Information Technology > QUESTIONS & ANSWERS > FedVTE Cyber Risk Management for Managers Questions and Answers Graded A+ (All)
FedVTE Cyber Risk Management for Managers Questions and Answers Graded A+
Document Content and Description Below
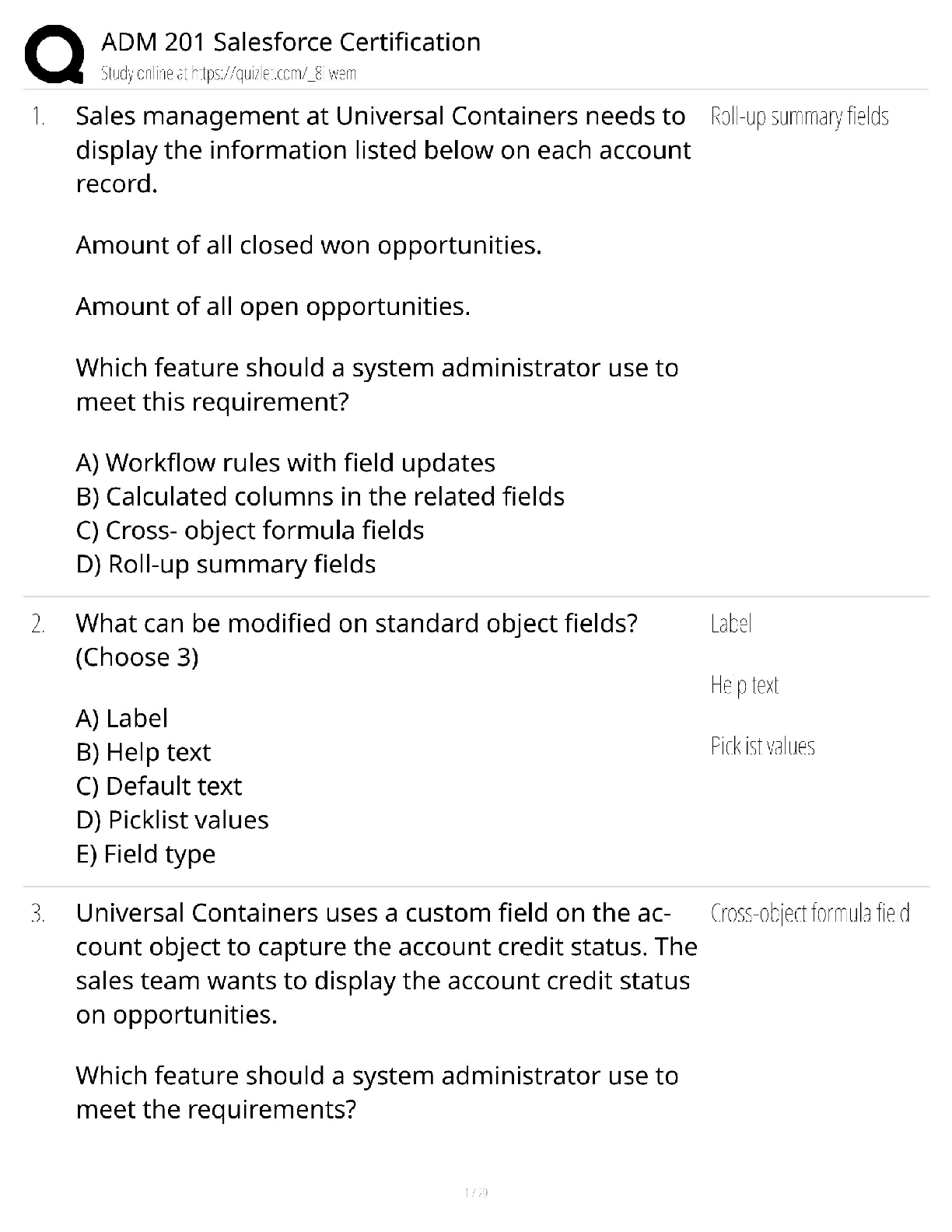
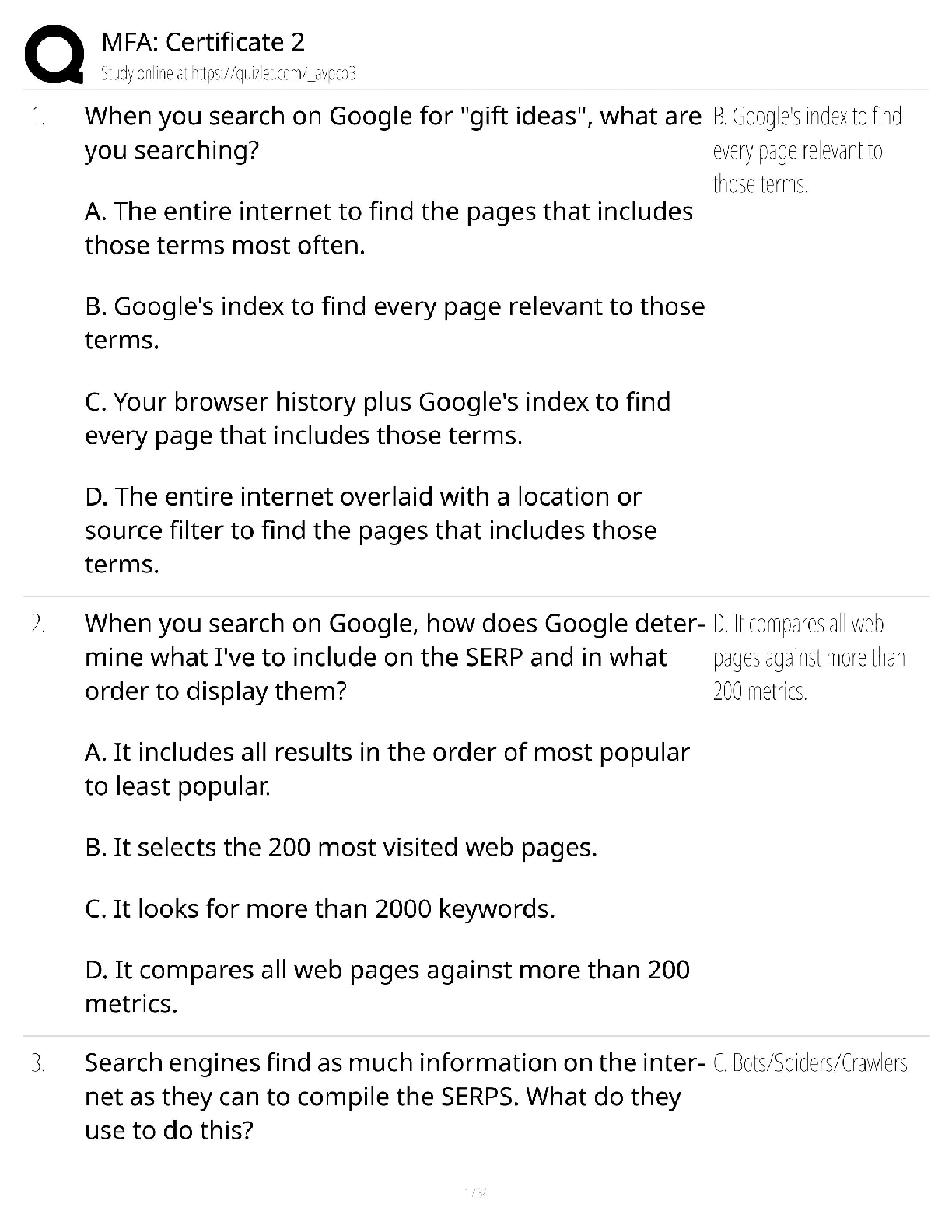
FedVTE Cyber Risk Management for Managers Questions and Answers Graded A+ Of the risk mitigation steps, in which step does management determine the most cost-effective control(s) for reducing risk ... to the organization's mission? ✔✔Step 4: Select Controls Which site is fully equipped, requiring only a short setup time due to restoring data backups and configurations? ✔✔Hot Data classification directly impacts which of the following? ✔✔All of the above A self-replicating program that requires user intervention to spread, and is typically comprised of a replication element and a payload is a(n)? ✔✔Virus In managing risks, eliminating the asset's exposure to risk, or eliminating the asset altogether, describes which one of the following? ✔✔Avoid Which type of analysis is often expressed as: annual loss expectancy = (asset value x exposure factor) x annual rate of occurrence? ✔✔Quantitative Analysis Covert security testing (white hat testing) involves testing without the knowledge of the organization's IT staff. ✔✔False People, information, and technology are examples of? ✔✔Assets Providing a basis for trust between organizations that depend on the information processed, stored, or transmitted by those systems is an Assurance "Expectation." ✔✔False Judgmental Valuation is considering variables such as technical complexity, control procedures in place, and financial loss. ✔✔False Low humidity within a server room could result in a static electricity build-up/discharge. ✔✔True Network architecture and configurations are part of which category of vulnerabilities? ✔✔Design Vulnerabilities Which of the following does an