MIDTERM EXAMINATION #2 OPERATING SYSTEM CONCEPTS
$ 7

Hunter College, CUNY - CHEM 225.RCChap 19 Aromatic Sub Su19 HW B KEY
$ 7

WGU C207 Final Self-Assessment Q&A complete solution
$ 9

Certified Ophthalmic Assistant
$ 7.5
.png)
NHA CCMA EXAM REVIEW 2022 Chief Complaint (With complete solution)
$ 14

NURS 6521N Final Exam 12 - Pharmocology
$ 15

Aging MT TD QUESTIONS AND ANSWERS VERIFIED
$ 11

NAPSRx® COMPLETE STUDY GUIDE LATEST 2022/2023
$ 13

OCR GCE Chemistry B H433/02 Scientific literacy in chemistry A Level Mark Scheme for June 2023
$ 11.5

eBook Teaching Democracy in an Age of Uncertainty Place-Responsive Learning 1st Edition ,by Gilbert Burgh, Simone Thornton
$ 29

Battlefield_Furniture_Case_Exercise_Ver_4.pptx
$ 7

ATI LPN PHARMACOLOGY EXAM2022
$ 14

Sophia Macroeconomics Milestone 1 Questions and Answers Latest Updated and Graded A+
$ 12
.png)
200question nclex exam Latest updated already graded A
$ 13
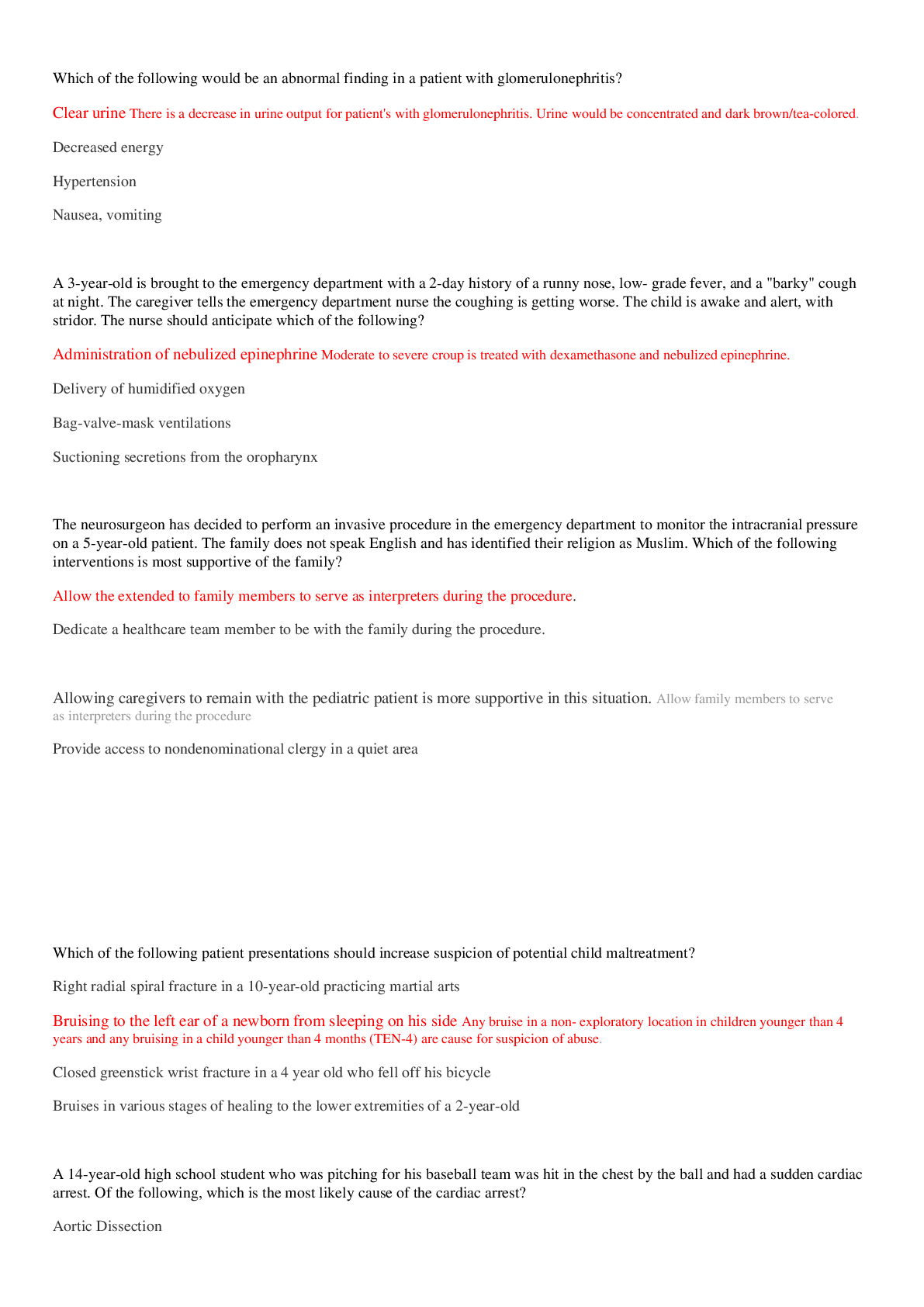
ENPC EXAM QUESTIONS (ANSWERED 100% CORRECT)
$ 10.5

