A customer has an established base of GVC VPN users with a WAN GroupVPN policy configured. The customer wants to begin an implementation for SSL VPN users. The existing group of GVC VPN users must be converted to SSL VPN
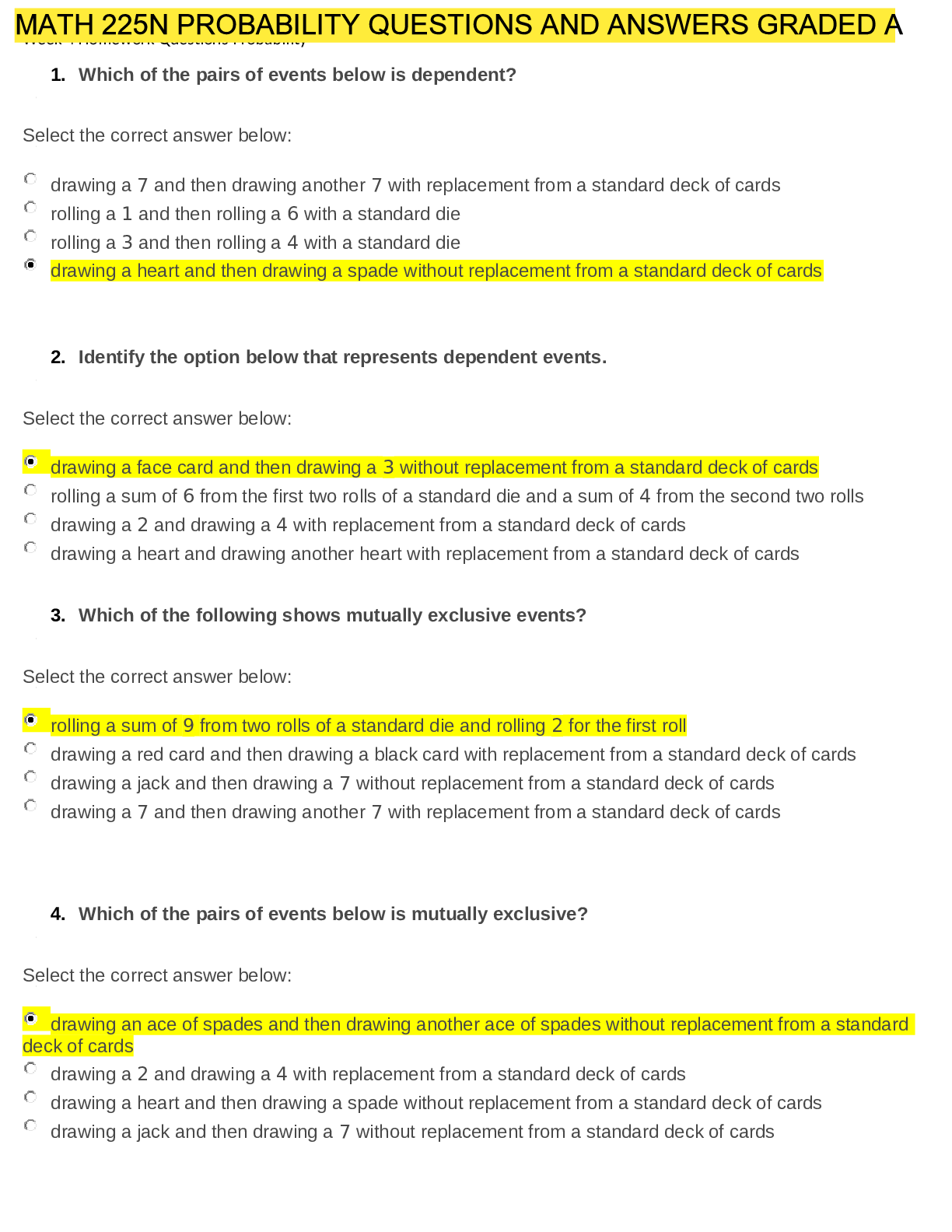
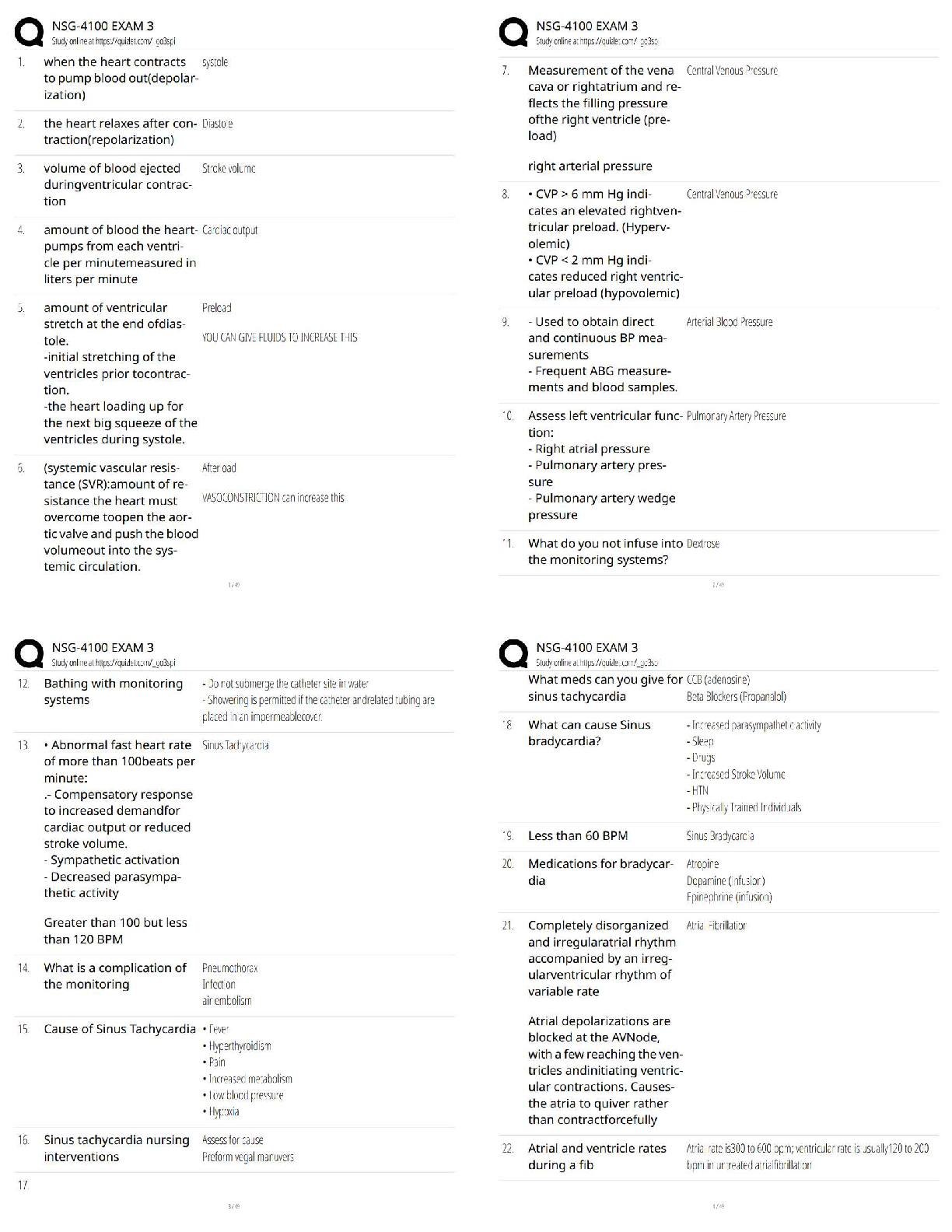
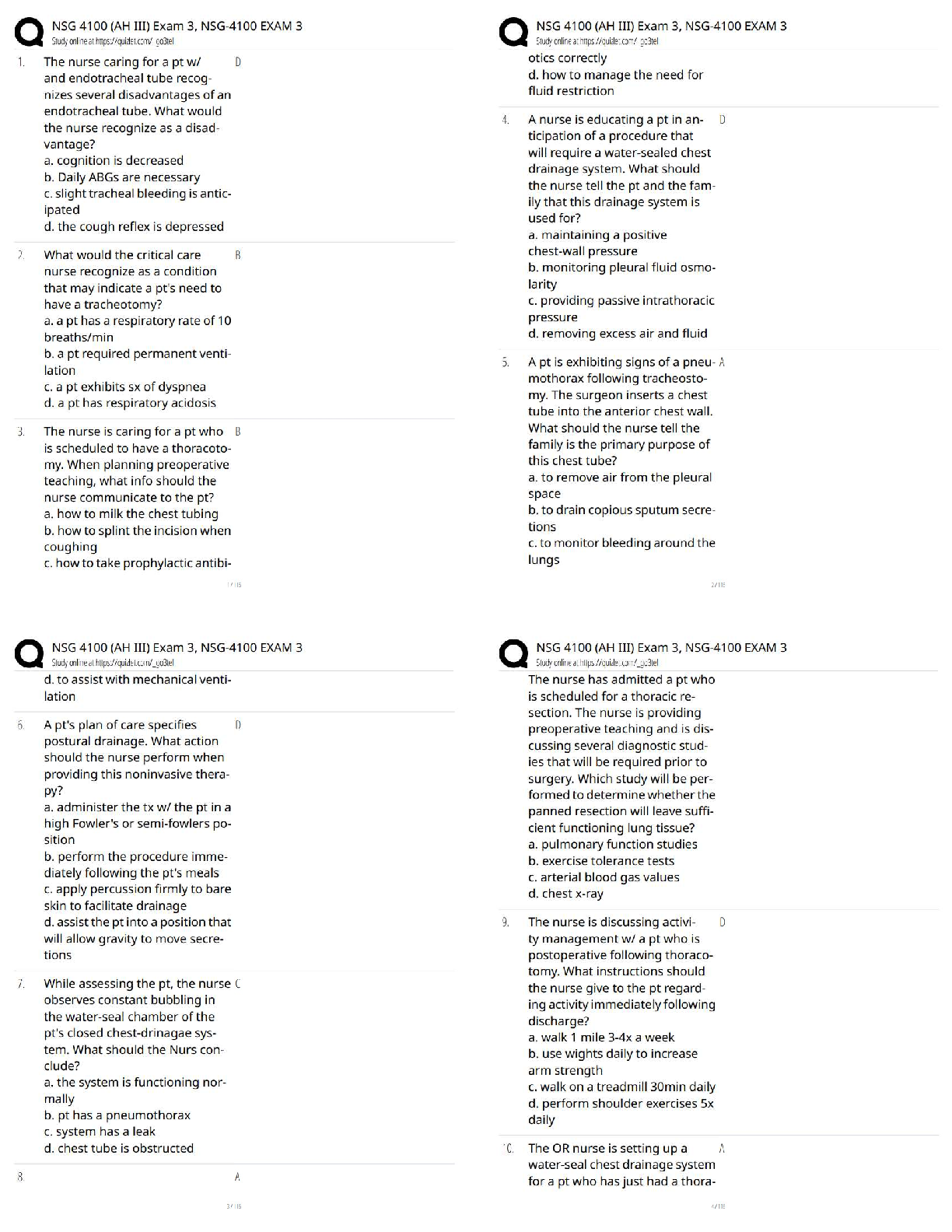
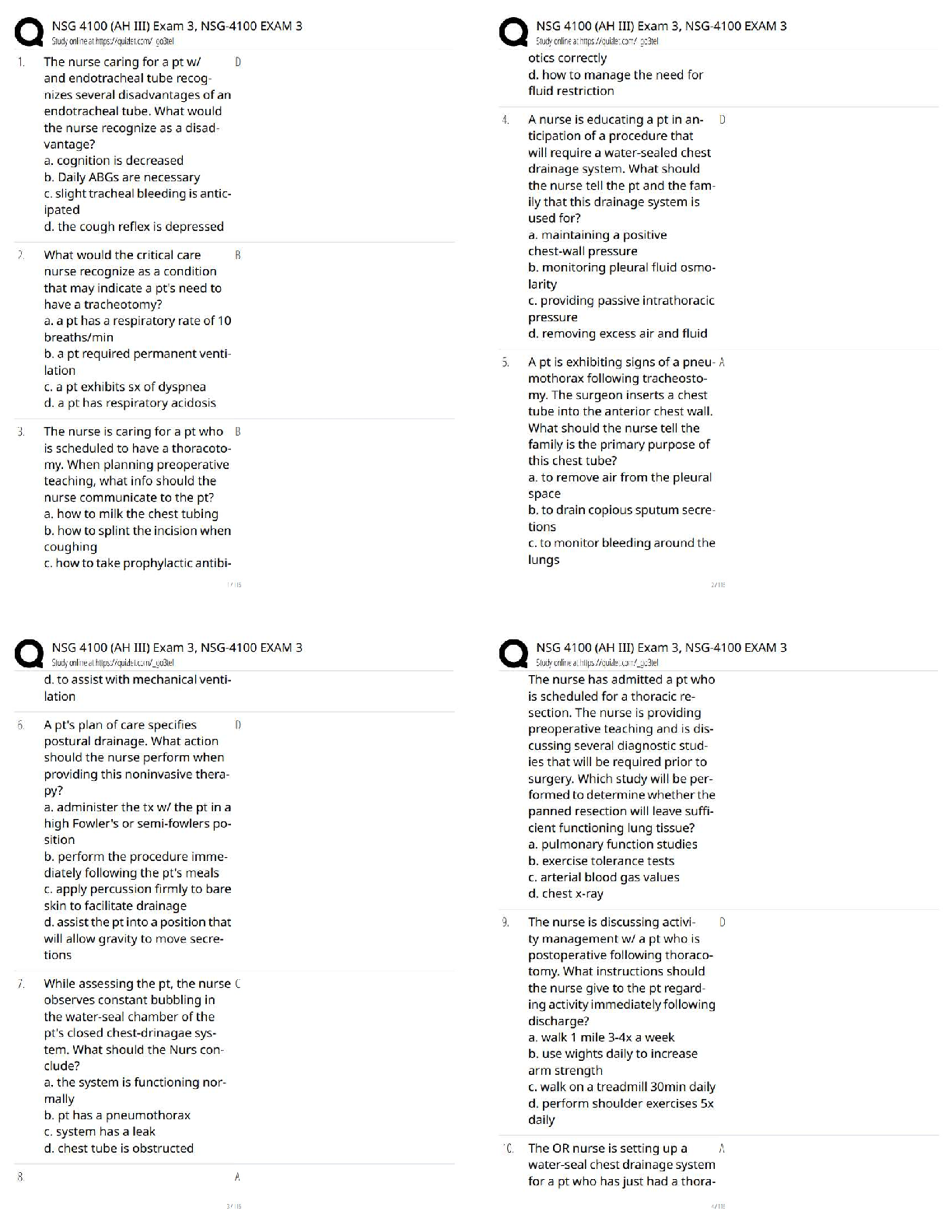
...
A customer has an established base of GVC VPN users with a WAN GroupVPN policy configured. The customer wants to begin an implementation for SSL VPN users. The existing group of GVC VPN users must be converted to SSL VPN users because the SonicWALL security appliance does not support both types of VPN users.
FALSE
SSL VPN eliminates the need for remote access authentication.
