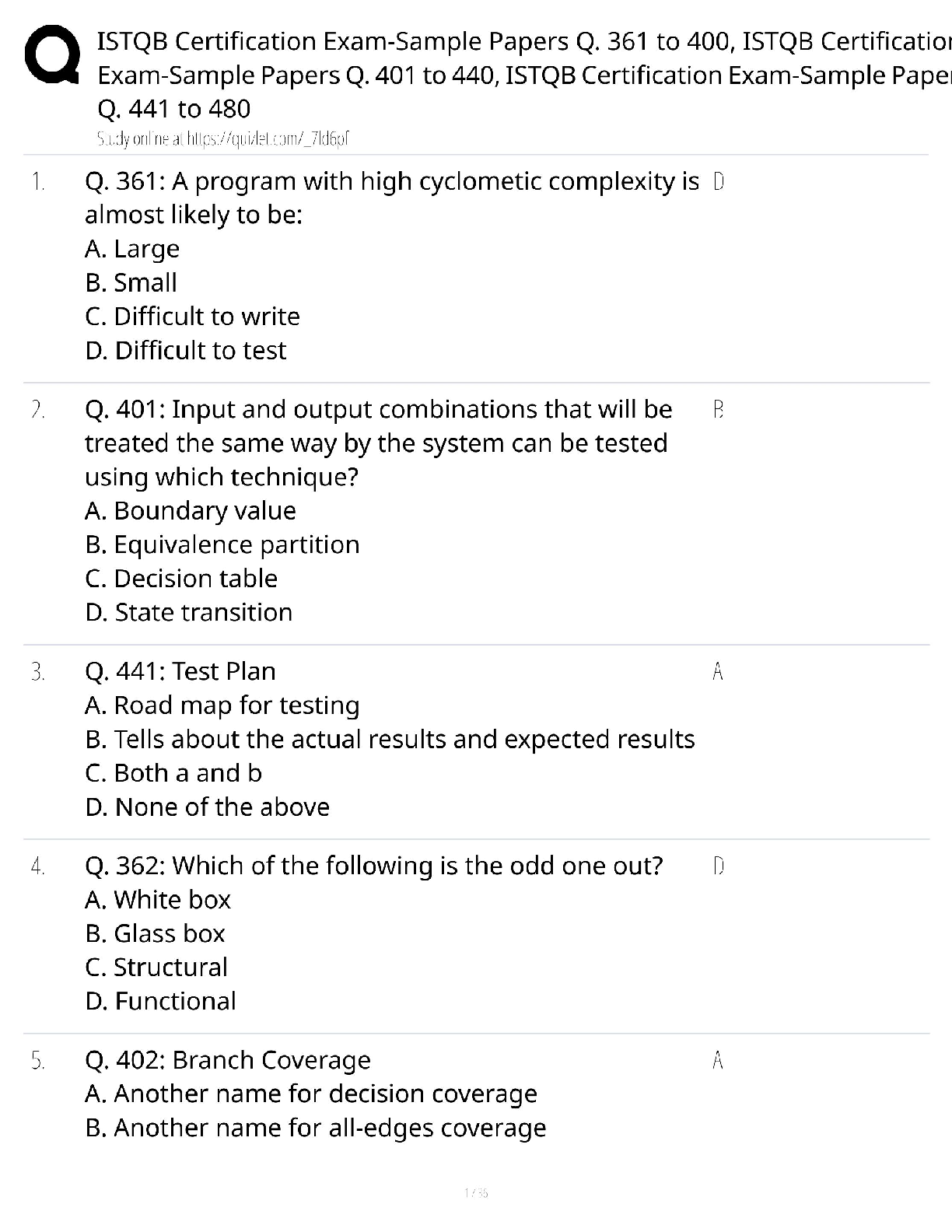
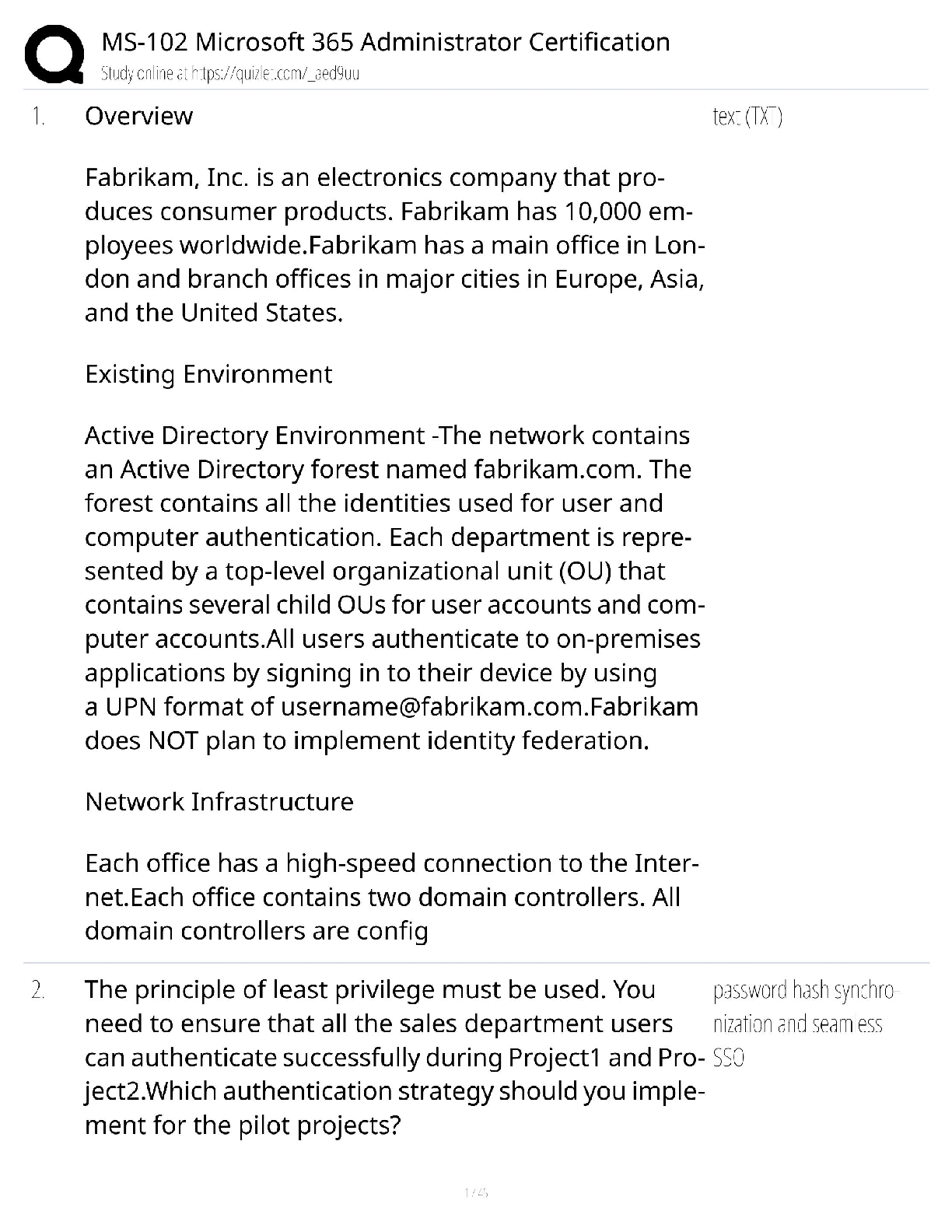
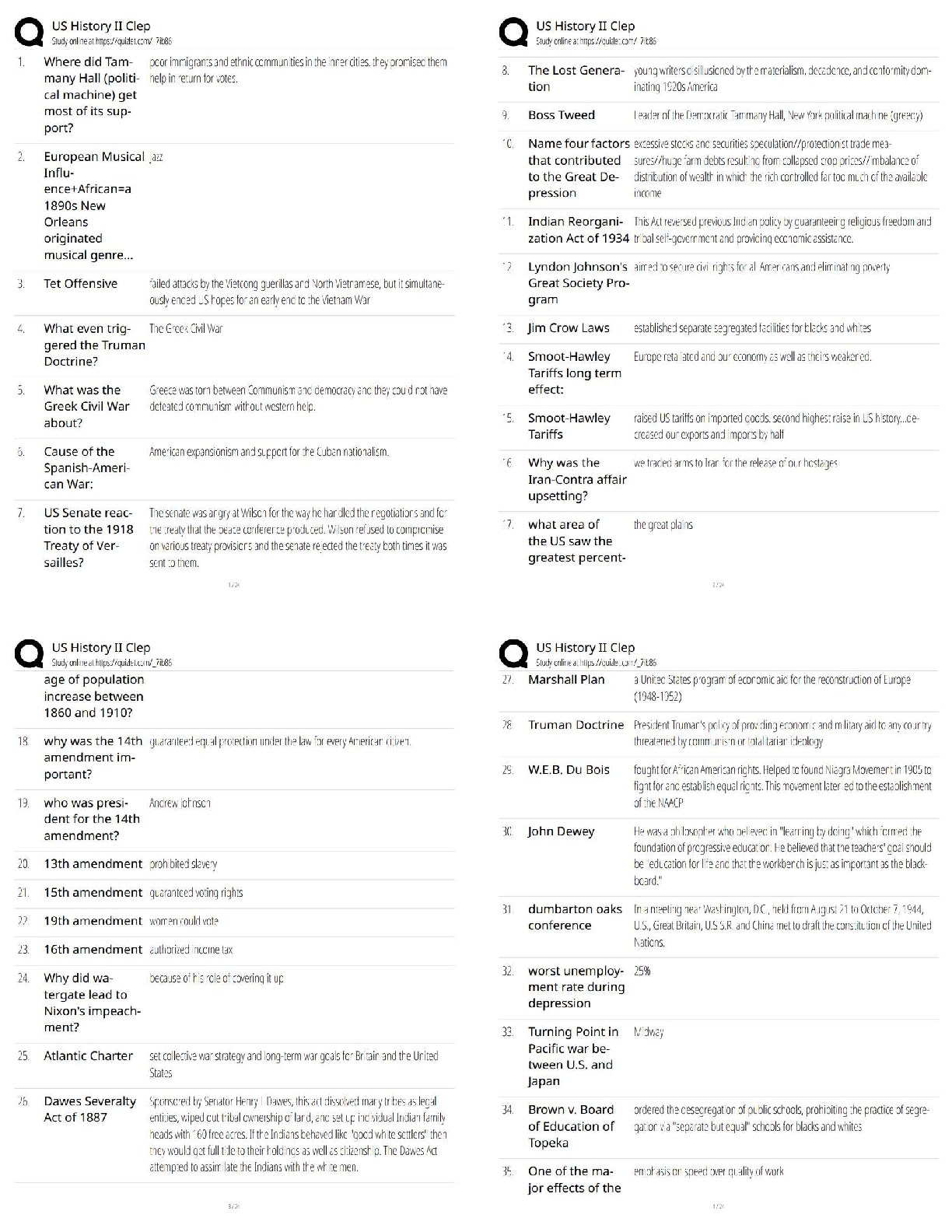
Programming > QUESTIONS & ANSWERS > C836 WGU COMPLETE QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS (All)
C836 WGU COMPLETE QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
Document Content and Description Below
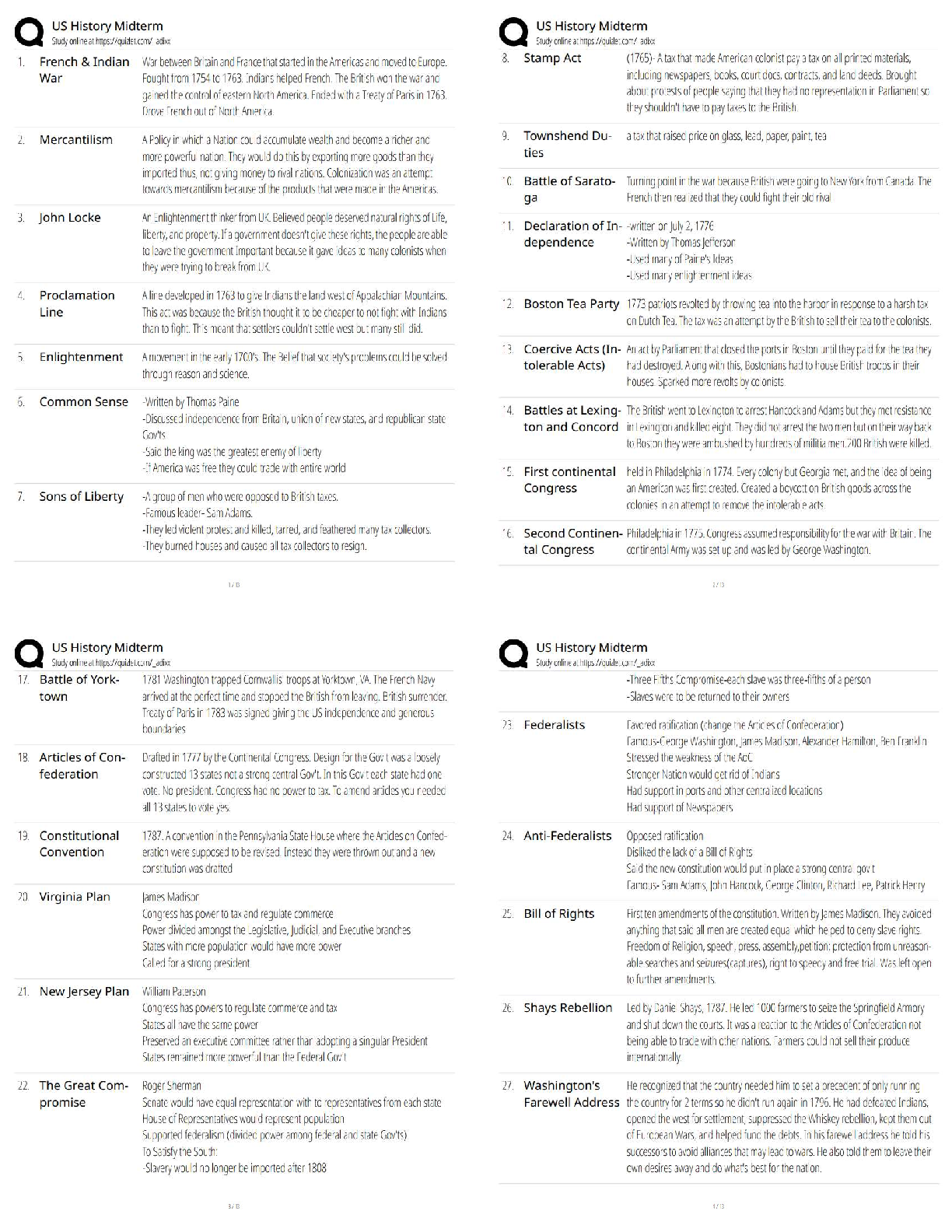
bounds checking ✔✔to set a limit on the amount of data we expect to receive to set aside storage for that data *required in most programming languages * prevents buffer overflows race conditio ... ns ✔✔A type of software development vulnerability that occurs when multiple processes or multiple threads within a process control or share access to a particular resource, and the correct handling of that resource depends on the proper ordering or timing of transactions input validation ✔✔a type of attack that can occur when we fail to validate the input to our applications or take steps to filter out unexpected or undesirable content format string attack ✔✔a type of input validation attacks in which certain print functions within a programming language can be used to manipulate or view the internal memory of an application authentication attack ✔✔A type of attack that can occur when we fail to use strong authentication mechanisms for our applications authorization attack ✔✔A type of attack that can occur when we fail to use authorization best practices for our applications [Show More]
Last updated: 2 years ago
Preview 1 out of 26 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jan 18, 2023
Number of pages
26
Written in
All
Additional information
This document has been written for:
Uploaded
Jan 18, 2023
Downloads
0
Views
120

.png)

.png)
.png)
.png)
.png)
.png)