Test Bank Perry Maternal Child Nursing Care 6th 2020
$ 7
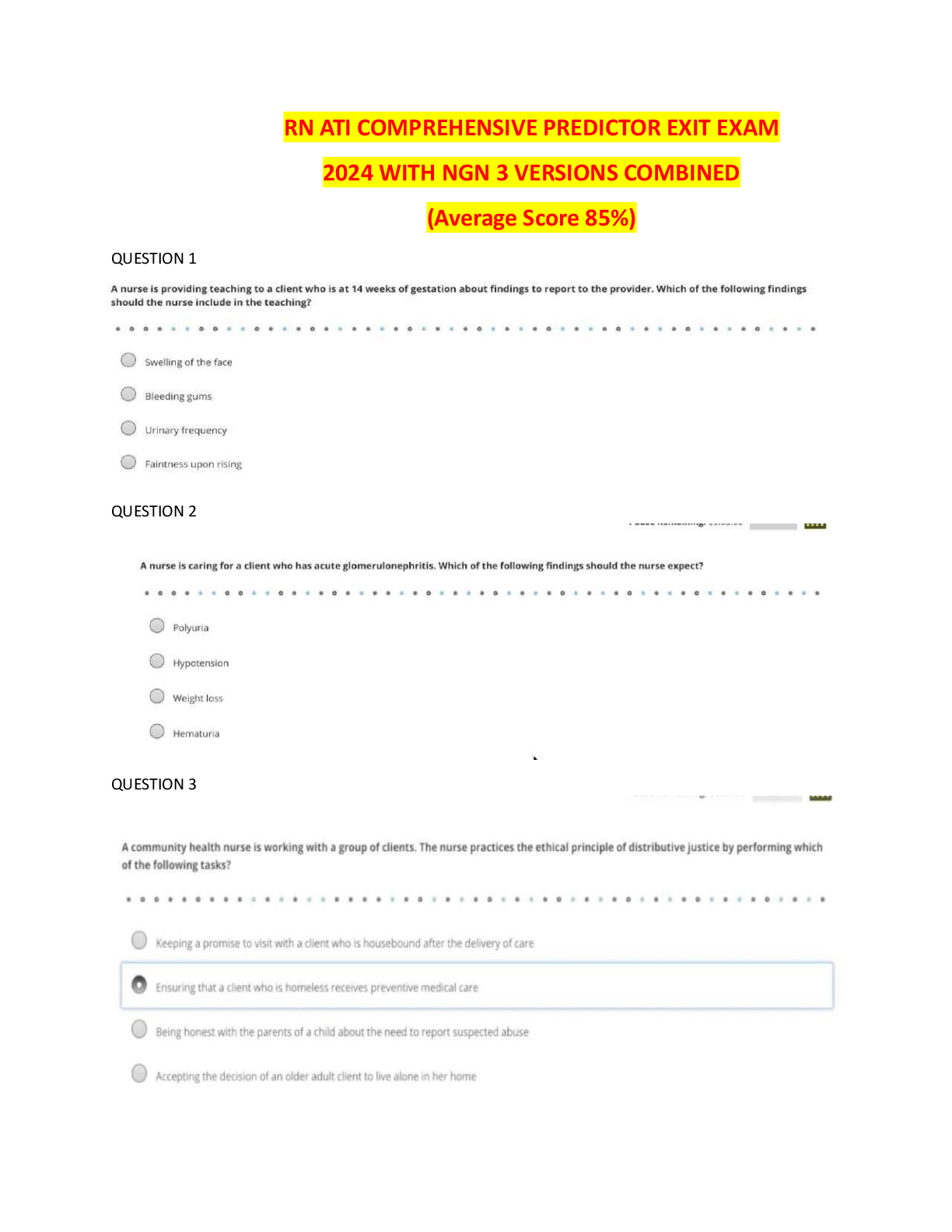
RN ATI COMPREHENSIVE PREDICTOR EXIT EXAM 2023-2024 COMPILATION (540 QUESTIONS)
$ 20

