 - Y3Q1.png)
Summary International Business Awareness (Law) - Y3Q1
$ 9
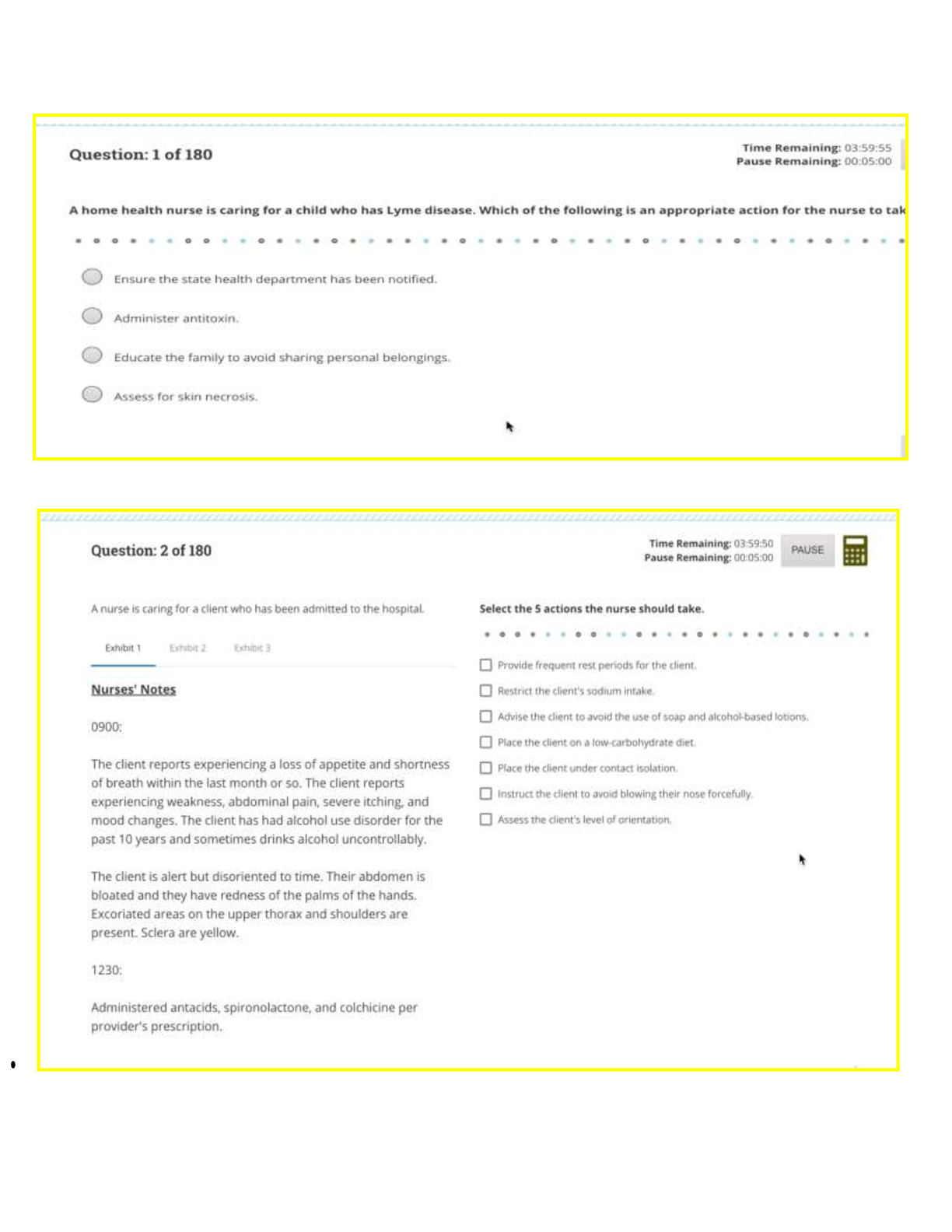
Ultimate Guide to RN ATI Comprehensive Predictor 2025 NGN Proctored Exam
Describe the purpose, intent, and security professional's role in each step of the Command Cyber Readiness Inspections (CCRI) process Correct Answer: Defining the scope, the inspection phase, documen ... tation of observations, and reporting findings. A security professional would have responsibilities in defining the scope of the inspection, overseeing the self-inspection and remediation efforts, and coordinating with the CCRI team throughout the remainder of the process List two factors that should be considered when determining position sensitivity Correct Answer: (1) Level of access to classified information (2) IT level needed (3) Duties associated with position Explain the process for responding to a "spillage" Correct Answer: 1. Detection (implied) 2. Notification and preliminary inquiry 3. Containment and continuity of operations 4. Formal inquiry 5. Resolution 6. Reporting Explain how the adjudication process contributes to effective risk management of DoD assets Correct Answer: Determines an individual's loyalty, reliability, and trustworthiness are in the best interest of national security Explain why access control measures are contingent on Force Protection Conditions Correct Answer: The Force Protection Conditions determine the amount of control measures needed to be taken in response to various levels of threats against military facilities or installations. Define the purpose and function of the militarily critical technologies list (MCTL) Correct Answer: Serves as a technical reference for the development and implementation of DoD technology, security policies on international transfers of defense-related goods, services, and technologies as administered by the Director, Defense Technology Security Administration (DTSA). Describe how authorization of Limited Access Authority impacts risk to DoD assets Correct Answer: Increases risk by allowing a foreign national access to classified information. Reduces risk by ensuring Foreign Nationals with a unique or unusual skills set have been properly investigated, adjudicated or vetted before being granted access to specific pieces of classified information only. List three different types of threats to classified information Correct Answer: (1) Insider threat (2) Foreign Intelligence entities (3) Cybersecurity Threat What is the security professionals' r [Show More]
Last updated: 3 years ago
Preview 1 out of 8 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Can't find what you want? Try our AI powered Search
Connected school, study & course
About the document
Uploaded On
Nov 21, 2022
Number of pages
8
Written in
All
This document has been written for:
Uploaded
Nov 21, 2022
Downloads
0
Views
105
Scholarfriends.com Online Platform by Browsegrades Inc. 651N South Broad St, Middletown DE. United States.
We're available through e-mail, Twitter, and live chat.
FAQ
Questions? Leave a message!
Copyright © Scholarfriends · High quality services·