effective monitoring program NOT include? ✔✔Security impact analyses on proposed or actual changes to the information system and its environment of operation Which of the following technical controls place servers that are accessible to the public in a special network? ✔✔De-Militarized Zone A locking mechanism which is controlled by a mechanical key pad is known as? ✔✔Cipher lock The risk equation is Risk = Threat x (Likelihood + Impact) x Vulnerability? ✔✔False Which of the following families of controls belongs to the technical class of controls? ✔✔Identification and Authentication NAT is a network address translation which makes a bridge between a local network and the Internet and maps network ports. ✔✔False Which one of the following is a challenge of determining impact and risk? ✔✔All of the above Which of the following is the ability to hide messages in existing data? ✔✔Steganography A vulnerability is described as "A flaw or weakness in system security procedures, design, implementation, or internal controls that, if exercised (accidentally triggered or intentionally exploited), would result in a security breach or a violation of the system's security policy." ✔✔True Attack scripts target web browsers such as IE, through XSS, and are typically written in JavaScript. ✔✔True Which risk comes from a failure of the controls to properly mitigate risk? ✔✔Control Which of the following malware will allow an atta [Show More]
Last updated: 2 years ago
Preview 1 out of 7 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
[SOLVED] FedVTE BUNDLED EXAMS QUESTIONS AND ANSWERS WITH COMPLETE AND VERIFIED SOLUTIONS
[SOLVED] FedVTE BUNDLED EXAMS QUESTIONS AND ANSWERS WITH COMPLETE AND VERIFIED SOLUTIONS
By Nutmegs 2 years ago
$20
20
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jan 02, 2023
Number of pages
7
Written in
All
Additional information
This document has been written for:
Uploaded
Jan 02, 2023
Downloads
0
Views
137








.png)