MODALITIES EXAM #2- SPRING 2022 | 150 QUESTONS AND ANSWERS
$ 10

NYSTCE CST MATH QUESTIONS AND ANSWERS 100% CORRECT
$ 11.5
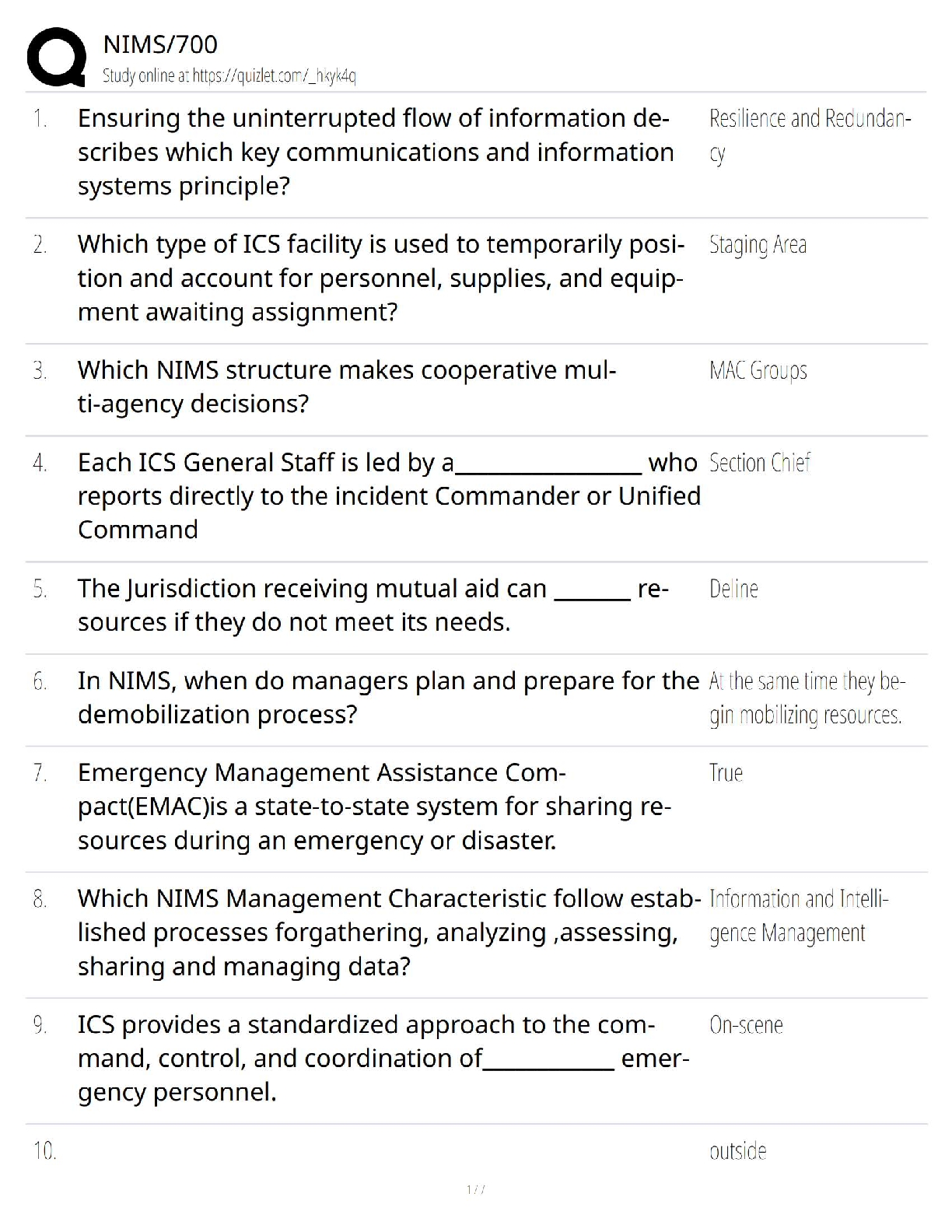
NIMS 700 / IS-700.B National Incident Management System 2025 – Study Guide & Exam Prep / New Version
$ 7

