EXIN ISFS - Information Security
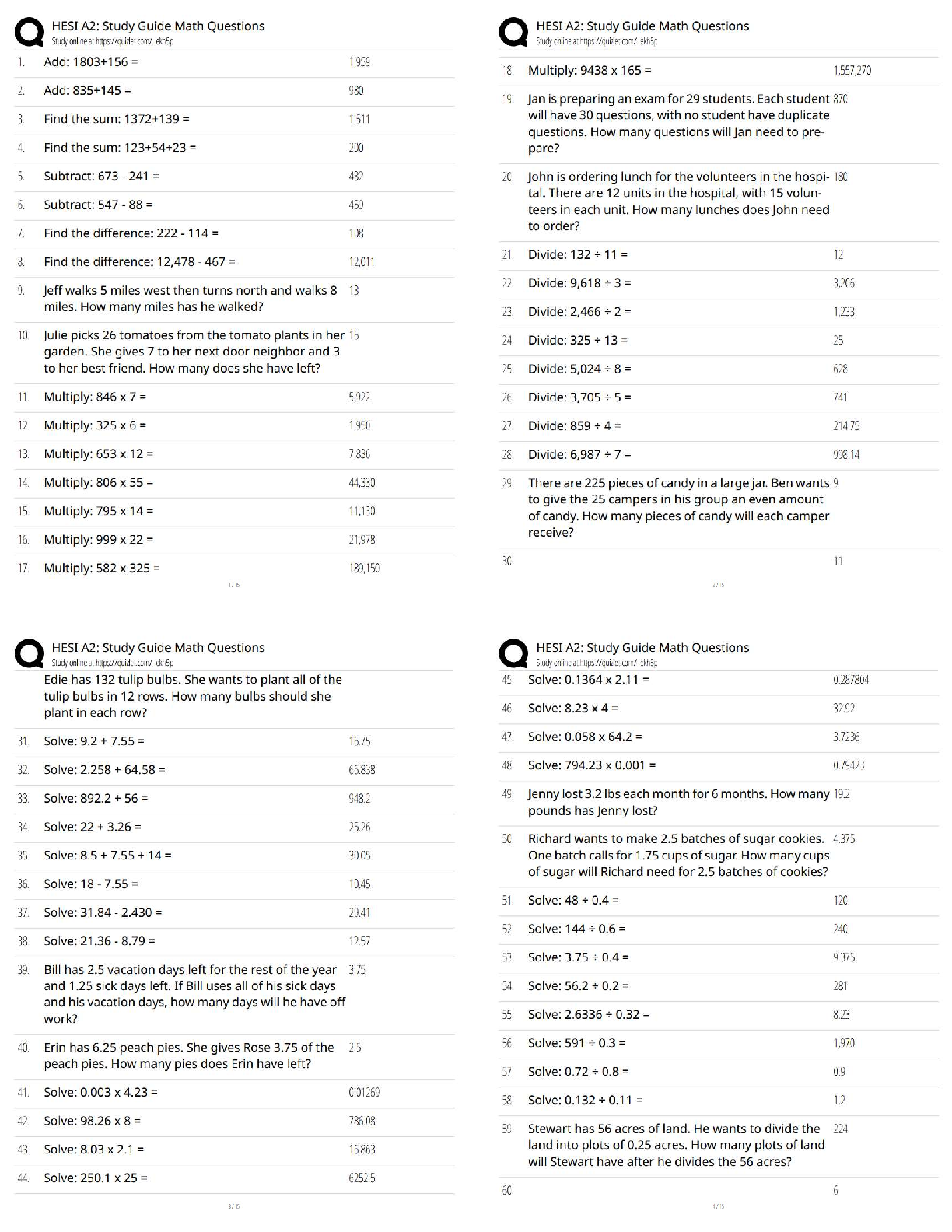
Foundation certification
What is the relationship between data and information?
A. Data is structured information.
B. Information is the meaning and value assigned to a collection of
...
EXIN ISFS - Information Security
Foundation certification
What is the relationship between data and information?
A. Data is structured information.
B. Information is the meaning and value assigned to a collection of data. - ✔✔B. Correct.
Information is data that has a meaning in some context for its receiver.
(Chapter 3)
In order to take out a fire insurance policy, an administration office must determine the value of
the data that it manages.
Which factor is not important for determining the value of data for an organization?
A. The content of data.
B. The degree to which missing, incomplete or incorrect data can be recovered.
C. The indispensability of data for the business processes.
D. The importance of the business processes that make use of the data. - ✔✔A. Correct. The
content of data does not determine its value. (Chapter 4)
A hacker gains access to a webserver and can view a file on the server containing credit card
numbers.
Which of the Confidentiality, Integrity, Availability (CIA) principles of the credit card file are
violated?
A. Availability
B. Confidentiality
C. Integrity - ✔✔B. Correct. The hacker was able to read the file (confidentiality). (Chapter 3)
There is a network printer in the hallway of the company where you work. Many employees
don't pick up their printouts immediately and leave them on the printer.
What are the consequences of this to the reliability of the information?
A. The integrity of the information is no longer guaranteed.
B. The availability of the information is no longer guaranteed.
C. The confidentiality of the information is no longer guaranteed. - ✔✔C. Correct. The
information can end up or be read by persons who should not have access to the information.
(Chapter 3)
A well-executed risk analysis provides a great deal of useful information. A risk analysis has
four main objectives.
What is not one of the four main objectives of a risk analysis?
A. Identifying assets and their value
B. Implementing counter measures
C. Establishing a balance between the costs of an incident and the costs of a security
measure
D. Determining relevant vulnerabilities and threats - ✔✔B. Correct. This is not an objective of a
risk analysis. Measures can be selected when in a risk analysis is determined which risks require
a security measure. (Chapter 3)
An administration office is going to determine the dangers to which it is exposed.
What do we call a possible event that can have a disruptive effect on the reliability of
information?
A. dependency
B. threat
C. vulnerability
D. risk - ✔✔B. Correct. A threat is a possible event that can have a disruptive effect on the
reliability of information. (Chapter 3)
What is the purpose of risk management?
A. To determine the probability that a certain risk will occur.
B. To determine the damage caused by possible security incidents.
C. To outline the threats to which IT resources are exposed.
D. To implement measures to reduce risks to an acceptable level. - ✔✔D. Correct. The purpose
of risk management is to reduce risks to an acceptable level. (Chapter 3)
A couple of years ago you started your com
[Show More]