FALSE
Which of the following correctly describes how a bandwidth management rule works?
-Can be configured for all VPN traffic
-Only applies to outbound traffic from the firewall to the WAN or any other destination
-Can be configured only for individual VPN Security Associations
-Only applies to inbound traffic from the WAN to the firewall
Can be configured for all VPN traffic
What are the benefits provided by a VPN (select all that apply)?
-Securely connects distributed networks together
-Prevents denial-of-service attacks on remote connections
-Enables a remote connection to the LAN via the Internet
-Assures remote clients have up-to-date anti-virus software
-Provides data confidentiality and sender authentication
-Securely connects distributed networks together
-Enables a remote connection to the LAN via the Internet
-Provides data confidentiality and sender authentication
What benefits are provided by a VPN (select all that apply)?
-Reporting
-Increased capacity
-Scalability
-Encryption
-Security
-Scalability
-Encryption
-Security
Which of the following is the most basic firewall technology?
-Packet filtering
-Single firewall
-Deep packet inspection
-Application proxies
-Packet filtering
The default firewall access rule allows all communication from the LAN to the Internet.
-True
-False
-True
What are two advantages of a multiple firewall?
-Protects restricted special resources
-Offers protection from external attacks while each network segment has free access to other segments
-Helps protect entire departments
What are two advantages of a multiple firewall?
-Protects restricted special resources
What is the purpose of a security policy?
-To authenticate the process by which users and devices are identified and granted access to the network
-To monitor the network security and make sure the firewall is configured properly to prevent inappropriate usage
-To make it more difficult for hackers to locate a security hole in a network's gateway
-To describe how a company wants to approach security, including rules of conduct and the determination of acceptable risk
-To describe how a company wants to approach security, including rules of conduct and the determination of acceptable risk
What question would you ask to get specific information on user restrictions?
-What kinds of network traffic will you allow?
-Will the computers be locked away from the public, or will they have access to the hardware?
-Will users be allowed to login at any time, from any location, to any machine?
-Who should be allowed to access your services?
-Will users be allowed to login at any time, from any location, to any machine?
Content Filtering Services applies to which of the following traffic protocols? (Select all that apply.)
-HTTPS
-FTP
-HTTP
-Email attachments
-HTTP
-HTTPS
If the appliance loses connection to the SonicWALL site rating library: (Select all that apply.)
-CFS blocks all web traffic (based on configuration)
-CFS continues to operate using the last ratings seen
-CFS allows all web traffic (based on configuration)
-CFS must use its internal logic to identify which traffic to block
-CFS blocks all web traffic (based on configuration)
-CFS allows all web traffic (based on configuration)
With SonicWALL CFS, network administrators have a flexible tool to provide comprehensive filtering based on which of the following? (Select all that apply.)
-Allowed domain designations
-Time of day
-SMTP
-Keywords
-LDAP Groups
-Forbidden domain designations
-FTP
-Allowed domain designations
-Time of day
-Keywords
-Forbidden domain designations
The default CFS policy when assigned "Via Users and Zones Screens" should be the most restrictive.
-True
-False
True
The SonicWALL Log can be exported in the following formats: �(Choose all that apply)
-Log View
-Comma-separated value (CSV)
-Tab Delimited
-Plain text
-Comma-separated value (CSV)
-Plain text
Which SonicWALL security services use the Deep Packet Inspection engine? (Select all that apply)
-IPS
-Anti-Spyware
-GVC
-GAV
-CFS
-IPS
-Anti-Spyware
-GAV
-CFS
A SonicWALL security appliance configured with Gateway Anti-Virus verifies and enforces the Desktop Anti-Virus client to the downstream workstation.
-True
-False
-False
The SonicWALL GAV engine can perform base64 decoding without ever reassembling the entire base64 encoded email stream.
-True
-False
-True
When you select "Prevent All" in the IPS Global Settings of the SonicWALL security appliance for High Priority Attacks, this allows all blocked attacks to be entered into the Log file of the security appliance.