PHARMACOLOGY RN FINAL EXAM 2022/2023
$ 10.5
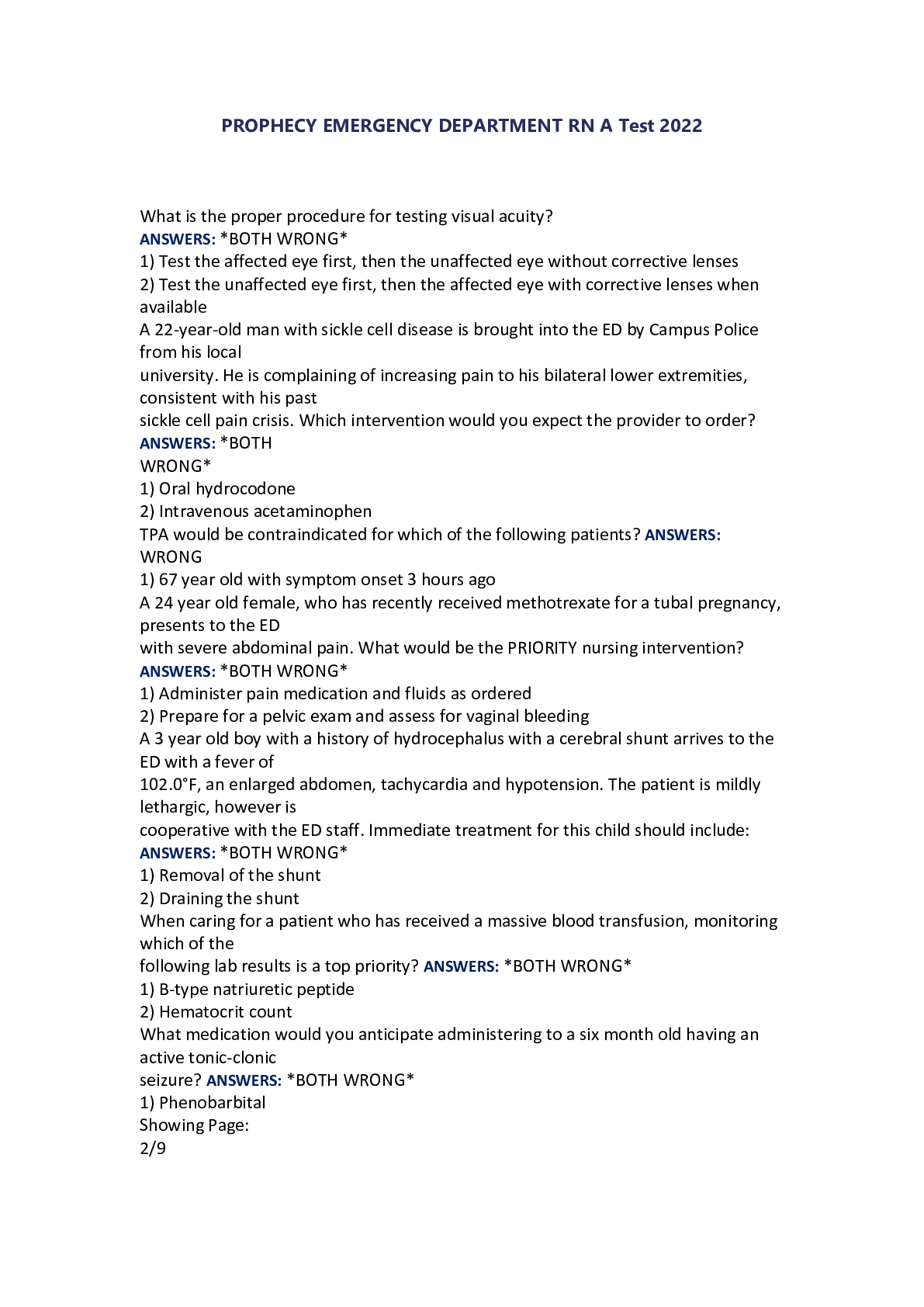
PROPHECY EMERGENCY DEPARTMENT RN A Test 2022
$ 15

I Human Interview Angela Cortez V5.1 PC PL (BASIC DDx)
$ 7

Creating Value with Data Analytics in Marketing Mastering Data Science, 2e Peter Verhoef, Edwin Kooge, Natasha Walk, Jaap Wieringa (Test Bank)
$ 25

