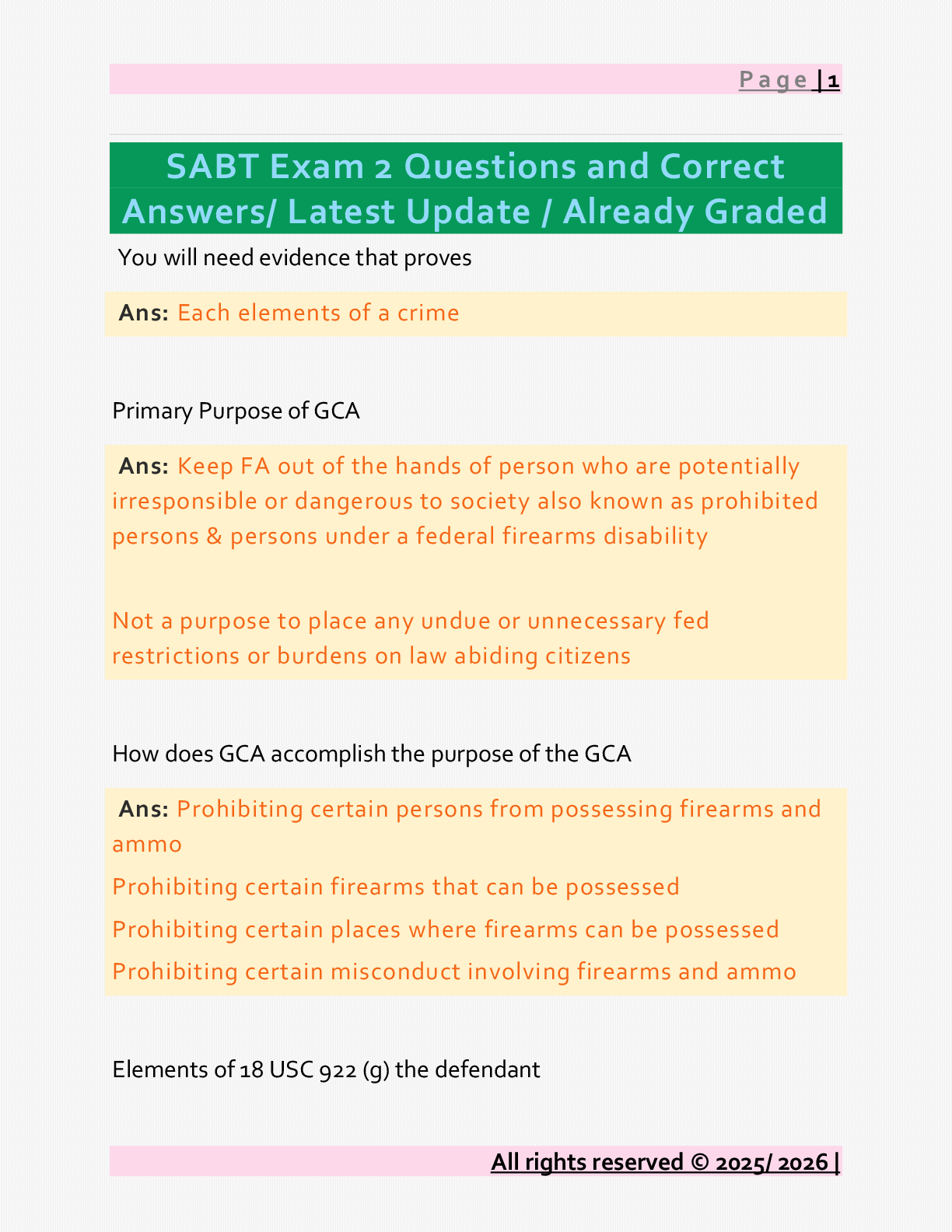
Several of your co-workers are having a discussion over the etc/passwd file. They are at odds over what types of encryption are used to secure Linux passwords.(Choose all that apply). A. Linux passw ... ords can be encrypted with MD5 C. Linux passwords can be encrypted with DES D. Linux passwords can be encrypted with Blowfish [Show More]
Last updated: 3 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 28, 2022
Number of pages
5
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 28, 2022
Downloads
0
Views
45