-True
-False
-False
SonicWALL GAV includes advanced decompression technology that can automatically decompress and scan files on a per packet basis to search for viruses and malware.
-True
-False
-True
The SonicWALL security appliance maintains an Event log for tracking potential security threats.
-True
-False
-True
Which Security Services of the SonicWALL security appliance use the SonicWALL Deep Packet Inspection engine?
-IPS, GAV, Anti-Spyware, and Viewpoint
-IPS, Anti-Spyware, Content Filtering
-IPS, GAV, and Anti-Spyware
-Global VPN Client
-IPS, GAV, and Anti-Spyware
In order for SonicWALL's Deep Packet Inspection engine to provide protection, where must GAV, IPS, and/or Gateway Anti-Spyware be configured?
-Firewall rules
-Enforced in the Zones and enabled in security services
-Address objects
-Zones
-NAT policies and firewall rules
-Zones
Which of the following LB/Failover methods would be selected if an administrator wanted to specify how much outbound traffic is sent through the primary and secondary WAN interfaces?
-Active/Passive
-Ratio based
-Round Robin
-Spill-Over based
-Ratio based
How does the SonicWALL maintain persistence with outbound load balancing?
-SSL Session ID
-Source IP and Destination IP
-Source and Destination Port
-Session Cookies
-Source IP and Destination IP
One requirement of WAN ISP Failover and Load balancing is?
-Twin-ax cables
-Standard OS
-A second ISP connection
-Cross-Over cable
-A second ISP connection
When WAN failover occurs, the firewall re-establishes all sessions using the new WAN interface with no traffic interruption thanks to the stored and tracked session states.
-True
-False
-False
Besides Probe Monitoring, one requirement of WAN ISP Failover and Load balancing is?
-Static IP Addresses on both WAN Interfaces
-Twin-ax cables
-Available Interface that can be configured as a secondary WAN
-Standard OS
-Available Interface that can be configured as a secondary WAN
The Company's security policy is to only allow WWW browsing by all internal users; no other internet traffic is permitted. Assuming that you are allowing DNS, what are the "Best Practices" firewall rules to accomplish this. Assume the following column headings:
(Select the one best answer)
--LAN > WAN(Intersection) - Any(Source) - Any(Destination) - HTTP(Service) - Allow(Action) - All(Users)
--WAN > LAN(Intersection) - Any(Source) - Any(Destination) - DNS(Service) - Allow(Action) - All(Users)
--WAN > WAN(Intersection) - Any(Source) -
Any(Destination) - Any(Service) - Deny(Action) - All(Users)
--LAN > WAN(Intersection) - Any(Source) - Any(Destination) - Any(Service) - Allow(Action) - All(Users)
--WAN > LAN(Intersection) - Any(Source) - Any(Destination) - HTTP(Service) - Allow(Action) - All(Users)
--LAN > WAN(Intersection) - Any(Source) - Any(Destination) - HTTP(Service) - Allow(Action) - All(Users)
Which of the following configurations takes precedence?
-Private NAT rules on DMZ
-Outbound WAN Load Balancing
-Global Public NAT rules
-Outbound Policy Based Route
-Outbound WAN Load Balancing
Which of the following LB/Failover methods allows an administrator to specify a threshold at which traffic is also sent out of the secondary WAN Interface?
-Spill-Over based
-Percentage based
-Round Robin
-Active/Passive
-Spill-Over based
Check Network Settings is a diagnostic tool which automatically checks the network connectivity and service availability of several pre-defined functional areas of SonicOS, returns the results, and attempts to describe the causes if any exceptions are detected.
-True
-False
-True
The default factory behavior of a SonicOS appliance is to allow all traffic from the LAN and block all traffic from the WAN.
-True
-False
-True
[Show More]









 (1).png)












.png)