NRS 160 Nutrition Proctored
$ 13

ATI Comprehensive Questions and Answers
$ 18

NUR 442 Exam 1 Questions
$ 18

RN ATI Mental Health 2025
$ 18

Med_surg_study_guide_test_2 2023
$ 18

FIN 36059 Exam 2023
$ 18

MSN571 MID-TERM PHARMACOLOGY QUESTIONS
$ 18
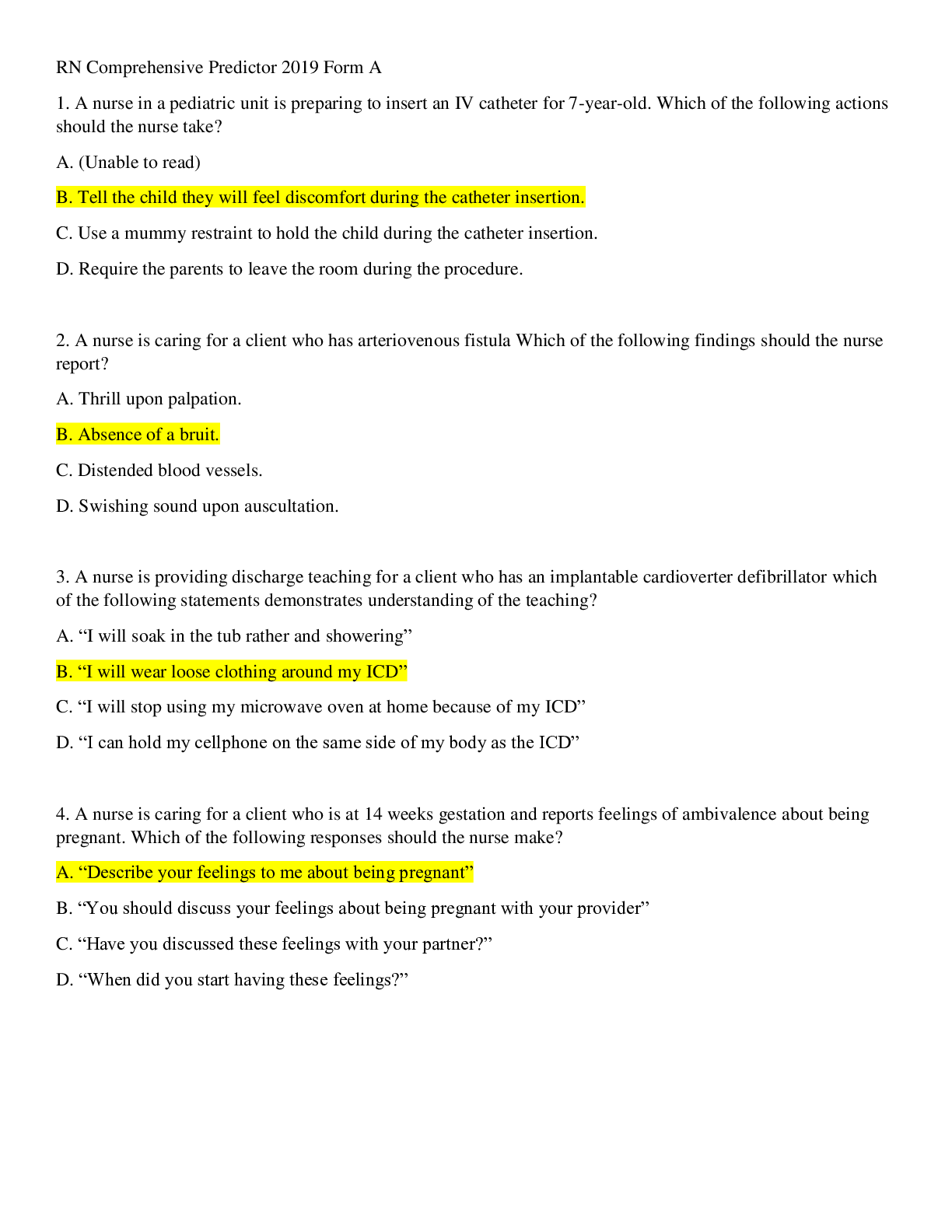
RN Comprehensive Predictor 2019 Form A
$ 15

WGU EXAM C708 PRINCIPLES OF FINANCE Questions and Answers Graded A+
$ 10.5

ATI RN COMMUNITY PROCTORED: FOCUS REVIEW 2021
$ 9
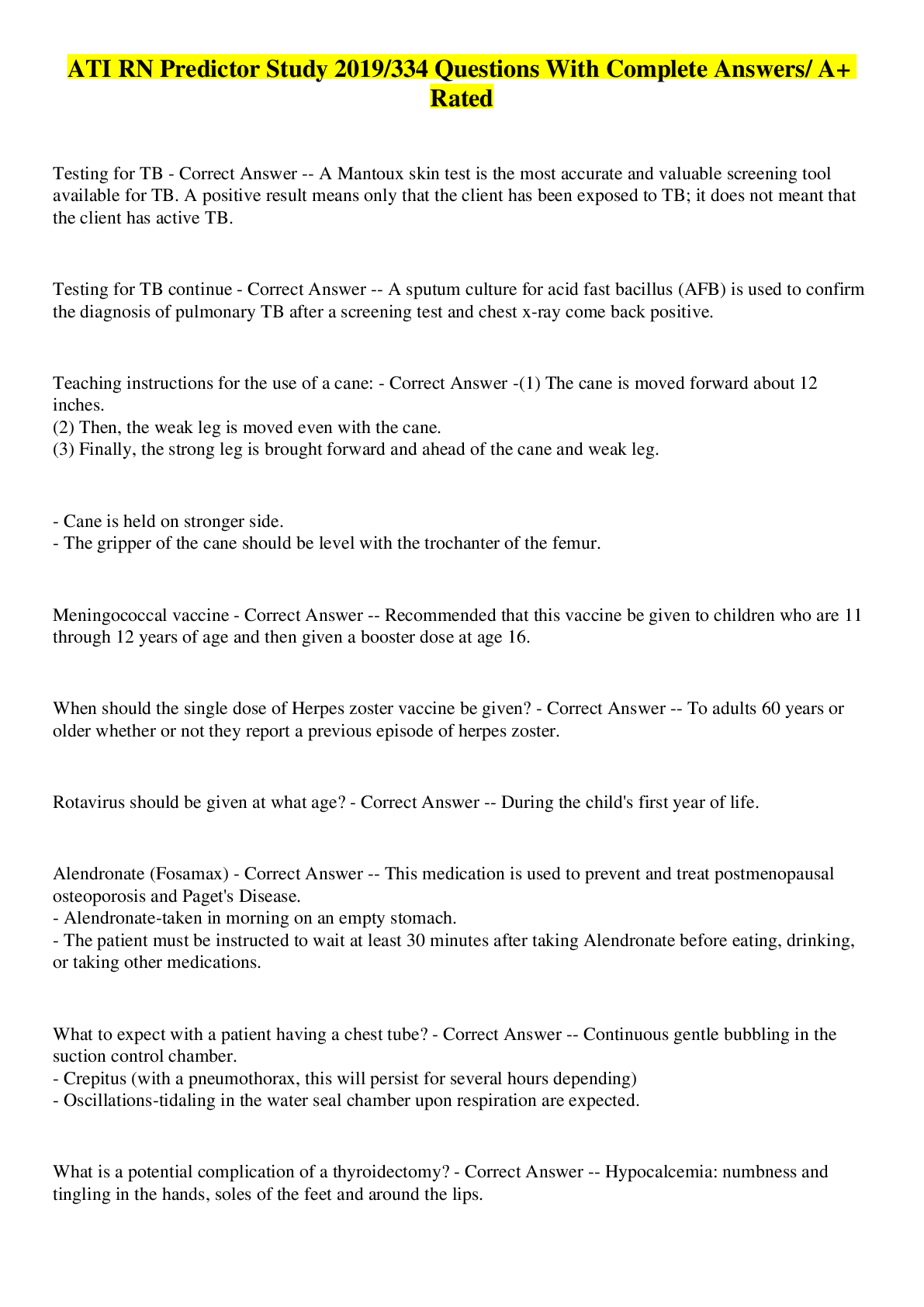
ATI RN Predictor Study 2019/334 Questions With Complete Answers/ A+ Rated
$ 14

