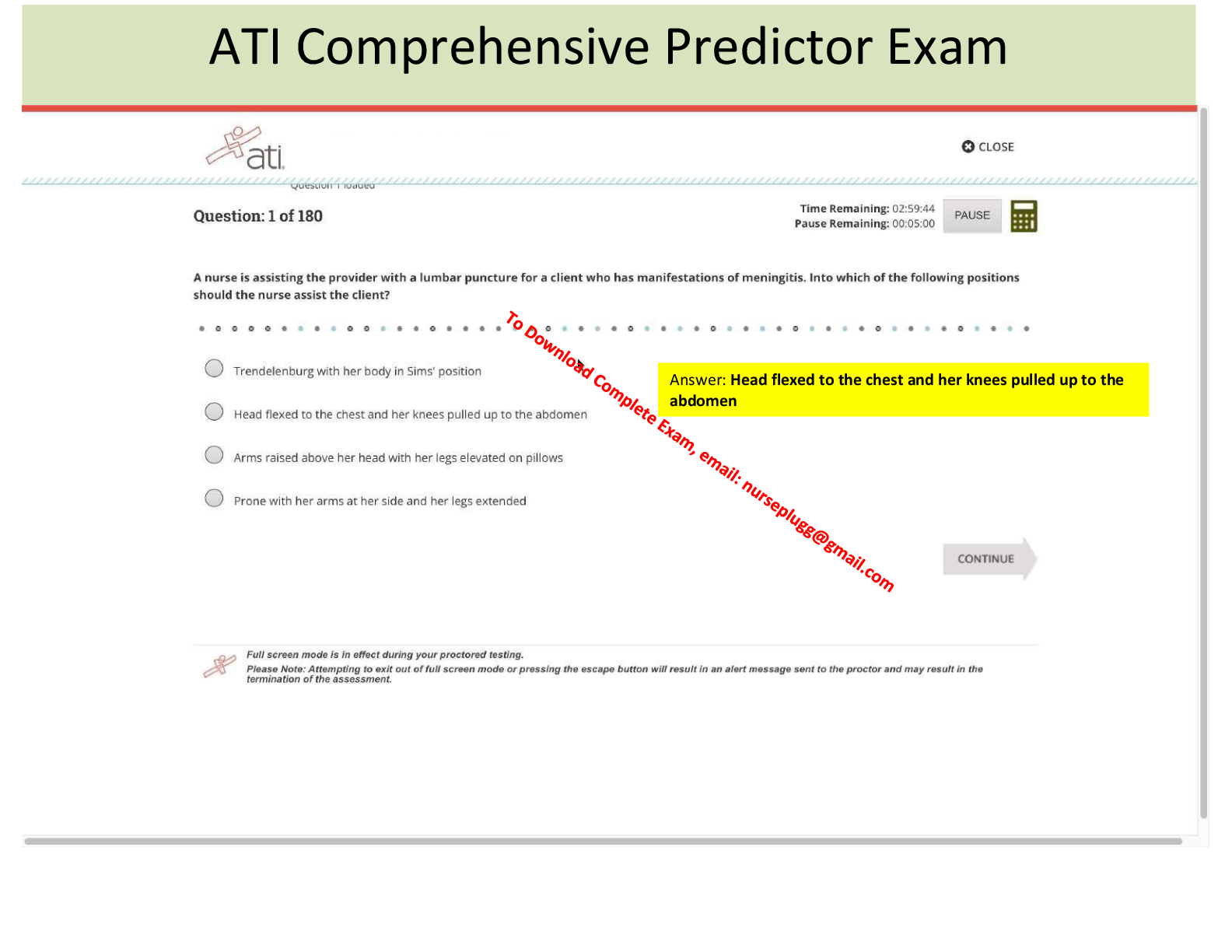
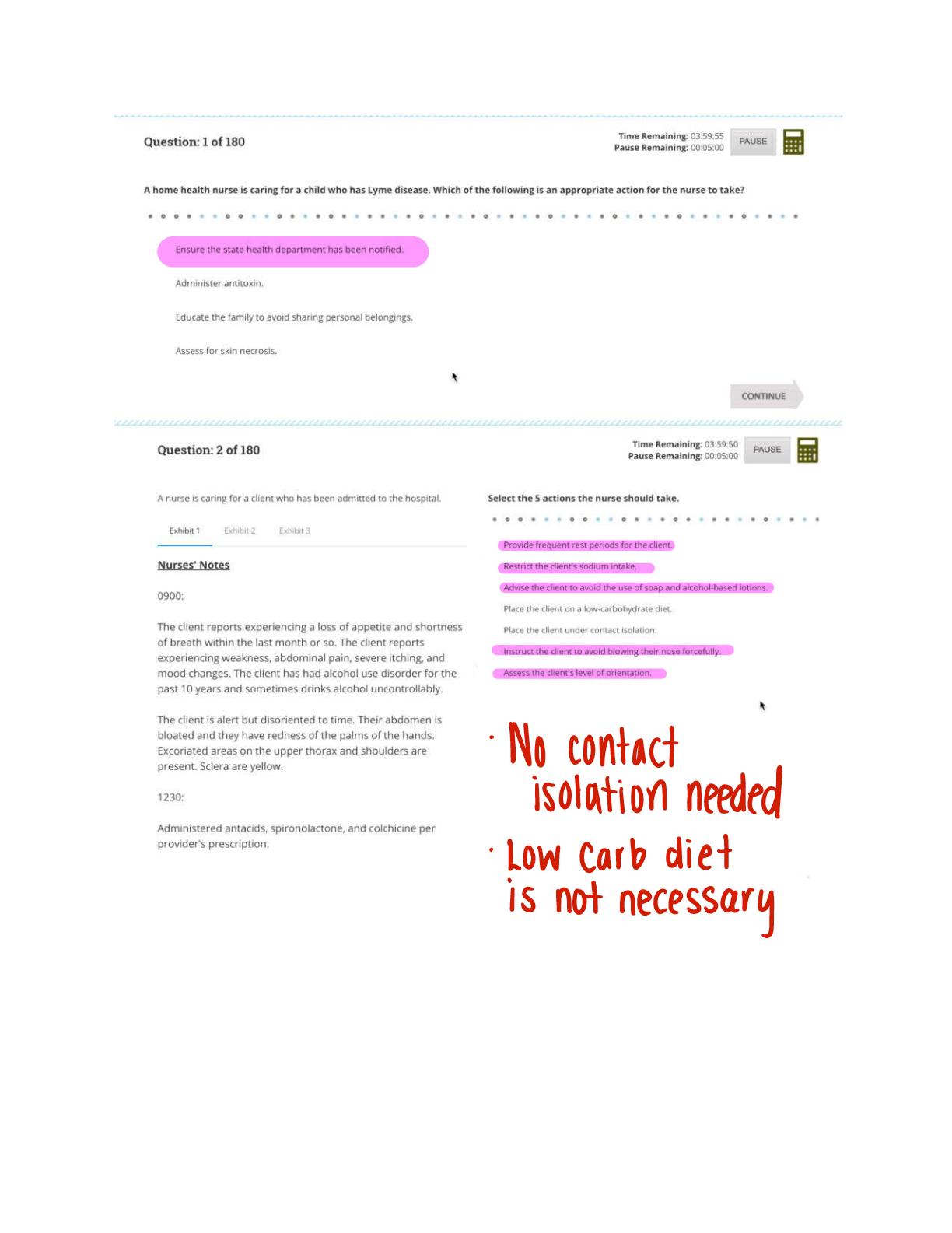
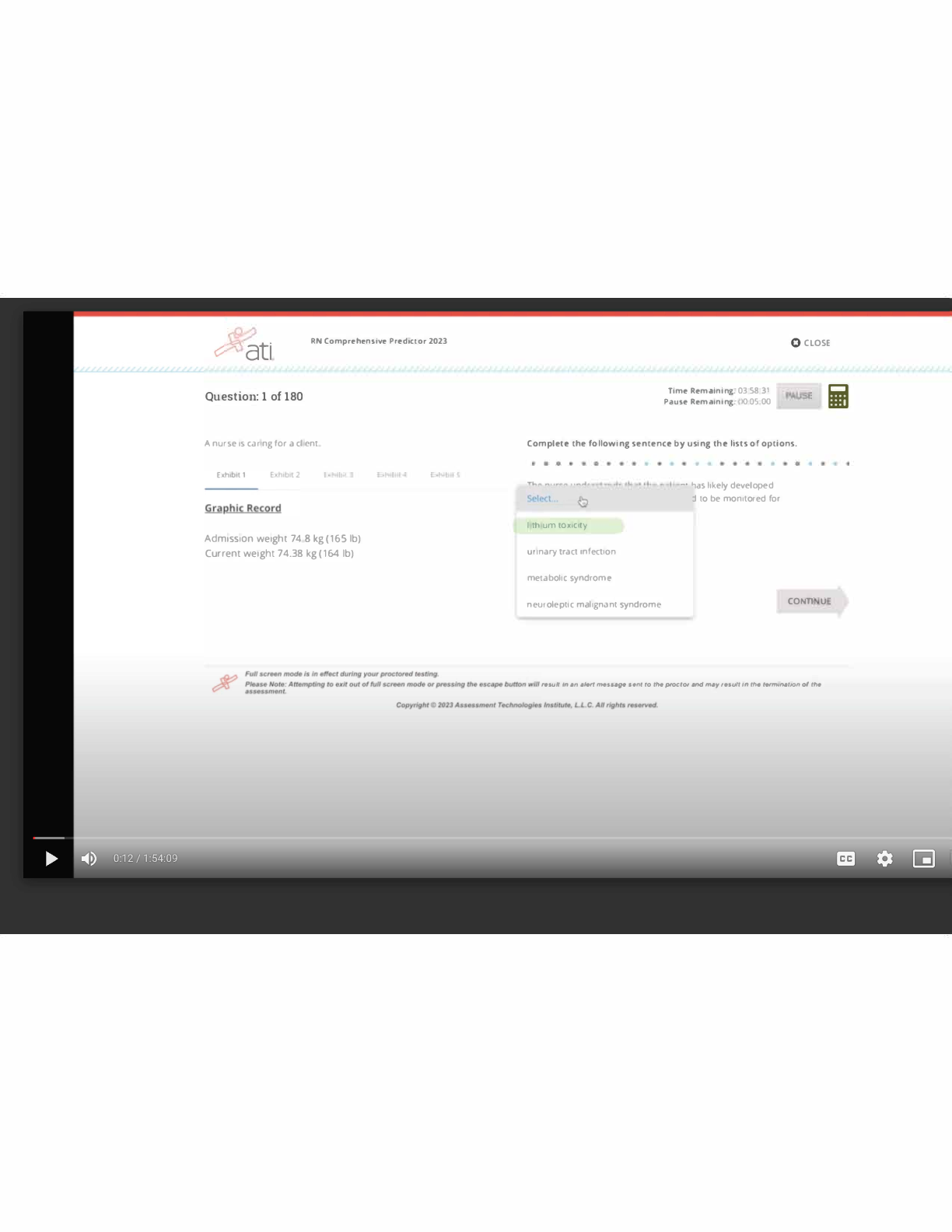
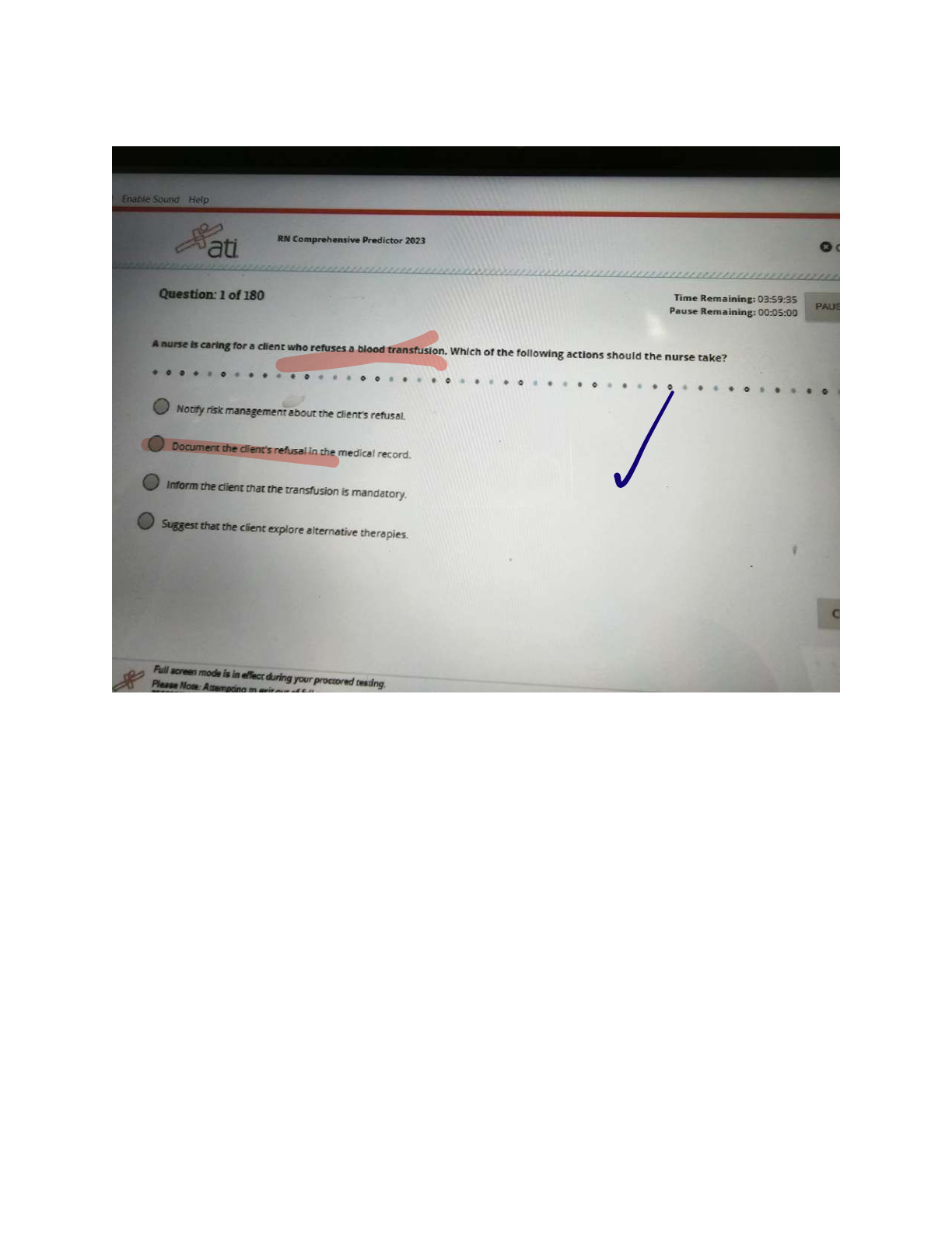
Special Access Program (SAP) - ANSWER A program established for a specific class of classified information that imposes safeguarding and access requirements that exceed those normally required for information at the same
...
Special Access Program (SAP) - ANSWER A program established for a specific class of classified information that imposes safeguarding and access requirements that exceed those normally required for information at the same classification level
Enhanced security requirements for protecting Special Access Program (SAP) information - ANSWER 1. Within Personnel Security:
• Access Rosters; • Billet Structures (if required); • Indoctrination Agreement; • Clearance based on an appropriate investigation completed within the last 5 years; • Individual must materially contribute to the program in addition to having the need to know; • All individuals with access to SAP are subject to a random counterintelligence scope polygraph examination; • Polygraph examination, if approved by the DepSecDef, may be used as a mandatory access determination; • Tier review process; • Personnel must have a Secret or Top Secret clearance; • SF-86 must be current within one year; • Limited Access; • Waivers required for foreign cohabitants, spouses, and immediate family members.
2. Within Industrial Security: The SecDef or DepSecDef can approve a carve-out provision to relieve Defense Security Service of industrial security oversight responsibilities.
3. Within Physical Security: • Access Control; • Maintain a SAP Facility; • Access Roster; • All SAPs must have an unclassified nickname/ Codeword (optional).
