Information Technology > QUESTIONS & ANSWERS > OPSEC QUESTIONS AND ANSWERS WITH COMPLETE SOLUTIONS (All)
OPSEC QUESTIONS AND ANSWERS WITH COMPLETE SOLUTIONS
Document Content and Description Below
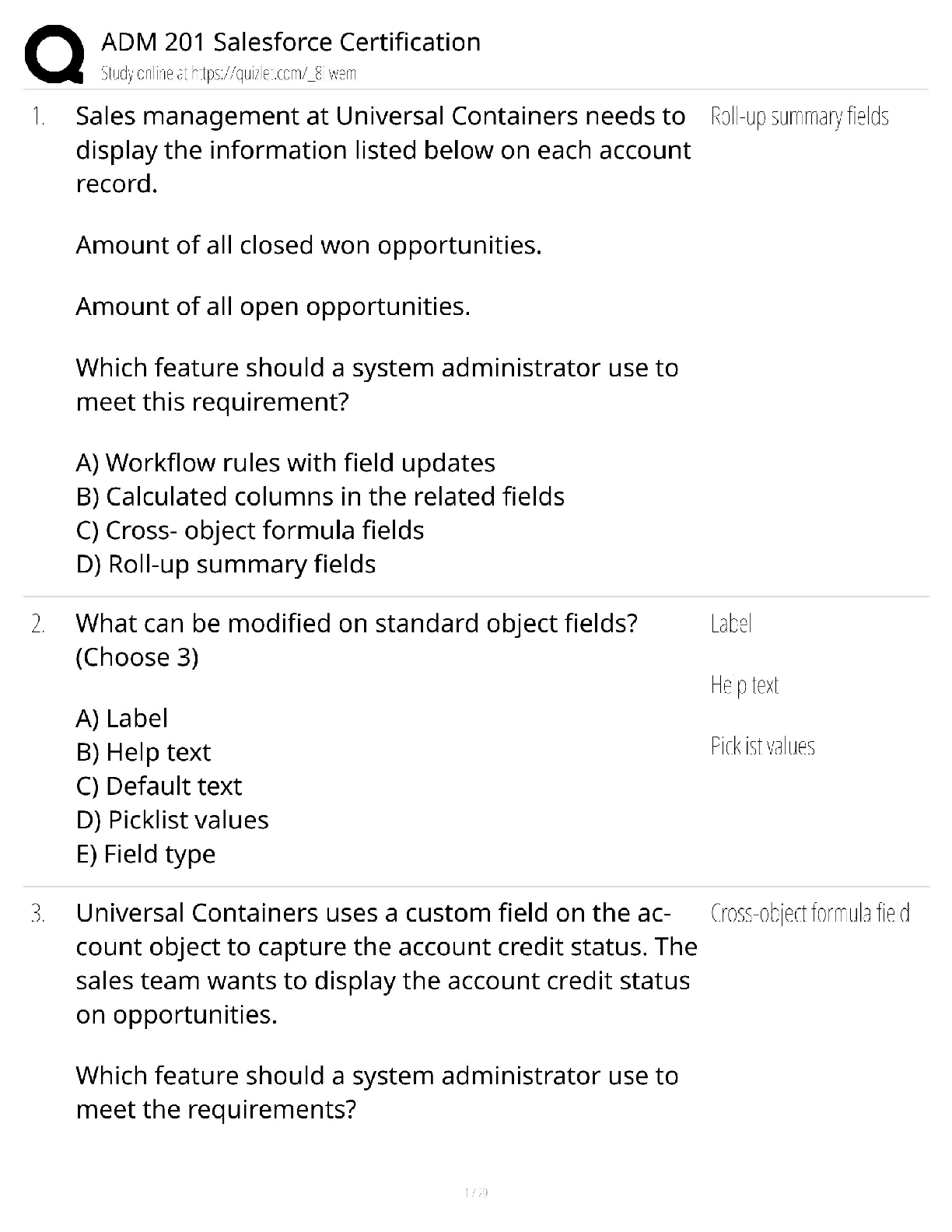
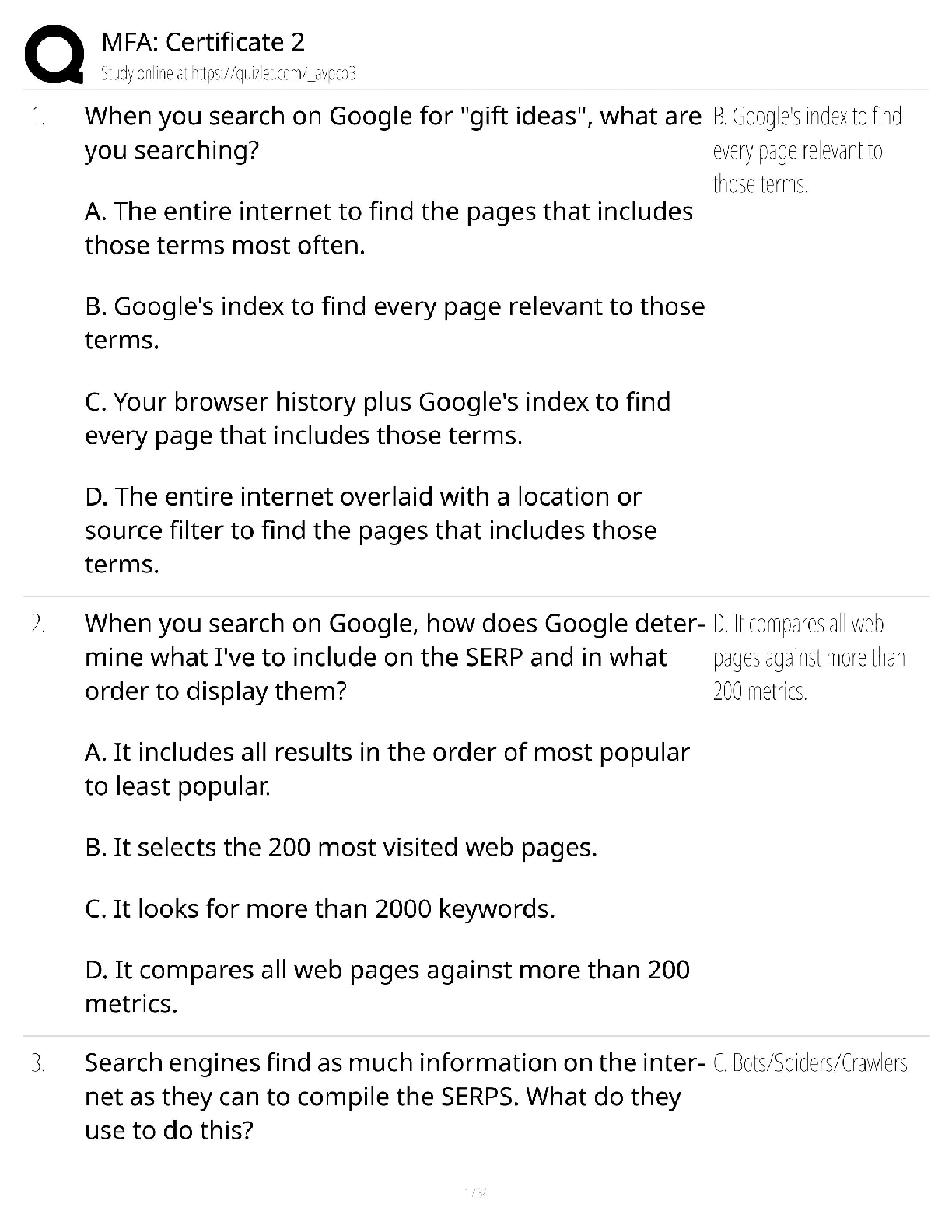
OPSEC QUESTIONS AND ANSWERS WITH COMPLETE SOLUTIONS All of the following are steps in the OPSEC process EXCEPT: ✔✔Measuring the amount of information that the adversary possesses Critical info ... rmation is: ✔✔Specific facts about friendly intentions, capabilities, and activities concerning operations and exercises. The two attributes that define a threat are: ✔✔The capability of an adversary coupled with intention to affect friendly operations. In gathering intelligence, adversaries look for __________, or those friendly actions and open sources of information that can be obtained and then interpreted to derive CI. ✔✔Indicators As a part of your OPSEC responsibilities, you should do all of the following EXCEPT: ✔✔Use the same password for all online accounts so that there is less potential for leaked information. The identification of critical information is a key part of the OPSEC process because: ✔✔It focuses the remainder of the OPSEC process on protecting vital information rather than attempting to protect all unclassified information. The purpose of OPSEC is to: ✔✔Reduce the vulnerability of US and multinational forces from successful adversary