eBook Becoming a Therapist 2nd Edition By Suzanne Bender , Edward Messner
$ 29

EXTRA ATI COMPREHENSIVE EXIT FINAL 2020 (100% Verified Solution Docs ) WITH ALL CORRECT QUESTIONS AND ANSWERS
$ 10.5

Activity: Moles, Avogadro, and Molar Mass
$ 9.5

Case Study: 1 Humongous Insueance Oveeview
$ 12

ILLINOIS PESTICIDE APPLICATOR EXAM RIGHTS-OFWAY LATEST 2024/2025 STUDY QUESTIONS WITH VERIFIED ANSWERS (GUARANTEED PASS) | RATED A+
$ 15.5

eBook Ethics in Psychology and the Mental Health Professions: Standards and Cases 4th Edition By Gerald P. Koocher , Patricia Keith-Spiegel
$ 29
I Human, Rebecca Fields New Case Study
$ 10

Mid term weeks 1-4 patho.VERIFIED ANSWERS 2022 UPDATE
$ 15.5

WGU BIOCHEMISTRY OA STUDY GUIDE FOR MODULE 1- 8 LATEST AND UPDATED SOLUTION 2023/2024
$ 12

eBook Blockchain Technology for Industry 4.0 Secure, Decentralized, Distributed and Trusted Industry Environment 1st Edition By Rodrigo da Rosa Righi , Antonio Marcos Alberti , Madhusudan Singh
$ 29

eBook Data Science and Analytics for SMEs Consulting, Tools, Practical Use Cases 1st Edition By Afolabi Ibukun Tolulope
$ 29

PESTICIDE REGULATION_DPR Laws and Regulations Study Guide in Depth Questions and Answers 2023 Rated A+
$ 10

Firefighter 1 & 2 Exam Study Guide Questions And Answers( Complete top Solution Rated A)
$ 12.5

University Of California | Econ-IS 13 Homework 2 .LATEST SOLUTION
$ 12.5

eBook Lehne's Pharmacotherapeutics for Advanced Practice Nurses and Physician Assistants 2nd Edition by Laura D. Rosenthal DNP RN ACNP-BC FAANP , Jacqueline Rosenjack Burchum DNSc FNP-BC CNE
$ 29

Instructor's Guide with Test Bank Police Leadership and Administration A 21st-Century Strategic Approach, 2nd Edition By Gennaro F. Vito, Anthony G. Vito, William F. Walsh
$ 19
PEARSON EDEXCEL LEVEL 3 GCE ECONOMICS, MARKETS AND BUSINESS BEHAVIOR. Q$ A answers.
$ 13

eBook International Models of Changemaker Education Programs, Methods, and Design 1st Edition By Viviana Alexandrowicz , Paul M. Rogers
$ 29