4. Within Information Security: • The use of HVSACO; • Transmission requirements (order of precedence).
Principle incident/events required to be reported to DoD counterintelligence (CI) organizations - ANSWER espionage, sabotage, terrorism, cyber
Indicators of insider threats - ANSWER 1. Failure to report overseas travel or contact with foreign nationals
2. Seeking to gain higher clearance or expand access outside the job scope
3. Engaging in classified conversations without a need to know
4. Working hours inconsistent with job assignment or insistence on working in private
5. Exploitable behavior traits
6. Repeated security violations
7. Attempting to enter areas not granted access to
8. Unexplained affluence/living above one's means
9. Anomalies (adversary taking actions which indicate they are knowledgeable to information)
10. Illegal downloads of information/files
Asset, threat, vulnerability, risk, countermeasures - ANSWER Elements that a security professional should consider when assessing and managing risks to DoD assets
The three categories of Special Access Programs - ANSWER acquisition, intelligence, and operations and support
Responsibilities of the Government SAP Security Officer/Contractor Program Security Officer (GSSO/CPSO): - ANSWER From Revision 1 Department of Defense Overprint to the National Industrial Security
Program Operating Manual Supplement - 1 April 2004:
• Possess a personnel clearance and Program access at least equal to the highest level of Program classified information involved.
• Provide security administration and management for his/her organization.
• Ensure personnel processed for access to a SAP meet the prerequisite personnel clearance and/or investigative requirements specified.
• Ensure adequate secure storage and work spaces.
• Ensure strict adherence to the provisions of the NISPOM, its supplement, and the Overprint.
• When required, establish and oversee a classified material control program for each SAP.
• When required, conduct an annual inventory of accountable classified material.
• When required, establish a SAPF.
• Establish and oversee a visitor control program.
• Monitor reproduction and/or duplication and destruction capability of SAP information
• Ensure adherence to special communications capabilities within the SAPF.
• Provide for initial Program indoctrination of employees after their access is approved; rebrief and debrief personnel as required.
• Establish and oversee specialized procedures for the transmission of SAP material to and from Program elements.
• When required, ensure contractual specific security requirements such as TEMPEST Automated Information System (AIS), and Operations Security (OPSEC) are accomplished.
• Establish security training and briefings specifically tailored to the unique requirements of the SAP.
List three primary authorities governing foreign disclosure of classified military information - ANSWER 1. Arms Export Control Act
2. National Security Decision Memorandum 119
3. National Disclosure Policy-1
4. International Traffic in Arms Regulation (ITAR)
5. E.O.s 12829, 13526
6. Bilateral Security Agreements
7. DoD 5220.22-M, "NISPOM"
Three different types of threats to classified information - ANSWER Insider Threat, Foreign Intelligence Entities (FIE) and Cybersecurity Threat
The concept of an insider threat - ANSWER An employee who may represent a threat to national security. These threats encompass potential espionage, violent acts against the Government or the nation, and unauthorized disclosure of classified information, including the vast amounts of classified data available on interconnected United States Government computer networks and systems.
The purpose of the Foreign Visitor Program - ANSWER To track and approve access by a foreign entity to information that is classified; and to approve access by a foreign entity to information that is unclassified, related to a U.S. Government contract, or plant visits covered by ITAR.
True - ANSWER True or False: Special access requirements are designed to provide an additional layer of security to some of our nation's most valuable assets.
False. Threats and vulnerabilities are related but distinct. Threats to national security exploit vulnerabilities. - ANSWER True or False: There is no difference between a threat and a vulnerability.
What SAPs aim to achieve - ANSWER 1. Protect technological breakthroughs
2. Cover exploitation of adversary vulnerabilities
3. Protect sensitive operational plans
4. Reduce intelligence on U.S. capabilities
Protection Level - ANSWER This communicates how the SAP is acknowledged and protected.
Acknowledged - ANSWER This protection level describes a SAP whose existence may be openly recognized. Its purpose may be identified. However, the details of the program (including its technologies, materials, and techniques) are classified as dictated by their vulnerability to exploitation and the risk of compromise. The funding is generally unclassified.
Unacknowledged - ANSWER This protection level describes a SAP whose existence and purpose are protected. The details, technologies, materials, and techniques are classified as dictated by their vulnerability to exploitation and the risk of compromise. The program funding is often classified, unacknowledged, or not directly linked to the program.