exploitation of critical information. What is the CIL? ✔✔The Critical Information List. A vulnerability exists when: ✔✔The adversary is capable of collecting critical information, correctly analyzing it, and then taking timely action. Operations Security (OPSEC) defines Critical Information as: ✔✔Specific facts about friendly intentions, capabilities, and activities needed by adversaries to plan and act effectively against friendly mission accomplishment. OPSEC countermeasures can be used to: ✔✔Prevent the adversary from detecting an indicator and from exploiting a vulnerability. Understanding that protection of sensitive unclassified information is: ✔✔The responsibility of all persons, including civilians and contractors OPSEC is concerned with: ✔✔Identifying, controlling, and protecting unclassified information that is associated with specific military operations and activities. [Show More]
Last updated: 2 years ago
Preview 1 out of 3 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
Operations Security (OPSEC) BUNDLED EXAMS QUESTIONS AND ANSWERS WITH COMPLETE & VERIFIED SOLUTIONS
Operations Security (OPSEC) BUNDLED EXAMS QUESTIONS AND ANSWERS WITH COMPLETE & VERIFIED SOLUTIONS
By Nutmegs 2 years ago
$17
17
Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jan 15, 2023
Number of pages
3
Written in
All
Additional information
This document has been written for:
Uploaded
Jan 15, 2023
Downloads
0
Views
135








.png)