NRSE 3540 ~ Exam 2 Study Guide
$ 18

NURS 6565 Exam Question And Answers (100% Correct Solutions)
$ 16.5

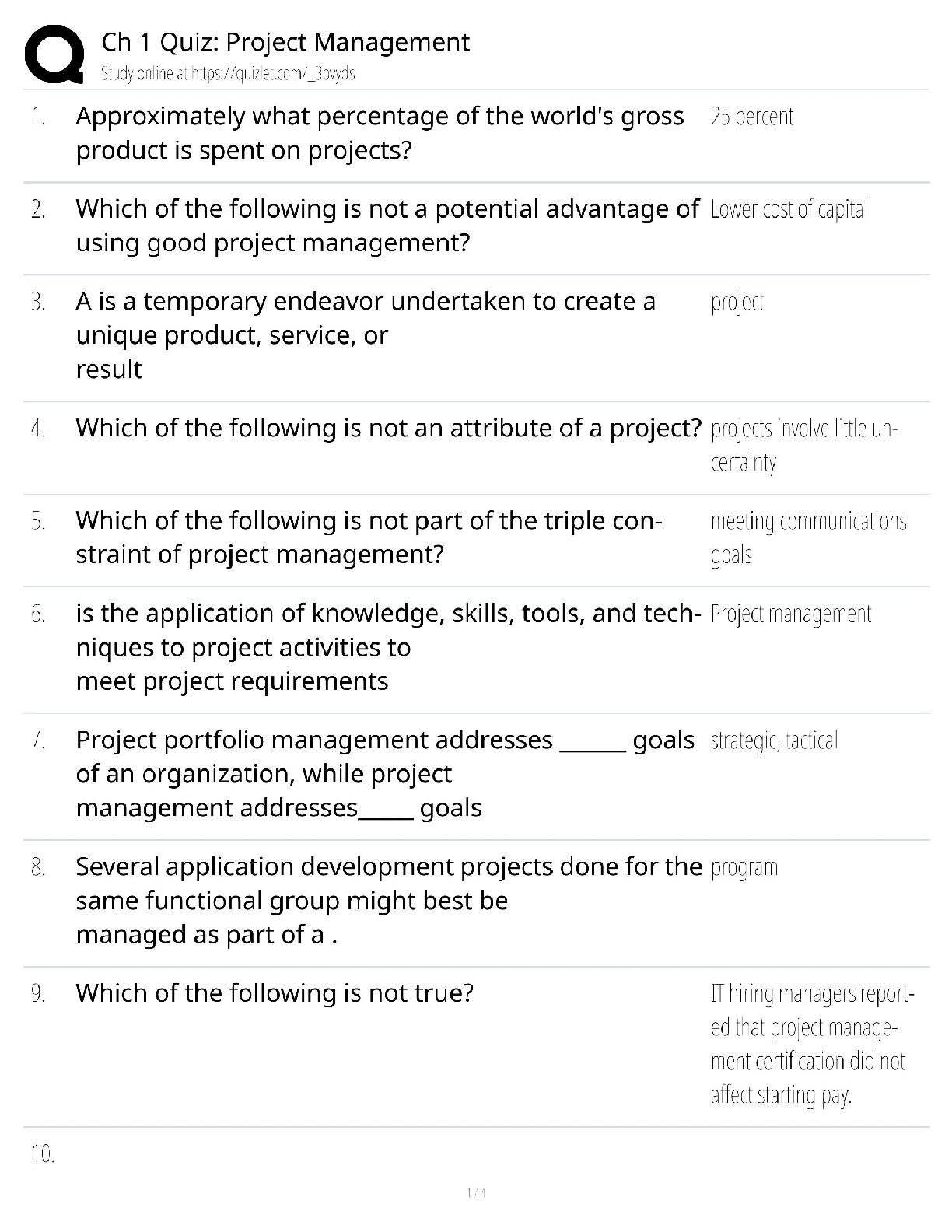
Project Management Assessments
$ 10.5

eBook Transformative Leadership in Education Equitable, Inclusive, and Quality Education in an Uncertain and Complex World, 3rd Edition by Carolyn M. Shields
$ 29
Paediatrics gastroenterology
$ 7.5

PESTICIDE APPLICATORS LICENSE REVISION QUESTIONS WITH ANSWER LATEST UPDATE 2024
$ 17

eBook When Middle-Class Parents Choose Urban Schools, Class, Race, and the Challenge of Equity in Public Education by Linn Posey-Maddox
$ 29

ATI RN LEADERSHIP PROCTORED: FOCUS REVIEW {UPDATED} | ATI RN LEADERSHIP PROCTORED: FOCUS REVIEW_A+
$ 6.5

health assessment in nursin1
$ 8

MATH 225N Week 1 Assignment / MATH225 Week 1 Assignment: Variables and Measures of Data: (Latest, 2020): Chamberlain College of Nursing | 100 % VERIFIED ANSWERS, GRADE A
$ 10
 Correct Study Guide, Download to Score A.png)
Case Study Rasmussen College Practical Nursing – A & P 1 MA278 BSC2, Module 1 Case Study, Ben, 6-month-old, (Latest 2021) Correct Study Guide, Download to Score A
$ 15

TEST BANK FOR INTRODUCTION TO CRITICAL CARE NURSING 7TH EDITION BY SOLE (Chapter 9: Ventilatory Assistance)
$ 9.5

Exam 3 Study Guide_2022_03_24_02_41_42.pdf
$ 10

Test Bank For International Financial Management, 9th Edition By Cheol Eun, Bruce Resnick, Tuugi Chuluun
$ 22
NR507 / NR 507 / NURS 507/ NURS507 FINAL EXAM STUDY GUIDE.
$ 12