SAP Lifecycle - ANSWER 1. Establishment (is extra protection warranted?)
2. Management and Administration (continued need? processed followed?)
3. Apportionment (proper measures in place? approval received)
4. Disestablishment (program no longer needed?)
Component-level SAP Central Offices - ANSWER Exist for each military component, the Joint Chiefs of Staff, Defense Advanced Research Projects Agency (DARPA), and Missile Defense Agency (MDA)
Special Access Program Oversight Committee (SAPOC) - ANSWER The final SAP approving body chaired by the Deputy Secretary of Defense
Senior Review Group (SRG) - ANSWER This group ensures there are no duplicative efforts across SAPs
DoD Special Access Central Office (SAPCO) - ANSWER DoD SAP legislative liaison that notifies Congress of SAP approval
Authorization, Appropriations, and Intelligence Congressional - ANSWER Congressional committees granted SAP access
OSD-level SAP Central Offices - ANSWER Exercise oversight authority for the specific SAP category under their purview.
Information System Security Managers (ISSM) - ANSWER Responsible for the security of information systems. They coordinate physical security measures and develop contingency plans for the protection of the information system.
DD 1540 - ANSWER Registration for scientific and technical info specs, government and contractors are required to fill out form, contractor a separate form for each request valid until contract expires
DD 441 DoD Security agreement - ANSWER a contractual agreement between the U.S. government and a cleared contractor facility
DD 441-1 - ANSWER Appendage to Security Agreement - list cleared divisions or branch offices that are included in and covered by the provisions of the organizations security agreement and certification pertaining to foreign interest
DD 254 DoD Contract Security Classification Spec - ANSWER provides to the contractor (or subcontractor) the security requirements and the classification guidance that would be necessary to perform on a classified contract
DD 1847 - ANSWER SCI Indoctrination Memo - Used to precisely identify individuals when it is necessary to certify their access to SCI
DD 1847-1 - ANSWER SCI NDA - used to precisely identify individuals when it is necessary to certify their access to SCI, non-disclosure agreement
DD 1848 - ANSWER SCI Debrief memo - A memo that records the fact that and individual was debriefed on a SCI SAP
DD 1870 - ANSWER Request for personnel security investigation SSBI, PR, SII or ENAC
DD 2024 - ANSWER DoD SCG Data Elements - this form is executed by the originator of each SCG issued pursuant to the req of DoD 5200.1-R, info sec program regulation to report: - approval (promulgation) of a new SCG; - revision of a SCG; reissuance; accomplishment of the biennial review; - cancellation; - correction of data on previously submitted form
DD 2056 - ANSWER Telephone monitoring notification decal. Used to notify a user that the telephone is subject to monitoring at all times, used of that telephone constitutes consent to monitoring
DD 2501 - ANSWER Courier Authorization - used to identify appropriately cleared personnel 1) recurrent need, 2) signed by appropriate security person, 3) Forms are controlled to preclude unauthorized use, 4) issued for no more than 1 year, 5) followed approved processes for SCI or SAP
DIS FL 381-R - ANSWER Letter of notification of facility security clearance. This document notifies a facility that they are cleared to handle classified material
DISCO Form 2 - ANSWER Request for Forms - additional PSQ and NAQ forms may be ordered from DISCO with this form
DISCO Form 560 - ANSWER Letter of Consent - Used by DISCO to notify a contractor that a PCL or limited access authorization has been granted to an employee
FD Form 258 - ANSWER Applicant Fingerprint Card - Fingerprint card used for military investigations
SF 85 - ANSWER Questionnaire for Non-Sensitive Positions - a permanent doc that may be used as the basis for future investigations, security clearances, determinations and suitability for employment, may be compared to previous security request
SF 85P-S - ANSWER Supplemental Questionnaire for Selected Positions - future investigations, security clearance investigations, determination for suitability for employment, may be compared to previous security request
SF 86 - ANSWER Questionnaire for National Security Positions - future investigations, security clearance investigations, determination for suitability for employment, may be compared to previous security request
SF 87 - ANSWER Applicant Fingerprint Card - fingerprint card required for civilian investigations
[Show More]