ATI Leadership Retake NCLEX Assignment
$ 9

ATI RN Maternal Newborn QuestionBank 202324
$ 39.5
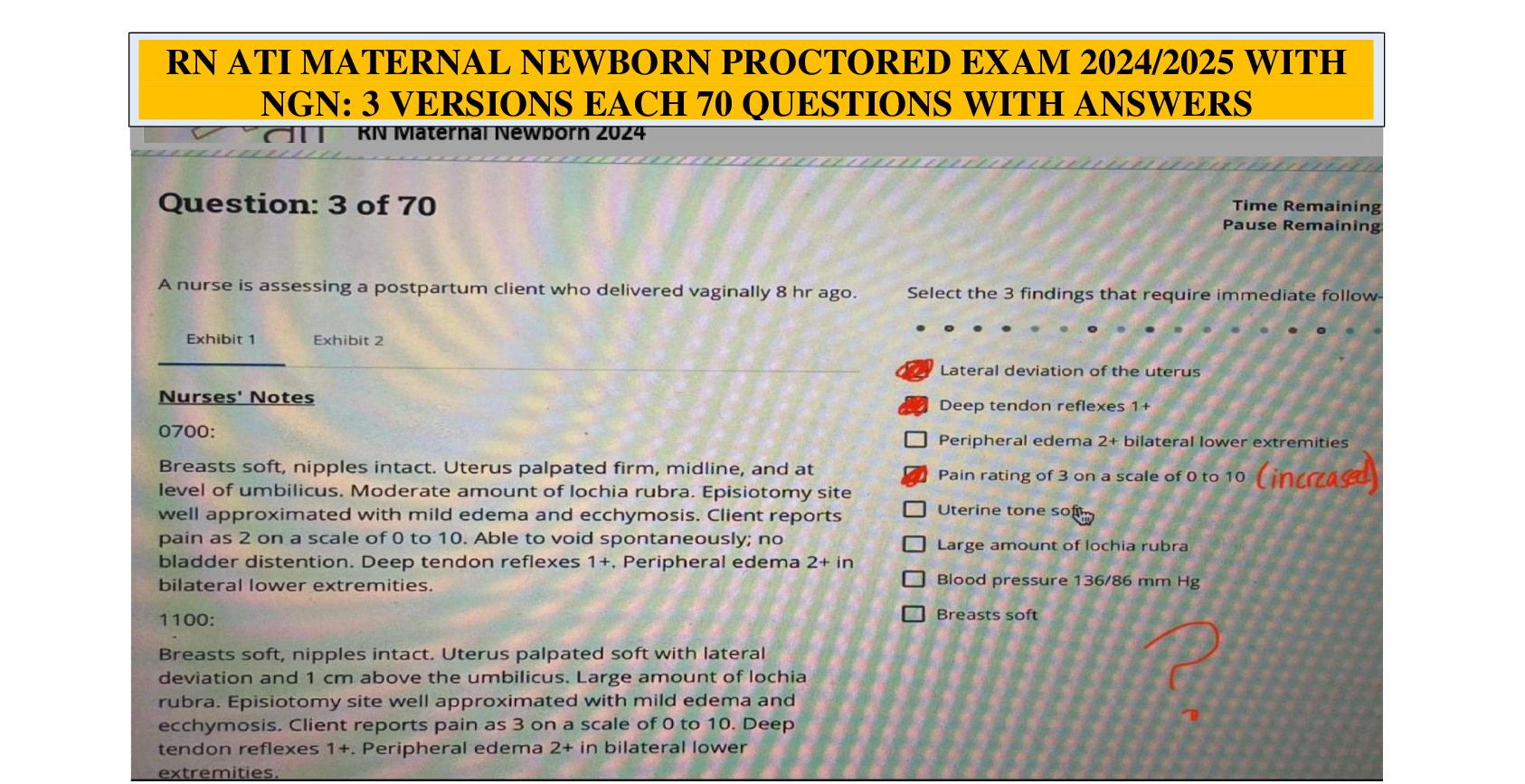
RN ATI Maternal Newborn Proctored Exam 2024/2025 |All Questions With NGN: 3 Versions Each 70 Questions With Answers
$ 45

Test Bank For Chemistry 8th Edition by Jill Robinson, John McMurry, Robert Fay Chapter 1-23
$ 19

Excel Crash Course Exam from Wall Street Prep (Finance) Questions and Answers 2023.
$ 22

CSBI – HFMA(Terms for HFMA certified specialist business intelligence)Questions And Answers.
$ 7

HESI A2 Math Questions and Answers New update
$ 9.5

SDV ABLE Exam with complete solution
$ 9.5
(Chamberlain) NR-283 Pathophysiology Comprehensive Final Exam Guide Q & S 2024
$ 15

NR 222WEEK 5 Health and Wellness
$ 30

Introduction to Finance Markets, Investments, and Financial Management, 16th Edition By Ronald Melicher, Edgar Norton | [eBook][PDF]
$ 26

Introduction to Corporate Finance, 5th Edition by Laurence Booth & W. Sean Cleary & Ian Rakita - Latest, Complete and Elaborated-FULL(864 Pages)-ALL Chapters
$ 46

ATI Test B. Questions and answers. Graded A+